The Top 5 Penetration Testing Tools and Their Reporting Features
Introduction
In the Cybersecurity world today, there is one methodology that has proven to be quite effective in determining the security vulnerabilities of any business entity: Penetration Testing. It can be explicitly defined as follows:
"It is the practice of testing a computer system, network, or web application, to find the vulnerabilities that an attacker can exploit."

Earn two pentesting certifications at once!
Enroll in one boot camp to earn both your Certified Ethical Hacker (CEH) and CompTIA PenTest+ certifications — backed with an Exam Pass Guarantee.
(SOURCE: http://searchsoftwarequality.techtarget.com/definition/penetration-testing)
Pen Testing can be done either manually or via the use of automated software packages, and it typically involves four primary steps:
- Gathering as much information and data as possible about the target before the actual test is conducted;
- Determining any known and unknown entry points;
- Attempting the actual Cyber-attack (or break in);
- Reporting the findings back to the relevant parties.
There is no doubt that all of these steps are important, but it is the last one which is probably the most crucial-after all, you need to know the results and interpret them to take the corrective actions needed. In this article, we examine some of the top Pen Testing Tools with robust reporting features that you and your team can use.
The Top 5 Pen Testing & Reporting Tools

Currently, this is the most widely used Pen Testing tool. The name "Metasploit" comes from the term exploit. In other words, this software package can literally "exploit" software code of any kind of application and can even deliver a specific payload which can examine the vulnerabilities and the weaknesses of the target, which go unnoticed. This tool can be used across a wide variety of environments, which includes both hardware and software platforms. It can also run on Open Source (Linux, Apache, etc.) and Closed Source Operating Systems (Apple iOS and OS X, Windows, etc.).
The reporting tools that come with Metasploit are highly customizable, and more detail on how to use them can be seen at this link:
https://blog.rapid7.com/2012/06/12/metasploit-custom-reporting-templates/
Another example of creating a Metasploit report is illustrated in the screenshot below:
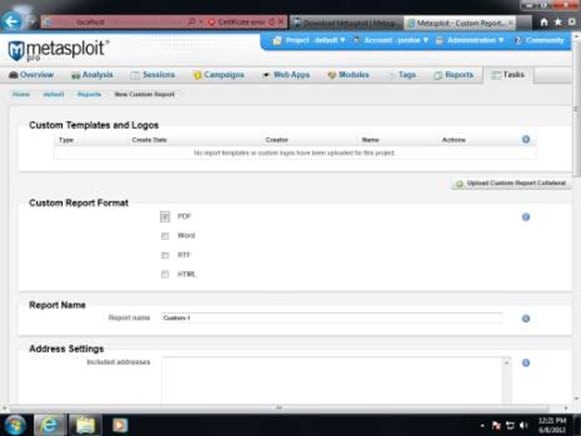
This example makes use of what is known as "Jasper Reports." To use this tool, you should be familiar with XML, Java, and SQL.
Details on using Jasper Reports for your use can be seen at this link:
https://blog.rapid7.com/2012/06/12/metasploit-custom-reporting-templates/
Metasploit can be downloaded for free here:

This is also another prevalent Pen Testing tool, as it has over 1.6 million users worldwide, and almost 25,000 business entities that make use of it. Here are some of the key features of it:
It is primary "sweet spot" is in conducting compliance checks, to make sure that your client is up to "snuff" with the latest federal mandates and regulations. Apart from being a Pen Testing tool, it is also deemed to be one of the most "robust" vulnerability identifier technologies that are available on the market today.
The reports that can be can be created are sorted out by the host that is being examined, and also by the specific Pen Testing feature that is being used. Further details on the reporting tools found in Nessus can be seen at this link:
http://info.tenable.com/rs/934-XQB-568/images/NessusPro__DS__EN_v8.pdf
An example of the type of reports that can be generated is illustrated below:

Some of the reports that can be generated include:
It comes with a 7-day free trial period, and it can be downloaded here:
https://www.tenable.com/products/nessus/nessus-professional
After the trial period is over, the annual subscription rate is $2,190 per year.

Although this tool can be used in a wide variety of Pen Testing environments, it has one primary purpose: The examination of network protocols, an analysis of the data and information that reside in the data packets, and any kind of encryption and decryption protocols that are used. Wireshark is used heavily by both the commercial and the non-commercial sectors, not-for-profit agencies, and even government entities as well.
Wireshark uses charts and views primarily as its main reporting functionalities. Specific details about it can be seen at this link:
https://www.riverbed.com/products/steelcentral/steelcentral-packet-analyzer-personal-edition.html
Best of all, Wireshark can be used across an entire array of platforms, which include the following:
One of the robust reporting tools for Wireshark is its "GeoIP" tool. With this, you can get a detailed view of IP addresses being examined worldwide. This is illustrated below:

The details on how to use this reporting tool can be seen here at this link:
Wireshark can be purchased at this link:

This tool is classified as an overall scanner, and many Pen Testers attest to how powerful it is when scanning for weaknesses and holes. For instance, it can scan for over 100 vulnerabilities, which include the following:
Its reporting tools come with the following functionalities:
-
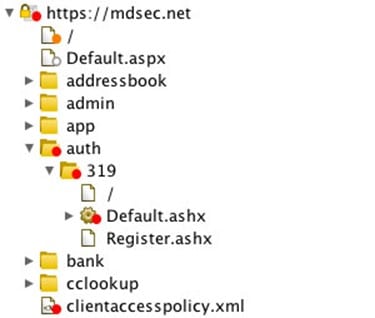
Target Site Map:
This displays all of the content which has been discovered at those points that are being Pen Tested. This is all displayed in a tree-like fashion, which shows all of the vulnerabilities found as well as their severity levels. This is illustrated below:
-
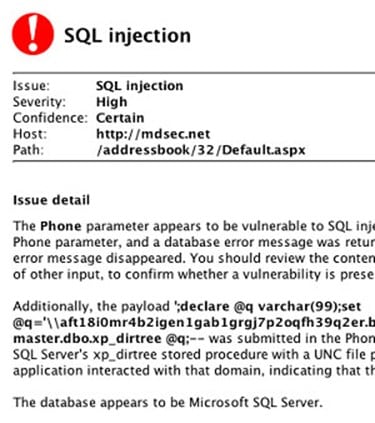
Customized Advisories:
This feature details the full content about the Security vulnerabilities which have been found, as a well as displaying a plan as to how to remedy them. An example of this is as follows:
-
Evidence:
Each Security vulnerability and weakness which has been discovered comes with the actual evidence to support it. This is particularly useful for software developers to quickly discover the holes and backdoors in the source code that they create, and how it should be fixed to the best extent possible.
-
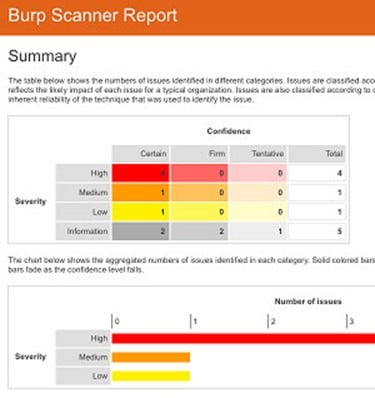
Easy to understand reports:
All of the data that is found in each scan can be created into an HTML format with the most relevant information highlighted. This is an example:
A trial version of Burpsuite can be downloaded at this link; but after that expires, the costs are $349.00 per year per user:

Unlike the other Pen Testing tools as described in this article, this one actually scans for the entire infrastructure of a business or a corporation. Their tools are grouped under one category called the "Retina Community." It can actually be viewed more as a Vulnerability Management platform. For example, it can scan for the following categories within an organization:
- Network security;
- Vulnerability assessments for Cloud-based assets;
- Web Security protection and scanning;
-
Endpoint assessments and protection.
Specific details about the reporting tools can be seen at this link:
https://www.beyondtrust.com/resources/data-sheet/retina-cs/?1486141809
However, in general, it consists of the following features:
- Multi-tiered architecture: The framework for each report is based upon the specificities of what is actually being Pen Tested;
- Threat Analytics dashboard: This allows you to prioritize and rank those Cyber threats from the most severe to the least possible risk of exposure;
- Resource Planning: This allows your team to build specific "what if" scenarios to plan for the proper allocation of resources during the actual Pen Testing cycle;
- Retina contains over 270+ customized reporting templates which can be tailored to the needs of your client to display the information and data which has been collected accurately;
- Compliance reporting: Make sure your client comes into compliance with Federal regulations such as HIPAA, Sarbanes-Oxley, etc.;
- Heat maps: You can display to your client in just a few seconds as to what the most vulnerable assets are in their IT infrastructure.
Here is an example of a Risk Matrix and Heat Report:
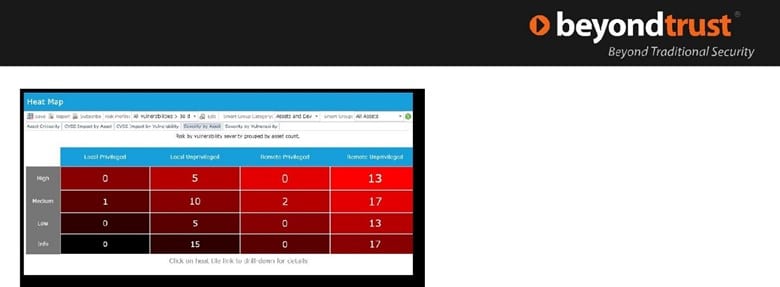
Here is an example of a Vulnerability and Threat Report:
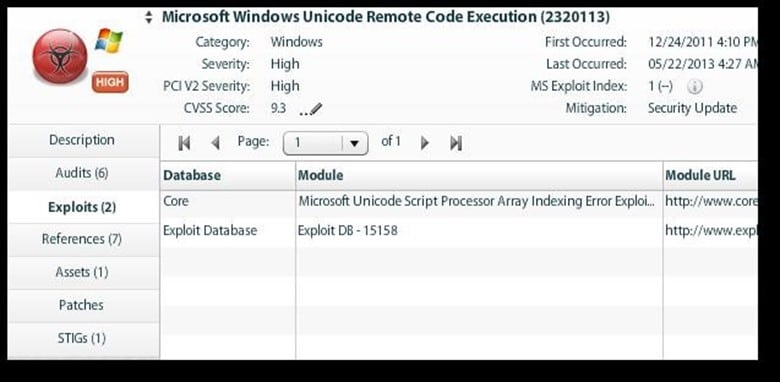
Here is an example of a Remediation Analysis Report:

There is a limited free trial of Retina, but after that expires, you will need to contact them to request a specific price quote. It can be downloaded at this link:
https://www.beyondtrust.com/free-trial-request/#Vulnerability-Management

FREE role-guided training plans
Conclusions
Overall, this article has examined some of the top Pen Testing tools (as well as their reporting features) which are being used the most thus far. Obviously, there is a quite a bit out there that you and your team can choose from. However, deciding the specific Pen Tool(s) to be used is primarily dependent upon the needs of your client, but also the environment that is being tested and the IT assets which reside in them.
Sources
- http://searchsoftwarequality.techtarget.com/definition/penetration-testing
- http://www.softwaretestinghelp.com/penetration-testing-tools/
- http://www.metasploit.com
- http://www.tenable.com
- http://info.tenable.com/rs/934-XQB-568/images/NessusPro__DS__EN_v8.pdf
- https://www.tenable.com/products/nessus/nessus-professional
- http://www.wireshark.org
- https://portswigger.net/burp/
- https://www.beyondtrust.com/products/retina/
- https://www.beyondtrust.com/resources/data-sheet/retina-cs/?1486141809
- https://www.beyondtrust.com/free-trial-request/#Vulnerability-Management
- https://blog.rapid7.com/2012/06/12/metasploit-custom-reporting-templates/
- http://www.behindthefirewalls.com/2013/11/how-to-create-geoip-map-report-wireshark.html
- https://www.beyondtrust.com/wp-content/uploads/DS_RetinaCS_Reports_Letter.pdf




