User Behavior Modeling with Mobile Device Sensors
Introduction
The rapid diffusion of mobile technology and the convergence of numerous services that use the paradigms, including social networking, cloud computing and payment, are urging IT and security industries to develop new solutions for the user authentication.
Passcodes, PINs and thumbprints are a few samples of mechanisms that could be adopted to protect mobile devices. Security experts are aware that human behavior represents the weakest link in the security chain. For this reason, one of their principal goals is to improve the user's experience with effective and easy to use security measures. The above methods for example are effective, but users are induced into misbehavior by laziness and carelessness.

What should you learn next?
Mobile devices are becoming an essential component in our daily life. They manage a huge quantity of information that concurs to the definition of our digital identity. Mobile devices are used to maintain relationships on a social network, to complete payments as part of a two-factor authentication scheme for web services, and to store sensitive user data.
Traditional authentication methods are perceived by mobile users as a waste of time. The majority of them do not use authentication on their mobile phones. The problem is that users are, in the majority of cases, totally unaware of principal cyber threats and ignore the importance of authentication processes.
Groups of research and mobile device vendors are trying to improve users' experience related the authentication processes by introducing user behavior and biometric analysis.
The research industry is trying to develop implicit authentication mechanisms that rely on user behavior, and is accomplished by building so-called user profiles from various sensor data.
The User Behavior Modelling approach with mobile device sensors
To overcome the users' wrong habits and improve their experience while maintaining a significant level of security, a group of researchers at the Glasgow Caledonian University (Hilmi Gunes Kayacık, Mike Just, Lynne Baillie, David Aspinall and Nicholas Micallef) has developed a sensor-based authentication method that could simplify the verification of a phone's user identity.
The proposed approach is based on the definition of a user profile through the data collected by the numerous sensors that are present in the mobile phone.
If the user behavior observed by the device sensors appears consistent with his profile, the device will have high comfort, while in the presence of some discrepancies a new authentication action is required and alternative measures will be triggered, such as requiring a passcode.
It is clear that this kind of approach is more comfortable for the user due to the reduction of the occurrences of explicit authentication. The approach encourages more individuals to adopt this kind of authentication mechanisms for their devices.
"We propose a lightweight, and temporally and spatially aware user behaviour modelling technique for sensor-based authentication. Operating in the background, our data driven technique compares current behaviour with a user profile. If the behaviour deviates sufficiently from the established norm, actions such as explicit authentication can be triggered. To support a quick and lightweight deployment, our solution automatically switches from training mode to deployment mode when the user's behaviour is sufficiently learned. Furthermore, it allows the device to automatically determine a suitable detection threshold," reports the abstract titled "Data Driven Authentication: On the Effectiveness of User Behaviour Modelling with Mobile Device Sensors".
User Behaviour Modelling could prevent unauthorized access to a user's phone, because the technique is able to discriminate the legitimate owner of the device.
The technique developed by the researchers is very effective. It is very interesting the way they create the user's profile based on habits, for example, examining the nearest cellphone towers to create contextual "anchors" used to define user behavior throughout the day. This means that the technique uses location data related to the user's movements during an ordinary day.
The researchers based their analysis on the concept of "anchor", a sort of snapshot used by the experts to gather information on the user habit, including mobile apps used, WI-Fi networks accessed, and connections with other devices through Bluetooth.
The "anchor" is also used to collect information related to the environment surrounding the mobile device, for example the noise and light levels of the areas visited by the user.
All the data collected by the researchers allowed them to profile users. The experts defined an algorithm to match real time behavior with normal behavioral patterns.
The results of the experiments conducted on the algorithm in a few weeks are surprising. The model allowed them to discover if a stranger had stolen a user's smartphone in two minutes with 99% accuracy.
The researchers also made a series of tests in a worst case scenario. For example, they simulated the theft of the mobile made by a roommate who was even given a list of the apps the owner generally used.
In this case, the software designed by the team of researchers discovered the theft in about ten minutes with 53% accuracy. The experts also explained that the algorithm presents a low rate of false positives.
The User Behavior Modelling technique
The researchers designed their software to operate in training mode until it will be able to track a user's profile. This activity is transparent for the end-user and will be completed once the application has defined a user's profile through the analysis of his routine.
The team of experts highlighted that, different from previous works, the "learning mode" implemented in the solution is incremental and collects data until it is able to track a user's profile.
"We however argue that training duration must be set automatically on a per user basis since, as our evaluation shows, there is no one-size-fits-all," states the paper.
Other similar works incorporated user feedback for refinement of tracked profiles, and they do not consider the duration of training. The first approach is not considerable for the deployment of the technology on a large scale, because it is reasonable to expect that a user will not expend any effort in 'teaching' the device by providing feedback, "but they will quickly grow tired if frequent and labor-intensive feedback is required".
The profiling technique elaborated by the experts is based on the definition of temporal and spatial models that are built starting from the data in a lightweight and non-parametric way.
Once the algorithm has qualified a profile, the training is completed and the application switches from the training mode to a deployment mode. At this point, every time the parameters defined by the model are below the threshold, which was calculated considering user settings, the software launches an authentication challenge.
The dataset used by the researchers for the tests is composed of data collected by seven staff and students of the Glasgow Caledonian University. The data collected in 2013 from Android devices includes various kinds of information like sensor data from WI-Fi networks, cell towers data, application usage, surrounding environment's parameters (light and noise levels) and device system stats. Data composing the dataset was collected in a period of variable duration, from 2 weeks to 14 weeks for different users. To improve the efficiency of the analysis, the experts included in the dataset a detailed diary for each profile, which allows them to conduct further investigation on anomalies.
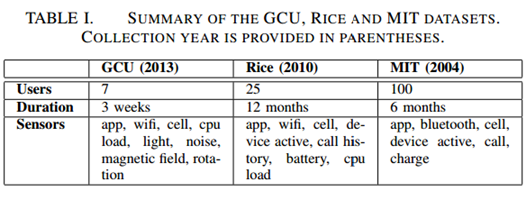
Figure 1 - Summary of the GCU, Rice and MIT datasets used in the tests
The researchers examined different attack scenarios based on the attacker's level of access to a user's frequent locations and his knowledge about the victim's habits. The experts defined two adversarial levels, the uninformed adversary, who knows very little about the victim and his behavior, and an informed adversary that has a deep knowledge of a target user and his behavior. Additionally, the researchers defined an outsider to be a person who steals the mobile and runs away, while an insider has access to a location that the user frequently visits and attempts to use the mobile device at the same places as the legitimate users.
The results are very interesting. The informed attacks produce higher comfort levels compared to uninformed attacks. Anyway, they are not able to bypass the detection mechanism developed by the researchers.
"The results indicate that uninformed attacks, both outsider and insider, are detected quicker than the informed attacks. Additionally during all four attacks, the comfort level dropped substantially below the owner's average. With the exception of informed insider attacks, arguably the most sophisticated of the four, attacks were detected with over 95% detection rate. Even when the attacker attempted evasion, the device locked in under 15 minutes," states the paper describing in detail the results of the attack.
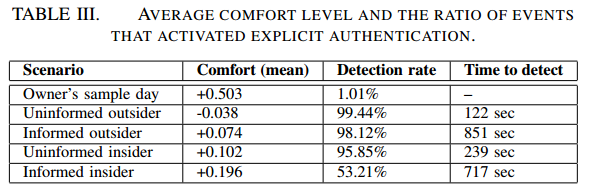
Figure 2 - Test Results
The researchers announced that they will continue the investigations on the use of behaviour modelling, in particular analyzing different supervised learning techniques for profiling.
Is the User Behavior Modelling an efficient theft deterrent?
Despite that results of tests conducted by the experts demonstrate that the technique could be very effective against the theft of mobile devices, there are serious considerations to make about the users' privacy. This kind of algorithms elaborates an impressive amount of data to profile users and to define a pattern for its analysis. Anyway, it is easy to predict that privacy advocates could criticize the technique due to possible use for surveillance purposes.
The data-tracking and user profiling through the definition of contextual anchors is very invasive. For this reason, it is crucial to understand how to implement the technique in a real commercial scenario. Principal providers of mobile OS and hardware vendors like Google and Apple are very interested in implementation of the technique in their operating systems.
The researchers explained that their "User Behavior Modelling" algorithm could be very effective for payment systems like Apple Pay, and could allow securing a user's daily purchases without constantly typing in secret passcodes.
The future applications of User Behavioral Modelling techniques depend on the capability of coders to implement models without user data ever leaving the device. The work we have analyzed proposed a lightweight, non-parametric modelling approach that can be implemented on modern mobile devices and determine when to stop the learning mode and the threshold for detection, both automatically from the data.
References
http://arxiv.org/abs/1410.7743
http://arxiv.org/ftp/arxiv/papers/1410/1410.7743.pdf





