Trend Micro OSINT Challenge
In this article, we are going to solve all three OSINT challenges from Trend Micro CTF.

FREE role-guided training plans
Challenge 1: Today you received an email that seemed to be from an online shopping site that you use - but when you followed the link something definitely did not seem right. It appears that the world's worst phisher must have set up the page - and has targeted you with a phishing attack!
The email text said you needed to visit a link to update the security of your account. However, the link actually leads to the site "ctf.superpopularonlineshop.com.definitelynotaphishingsite.com."
For this challenge, you must find the "Real Person" who is behind this attack - leveraging your Open Source Intelligence (OSINT) skills.
The Flag will be found on one of their social profile pages
Solution: We started from investigating the website ctf.superpopularonlineshop.com.definitelynotaphishingsite.com
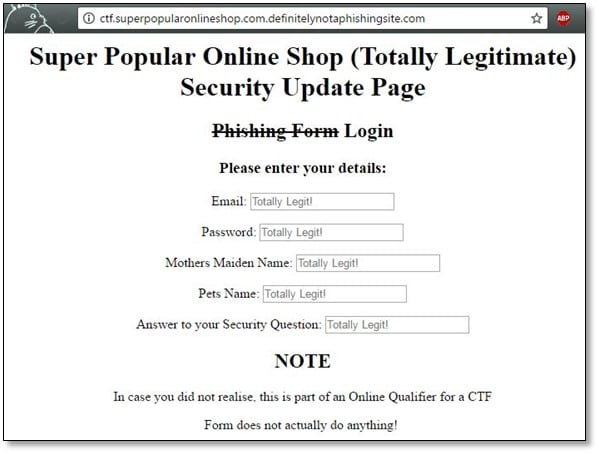
So, the site was an obvious phishing site we copied the domain definitelnotaphishingsite.com and searched it on whois for gathering domain information.
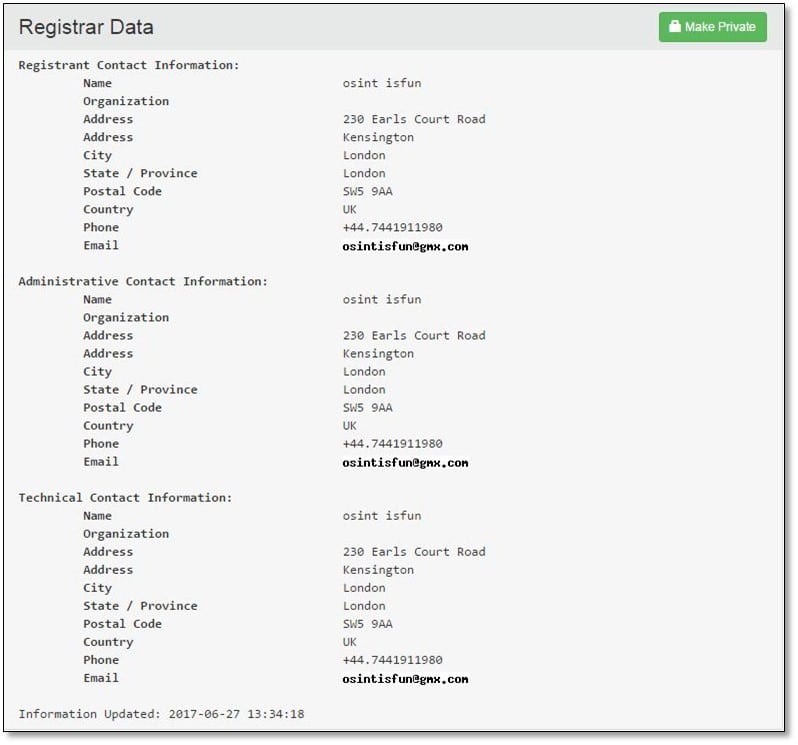
From whois, we got two information Phone and Email details we simply searched the Email osintisfun@gmx.com on Google, and we found a pastebin link on search result which contained the email address. So, we opened the link one more whois detail which contains the same phone and email address but having one more extra information which was another domain name T3M4.com.
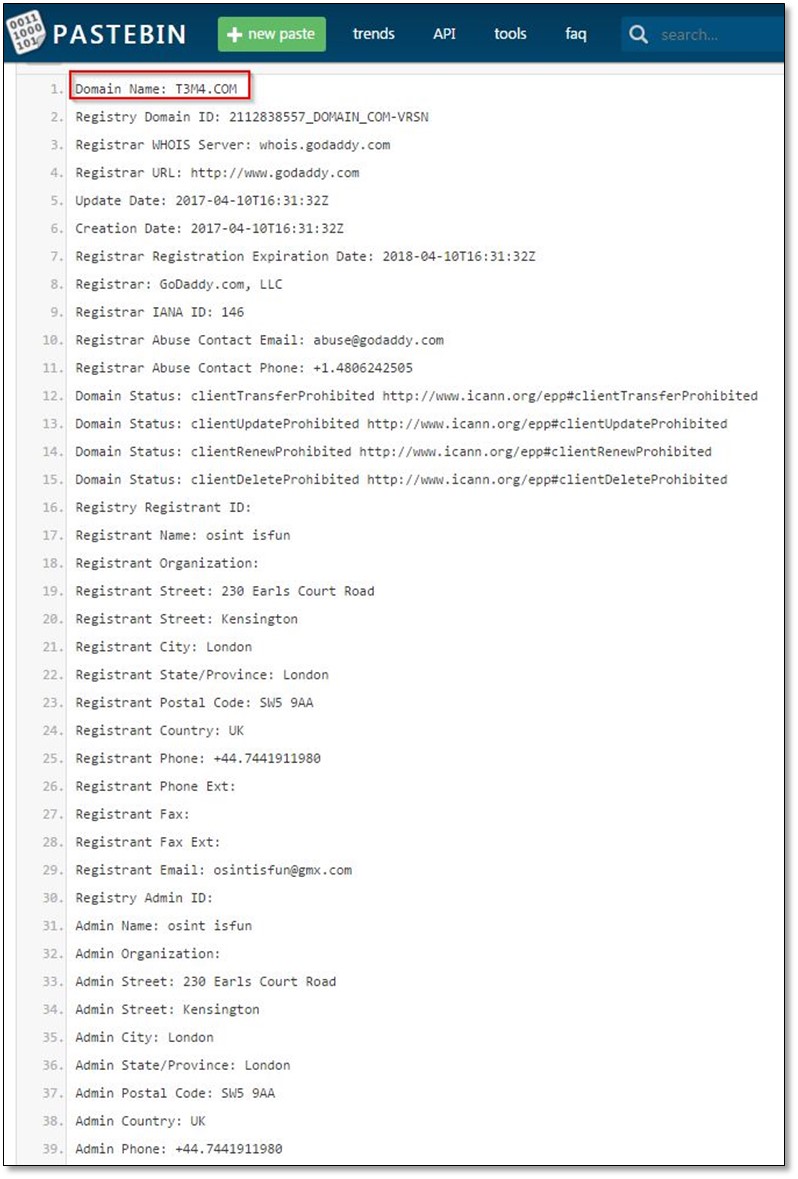
We opened the domain, and it redirected to another site.
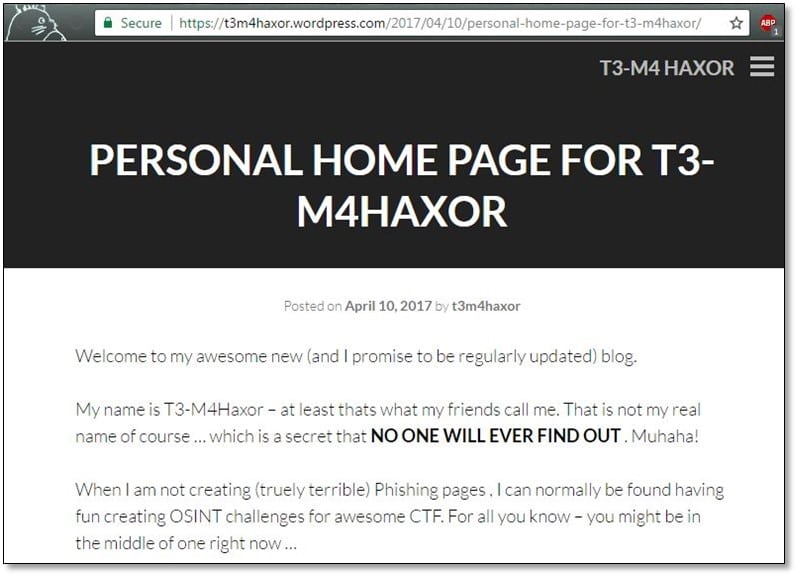
From the WordPress blog, we got the name of the phishing page creator which was T3-M4Haxor. So quickly did google search for this name and we found a twitter profile on search result
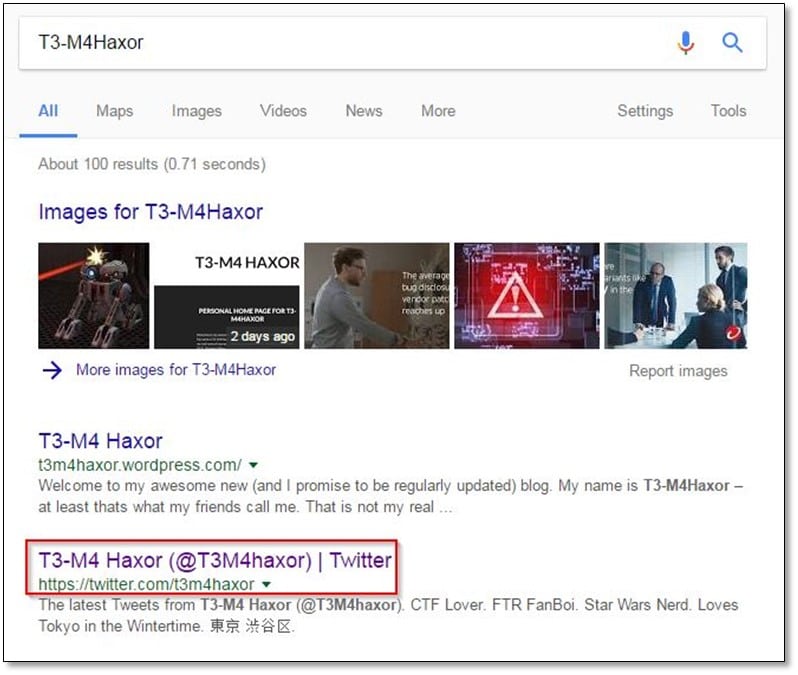
We opened the Twitter profile and did some profiling on it, we checked his all tweets, following, and followers for gathering intel about him.
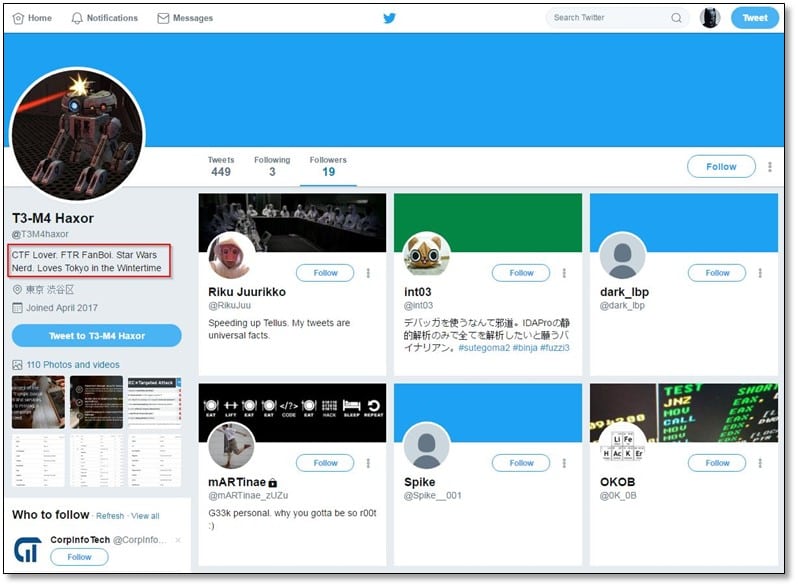
While looking into his followers' profiles, we found one similarity with his follower that both people are Star Wars fan.
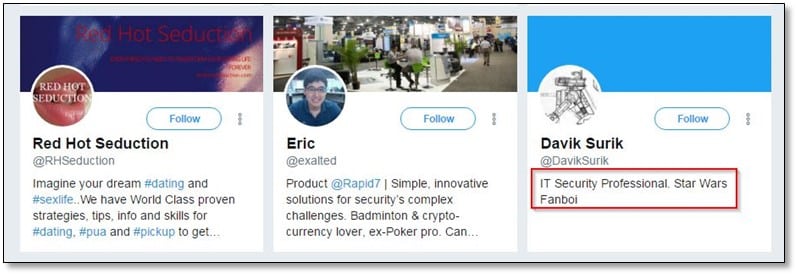
We searched for Davik Surik name on Google and found his LinkedIn profile with interesting details.
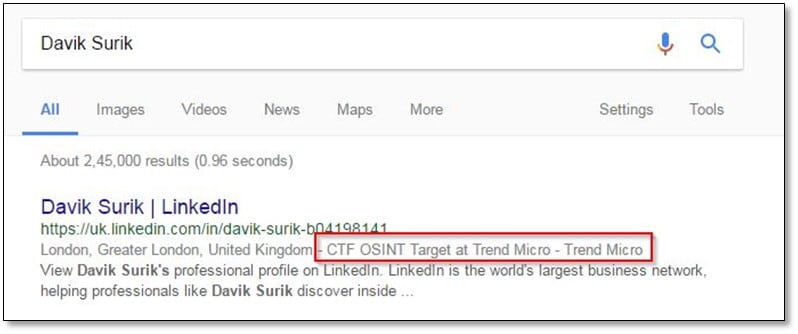
After opening the profile, we found that he was the member of this CTF creator and also, we found the secret flag.
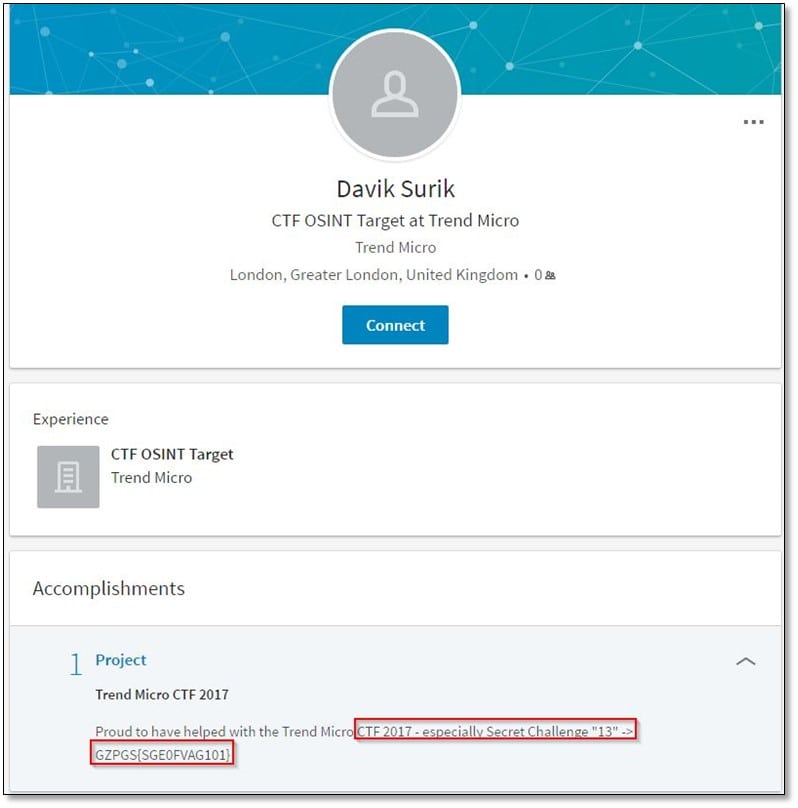
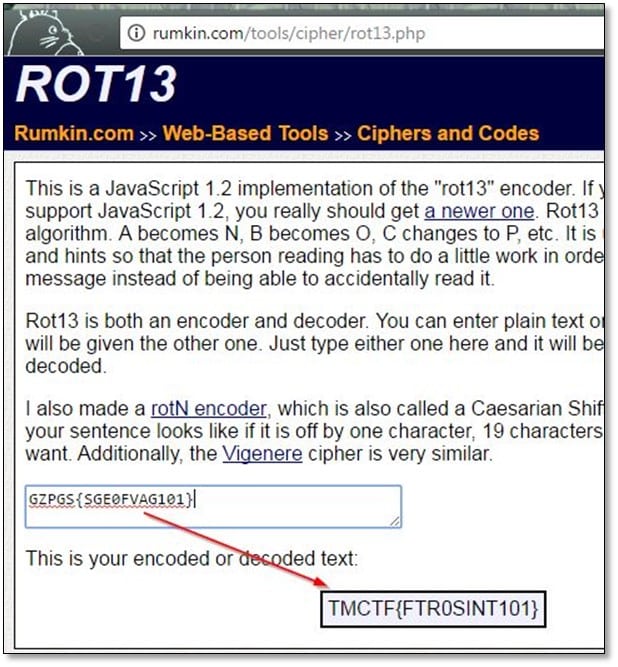
The flag doesn't seem to be in plain-text, and there was a hint for that Secret Challenge "13" the number 13 hints at the ROT 13 cipher and decrypted it by using online cipher decrypter.
Challenge 2: A customer suspects that his email account is being targeted to be hacked. He has asked you to investigate and trace his attacker's real name (flag).
During your talk, he mentioned a suspicious email that he received about a bank transfer from someone he doesn't know. He actually tried to investigate by himself and found out the email was crafted to hide the real sender. He was able to go as far as finding a related Facebook account by adding "tmctf" to the name he found from the email, and that was as far as he got. Unfortunately, he deleted the email after this, thinking it was just a random phishing email. He provided you with pcap logs from his machine to start your investigation.
Download the file (https://s3-ap-northeast-1.amazonaws.com/trendmicro-ctf-2017/Pi1T3ou0CquyBbYosgng/files18.enc)
Decrypt the downloaded file by the following command.
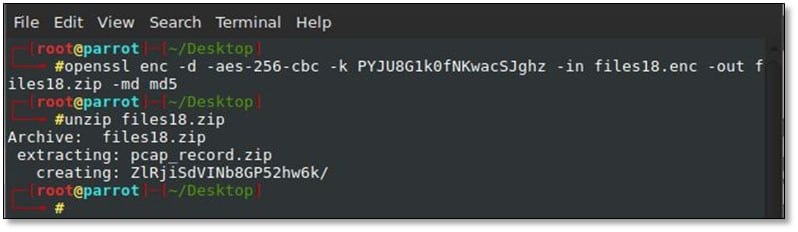
> openssl enc -d -aes-256-cbc -k PYJU8G1k0fNKwacSJghz -in files18.enc -out files18.zip -md md5
> unzip files18.zip
> ZIP password: virus
Solution: We downloaded the file and decrypted the file by using the given openssl command.
Once we have extracted the file, we loaded the pcap file in Wireshark and start investigating the traffic. Since we have to investigate the email, we have added the pop filter in Wireshark.
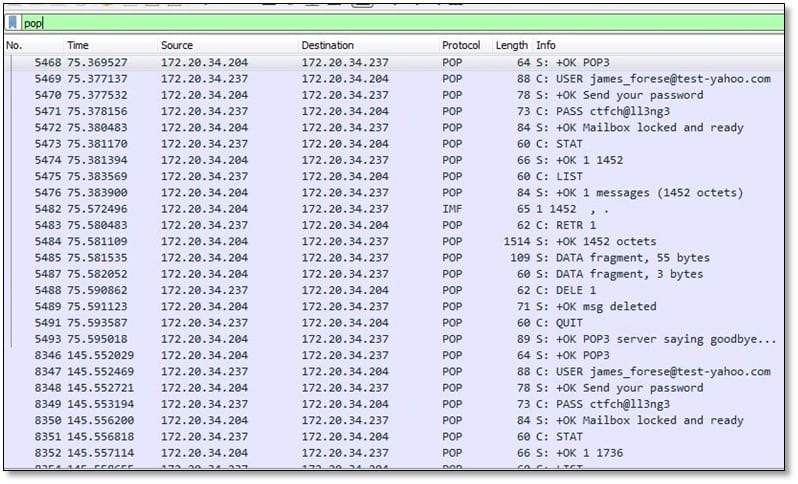
As can be seen above after applying the filter we were able to see lots of interesting stuff in the traffic. So, we selected the first stream and checked the TCP stream by doing right click and Follow TCP stream.
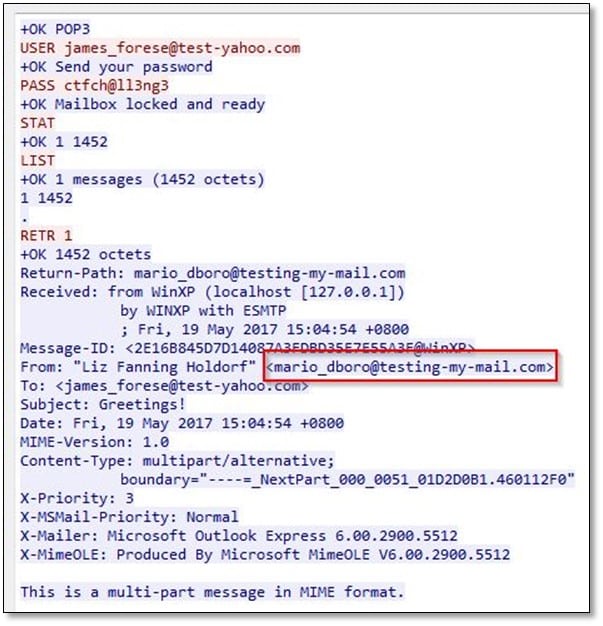
In the TCP stream, we found the From email section, and it was sent from mario_dboro@testing-my-mail.com. Once we found the email ID, we searched for it on Facebook by adding tmctf keyword as suggested in the challenge description and we found the profile, and on the wall post, we found the community page link.
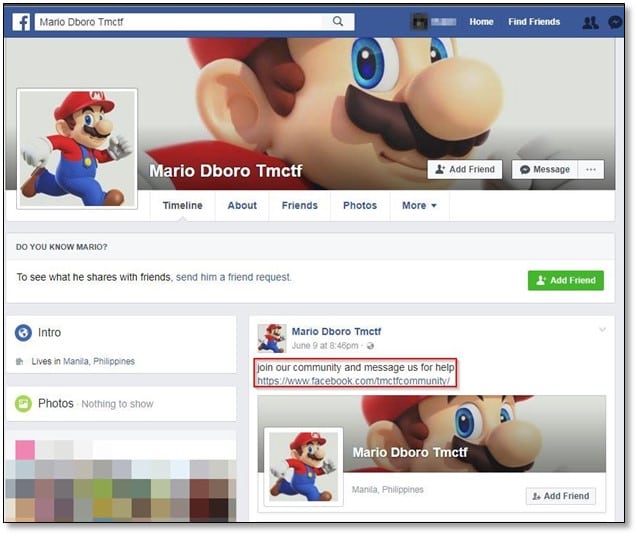
After opening the community page, we messaged them for help, and we received a reply.
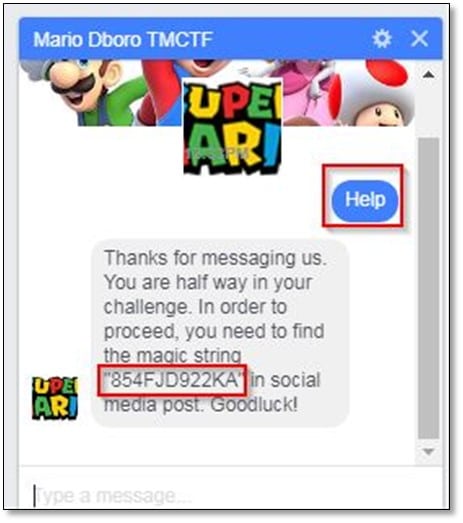
In the reply message, they provided the following "854FJD922KA" alphanumeric string, and we need to find the string on social media post. After searching it on Google, we found the Twitter link.
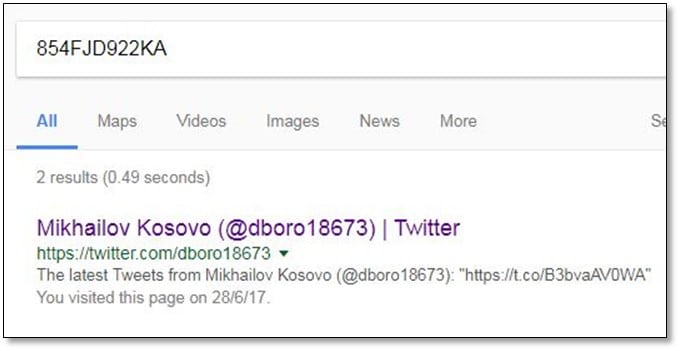
After looking on to the Twitter user's tweets, we found a short URL, and we opened the link.
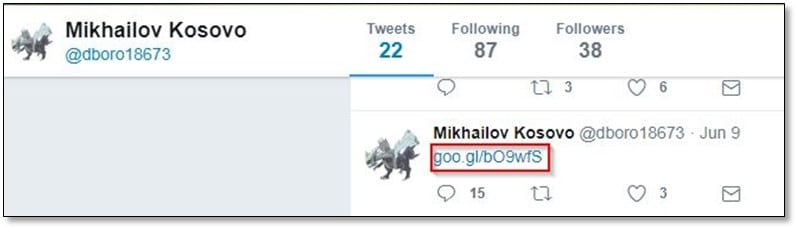
The link redirected to Pastebin post which contained an email address.
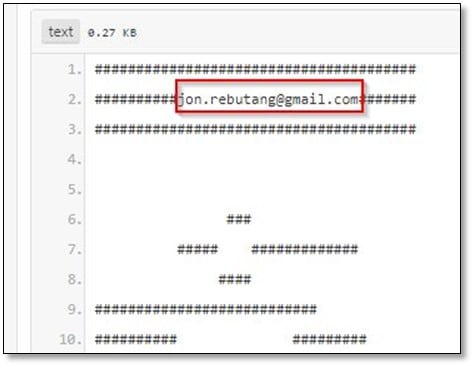
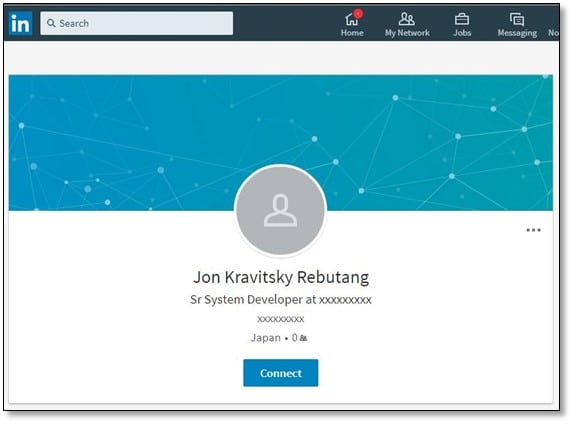
So, we searched for that email in Google, Twitter, Facebook, and LinkedIn but didn't found anything related to that email so when we searched for Jon Rebutang by his name on LinkedIn we got the account.
Challenge 3: Within the ICS environment there has been some odd behavior with one of the network switches. You have asked your Network Administrators to see if they could pull some traffic from their packet capture solution. They dug into the issue and couldn't make sense of what's going on but think that there may be an attacker that has figured out a backdoor into the system based off an SSH connection.
Figure out how the attacker was able to exploit the system and utilize the backdoor to SSH into the system
To submit the flag, you'll have to wrap the backdoor into TMCTF{}
Download the file (https://s3-ap-northeast-1.amazonaws.com/trendmicro-ctf-2017/2VjxmQSdV3uBQvReFLea/files19.enc)
Decrypt the downloaded file by the following command.
> openssl enc -d -aes-256-cbc -k lnlzeirDTOWxKBdpBTsz -in files19.enc -out files19.zip –md md5
> unzip files19.zip
Solution: We downloaded the file and decrypted the file by using the given openssl command and extracted the zip file.
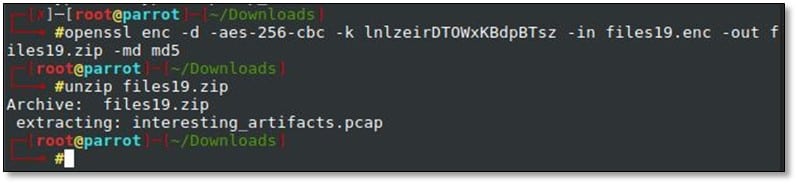
From the zip file, we got a pcap file, and we opened it by using Wireshark.
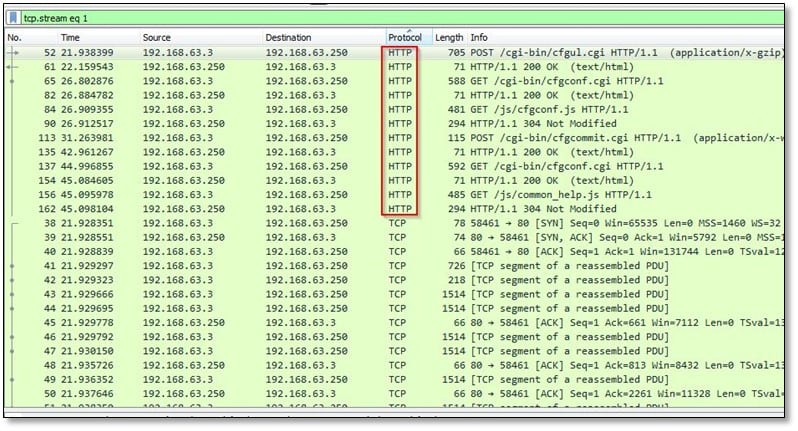
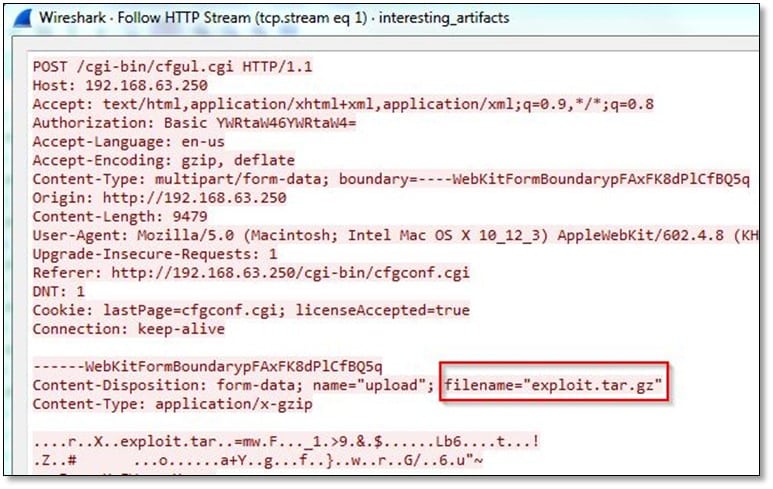
From Wireshark, we start investigating the HTTP traffic, and we noticed an exploit file attachment in POST request.
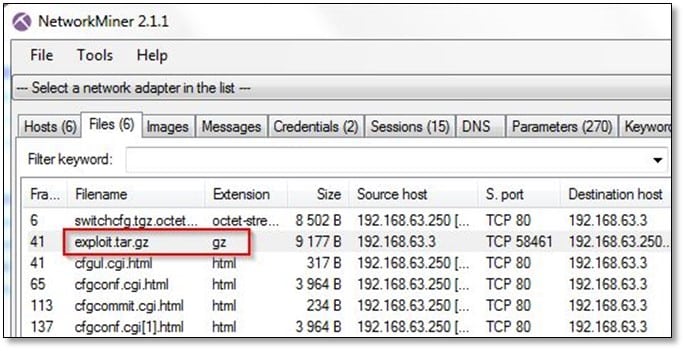
By using Network miner tool, we extracted the exploit.tar.gz file
Inside the exploit file, we found the etc, usr and var directory.
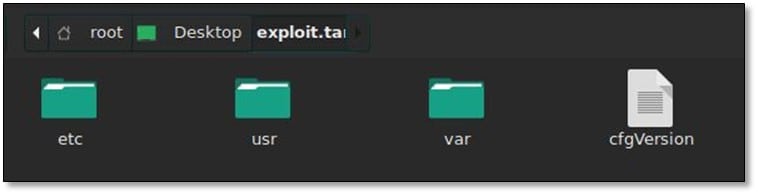
From the etc directory we found the passwd file, and we ran JohnTheRipper on it.
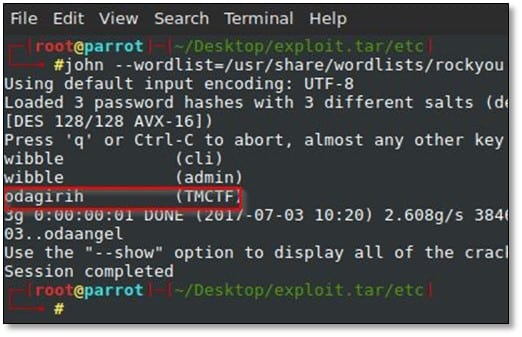
We found the password for TMCTF user who was supposed to be the flag, but it was not the password got truncated because DES uses a 56-bit key, where passwords are truncated to 8 characters and coerced into 7 bits each, so we grep the rockyou.txt file for the full password.
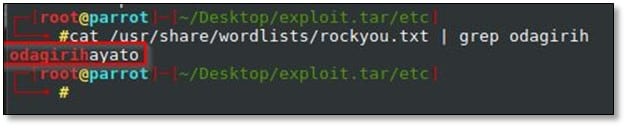
So, the final flag was TMCTF{odagirihayayo}

FREE role-guided training plans
Reference: https://ctftime.org/event/475




