.NET reversing with Reflexil
Technically speaking a .NET built software or component (DLL) resembles an executable assembly. That's because it's compiled in MSIL, and you can usually view the source in Reflector and many other tools such Ispy. But when it comes to commercial software, more and more complicated protection mechanisms are being implemented to shield them. After analyzing many products, I discovered so much about how all these components share to protect themselves. My motive to write this paper is that I couldn't find any papers on this topic in detail. That's because hackers are still not interested in this platform yet. Today, I have chosen a target that is unfortunately full of bugs, so don't expect it to be very hard. This is just an introduction, and later I will demonstrate more difficult subjects, such as code injection.
This article illustrates these topics in detail:

Become a certified reverse engineer!
Reversing is impossible without the using appropriate tools. There are numerous programs available out there that can be used for executing reverse engineering, some are freeware and others are commercialized. Thus, understanding the differences between these tools and choosing the right ones is critical. It's up to you to decide whether your reversing projects justify spending money on software.
In the context of .NET, the modification of software methods with MSIL at runtime is captivating. It helps with implementing software protection, hooking, and other functions. But there's a challenge. The IL instruction code could have been JIT complied to native code before it's possible to alter it. Also, the .NET CLR implementation isn't detailed. It changes with each version. We need a stable approach without being dependent on the precise memory layout. Reflexil is a great tool for doing an in-depth examination of various types of assemblies and also for disassembling IL code with .NET support. It allows modifications of IL code by using the powerful Mono.Cecil library.
Prerequisite
This tutorial requires a thorough understanding of MSIL code instruction. This paper mentions malfunctioning instructions, in order to patch an executable. You need to install the following programs on the reverse engineering machine:
- Reflector 7.x version
- Reflexil Plugin
- Visual Studio 2010 or later
Reflexil Installation and configuration
The Reflexil installation process includes a couple of steps. First of all, we have to download the program. Reflexil isn't full-fledged software. It's a plugin, and can be connected to Reflector by importing its DLL file. The DLL file could be downloaded from www.reflexil.net. It's open source and not commercialized yet.
Open the Reflector IDE, and go to Tools, Add-Ins. The Reflexil file that we downloaded earlier is a DLL, in a folder along with other supporting files. So, all we have to do is import the Reflexil.Reflector.dll file in the Add-Ins dialog box.
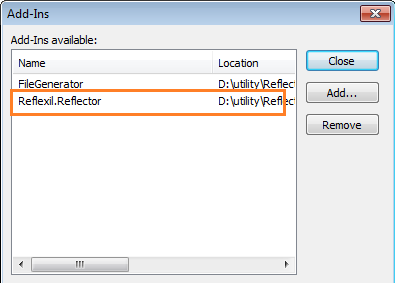
After successfully adding the Reflexil DLL file, notice the Reflexil option appears in the Reflector Tools menu. The Sebastien LEBRETON Reflexil editor will be appear while clicking the option.
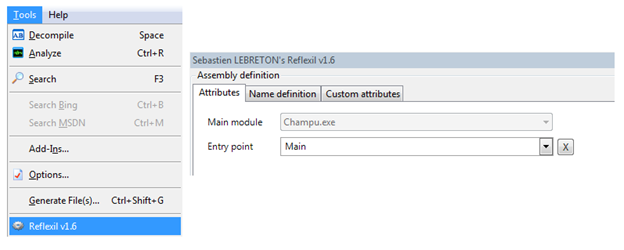
Now, the magic is, we can manipulate Reflector functionality with Reflexil's features, which we shall examine in the next section. We can overcome the various limitations of Reflector, such as .NET byte code editing, and re-saving the assembly without the assistance of Visual Studio.
Encountering with Reflexil
Reflexil is a plugin for Redgate Reflector. It exists to to extend the functionality of Reflector. Reflexil is usually a .NET assembly editor. It uses the open source Mono.Ceil libraries, and it's capable of rewriting MSIL opcode instructions, as well as saving as a modification, like to OllyDbg and IDApro. It has the following advantages:
-
Code injection support with intellisense: It's possible to open assembly source code into Reflexil, rather than Visual Studio, for code analysis and modification. This is the real beauty of Reflexil when used by by reverse engineers. It also uses intellisense during code editing, much like Visual Studio.
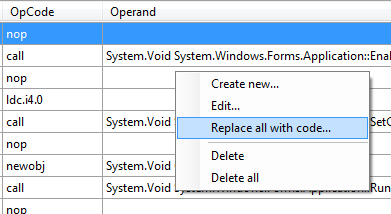
The Replace all with code option converts an entire opcode instruction into C# or VB.net, like Visual Studio.
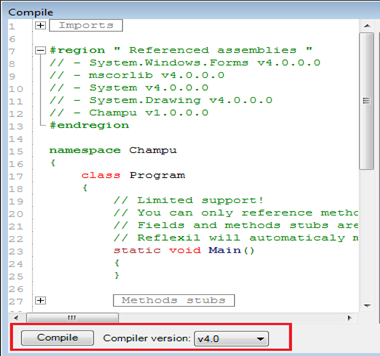
As noticed in the above image, we can update or insert code, as well as re-compile it by choosing a specific compiler version.
-
PE entry Verifier: Reflexil uses the PE file verification utility in order to confirm the assembly development platform origin. That's because every assembly executed under CLR has a PE file entry.
-
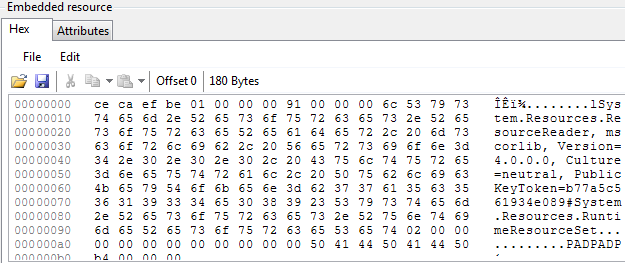
Resource Editing: Reflexil is capable of modifying or updating linked resources, such as control, images, languages, by mounting their code in hexidecimal. We can modify any resource just by stipulating the corresponding byte sequences.
-
Method attributes editor: Reflexil can easily modify any existing assembly method's signatures, scope and parameters entries.
-
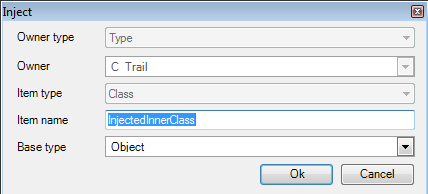
Rename, delete or inject entities: By using code injection tactics, it's possible to insert, rename or delete new specifications, such as class, methods, properties, and fields.
-
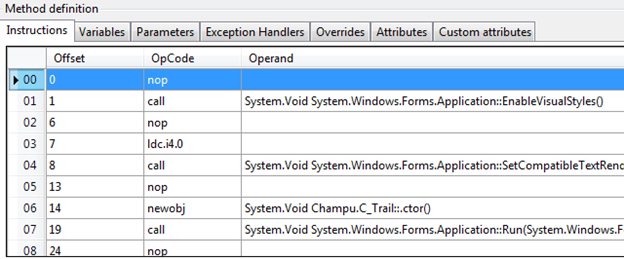
IL instruction editor: Reflexil eludes the auxiliary dependencies over ILDASM, in order to manipulate related MSIL code of an assembly. We can update any MSIL opcode instruction with great ease, just by decompiling the entire IL code.
-
Strong Name Remover: Assemblies are typically protected by strong names, so that no one can misuse them. Reflexil is capable of removing the sign assembly restrictions, just by removing their strong name. It can also remove the supporting reference assemblies.
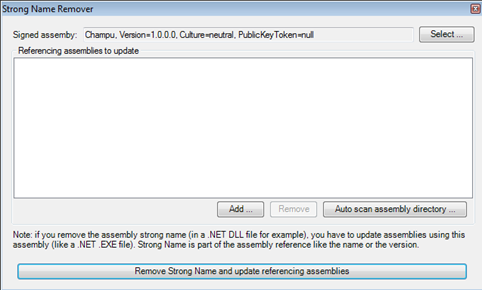
- Assembly source code deciphering: An ssembly's source code can be protected by implementing obfuscation tactics in order to obstruct code dissembly. That's done by inserting some bizarre instructions. It's possible to de-obfuscate the source code of an assembly with Reflexil.
The Victim
The tools that are used to dissemble or patch the code, such as CFF Explorer, Reflector, and Reflexil can be used both offensively and defensively. It depends on a user's attitude, how they use the features as for their needs. Some unscrupulous exploits these tools have to execute reverse engineering, and some use them in order to audit vulnerabilities in existing code.
The following code is manipulated with Reflexil using both defensive and offensive reverse engineering. Analogously, Reflexil is a buggy program. Unfortunately, we don't have the source code of the program, so that we could fix it. So use Reflexil to handle inherent issues.
Let's consider the program and analyze its output. We'll identify couple of glitches, both in the functionality and the user interface. This program is substandard and doesn't fulfill expectations.
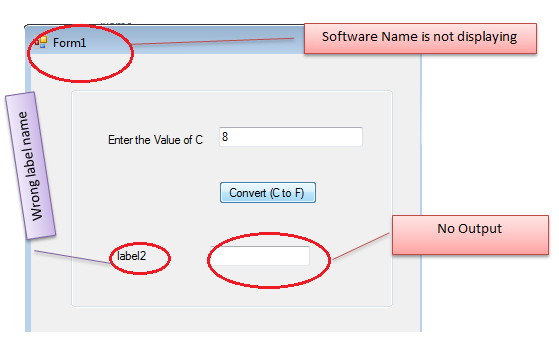
We've provided only the executable of the malfunctioned software, and we have to fix the following problems using Reflexil. In this scenario, Reflector isn't sufficent, because we have to change and patch byte code for proper functionality. Reflector is only useful for detecting errors by dissembling source code.
Reversing Tutorial (Patching the Binary)
This is an exhaustive task which requires much opcode analysis. Make sure that the Reflexil plugin is correctly configured, and open the Reflector. Open the exe file. Right click the reflexilTut namespace after choosing it from the left pane, and select the Go To Entry Point option.
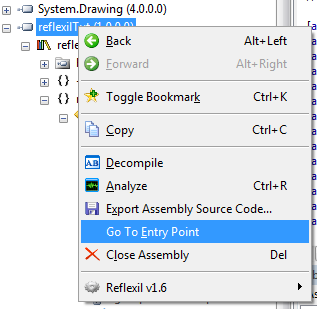
Finally, open Reflexil from the Tool menu. Now, you're going to see many more features in Reflector. Our ,ain areas of interest in the assembly are below.
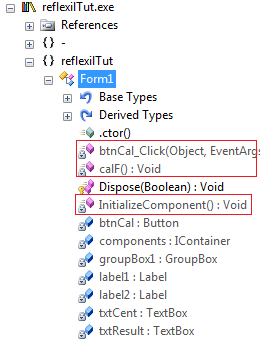
Sadly, this is a buggy program. So, after scrutinizing the software, we've identified the following bugs that need to be patched with Reflexil.
Blank Output Bug Patching
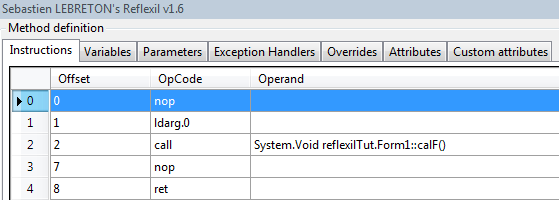
There's no output displayed in the output box after entering the value of a centigrade. We can see that the calF() method is performing all of the calculation. The point of checking is to confirm the calling of this method in the Button Click event. Decompile the button control code in Reflector. Strangely, there's no calF() entry.
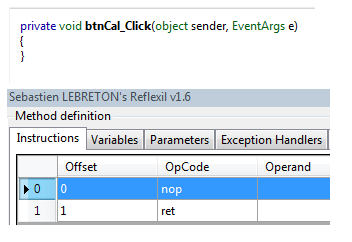
Right click the first instruction value by selecting the Reflexil editor, and choose the Create new.. option. We have to enter the CalF() method manually. Select the ildarg.0 opcode from the OpCode dropdown box, and click on Insert after selection.
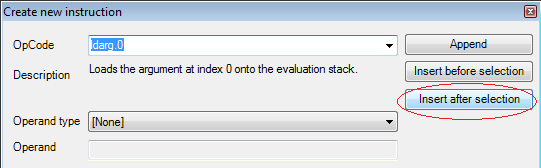
Click the Create New option and make an entry for the calF() method reference.
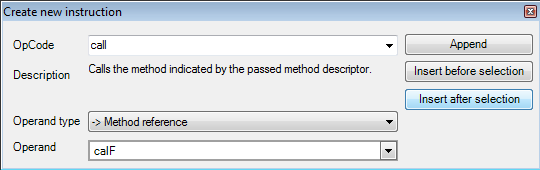
Finally, create an entry for nop (no operation.)
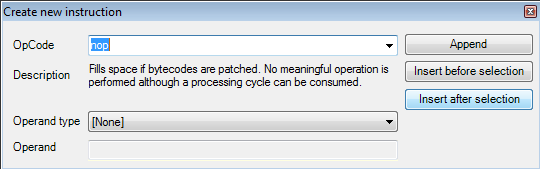
After making those changes, we can see the new calF() method instruction in Reflexil.
Save the changes and notice that this time, the calculated F value is displaying in the output box.
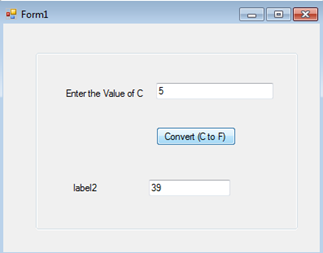
Wrong Label Name Fixing
This software also displays label2 before the output textbox, which makes no sense. The developer would forgot to change the value. Select the InitilaizeComponent() method, the repository of the user controls. Find the relevant instruction, which requires some analysis.
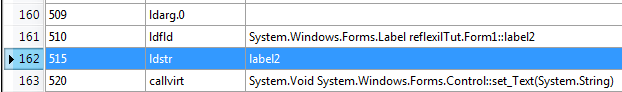
We have to change the instruction's 515 ldstr value. Edit the value by right clicking the instruction and enter a label name in the operand section.
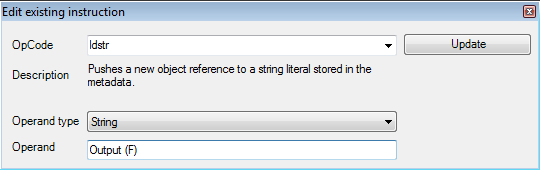
The change replicates in the user interface, after saving the change.
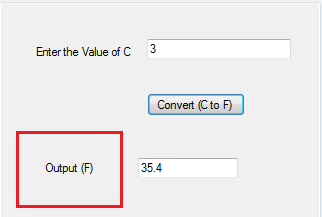
Software Name Fixing
In another strange error, the program shows Form1 as its name. That's not the protocol, it should be a meaningful name. Again, go to InitializeComponent() method in Reflector by expanding Form1. Notice the ldstr instruction, which shows Form1 as its operand value.
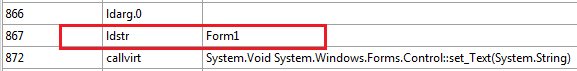
Select the instruction to edit its value. Change the string operand type to "Cent to F" and update.
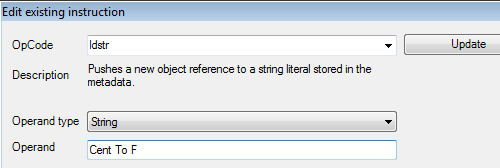
After saving, you can see the change.

Logical Error Fixing
All user interface glitches have been fixed. But the program is still has bugs. By examining the output, the program doesn't produce the correct output. It's not converting Centigrade to Fahrenheit properly. After decompilng the executable, we can see the calculation mistake in the code. 30 should be 32.
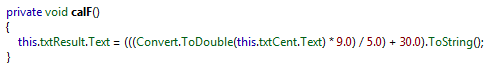
To replace the value, select the instruction, right click and choose Edit.
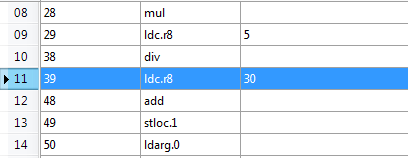
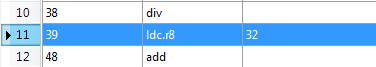
Change the Operand value to 32 and click on Update to save it permanently. You can see the reflected changes.
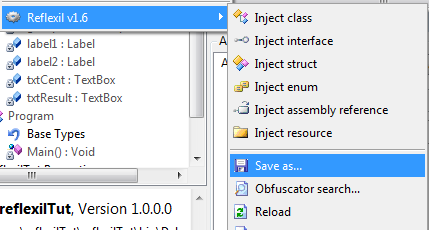
Finally, we've fixed all the detected glitches with Reflexil. It's time to save the modifications, so that we can create an error free version. Select the executable in Reflector's left pane, choose Reflexil and click on Save as. It'll produce an updated .exe file.
Testing the Patched Program
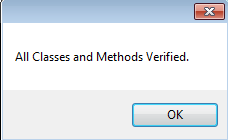
We've patched all the bugs changing the code. The final task is to confirm whether we've done it correctly. We've made changes in the opcode, so it's possible it doesn't comply with .NET framework standards. The simplest way to validate the changes is to verify the executable. If everything is correct, it will show this message.
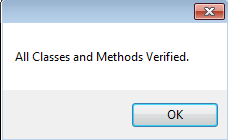
Congratulations! We've done it. Now, see your modified code, which is working properly and error-free. Just compare the following as seen below.
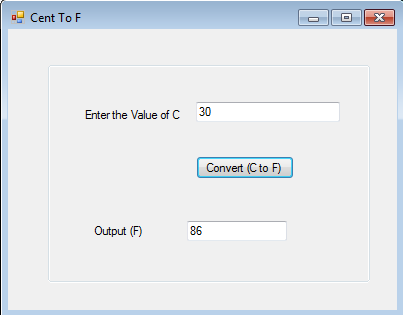
Final Note
This paper intended to showcase the bug fixing process for existing software, which is an issue these days. It's great to use Reflexil, a Reflector plug-in.
It shows the Reflexil's reverse engineering features and functionality for .NET framework. We understand how to modify .NET binary code by with Reflexil for reverse engineering .NET programs. We can't edit source code or MSIL code with Reflector for now. We can defeat that limitation by using Reflexil.
The paper describes the beauty of Reflexil. It can be used to edit corresponding byte code or source code, without having the actual source code. In the next article, we'll demonstrate code Injection with Reflexil.





