Cyber-Terrorism: Complexity and Strategy
The Internet has fundamentally altered the world we live in and interact. As former Secretary of Defense Leon Panetta (2012) remarked in a speech before the Business Executives for National Security, "Cyberspace has fundamentally transformed the global economy. It's transformed our way of live, providing two billion people across the world with instant access to information, to communication, to economic opportunities" (Panetta, 2012).
Examples of the changes he spoke of include using video applications instead of placing a call to another country, instant messaging and text messaging in lieu of writing a letter or even the growing 'Internet of Things' (IOT) where physical objects linked through IP-based connections are networked together (Weber, 2013) or what Hildebrandt (2011) calls "proactive technology infrastructure" (p. 224) that begins to anticipate our needs as consumers.
For all the vast opportunities the Internet provides, it exposes potential vulnerabilities that can be exploited by adversaries. Recent news reports indicate the level of sophistication and the costs of dealing with these vulnerabilities are increasing substantially (Corrin, 2013).
Presidential Decision Directive (PDD 63) documented the industries we rely on to preserve life and property and economic functions: information and communications, banking and finance, water, transportation, law enforcement, public health, and power (US Government, 1998).
With our reliance on the Internet connecting these infrastructures, terrorism via computer is thought to be an imminent concern. Unfortunately, cyberterrorism is a strategy that has been overstated to the public and policy makers leading to public fear and questionable public policy.
DEFINING THE STRATEGY
When one thinks of terrorism, the 2001 attacks on the Pentagon and the World Trade Center immediately come to mind as well as the subway bombings in London and Madrid by Al Qaeda that same decade. Other examples include the Achille Lauro hijacking in 1985 or the Black September attack in Munich at the Olympics in 1972 by the Palestinian Liberation Organization.
However, many posit that our reliance on computers makes us vulnerable to cyberterrorist attacks. As former Secretary Panetta (2012) said, "A cyber-attack perpetuated by nation states or violent extremist groups could be as destructive as the terrorist attack on 9/11. Such a destructive attack could virtually paralyze the nation" (Panetta, 2012). Therefore, it would a mistake to not consider it under the banner of 'The Art of the Possible'.
Former Director of the Federal Bureau of Investigation (FBI) Robert Mueller, in a 2012 speech before an auditorium of cybersecurity professionals asserted modern terrorists are increasing their technological acumen. Specifically, he said, "much like every other multi-national organization, [terrorists] are using the Internet to grow their business and connect with like-minded individuals. And they are not hiding in the shadows of cyber space" (Mueller, 2012).
He goes on to say that terrorists themselves believe that cyber-warfare is the way of the future. As important as understanding the weapons or threat actors involved is, it is equally as important to properly define the strategy those actors might employ. This has proven unfortunately elusive.
The US Department of State defines orthodox terrorism as "premeditated, politically motivated violence perpetrated against noncombatant targets by subnational groups or clandestine agents, usually intended to in?uence an audience" (US Department of State, 2012). Others have provided variations on this theme.
For the sake of simplicity, this paper defines it as the calculated use of violence or its threatened use to force a political change by non-state actors (Hoffman, 2006, p. 40). Unfortunately, simply taking the term cyber and adding it to terrorism as Collins did does not make it any easier to comprehend (Conway, What is Cyberterrorism?, 2002).
Saying that (from the State Department definition) cyberterrorism is the calculated use of violence or its threatened use to force a political change by non-state actors using computers is not accurate. Simply using the Internet or cyberspace to "to grow their business and connect with like-minded individuals," as Mueller (2012) noted, is not cyberterrorism. Nor is cyberterrorism using the Internet to increase pressure on a government as Saint-Claire (2011) says the Zapatista rebels did in the mid 1990's (p. 85).
Simply "being" in cyberspace does not satisfy the definition of terrorism. It is necessary to denote the function cyberspace plays in the terrorist act in order to consider it cyberterrorism (Conway, What is Cyberterrorism?, 2002).
In her paper "What is Cyberterrorism?" Conway (2002) runs through a litany of potential definitions of the strategy of cyberterrorism all centering around the idea of non-state entities causing politically motivated damage or destruction to information, computer systems and/or computer programs through a computer or information system that could result in violence or the threat of violence against innocent people (Conway, What is Cyberterrorism?, 2002).
This definition allows for the information system as a weapon (damage to an information system connected to a physical system such as a supervisory control and data acquisition (SCADA) system using a virus or worm) but not the physical destruction of a large network communications hub with conventional explosives, such as the Metropolitan Area Exchange, East (MAE-East) location in Reston, Virginia where a significant number of major Internet service providers provide connectivity (Cryptome, 2006).
This is an important distinction. Allowing a cyberterrorist attack to include the physical destruction of a facility like MAE-East blurs the definition of cyberterrorism with traditional terrorism and therefore hinders the discussion from making forward progress by rendering cyberterrorism as indistinguishable as a tactic.
Another critical distinction is that this definition does not include those organizations conducting state-sponsored acts of cyberterrorism. Receiving funding and/or technical assistance from a sovereign country should negate any proposed example since it would not be consistent with the "non-state" portion of the definition.
Ahmad and Yunos (2012) have also described five critical components of cyberterrorism that align with Conway's decade-old definition (p. 151):
- An attack must be politically-motivated in nature and lead to death or injury
- An attack must cause fear and/or physical harm through cyber techniques
- An attack must be against critical information infrastructures such as financial, energy, transportation, and government
- An attack against non-essential services is not cyberterrorism
- An attack for financial gain as its primary motive is not cyberterrorism
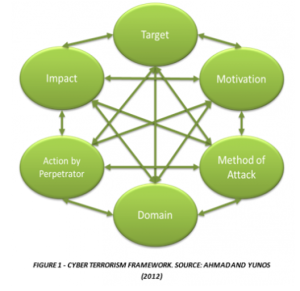
Ahmad and Yunos (2012) have developed a framework around these components to determine if something is actually cyberterrorism. This framework "provides a baseline when establishing and defining cyber terrorism" (p. 154).
Figure 1 outlines the key elements of the framework: Who is the target of the attack (target); why is the target being attacked (motivation); how is the target being attacked (method of attack); where is the attack happening (domain); what specific actions are the attackers performing (action by perpetrator); and what impact is the attack having to the target (impact)? Applying this framework is straightforward.
For example, Verton (2003) lays out a fictional scenario in his book Black Ice: The Invisible Threat of Cyber-Terrorism where traditional terrorist tactics such as using stolen fuel trucks as mobile bombs is combined with attacks from paid Russian computer hackers to start "a simultaneous cyber-onslaught against remaining utility control centers that penetrated critical Supervisory Control and Data Acquisitions (SCADA) systems – the digital brains of the electric grid and natural gas pipelines" (p. 8).
From the framework, we see the target is focused on a more dispersed audience than the organization that runs the grid; it is aimed at the public who relies on the grid (Ahmad & Yunos, 2012, p. 154). The attack is trying to generate fear.
The motivation in this scenario is religious ideology (Verton, 2003, p. 3). The method of attack (unleashing network-based attacks) is the Internet-as-weapon model Conway (2002) postulates. The domain of the attack is self-evident.
In this imaginary operation, the specific actions taken by the terrorists related to cyber were effects-based in that they were designed to, once undertaken, generate an emotional response (fear) on the part of the public that relies on the targeted service (Ahmad & Yunos, 2012, p. 156).
The final component of the framework involves impact. As cyberterrorism involves generating the emotion from the previous element across the wider audience in addition to the initial target, it has a larger impact than say a bank robbery (Ahmad & Yunos, 2012, p. 156).
It is clear from this example the proposed framework correctly identified the scenario as true cyberterrorism. However, when examined in more detail, Verton's (2003) scenario remains fictional.
There is a common idea in the news industry that says, 'If it bleeds, it leads;' stories need a sensationalist angle to catch a reader's or viewer's attention.
Conway (2002) complains stories about cyberterrorism sell papers, television, and Internet advertising but do nothing to advance any basic understanding of the problem (p. 436). In a separate article, Conway (2011) says "the term 'cyberterrorism' unites two significant modern fears: fear of technology and fear of [traditional] terrorism" (Against Cyberterrorism, p. 26). As noted previously, fear sells.
A sampling of news reports or commentaries on the subject makes Conway's point. Berner (2003) laments the fact the media glorified the dangers from cyberterrorists but then goes on to note "the resources to launch a cyber-attack are commonplace: a computer and a connection to the Internet are all that is really needed to wreak havoc" (Cyber-terrorism: reality or paranoia?, p. 2).
He lists several "traditional weapons of cyber-terrorist" (p.2) to include:
- Computer viruses
- Password cracking tools
- Network sniffing tools (to monitor traffic going on a network connection)
- Dumpster diving (physically going through trashcans looking for potentially sensitive information to use in an attack
What Berner (2003) fails to relay to his readers is that these are tools of common computer criminals, not necessarily cyberterrorists. In essence, he is blending cybercrime with cyberterrorist; he is guilty of what he criticizes others in the media of doing.
In a 2004 article in Forbes magazine, Lenzner and Vardi discuss the ability of terrorists to "shut down chunks of the Internet" (p. 13). They clearly conflate physical terrorist acts such as the September 2001 attacks with looming threats to the Internet (Lenzner & Vardi, 2004). The confusion is then created in readers' minds regarding the exact nature of the threat. This is known as fear, uncertainty, and doubt (FUD).
Traditionally defined, FUD is the concern generated about potentially switching to a competitor's products or services. It is used by ethically challenged businesses. However, in this case the meaning is less capitalist. FUD refers to the fear or worry created by something one does not fully understand.
By using terms such as cyber-attack, terrorist, 9/11, computers, tragedy, and the like, unwary readers get the sense that a computer apocalypse is nigh. Neither Berner (2003), nor Lenzner & Vardi (2004) are the only culprits in the FUD-development department. Malone (2005) says (in hyperbolic terms)
Increasingly, I am struck that there are distinct parallels between hackers and terrorists. Both are essentially powerless people who believe that they are superior to everyone else. And both are furious that, for some inexplicable reason, history has turned against them and showered its favors on the suits/infidels.
The only answer, then — one that will punish the nonbelievers and reward the Illuminati with fame (or notoriety) and power — is to destroy the greatest institutions of those history has favored. Only then will the unbelievers (and the insufficiently committed) appreciate just how superior the Illuminati really are. (Malone, 2005)
Malone, according to his biography should know better than to merge hacking and terrorism. He has reported on Silicon Valley and its industries for over two decades in several periodicals including the San Jose Mercury News, a leading technology-focused newspaper. Another example is an article from UPI (2006) that reports two men were arrested for "using the Internet and computer technology to support terrorism" (United Press International, 2006).
The headline read, "Two arrested for cyber terror support." A final cursory example of media reporting on cyber-terror could be an article in the United Kingdom's Telegraph newspaper on the restructuring of the UK's Home Office. In the article, former Home Secretary John Reid is quoted as warning of "devastating consequences" of cyberterrorism on the country's critical infrastructure (Jones, 2007); however, he provides no actual evidence of any urgent or legitimate threat.
Unfortunately, it is not just news that is distorting the idea of cyberterrorism as a strategy. Verton (2003) confuses cyberterrorism with traditional terrorism when he says "Terrorist groups that want to amplify the chaos and confusion of physical attacks or directly target the economy can succeed by launching traditional-style terrorist assaults against the nation's cyber-infrastructure" (p. 19).
As Conway (2002) notes, along with Ahmad and Yunos (2012), this is not cyberterrorism. When he notes that "skilled attackers" (p. 46) are the greatest threat the United States faces, he is mixing terrorist capabilities and computer capabilities a la Malone (2005). Terrorists and hackers each have a different motivation and the two should not be confused. Terrorists (in this case religiously motivated terrorists i.e. Al Qaeda like in Verton's scenario (Verton, 2003, p. 3)) have a clear political motivation (Hoffman, 2006, p. 2).
At its core, terrorism is about power and maintaining power. Terrorists' use of computers to spread an overtly political message on a chat forum is not any different from a local parent-teacher association using a website to announce an upcoming bake sale (this should not be confused with coordinating operational details about an attack). Certainly the end-state is different, but the using the Internet to communicate a widely disseminated message is the exact purpose of the medium.
However, even the federal government has gotten in on the act of misidentifying cyberterrorism. FBI Director Mueller warned the nation of Al Qaeda in the Arabian Peninsula's (AQAP) "full-color, English-language online magazine" and Al-Shabaab's twitter account (Mueller, 2012). In both of Mueller's (2012) examples, the employment of less radical theology as a counterweight should be considered (Witty, 2008, p. 103).
Even academia creates a misperception. Gable (2012) believes the most glaring threat facing the nation's critical infrastructure is the TCP/IP protocol that supports Internet communications and connectivity (p. 57). She goes on, as observed in other examples, to blend two fundamentally different concepts: "Indeed, cyberterrorists and hackers attempt to penetrate Department of Defense computer systems thousands of times a day" (p. 60).
While that may be true, under a framework such as Ahmad and Yunos propose, it becomes evident that because the threat actors have different motivations, only one can be labeled cyberterrorism.
REFERENCES
- Ahmad, R., & Yunos, Z. (2012). A Dynamic Cyber Terrorism Framework. International Journal of Computer Science and Information Security, 149-158.
- Berner, S. (2003, March). Cyber-terrorism: reality or paranoia? South African Journal of Information Management, 5(1). Conway, M. (2002). What is Cyberterrorism? Current History, 436-442.
- Conway, M. (2007). Cyberterrorism: Hype and Reality. In L. Armistead, Information Warfare: Separating Hype from Reality (pp. 72-94). Dulles, VA: Potomac Books.
- Conway, M. (2011). Against Cyberterrorism. Communications of the ACM, 26-28.
- Corrin, A. (2013, October 08). Frequency, costs of cyberattacks on the rise. Retrieved from Federal Computer Week: http://fcw.com/articles/2013/10/08/cyberattacks-frequency-costs-rise.aspx
- Cryptome. (2006, February 13). MAE East Colocation Birdseye. Retrieved from Cryptome: http://cryptome.org/eyeball/mae-east/maee-birdseye.htm
- Gable, K. A. (2012). Cyber-Apocalypse Now: Securing the Internet Against Cyberterrorism and Using Universal Jurisdiction as a Deterrent. Vanderbilt Journal of Transnational Law, 57-118.
- Hildebrandt, M. (2011). Legal Protections by Design: Objections and Refutations. Legisprudence, 5(2), 223-248.
- Hoffman, B. (2006). Inside Terrorism. New York: Columbia University Press.
- Jones, G. (2007, April 26). Cyber terror threat is growing, says Reid. Retrieved from The Telegraph: http://www.telegraph.co.uk/news/uknews/1549757/Cyber-terror-threat-is-growing-says-Reid.html
- Lenzner, R., & Vardi, N. (2004). The Next Threat. Retrieved from Forbes: http://www.forbes.com/forbes/2004/0920/070.html
- Lewis, J. A. (2002). Assessing the Risk of Cyber Terrorism, Cyber War and Other Cyber Threats. Washington, DC: Center for Strategic and International Studies.
- Malone, M. S. (2005, August 18). Silicon Insider: Fighting Cyberterror. Retrieved from ABC News: http://abcnews.go.com/Business/SiliconInsider/story?id=1067367&page=1
- Mueller, R. (2012, March 01). Prepared Remarks at RSA Cyber Security Conference. San Francisco, CA.
- Nacos, B. (2000). Accomplice or Witness? The Media's Role in Terrorism. Current History, 174-178.
- National Consortium for the Study of Terrorism and Responses to Terrorism. (2012). Global Terrorism Database Search Results . Retrieved from University of Maryland: http://www.start.umd.edu/gtd/search/Results.aspx?search=cyber&sa.x=-852&sa.y=-138&sa=Search
- Nyugan, R. (2013). Navigating Jus Ad Bellum in the Age of Cyber Warfare. California Law Review, 1079-1129.
- Panetta, L. (2012, October 11). Address at Business Executives for National Security. New York, NY.
- Saint-Claire, S. (2011). Overview and Analysis of Cyber Terrorism. School of Doctoral Studies (European Union) Journal, 85-98.
- Shiryaev, Y. (2012). Cyberterrorism in the Context of Contemporary International Law. San Diego International Law Journal, 139-192.
- United Press International. (2006, August 24). Two arrested for cyber terror support. Retrieved from UPI.com: http://www.upi.com/Business_News/Security-Industry/2006/08/24/Two-arrested-for-cyber-terror-support/UPI-23391156446719/
- US Department of Defense. (2012, June 20). DoD Operaitions Security (OPSEC) Program. Retrieved from Defense Technical Infomration Center: http://www.dtic.mil/whs/directives/corres/pdf/520502e.pdf
- US Department of State. (2012, May 30). Country Reports on Terrorism. Retrieved from US Department of State Bureau of Counterterrorism: http://www.state.gov/j/ct/rls/crt/2012/209990.htm
- US Government. (1998, May 22). Critical Infrastructure Protection (Presidential Decision Directive 63). Retrieved from Federation of American Scientists: http://www.fas.org/irp/offdocs/pdd/pdd-63.htm
- US Government. (2001, October 26). USA PATRIOT Act. Washington, DC.
- Verton, D. (2003). Black Ice: The Invisible Threat of Cyber-Terrorism. New York: McGraw-Hill/Osbourne.
- Weber, R. H. (2013). Internet of things – Governance quo vadis? Computer Law and Security Review, 29, 341-347.
- Witty, D. M. (2008). Attacking al Qaeda's Operational Centers of Gravity. Joint Forces Quarterly, 98-103.