Penetration testing
Beginner’s guide to Pentesting IoT Architecture/Network and Setting up IoT Pentesting Lab - Part 2
June 21, 2018 by
Nitesh Malviya
This is the 2nd part in Pentesting and Setting up our own IoT Lab. I hope you have gone through the first part. If not, please go through it.
Pentesting and Setting up our own Lab – Instead of creating two separate sections (one for pentesting and other for Lab) I will cover both the part together and at the end you will realize this approach is better than the former one.
What should you learn next?
From SOC Analyst to Secure Coder to Security Manager — our team of experts has 12 free training plans to help you hit your goals. Get your free copy now.
This section covers all the steps mentioned in the last post, and the following IoT architecture will be used as a reference for the explanation –
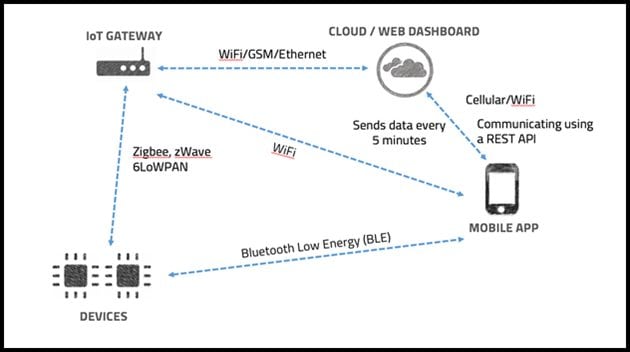
This is the same architecture which was used in the last post.
Explanation of each step and setting up our own IoT Lab –
-
List all the components involved in the given scope - This is the first step. Applying the above steps following elements are identified –
- IoT Device
- Mobile application(Android/iOS/Windows) installed on the mobile phone
- IoT Gateway
- Cloud/Web Interface
Make an architecture connecting all the components with each other – This has been already done, but in real time, you will have to make a one. It's easy, just connect all the components which share and exchange data with each other.
Mark how various components communicate with each other and what protocols do they make use of – This step is also done for us. In this step, we need to mention the protocols being used for communication.
Once the architecture and communication flow is ready, pentest each component independently – This is the most critical step. This step involves pentesting each component individually. Following components have been identified –
IoT Device – Usually a pentesting consists of the software side of any device/implementation. However, with the advent of IoT, we need to consider Hardware aspect as well. An IoT device contains firmware installed on it and physically is with the end user, unlike web or cloud server. Thus, there involves the chance of a physical attack on the device. Due to this, a penetration tester should consider hardware aspect as well. Typical IoT device Pentesting involves the following elements –
Hardware Security – Hardware security involves dealing with UART, JTAG, SPI, and I2C interface. Description of all these interfaces is out of the scope. Different hardware tools are required while dealing with these interfaces, but a comprehensive list includes following hardware tools – Multimeter, Arduino, USB to Serial adapters – Shikra, USB-TO-TTL, FT232 FTDI, BusPirate, ChipWhisperer, Jumper Wires, BreadBoard, Salea Logic Analyzer, Jtagulator, etc. For analyzing the hardware communications following software is widely used – Minicom, OpenOCD, Spiflash, baud rate.py, flash ROM, etc.
Software Security – This involves the security of firmware – Firmware Extraction and Reversing. For firmware security widely – Binwalk, FAT, Firmadyne, Firmwalker, GDB, Radare2, IDA, Qemu is used.
Radio Communication – Certain IoT device like Smart Bell, Car key fob involves Radio Communication and various attacks on Radio communication can be carried out. Following tools are used – GQRX, SDR#, Audacity, URH, RTL-SDR, HackRF, and RFCat
Web/Cloud Interface – This typically involves pentesting the Web/Cloud Interface. It is same as Web Application or Cloud Application Penetration Testing and involves the same set of tools used for Web/Cloud Penetration Testing.
Mobile Application – This involves pentesting of Android and iOS Application. It also includes the same set of tools used in Android and iOS Pentesting.
Wireless Access Point/Wi-Fi Gateway – This involves Wi-Fi Penetration Testing and mainly deals with the WPA2 attack, Weak Password Brute Force, etc.
After pentesting the components independently, pentest the communication protocol between 2 or more component – This step is the last step, and it usually involves pentesting the communication protocol between the components. Widely Bluetooth and ZigBee are used, and we need following a set of tools – Ubertooth, CSR4.0, Wireshark, Hcitool, Gatttool, Gattacker, Atmel Raven USB and KillerBee Framework.
IoT is new, and you may come across different implementation or a new protocol. Thus the choice of tools and software may vary, but the above set of tools should get your work done 90% of the time.
What should you learn next?
From SOC Analyst to Secure Coder to Security Manager — our team of experts has 12 free training plans to help you hit your goals. Get your free copy now.
This is enough to set our own lab and getting started with Pentesting an IoT Network/Environment. That's it for this post guys. Thank you.
Nitesh Malviya is a Security Consultant. He has prior experience in Web Appsec, Mobile Appsec and VAPT. At present he works on IoT, Radio and Cloud Security and open to explore various domains of CyberSecurity. He can be reached on his personal blog - https://nitmalviya03.wordpress.com/ and Linkedin - https://www.linkedin.com/in/nitmalviya03/.







