Tiredful API Part One
In this post, I will explain how to solve Tiredful-API. Let's start.
What is TIREDFUL-API
TIREDFUL-API is an intentionally designed broken web application based on REST API. The App aims to teach developers/QA/security professionals, flaws that are generally present in web services (REST API) due to poor or insecure coding practices.

Earn two pentesting certifications at once!
Enroll in one boot camp to earn both your Certified Ethical Hacker (CEH) and CompTIA PenTest+ certifications — backed with an Exam Pass Guarantee.
Please find below the screenshot of Tiredful-API –
List of Vulnerabilities in Tiredful-API
In the current version, Tiredful-API includes following vulnerabilities for practice –
- Information Disclosure
- Insecure Direct Object Reference
- Access Control
- Throttling
- SQL Injection (SQLite)
- Cross Site Scripting.
Getting and Setting Tiredful-API on the local system
Tiredful-API can be set up in two ways:
- Running the server on the local system
- Docker Container
Running the server on the local system
In this method, the Tiredful-API can be set up on the local system by downloading the files from the official source. Tiredful-API can be downloaded from here. Once you have downloaded the setup, extract the zip file, and you should see the files shown below –

Click on the Tiredful-API folder for the files shown below –

We need to run manage.py file for starting the API web server. The Tiredful-API is developed using Django Framework and Django Rest Framework, so one should have Django and Python installed on the local system. Once you have both the software installed, the web server can be simply started using the command -
python manage.py runserver
If static files fail to load, then just execute the above command with the insecure flag. The command with the insecure flag is - python manage.py runserver --insecure
This should start the web server on the local system. By default, the web server runs on port number 8000.
Docker Container
Tiredful-API can be run via Docker. Execute the following command to run via Docker:
docker build -t tiredful.
docker run -p 8000:8000 --name tiredful -it tiredful
Browse to http://localhost:8000 for getting started.
Now everything is setup, let's start solving the vulnerable API.
You can use any RESTClient app like Postman, RestClient addon for Browsers, Curl, etc. for connecting and communicating with the endpoint. I will be using RESTClient Firefox add-on for connecting and communicating with the API.
Tiredful API challenges and Solutions
Insecure Direct Object Reference
Insecure Direct Object Reference occurs when an application provides direct access to objects based on the user-supplied input. As a result of this vulnerability, attackers can bypass authorization and access resources in the system directly, for example, database records or files.
Challenge Description – Here is the description of the challenge
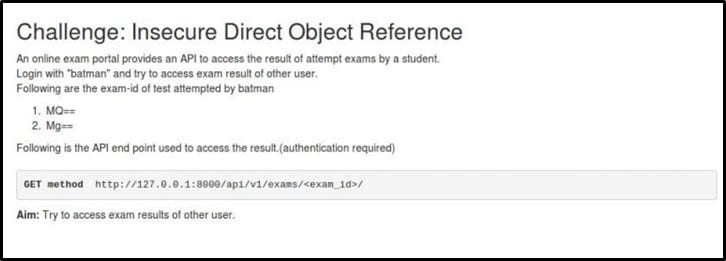
The aim is to access exam results of another user.
The above image shows API endpoint as <host>/api/v1/exams/<exam_id>/.
As per the challenge description, user batman took the exams with exam id MQ== and Mg==. These ids are Base64 encoded. So, to access the exam result of another user, we need to manipulate the exam id and encode it in base64 form.
As per the challenge description, we need to log in with user id as "batman" for getting the access token. The password for the user "batman" is Batman@123. Login with the username and password for getting the access token.
Now let's try accessing the result of another user by manipulating and encoding the exam id. Once the id is encoded we just append it to the end of the URL and send the request to the server. One of a kind is shown below with exam id 56. I have encoded the id, and the base64 of 56 is NTY=. I just append it to the URL, and the request becomes http://127.0.0.1:8000/api/v1/exams/NTY=/
The output for the above URL is shown below
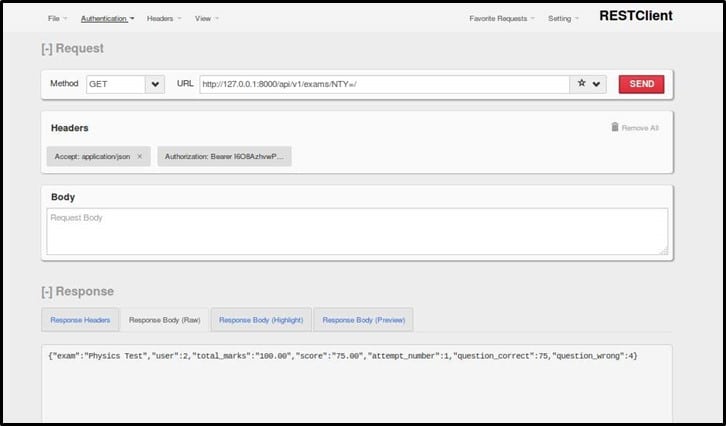
Thus, I can access the result of another user as shown in the response by manipulating the id parameter as shown above.
Information Disclosure
Information disclosure is when an application fails to properly protect sensitive information from parties that are not supposed to have access to such information in normal circumstances.
Challenge Description – Here is the description of the challenge
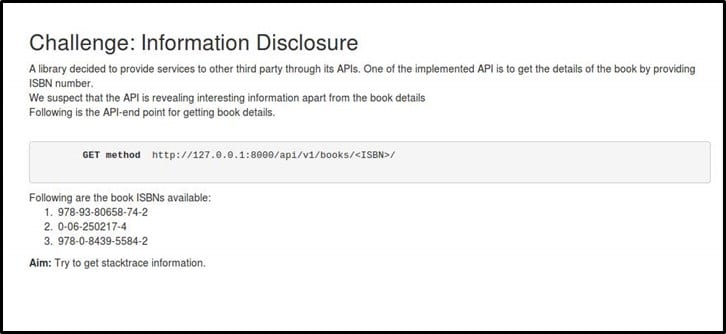
The aim is to get stacktrace information.
The above image shows API endpoint as <host>/api/v1/books/<ISBN>/.
As per the challenge description, we can retrieve the information of the book by passing the valid ISBN. Now we must retrieve the stacktrace information. Let's do it by passing the invalid ISBN and see what information is obtained.
Issue an HTTP GET request to the endpoint as shown
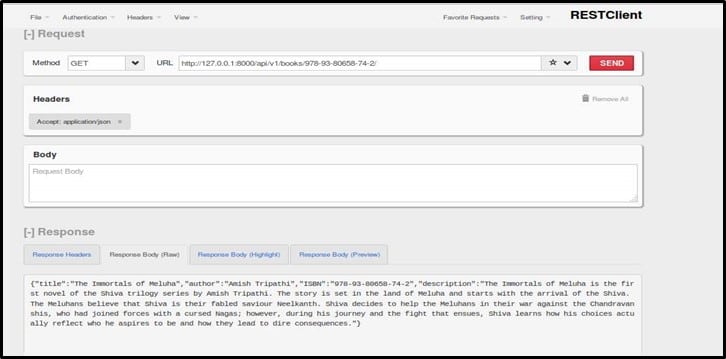
As shown in the response, valid description is obtained.
Now let's issue the invalid ISBN as shown below and check the response
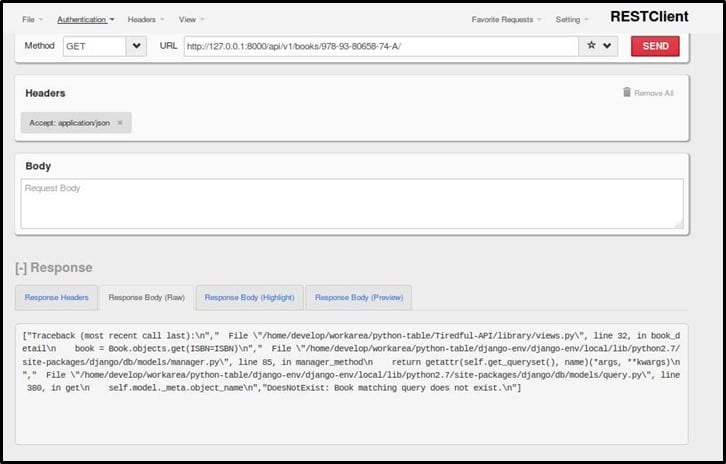
Yeah, the stack trace information is displayed as shown.
Access Control
Access control is a way of limiting access to a system or to physical or virtual resources. In computing, access control is a process by which users are granted access and certain privileges to systems, resources or information.
Challenge Description – Here is the screenshot of the challenge
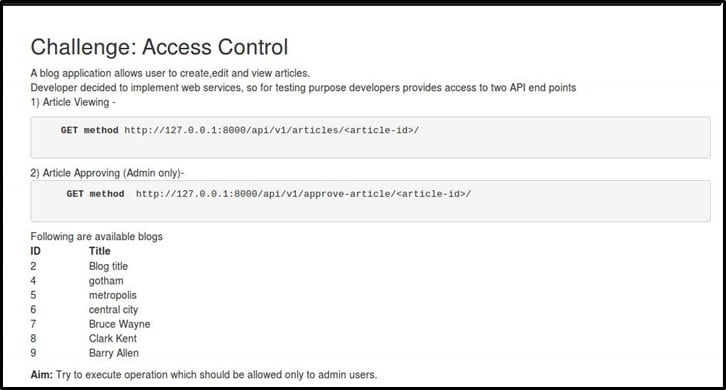
The aim is to execute any operation which only an admin user can perform.
There are two endpoints in this challenge – One for viewing the article and other for approving the article. Any user can view the article, but the right of approving the article is with admin user only.
I started interacting with the API by setting the article-id as 2. When sent the request with article id as 2, this is what I received in response
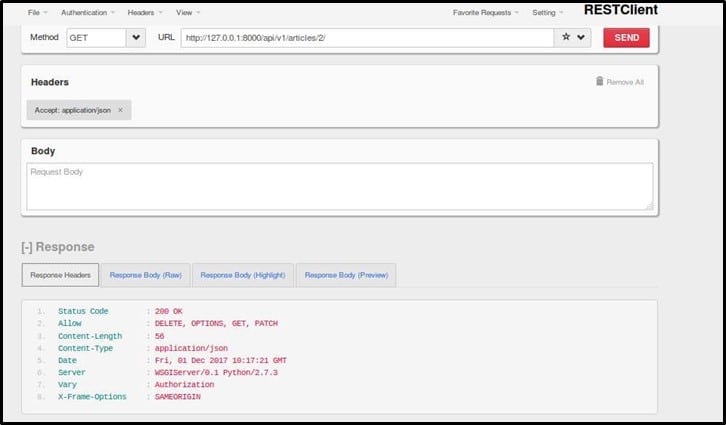
Yeah, delete method is supported.
In any application, the right of deleting the article is assigned to admin user only. Let's try deleting the article being a non-admin user.
Here is the request for deleting the article as a non-admin user. Let's see what we receive in response
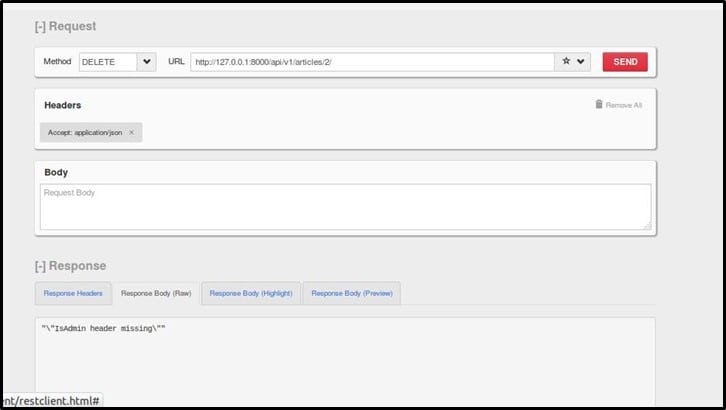
So, we get an error – "IsAdmin header missing." It means if we add the header to the request, we may end up deleting an article though being a non-admin user. Let's try doing it
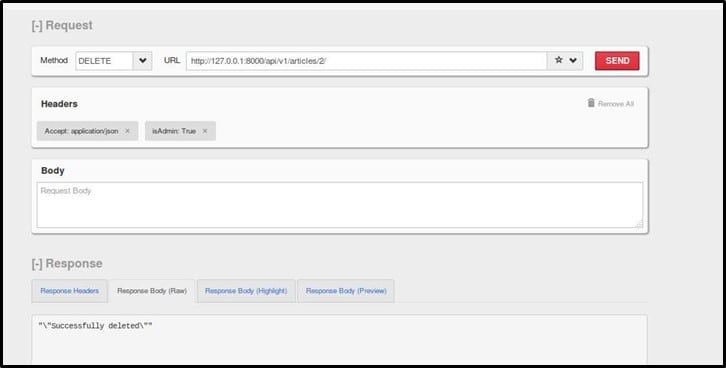
Yeah as seen in the response we deleted the article successfully.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
That's it for this part. In the next part, we will be solving the remaining challenges




