Snowden's New Revelations on Dominance in Cyberspace
Edward Snowden is continuing to release the documents he collected during his service at the NSA. His revelations on the mass surveillance operated by US intelligence and its allies, the so-called Five Eyes (Australia, Canada, New Zealand, United Kingdom, and the United States), have shocked the IT industry, but experts say the worst is yet to come. The secret documents disclosed by Snowden with the support of the principal media agencies raise a lively debate and reveal a disturbing scenario. We are in the midst of an electronic war, where cyberspace is the battlefield in which various governments are confronting on a technological level. Cyber espionage, sabotage and hacking are the main activities of governments, and the documents leaked by Edward Snowden could help us to understand how a superpower like the US works to collect information to strengthen its domination in cyberspace.
NSA Digital Arms Race
The US government is among the actors that are increasingly investing in new technology to improve their cyber capabilities. The NSA is significantly improving its methods in response to the public revelations of the whistleblower Edward Snowden, who is continuing to reveal the techniques, tactics and procedures of US intelligence.

FREE role-guided training plans
The 2013 US secret intelligence budget for the improvement of cyber capabilities and to strengthen offensive operations required around $1 billion. In 2014 the budget was fivefold, and analysts say these figures represent the tip of the iceberg and are set to grow rapidly.
A new collection of documents leaked by Snowden demonstrates that US intelligence is preparing for the future, aiming to control the Internet and any computing infrastructure of foreign governments. The US cyber experts are developing a new set of tools to infiltrate and compromise foreign infrastructure.
The German magazine Der Spiegel with a team of experts have recently viewed the secret documents and revealed that the NSA is preparing the USA for "Future Battle". The agency engaged a Digital Arms Race to build a new cyber arsenal with the purpose to compromise the enemy's computer network. Cyberspace is the fifth element of warfare and US analysts consider its control strategic. Der Spiegel confirmed that the NSA analysis seems to have no doubts according to the viewed documents:
"The next major conflict will start in cyberspace."
The US government is heavily invested to create a new generation of cyber weapons that are specifically designed hit the critical infrastructure of foreign countries, including facilities, telecommunications, banking systems, factories and transportation.
The new collection of leaked documents reveals that the US government has defined a digital war strategy, and that mass surveillance operated by the NSA is just "Phase 0″ of America's plan.
US intelligence is driving the effort of its experts to detection of critical vulnerabilities in enemy systems. Such flaws could be exploited to inject "stealthy implants" that allow the agency "permanent accesses" to the targets.
"According to top secret documents from the archive of NSA whistleblower Edward Snowden seen exclusively by SPIEGEL, they are planning for wars of the future in which the Internet will play a critical role, with the aim of being able to use the net to paralyze computer networks and, by doing so, potentially all the infrastructure they control, including power and water supplies, factories, airports or the flow of money," states Der Spiegel magazine.
One of the documents disclosed by Snowden explicitly refers to "Phase Three" of the US strategy with a disturbing appellation; it is labeled as "Dominate," and enables the NSA to "control/destroy critical systems & networks at will through pre-positioned accesses (laid in Phase 0)." Basically, while in the Phase 0 the US government has gathered information through its surveillance programs and has gained persistence on the targets by using various kinds of implants. In Phase 3, the US cyber units will move the attacks.
US intelligence is working to reach a "real time controlled escalation."
"Phase Three has been achieved — a phase headed by the word 'dominate' in the documents. This enables them to 'control/destroy critical systems & networks at will through pre-positioned accesses (laid in Phase 0).' Critical infrastructure is considered by the agency to be anything that is important in keeping a society running: energy, communications and transportation. The internal documents state that the ultimate goal is 'real time controlled escalation'."
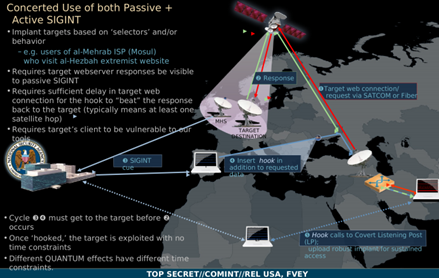
Figure 1 - Snowden slide on NSA digital war strategy
The US intelligence and its allies, the Five Eyes, adopted various techniques to achieve Phase 0 of the strategy. Malware development, sophisticated hardware implants, and wiretapping of undersea cables are just a few samples of these activities.
Der Spiegel also introduced a hacking elite team codenamed S321, described as "just a bunch of hackers", working for the Remote Operations Center (ROC) at the agency's headquarters in Fort Meade, Maryland.
"The unit responsible for covert operations, S321 employees are located on the third floor of one of the main buildings on the NSA's campus. In one report from the Snowden archive, an NSA man reminisces about how, when they got started, the ROC people were 'just a bunch of hackers.' Initially, people worked 'in a more ad hoc manner,' the report states. Nowadays, however, procedures are 'more systematic'. Even before NSA management massively expanded the ROC group during the summer of 2005, the department's motto was, 'Your data is our data, your equipment is our equipment.'"
S321 is just one of the hacking teams that the US governments is preparing for its incursion in cyberspace. The documents disclosed by Snowden also reveal another group working on the project of "global network dominance", codenamed Transgression, and serving for the department S31177. The department S31177 operates to track and prevent foreign cyber attacks.
"This form of 'Cyber Counter Intelligence' counts among the most delicate forms of modern spying."
The GENIE Project
One of documents disclosed by Der Spiegel reports that all the active collection and offensive activities run by the NSA are funded under a program called GENIE.
"The GENIE project plans, equips, and conducts Endpoint operations that actively compromise otherwise intactable targets and complement Midpoint programs that passively eavesdrop on communication links". This is the description provided by the NSA for the GENIE project. The program dedicates a special effort and budget to defensive activities like "sustaining covert domestic" surveillance.
In reality, the project is much more complex. US Intelligence is spending tens of millions of dollars to acquire zero-day vulnerabilities from third parties under a program codenamed "Community Investment".
The majority of the activities detailed in the archives recently disclosed by Snowden through the various media agencies are financed through the GENIE project. The documents demonstrate that NSA allocated more than 650 million dollars in 2013, an investment that will become billions in the next years.
QWERTY linked to Regin and WARRIORPRIDE
Hacking platforms, hardware and software implants and malware are part of the arsenal that the NSA is sharing with its allies, the Five Eyes.
Researchers at Kaspersky Lab have discovered a link between the Regin malware platform and the attack platform described in the last collection of documents published by Edward Snowden to Der Spiegel magazine. The experts have found significant similarities between the source code of Regin malware and the code of a Keylogger dubbed QWERTY, which is allegedly used by Five Eyes intelligence.
The Regin malware platform was uncovered in late November by the researchers at Symantec. It is an advanced spying tool that has been used in cyber espionage campaigns against governments, infrastructure operators, private companies, GSM telecom network operators, researchers, and private individuals.
Regin is a very sophisticated malicious code. It has a degree of technical competence rarely seen, with some resemblance to other government malware, like Flame, Duqu and the popular Stuxnet. Regin has a modular structure that gives the malware a great versatility. Experts speculated that it was tailored by US operators to run targeted campaigns.
This time, the researchers at Kaspersky Lab have discovered a shared code and functionality between Regin and Querty. By taking in consideration the high complexity of the Regin malware platform and the effort spent for its design, researchers speculated that the developers used the same platform, or belong to the same development team. Kaspersky researchers Raiu and Soumenkov confirmed that the QWERTY malware is identical in functionality to a specific Regin plugin.
"Considering the extreme complexity of the Regin platform and little chance that it can be duplicated by somebody without having access to its source codes, we conclude the QWERTY malware developers and the Regin developers are the same or working together," wrote Kaspersky Lab researchers Costin Raiu and Igor Soumenkov in a report published on the Securelist blog.
The last documents leaked by Edward Snowden and published by Der Spiegel magazine provide an overview of the malware platform, codenamed WARRIORPRIDE, which includes the QWERTY module used by the authors to log keystrokes from compromised Windows machines. Der Spiegel magazine confirmed that the WARRIORPRIDE malware is likely several years old and it has likely already been replaced.
The expert Claudio Guarnieri, involved in the analysis of the Snowden documents, provided a detailed overview of the last set of documents released by Der Spiegel. Guarnieri explained that WARRIORPRIDE is a platform designed by the Canadian Intelligence Agency, the CSEC, that presented it as a "scalable, flexible, portable CNE platform" unified across Five Eyes.
WARRIORPRIDE is a complex modular toolkit that includes a variety of plugins, including QWERTY.
"While we know that the Canadians certainly make use of WARRIORPRIDE, strings in one of the QWERTY binaries suggest that the Australian Defense Signals Directorate (DSD), now just known as Australian Signals Directorate (ASD), might have had a part in the development," wrote Guarnieri.
QWERTY is composed of a core driver called QWERTYKM, which was designed to hook Windows keyboard manager and the QWERTYLP library, which logs user activity.

Figure 2 - WARRIORPRIDE Slide - Canadian Intelligence Agency
"Its structure is really simple. It's made of a core component called QwertyKM, a driver that interfaces directly with Windows' keyboard manager, and a QwertyLP library which interacts with the driver to retrieve the keys pressed by the user and keep track of them in a file. QWERTY is composed of the following binary files: • 20120.dll • 20121.dll • 20123.sys," reported one of the documents publicly disclosed by the news agency.
20123.sys is the kernel mode component of the QWERTY keylogger that was developed starting from a plug-in called 50251 found in a Regin module.
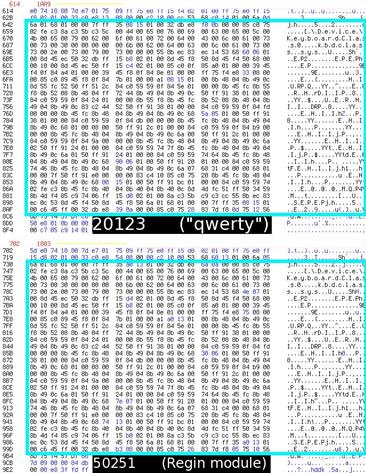
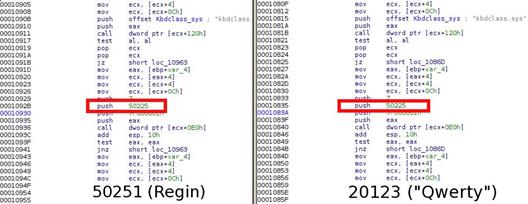
Figure 3 - Comparison Regin and QWERTY
By comparing side-by-side the codes of the two agents Regin and QWERTY, the source code appears identical. In particular, one piece of code references plug-ins of the Regin platform, and it is used in QWERTY and its Regin counterpart.
"Most of the 'Qwerty' components call plugins from the same pack (with plugin numbers 20121 – 20123), however there is also one piece code that references plugins from the Regin platform. One particular part of code is used in both the 'Qwerty' 20123 module and the Regin's 50251 counterpart, and it addresses the plugin 50225 that can be found in the virtual filesystems of Regin. The Regin's plugin 50225 is responsible for kernel-mode hooking," continues the Securelist blog post.
The researchers at Kaspersky Lab have no doubts, the QWERTY malware is a plugin designed to work as part of the Regin platform.
"This is solid proof that the QWERTY plugin can only operate as part of the Regin platform, leveraging the kernel hooking functions from plugin 50225," Raiu and Soumenkov wrote. "As an additional proof that both modules use the same software platform, we can take a look at functions exported by ordinal 1 of both modules … They contain the startup code that can be found in any other plugin of Regin, and include the actual plugin number that is registered within the platform to allow further addressing of the module. This only makes sense if the modules are used with the Regin platform orchestrator."
Concluding, the Regin platform and WARRIORPRIDE are the result of a joint effort of the Five Eyes development teams, which shared resources and knowledge on government malware development.
"It is clear now that Five Eyes, especially other than the NSA I imagine, joined efforts to share resources and collectively develop a unified malware program," said Guarnieri.
New revelations on the NSA hacking infrastructure
The last wave of documents leaked by Edward Snowden and published by Der Spiegel magazine provided further details on the hacking operations run by the NSA against the systems of foreign governments by implanting a malware. According to the files disclosed by Edward Snowden, the NSA secretly tapped into South Korean networks to run cyber espionage operations against North Korea by compromising its networks to collect information.
"Spurred by growing concern about North Korea's maturing capabilities, the American spy agency drilled into the Chinese networks that connect North Korea to the outside world, picked through connections in Malaysia favored by North Korean hackers and penetrated directly into the North with the help of South Korea and other American allies, according to former United States and foreign officials, computer experts later briefed on the operations and a newly disclosed N.S.A. document," reports The New York Times.
The NSA hackers compromised the North Korean systems by spreading malicious code through spear phishing campaigns:
"The N.S.A.'s success in getting into North Korea's systems in recent years should have allowed the agency to see the first 'spear phishing' attacks on Sony — the use of emails that put malicious code into a computer system if an unknowing user clicks on a link — when the attacks began in early September, according to two American officials."
One of the reports published by the German magazine describes how the NSA's Tailored Access Office hijacked a botnet. The operation is coded as "Boxingrumble." The Boxingrumble was initially used to target the computers of Chinese and Vietnamese dissidents and was being used to target the DOD's unclassified NIPRNET network.
When the attack hit the DoD network, the US cyber units detected the offensive by using the Turmoil system and processed data acquired on the attackers with the Xkeyscore platform. Once they identified the machines composing the botnet, the TAO hackers blocked the attack by redirecting it to honeypots used to profile the malware spread by the threat actor. Then the US intelligence deflected the attack by involving the "Quantum" platform to inject its malicious traffic in the adversary networks.
"The NSA was able to deflect the attack and fool the botnet into treating one of TAO's servers as a trusted command and control (C&C or C2) server. TAO then used that position of trust, gained by executing a DNS spoofing attack injected into the botnet's traffic, to gather intelligence from the bots and distribute the NSA's own implant malware to the targets," reports ArsTechnica.
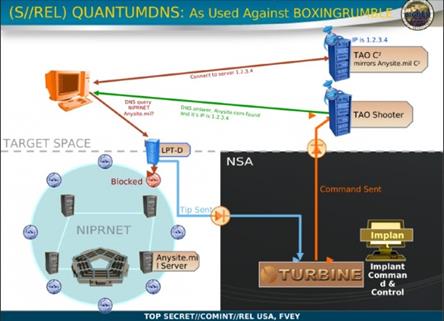
Figure 4 - Boxingrumble botnet hijacking
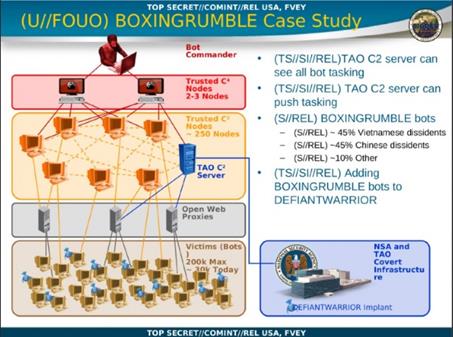
Figure 5 - Boxingrumble botnet hijacking
The US cyber army used a DNS spoofing attack to hijack to the botnet. Once they controlled the malicious infrastructure, the NSA hackers spread their own custom malware in the targeted network of the Korean government.
Another presentation leaked by Snowden reveals that the bot-hijacking attack dubbed "Quantumbot" was conducted as part of a larger operation codenamed DEFIANT WARRIOR, which utilized the XKeyscore platform to elaborate information gathered on the targets. The operation involved all the intelligence agencies belonging to the Five Eyes alliance and their infrastructure.
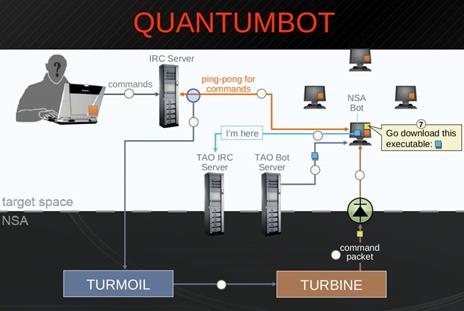
Figure 6 - Quantumbot Slide
The documents also revealed the NSA's Tutelage program, which is directly linked to the Turmoil architecture, and that is part of the Turbulence family of surveillance/hacking platforms.
Not only NSA … Snowden documents on Canadian Intelligence
The documents collected by Edward Snowden when he was working as a consultant for the NSA revealed the intense collaboration between the intelligence agencies of the Five Eyes. In the last archives disclosed by the news agencies are reported the activities conducted by the Communications Security Establishment (CSE), the Canadian government's national cryptologic agency.
The Intercept has published two reports detailing the operations run by Canadians spies. The first report described the information gathering activities conducted by the Canadian government in partnership with British intelligence. The spies have been collecting sensitive information by compromising smartphones of users all around the world.
"British and Canadian spy agencies accumulated sensitive data on smartphone users, including location, app preferences, and unique device identifiers, by piggybacking on ubiquitous software from advertising and analytics companies, according to a document obtained by NSA whistleblower Edward Snowden," states The Intercept.
The files documented the infrastructure and the methods used by British and Canadian intelligence agencies to collect device data, location information, IP addresses and other data as part of the program codenamed BADASS (BEGAL Automated Deployment And Survey System). The agents used software filters to collect information from unencrypted Internet traffic, sent by the mobile devices and the apps installed on them to servers run by advertising and analytics companies.
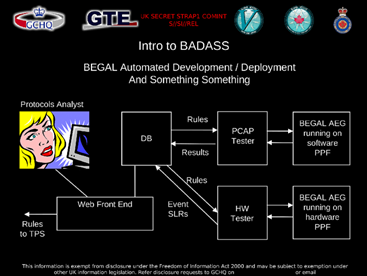
Figure 7 - BADASS (BEGAL Automated Deployment And Survey System) Program
The spies collected data from mobile devices to identify users and track their profile and their location at every moment. The overall information collected by the agents on each individual represents the base to run further targeted attacks.
A presentation of the BADASS program shows how the intelligence agencies also use Google's advertisement network AdMob as an example of intercepted, unencrypted data. The agencies exploited ads included in the majority of free mobile apps. In a specific case, if the app uses AdMob then the spies were able to collect user information the applications send back to AdMob's servers while loading the ad.
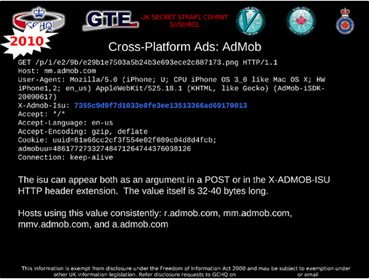
Figure 8 - BADASS program uses Google's advertisement network AdMob
Despite that Google already supports the ability for app developers to enable HTTPS for ad requests, only a small portion of AdMob users actually use it.
"The BADASS presentation also shows that British and Canadian intelligence were targeting Mobclix, Mydas, Medialets, and MSN Mobile Advertising. But it's clear that any mobile-related plaintext traffic from any company is a potential target," states the report from the Intercept.
A second report disclosed by The Intercept provided interesting details on the way Canadian intelligence is tapping Internet cables to analyze HTTP metadata related to uploads and downloads to and from 102 popular file-sharing websites including RapidShare, SendSpace, and MegaUpload.
The report documents a project codenamed LEVITATION that includes the monitoring of the most popular fire sharing platform. The cyber spies monitored about 10 to 15 million "free file upload" events per day, and the archive revealed that the Canadian Intelligence Agency has identified some 350 "interesting" downloads each month.
"Canada's leading surveillance agency is monitoring millions of Internet users' file downloads in a dragnet search to identify extremists, according to top-secret documents. The covert operation, revealed Wednesday by CBC News in collaboration with The Intercept, taps into Internet cables and analyzes records of up to 15 million downloads daily from popular websites commonly used to share videos, photographs, music, and other files," reports The Intercept.
The files confirm that the LEVITATION program does not rely on cooperation from the file-sharing companies. Another document from CSE mentions another operation codenamed ATOMIC BANJO in which the CSE agency obtains the data directly from Internet cables that it has tapped into. The cyber spies were able to syphon the unique IP address of each computer that downloaded files from the targeted websites.
"The IP addresses are valuable pieces of information to CSE's analysts, helping to identify people whose downloads have been flagged as suspicious. The analysts use the IP addresses as a kind of search term, entering them into other surveillance databases that they have access to, such as the vast repositories of intercepted Internet data shared with the Canadian agency by the NSA and its British counterpart Government Communications Headquarters," continues The Intercept, highlighting the collaboration with other intelligence agencies of the Five Eyes.

Figure 9 - ATOMIC BANJO program
The LEVITATION program was extended to numerous countries worldwide. The agents were able to monitor downloads in Europe, Middle East, North Africa, and North America.
Ron Deibert, director of University of Toronto-based Internet security think tank Citizen Lab, said LEVITATION illustrates the "giant X-ray machine over all our digital lives."
"Every single thing that you do – in this case uploading/downloading files to these sites – that act is being archived, collected and analyzed," Deibert said.
It is important to highlight that some of the file-sharing services have introduced encryption to protect their users, but numerous services still haven't implemented it.
Conclusion
The recent documents disclosed by Edward Snowden provide further information on the program financed by the US government and operated by the various units under the NSA TAO hacking team. The documents provide useful information on the infrastructure and malware used by the intelligence agencies to hack foreign government networks and explain how the NSA is working with its allies with the intent to "dominate" cyberspace.
The number of programs financed by the NSA and its allies is impressive, a surveillance dragnet that is able to spy on every individual on the Internet by using complex architecture and sophisticated malware.
The real problem now is to understand how the disclosure of the above information is changing the secret operations run by the NSA and its allies.
I'm afraid of the answer ...
References
http://securityaffairs.co/wordpress/32592/intelligence/nsa-compromised-systems-north-korea.html
http://securityaffairs.co/wordpress/32377/intelligence/nsa-digital-arms-race.html
http://securityaffairs.co/wordpress/32818/intelligence/regin-qwerty-keylogger-fiveeyes.html
http://securityaffairs.co/wordpress/32437/intelligence/china-stole-plans-f-35-aircraft.html
http://securityaffairs.co/wordpress/32592/intelligence/nsa-compromised-systems-north-korea.html
http://securityaffairs.co/wordpress/32887/intelligence/snowden-on-canadian-intelligence.html
https://nex.sx/blog/2015-01-27-everything-we-know-of-nsa-and-five-eyes-malware.html
https://firstlook.org/theintercept/2015/01/26/secret-badass-spy-program/
http://www.spiegel.de/media/media-35660.pdf
https://firstlook.org/theintercept/2015/01/28/canada-cse-levitation-mass-surveillance/
http://www.spiegel.de/media/media-35685.pdf
http://www.theregister.co.uk/2015/01/19/nsa_steals_malware/
http://www.spiegel.de/media/media-35665.pdf
http://www.spiegel.de/media/media-35689.pdf
https://firstlook.org/theintercept/2014/11/24/secret-regin-malware-belgacom-nsa-gchq/
http://www.spiegel.de/media/media-35668.pdf
https://nex.sx/blog/2015-01-27-everything-we-know-of-nsa-and-five-eyes-malware.html
http://securityaffairs.co/wordpress/32518/hacking/turnipschool-diy-nsa-spy.html
https://firstlook.org/theintercept/2015/01/26/secret-badass-spy-program/
https://firstlook.org/theintercept/2015/01/28/canada-cse-levitation-mass-surveillance/
https://www.documentcloud.org/documents/1510163-cse-presentation-on-the-levitation-project.html

FREE role-guided training plans




