Understanding Critical Windows Artifacts and Their Relevance During An Investigation: Artifacts
We discussed NTFS timestamps in Part 1 of this series. In this article, we will look at some of the artifacts which can point out a program execution on a Windows system. Mainly we will talk about artifacts such as Prefetch Files, Application Compatibility Cache (shim cache, RecentFileCache, amcache), Jump Lists, Most Recently Used (MRU-Last Visited, RunMRU), UserAssist.
So let's see how what these interesting artifacts are, where are they located and how they can be useful during an investigation.
Learn Digital Forensics
Prefetch Files
Whenever an Application is executed/run, Windows creates a corresponding prefetch files (.pf).Mani purpose of a prefetch file is to decrease the start time of the application. Its format is usually like the name of the executable followed by a hash of the location from where it was run and a .pf extension. Each prefetch file will contain Most important artifact inside a .pf file is what files/directories/dlls used by the application during first 10 seconds of the startup that actually will be used by the system when the application is executed again and will be loaded in memory even before it is asked by underlying application code/dependency. On the drive, the prefetch files are location at C:WindowsPrefetch and on registry it is located at HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSession ManagerMemory ManagementPrefetchParameters. EnablePrefetcher key should be set to following values:
0: Disables Prefetching.
1: Enabled Prefetching on Application Start.
2: Enabled Prefetching for Boot.
3: Enabled Prefetching for Application Startup and Boot.
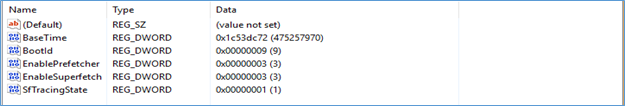
Below we can see the prefetch on the system using WinPrefetchView tool. Here is an example of a Splunk Prefetch file and note created time, modification time and last run time are all same. It also shows the path from where the application was run.
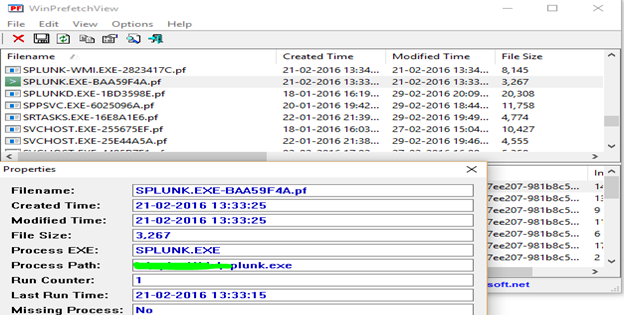
Since the attackers now have become intelligent, they even remove all these prefetch files from the system before leaving the system to remove any trail. However, Prefetch files also exist in memory and can be parsed by a volatility plugin named 'prefetchparser'. This is a very simple plugin and just requires the image name. Syntax is
-
vol.py –f <imagename> prefetchparser
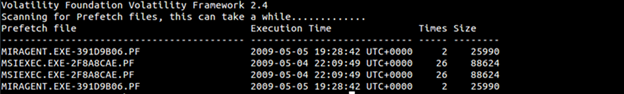
UserAssist Key
This key is used to fill up User Start Menu with the frequently used GUI-based applications. What it does is that it maintains a count of applications under each user's NTUSER.DAT file. It is located in registry at HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExplorerUserAssist and if you are in Win 7 there will be 2 GUID:
- CEBFF5CD-…:Executable File Location
- F4E57C4B-…..: Shortcut File Execution
Values there are ROT-13 encoded, but count value can be parsed using RegRipper with its userassist plugin. Below is a sample output of RegRipper parsing the count of userassist along with the executable location.
Jump Lists
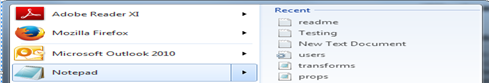
Jump Lists are an addition to Windows 7 and are an indication of Recent User Activity. User activity can be either via keyboard, console or RDP. It will give an indication which files the user has recently opened under the respective application. Below is a snapshot of recent Files which were opened in Notepad. Windows derive these lists from two folders namely
-
AutomaticDestination : Located at C:Users<Username>AppDataRoamingMicrosoftWindowsRecent. Files in this location are named 16 hexadecimal digits which are called as AppID and followed by the extension automaticDestinations-ms. This folder has a Compound File Binary(CFB) which act as a container for DestList stream(which is a collection of MRU/MFU entries with timestamp information, target file name, etc.) and individual SHLLINK streams.
Note: IF you cannot see Automatic Destinations folder in the above-specified path try specifying the full path in explorer or navigate via cmd.
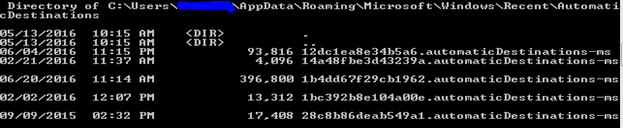
- CustomDestination: C:Users<Username>AppDataRoamingMicrosoftWindowsRecent. The structure is similar to that of Automatic Destinations except the SHLLINK structures are packed sequentially.
Note: IF you cannot see Automatic Destinations folder in the above-specified path try specifying the full path in explorer or navigate via cmd.
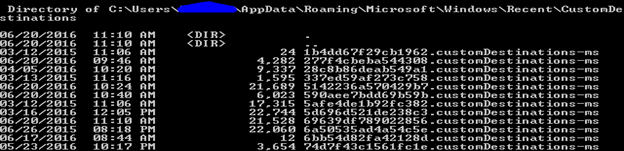
The file structure at both these locations can be parsed by TZWorks 'jmp' tool.
For Windows to create these lists, make sure you have enabled it under Start Menu like below.
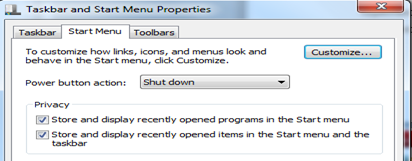
Most Recently Used
-
RunMRU: Any program launched from Start>Run command can also be used to see what programs the user has launched via this route. These entries get logged under HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExplorerRunMRU, and there will be a list of all the programs launched from Run.It will also contain an MRULISt which will show the order of these with the first entry being the most recent. Example, I have launched cmd.exe from Run and then Refresh registry and below we can see cmd exe marked as key name 'f' and MRUList is updated to show the febdca.

-
Last Visited MRU: This key tracks the executable that was used to open files identified by the OpenSaveMRU key. To illustrate this I have created two files on my desktop named TestingLastVisitedMRU1 and opened it from Notepad(File>Open) Below are the changes that can be seen:
- HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExplorerComDlg32OpenSavePidlMRU*

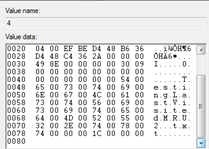
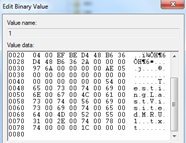
- HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExplorerComDlg32OpenSavePidlMRUtxt

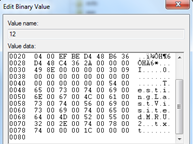
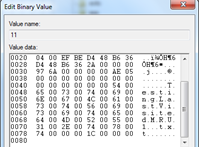
- HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExplorerComDlg32LastVisitedPidlMRU

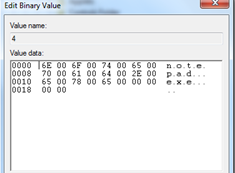
This is not a definitive list of entries that got updated when the file is being created and accessed as there will be several other entries like RecentFolder, Prefetch Files got updated, but it can be seen above as how OpenSaveMRU is related to LastVisitedMRU.
Application Compatibility Cache
This corresponding registry key will check to see if an executable requires shimming (providing compatibility among different versions). AppCompatCache will track an executable file last modification date, file path, and file size. In Windows XP it was also tracking last time executed but with WIN7+, WIN 2008+ it is not able to do so. It is located at HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSession ManagerAppCompatCache. One important point to note for this cache is that entries are realized into the registry only after system shutdown/restart. So it will be not be something we are catching live on system (how to do that in just a bit)
To read this cache, a tool known as shimcacheparser.py is used. Its syntax is
- ShimCacheParser.py –I <REGISTRY_HIVE>. Below is the output for a Win7 system.
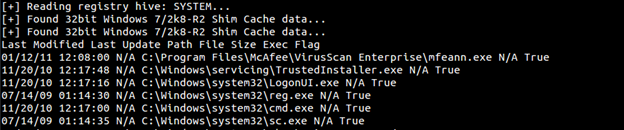
Since from Windows 7+, 2008+; last execution time is not getting noted, we have an execution flag from which gives us a high probability that the system was executed on the system.
Also there we can extract this cache from memory using Volatility's ShimCache plugin.
To catch latest executables executed on system we can use RecentFileCache.bcf which is a temporary registry located at C:WindowsAppCompatProgramsRecentFileCache.bcf. This registry gets overwritten with each ProgramDataUpdater Task, so data in this cache is short lived. This file can be parsed with rcf.pl (Harlen Carvey's) or rfcparse.py (https://github.com/sysforensics/RecentFileCacheParser)
Amcache.hve
Starting from Windows 8+ RecentFileCache.bcf has been replaced with amcache.hve . This new hive will contain Last Modification Time, SHA1 hash and other details.
Learn Digital Forensics
I will cover more details on amcache.hve this in the next article along with some other interesting artifacts.





