What is behind that QR code?
With the huge popularity in mobile devices like the smartphone and tablets, two dimensional barcodes, or the so-called QR codes are beloved by marketers. QR codes or Quick Response codes were designed for automotive industry in Japan. Now, QR codes have become popular outside the industry due to greater reliability and greater storage space.
Originally designed for industrial application, the QR code has gained popularity in advertising industry.
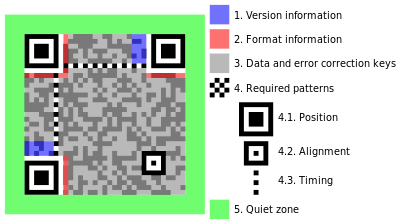
Now lets see how they operate on mobile platforms.
QR codes can be used in iOS devices like iPhone/iPad/iPod and Google's Android operating system, as well as the 3rd party applications like the 'Google Goggles'.
The browsers in these devices support URI redirection, allowing the metadata from the QR code to the existing applications on the device.
Fig. QR code

It is believed that by the use of this advertising technique, marketers can use the behavior of scanning to get consumers to buy, causing it to have a better impact on the business.
But this huge popularity in the marketing and business world invites some nasty and gruesome evil. Malicious hackers. These attackers depend on human curiosity and the innate obfuscation of the QR codes to craft an attack. If people see a random code that is not connected to anything, maybe just a sticker on the wall, they are going to scan it just because they want to know.
The biggest risk is that people cannot control their curiosity and hence they face severe consequences.
This is what a pro-American hacker, Jester, was banking on when he decided to change his Twitter avatar to a QR code to craft an attack.
In his blog, he said that anyone who scanned the QR code on his twitter page was redirected to a jolly little greeting via their default web browser on their mobile device on some free web hosting.
The greeting on the page featured the word 'Boo!' directly below it.
He claimed that he has exploited the open source Webkit built into the device's default browser. This is the same vulnerability which was exploited in "Mobile Rat, turning android mobile into ultimate spy tool" as was demonstrated at the RSA conference.
This curiosity pwned the cat thing went on for 5 days without being noticed. During these 5 days, the QR code was scanned nearly over 1200 times and over 500 devices reverse shelled back to the server on the listening mode.
According to Tom Teller, a security evangelist at Checkpoint said, "It is a drive by download attack, where a user scans a bar code and is redirected to an unknown website. Once the website is visited, the modified exploits will affect the system software and additional malware will get deployed such as keyloggers."
If you think this is the end, you are wrong. Attackers have gone ahead with exploiting vulnerabilities on mobile platform by misusing the various protocols and invoking service set commands on the mobile device. This art of attack is called 'Telpic attack'.
Telpic attack uses similar technique of using QR code as an attack vector. As described in Tech Experiments, "It is a malicious way of tricking an android user into reading a QR code through mobile camera redirecting it to malicious URL." This technique is not just limited to malicious URLs but also executing USSD or the 'Unstructured Supplementary Service Data', which is a vendor-specific command.
There are tons of service list commands starting from displaying the IMEI number to executing a factory reset command. Google it and you will find plenty of service list commands for various platforms and various models.
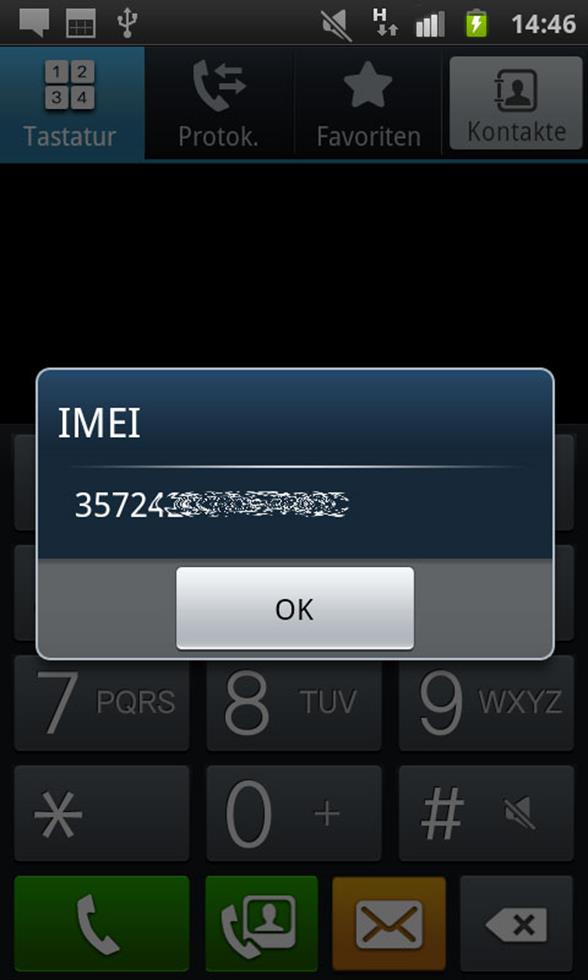
These service list commands are executed by exploiting the vulnerability of the 'tel' protocol available on mobile platforms. You must have seen various mobile websites offering call button option, and when you click on one of those, you are redirected to the dialer of your phone. Here is where the tel protocol is used to call the number from the mobile phone's dialer.
If an attacker generates a QR code embedding this protocol with a factory reset service command, think what havoc it may cause! As soon as the victim scans the QR code, the tel protocol will be invoked, followed by the service command to reset the mobile phone, and thus your entire settings and data from your device will be wiped in a matter of seconds.
These kinds of malicious codes can spread though scanning a QR code, a catchy URL, a Near field communication (NFC) sharing, etc. When tested on Samsung Galaxy's android platform 2.2 (Froyo), I was able to execute the service set command to display IMEI just by scanning the QR code.While on Sony Xperia, with android 4.0.4 (ICS), the service command did not get executed. While on an iPhone, the dialer didn't seem to execute the command automatically. The user has to click the send button before making any USSD requests. There are plenty of devices that are vulnerable, you just need to find one. Some mobile phones have received a patch to fix this bug. The most threatening USSD code is the factory reset code.
The next time you see a QR code in the wild, think twice before scanning. Do not let your curiosity cloud your judgment.
What is the antidote ?
1. First of all you need to verify if you are susceptible to the vulnerability. Open the following link on your mobile's default browser:
http://mobtest.indianhans.org
If you see your IMEI number, go to step number 2.
2. Install a dialer other than the default one, thus stopping the auto execution of any malicious USSD code. After installing the new dialer follow step 1 again to ensure that the new installed dialer is safe to use.

FREE role-guided training plans
References:





