Tunnelling SSH Traffic
Overview
Security plays an important role in our internet world. As the number of users on the internet increases, it's necessary to have secure communication between the sender and the receiver. Tunnelling is the method of protecting web traffic from our local machine in order to get privacy. Once traffic is tunnelled, no eavesdropper can peep at the channel to get information. First we will look at SSH and its benefits.
SSH is program and protocol to encrypt data in transit and can be used to secure traffic for file transfer and port redirection. SSH provides authentication and secure transmission over vulnerable channels, like the internet. Imagine you're sitting in an internet cafe and want to check your email. Do you trust the internet connection? If not, this is where SSH tunnelling plays a role.
You need to have an SSH client and SSH server. Then, forward information over the encrypted channel to your server of interest. SSH has a client server architecture, and comes with all Linux distributions, MAC OS X, AIX, Solaris, Open BSD and other UNIX variants. It's a complete replacement for telnet, rlogin, rsh, rcp, ftp, etc. Now companies no longer use telnet or rlogin mechanisms to access network resources remotely.
SSH Components
The SSH protocol consists of the following components:
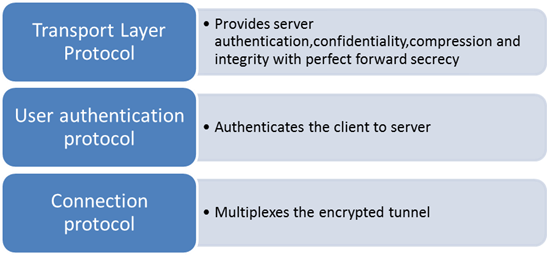
The SSH software package consists of server and client tools. Both of the components need to be installed and configured prior to use. The server is not limited to Microsoft or Apache server. It could also be firewalls, routers and switches.
SSH uses port 22, and helps to control web, application, server and network resources remotely. The use of SSH at both endpoints requires a digital certificate. SSH uses RSA public key cryptography for connection and authentication and DES, 3DES, and AES for encryption. All encryption, integrity, and public key algorithms that are used in SSH are well known and are available on the internet.
Common SSH Uses
Secure shell can be used to provide:
-
Secure command shell
- A secure command shell is used to view and edit files in a directory, or access any specific application. Users who login to the servers via ssh can delete, start, and stop new services, change file permissions and more. While using Wireshark to sniff traffic, it would be completely encrypted. Putty is the best tool to use for SSH sessions. An SSH server needs to started at the server end.
-
Secure file transfer
- Is a subsystem of the SSH protocol. This mechanism is used to securely transfer files, and is now popular in all network devices for transferring files. SFTP encrypts usernames and passwords, as well as the data being sent. It uses the same port 22 to transfer files, eliminating the need to open another port in the firewall to enable the transfer.
- Port forwarding
Port forwarding is also referred to as tunneling. The SSH connection protocol can be used as proxy forwarding for protocols such as HTTP and POP3. It's a serious concern for all network administrators who are controlling users in accessing certain applications. Traffic is tunnelled via SSH, and network engineers are unaware of that traffic happening in the network. That tunnelled traffic violates companies' security policies and is a real threat to an organization.
Administrators should use technologies or mechanisms to control the proxy forwarding functionality so that security policies are upheld. Firewalls can be spoofed using ports and protocols. When we use the internet, all data flows through a firewall or proxy. A network administrator can set policies on those devices to prevent usage. By tunnelling traffic, we can bypass the firewall as well as the proxy, keeping us anonymous in the network. This technique can also bypass national level filters, censhorship, PRISM, and other restrictions that are used to control web traffic. These days, many advanced firewalls and proxy filters work to detect and decrypt SSH tunnelling.
Setting Up an SSH Tunnel
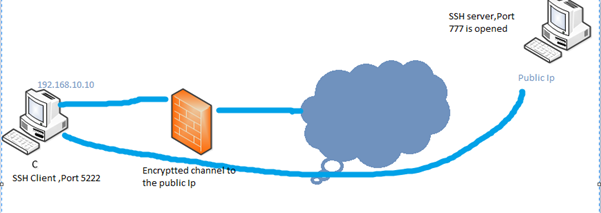
Let's say computer C resides in an organization where the web request traffic is manned by a firewall. To get unlimited access to all websites, we need to setup an SSH server in our home PC, which has a public IP address.
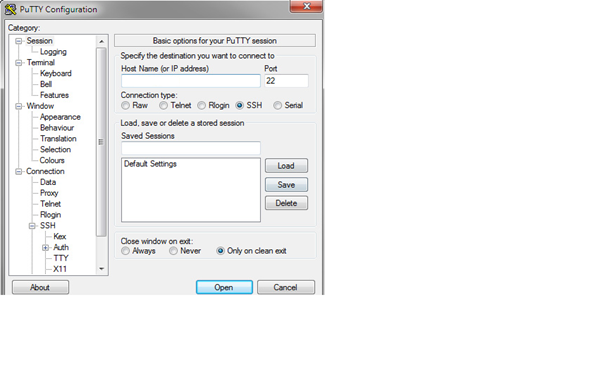
Launch a putty client, and input the following configuration:
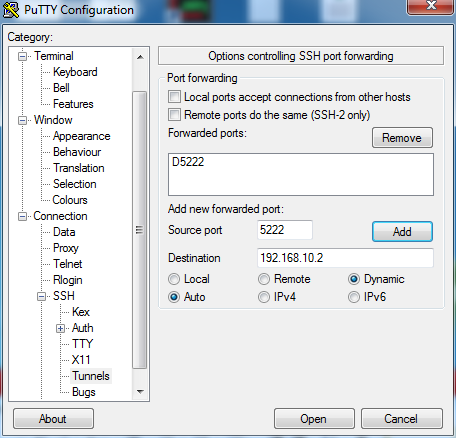
Once the following settings are configured, port 5222 will appear in the forwarded port list. That binds the SOCKS proxy on your loopback address. Once the tunnel is set up, we need to force the traffic to go through the tunnel. In the proxy settings of any web browser, add 127.0.0.1 and port 5222 to the SOCKS host. Make sure you select the latest version of the SOCKS proxy.
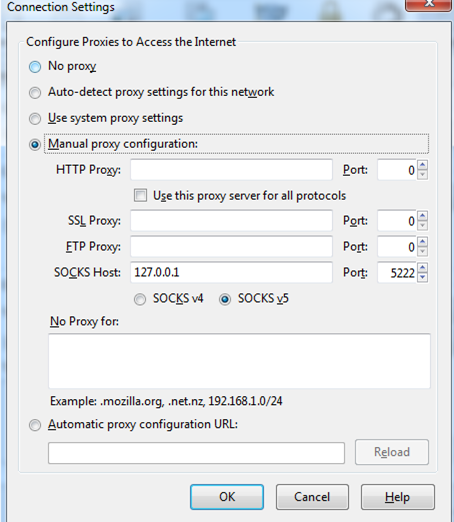
Once you configure the settings above, log in to putty, and SSH the server. Make sure that port 777 is open on the destination IP.
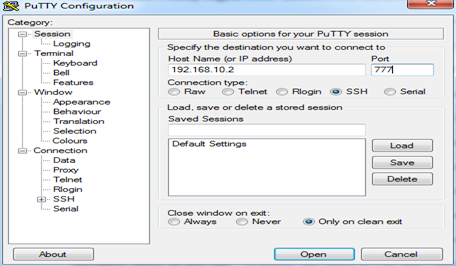

Now you can surf the internet using the SSH tunnel. You can internet traffic, as long as you're logged into the SSH server. If the session is disconnected, then tunnelling is lost.
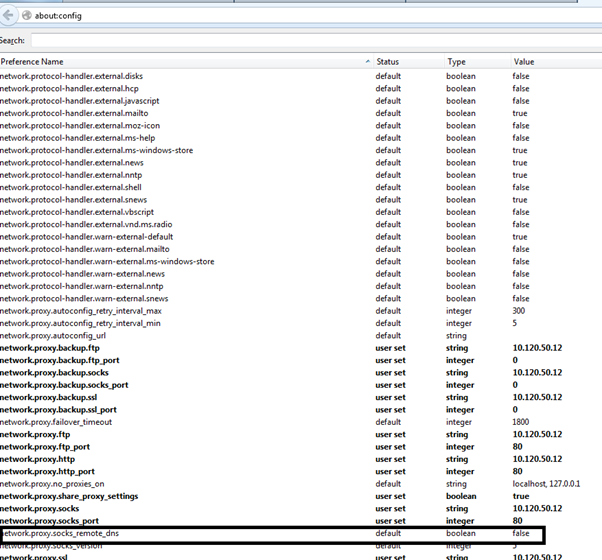
All our traffic will go through the SSH tunnel, but DNS requests will use the local DNS server to resolve queries. The next step is to tunnel the DNS request. The purpose of that is to access websites we might otherwise not able to, or to just anonymize browsing. To do that with Firefox, type about:config in the address bar and look for the "network.proxy.socks_remote_dns" entry. Set it to "true." The option will only take effect if you use the SOCKS proxy, level 5.
There are also plugins available to switch a proxy from one location to another location, such as Foxyproxy or Switch proxy tool. They offer the ability to choose multiple proxy entries and to turn them on and off automatically. The "Hide My Ass" website updates a list of proxies frequently. The site recommends that you use any proxy from the list, for proxy chaining. That way, you can fool the CERT engineers!
Threats addressed by SSH
-
Eavesdropping
-
A sniffer can be used to intercept information transmitted over the wire. That sniffing is done without the knowledge of the client and server. Since SSH encrypts data traffic, it's not vulnerable to such traffic, and cannot be decrypted by an eavesdropper.
-
Man in the Middle Attacks
If the host key exchange between the client and the server is compromised, then a "Man in the Middle" attack fools the server and the client into thinking that they are communicating to a real entity. So, an attacker can intercept all the traffic between the two. SSH protects against such attacks through host authentication, with the help of public and private keys.
-
Recommendations to detect SSH Tunnelling
- Use SIEM solution to monitor and investigate if a user uses more SSH connections than typical for web traffic
- Limit the potential use of SSH traffic, unless a specific request is made
- Use an IDS/IPS device to detect SSH tunnelling
- Use next generation firewalls that can detect SSH tunnelling
- Case to case analysis is required on all websites that a proxy has classified as "uncategorized category"
References
http://www.vandyke.com/solutions/ssh_overview/ssh_overview.pdf

FREE role-guided training plans





