The importance of knowing the OWASP Top Ten
A security research team recently conducted a survey of 3,100 cybersecurity professionals around the world, and one of the questions they asked was, “How many web applications does your organization use today?”
The answers were very intriguing.
FREE role-guided training plans

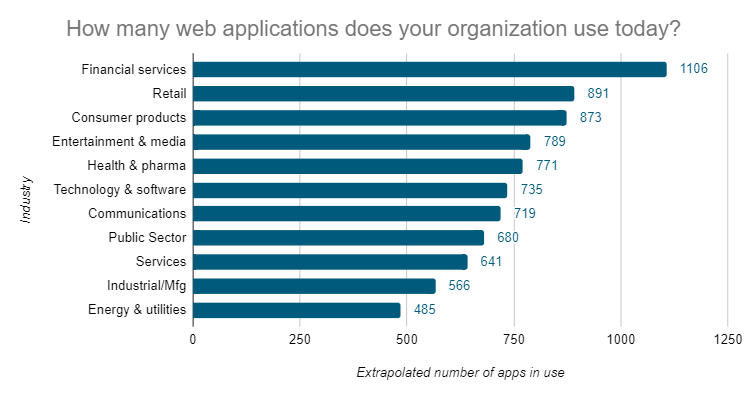
On average, companies use 765 different web applications to run their business. That’s a lot of web applications! Unfortunately, every one of them may face a potential attack — and 30-45% of those web applications are critical to business success, according to respondents.
That’s why it’s important to know the security risks associated with web applications and the mitigation steps you can take to keep them safe.
Importance of the OWASP Top Ten

About every three years, the Open Web Application Security Project (OWASP) publishes a list of the top web application security risks, known as the OWASP Top Ten. It represents a broad consensus of the most critical security risks to web applications, selected and prioritized according to the prevalence and severity of each risk.
The most recent version was published in 2017 (previous versions were published in 2004, 2007, 2010, and 2013). The current top web application security risks are:
1. Injection
Injection flaws, such as SQL, NoSQL, OS and LDAP injection, occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization.
2. Broken Authentication
Application functions related to authentication and session management are often implemented incorrectly, allowing attackers to compromise passwords, keys or session tokens, or to exploit other implementation flaws to assume users’ identities.
3. Sensitive Data Exposure
Many web applications and APIs do not properly protect sensitive data, such as financial data, healthcare data and other personally identifiable information (PII). Attackers may steal or modify weakly protected data to conduct credit card fraud, identity theft or other crimes.
4. XML External Entities (XXE)
Many older or poorly configured XML processors evaluate external entity references within XML documents. External entities can be used to disclose internal files using the file URI handler, internal file shares, internal port scanning, remote code execution and denial-of-service attacks.
5. Broken Access Control
Restrictions on what authenticated users are allowed to do are often not properly enforced. Attackers can exploit these flaws to access unauthorized functionality or data, such as access other users' accounts, view sensitive files, modify other users’ data, change access rights and more.
6. Security Misconfiguration
Security misconfiguration is the most commonly seen issue in the OWASP Top Ten. This is often a result of insecure default configurations, incomplete or ad hoc configurations, open cloud storage, misconfigured HTTP headers and verbose error messages containing sensitive information.
7. Cross Site Scripting (XSS)
XSS flaws occur when an application includes untrusted data in a new web page without proper validation or escaping, or updates an existing web page with user-supplied data using a browser API that can create HTML or JavaScript.
8. Insecure Deserialization
Insecure deserialization often leads to remote code execution. Even so, they can be used to perform attacks, including replay attacks, injection attacks and privilege escalation attacks.
9. Using Components with Known Vulnerabilities
Components, such as libraries, frameworks and other software modules, run with the same privileges as the application. If a vulnerable component is exploited, such an attack can facilitate serious data loss or server takeover.
10. Insufficient Logging and Monitoring
Insufficient logging and monitoring, coupled with missing or ineffective integration with incident response, allows attackers to further attack systems, maintain persistence, pivot to more systems — and tamper, extract or destroy data.
What are the top risks for your organization?
The OWASP list may not be the same as your organization-specific list. For example, insufficient logging and monitoring might be the biggest security risk your organization faces. It’s always important to consider your own “top 10” list, but the OWASP list provides a great foundation.
Determining your own top 10 list can be a fairly involved process, but a good place to start is with Dynamic Application Security Testing (DAST) and Static Application Security Testing (SAST). Many DAST and SAST providers will create a rank order list of the vulnerabilities found in your web applications. You can take these lists and overlay them with the criticality levels of how they would impact your business. This can provide a great foundation for your own specific “top 10” list.
Mitigating web application security risks
Attackers will come after your web applications whether you understand the risks or not. If you have a good understanding of the risks, you can provide better security mechanisms and coding practices to stop these attacks from getting out of control.
In 2019, the average cost of a data breach was $3.92 million, and the average time to identify and contain a breach was 279 days. Don’t be the next victim of one of these attacks! Know the risks, mitigate the risks and provide sound security for your web applications. After all, they are critical to the mission of your business.
For more information about common web application risks, check out my Infosec Skills learning path, where I dive into detail on each of the security risks and provide real-world examples, videos and demos on how to mitigate each of them.



