Tips for Managing Physical Security
What is Physical Security?
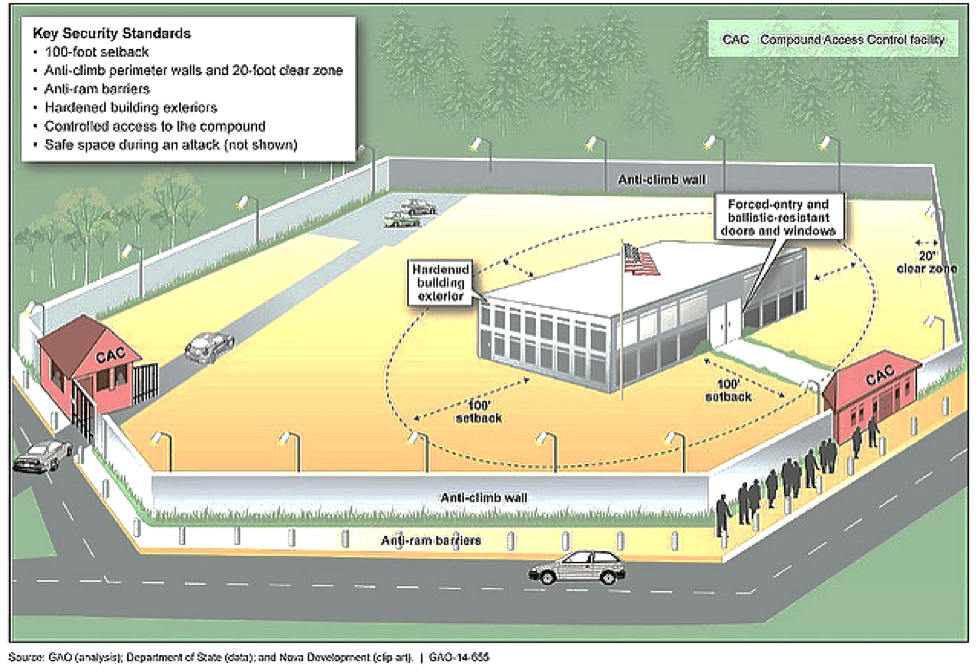
Source: GAO
Phishing simulations & training
According to the security expert S. Harris, “physical security protects people, data, equipment, systems, facilities and company assets.” She also enumerates various means through which this protection is managed: “site design and layout, environmental components, emergency response readiness, training, access control, intrusion detection, and power and fire protection.” The emphasis of this writing is on physical security through training of personnel based on a proper security awareness training program.
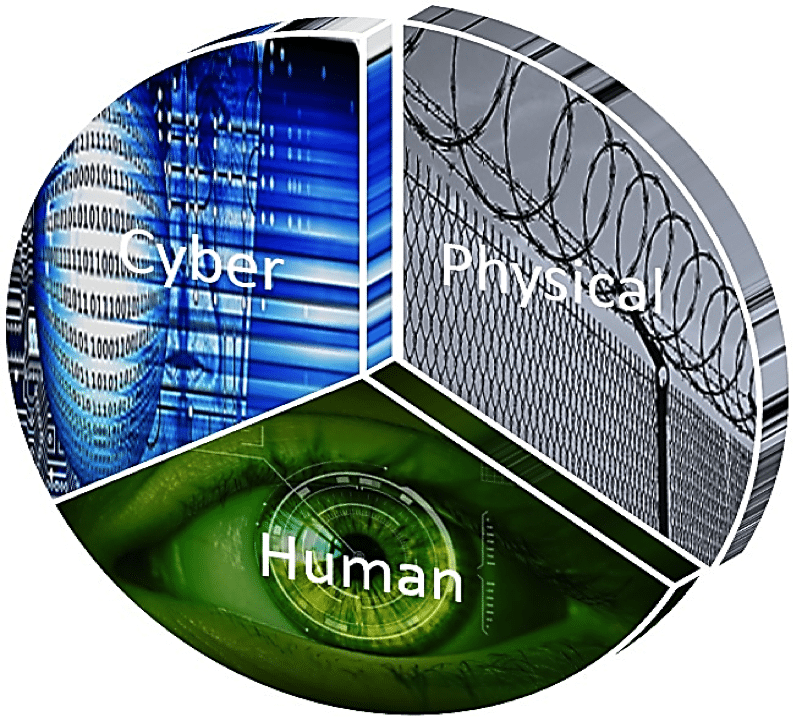
Justin Bonnema, a writer at the Security Awareness Company (SAC), points out that there are three domains of security:
- Cyber (e.g., computer, network and information security; important tasks: encryption, data backups).
- Human (e.g., employees, consultants, suppliers, partners and anyone in contact with your company, important tasks: prevention of social engineering scams).
- Physical (e.g., the wires, silicon, glass, and structures; important tasks: locked doors, clean desks, situational awareness, shredding).
These domains are so intertwined that one small issue in one domain may tip the balance in the other two.
Without physical security controls in place, most digital defenses could be rendered useless. Some workable solutions for most of the physical security threats are alarm systems, mantraps, and physical intrusion detection systems. People, not walls, however, are the first line of defense in the physical security paradigm. One insider alone can take out of the equation the thickest walls and every cutting-edge technology. Moreover, an IBM study established that human error is at the root of 95% of all security incidents.
Because nowadays the emphasis is on technical controls, many workers tend to neglect purely physical concerns in their own department. Not practicing due diligence regarding all mandatory physical security requirements can be a justa causa for companies to be held criminally or monetarily liable. Leaving devices unattended is the easiest way to have them stolen. Such devices that happen to contain personally identifiable information (PII) is an excellent illustration of a reason for initiating litigation against an organization on the grounds of negligence.
A scenario like this should not seem implausible: about 74,000 workers were included in data breach statistics due to laptop theft with unencrypted personal data. The phenomenon called Internet of things (IoT) is widening the spectrum of physical security. Today so many mobile devices exist that it comes as no surprise that they are an easy mark for experienced thieves.
Physical access to a company’s IT systems will make hacking them much easier by all means. While hacking into access control smart cards, for example, is a potential way in for any intruder, the primary focus of this writing is non-technical ways to defeat physical security.
[Free] Marine Lowlifes Campaign Kit
You don't need an unlimited budget or dozens of hours to create a truly engaging security awareness campaign. You just need the right resources and a playbook.
[Download] Free Security Awareness Kit
II. Common Physical Security Threats
Social Engineering
Social engineering attacks prey on human nature and good will. A con artist tries to gain the trust of an inside person using deception techniques (e.g., impersonation or conniving behavior such as false flattery). Additional human traits that social engineering attackers strive to exploit are: desire to provide assistance, a propensity to boast, and general lack of vigilance. In other words, social engineering attacks attempt to bypass IT and physical security controls by targeting humans.
With respect to physical security, the goal of the attacker is to use the social engineering attack as a stepping-stone to the organization’s IT infrastructure or physical facility. By way of illustration, a malicious actor could attempt to infiltrate a particular building under the guise of a repair technician. Once he achieves this goal, he can choose then to install a sniffer to capture all kinds of sensitive data.
Piggybacking and Tailgating
Piggybacking and Tailgating happen when someone who does not have access takes advantage of another person who has to infiltrate into a secure area.
Tailgating occurs when an intruder creeps into a protected zone with a person or a group of persons without their knowledge. An example of this act is when an intruder follows an unsuspecting employee. The employee unlocks a door to a secure area, but he is not observant of everything around him, and the intruder manages to set his foot on the closing door and eventually to enter the restricted zone.
Piggybacking, on the other hand, happens when an intruder (“being given a piggyback ride”) goes inside a security perimeter accompanied by a person who has access and who is fully aware of the fact that he lets in another person. However, he usually does not recognize the intruder as such. Common examples of piggybacking are:
- When a security guard or employee gives access to an attacker who claims to have forgotten his key
- When an attacker disguises himself as a technician and then convinces a security guard/employee to let him come in through a door that leads to a security area
- When an attacker approaches a door that leads to a security area, carrying a large, heavy-looking object, such as a big cardboard box, and politely asks a security guard/employee to open and hold the door for him
Dumpster Diving
The act of going through the thrash of a given entity in search of information that might be helpful for refining strategies for a potential attack. Often what is found in the dumpsters is combined with other information. Kevin Mitnick, for instance, once used company newsletters to inquire about the new hires, who will be more inclined to give out sensitive information to the “top floor” out of a desire to make a good first impression.
What are the most common types of intelligence the attackers are looking for when they ransack someone’s garbage? Mostly things like network configurations, access documents, discarded storage media, information on employees; all sensitive information that might be used in a social engineering scenario.
So many companies are careless about their litter and the garbage disposal process as a whole. Moreover, even nowadays, a great deal of valuable information in organizations is being printed out, whether we consider it in the context of proprietary or seemingly benign data. Workers still chose to ignore the risks and dispose of important business or employee documents by throwing them straight into the bin. This security lapse leads to a very basic but easily exploited vulnerability. Carelessness usually comes at a great cost. CVS Caremark, the retail pharmacy was subjected to a $2.25 million fine for poor physical security controls after a thorough investigation by the Department of Health and Human Services Office for Civil Rights (HHS-OCR) and the Federal Trade Commission (FTC). The two institutions determined that CVS dumped sensitive objects, such as medication instruction sheets and prescription drug bottle labels, into public dumpsters.
Dumpster diving as a nefarious activity is directly connected to the physical security of a certain corporation. It tests the ability of that corporation to restrict access of unauthorized persons to its thrash repository. Many organizations resort to special locked receptacles dispersed within the confines of organizations for their workers to safely discard sensitive or proprietary data. The receptacles work by the principle of post office mailboxes – you can place an item inside them, but you cannot take it back once it is in there.
Every measure that effectively blocks the access to a company’s dumpsters will do – shredders, locks, and encouraging employees to follow all disposal procedures, to name but a few. A cross cut shredder is probably the most effective type of shredder since it will turn the entire paper into miniature confetti-like scraps.
Nevertheless, these measures would be futile if a stringent awareness campaign does not accompany them to teach employees how to use and apply the measures.
Shoulder Surfing (example: peering over somebody else’s shoulder to look at a visible password)
Sometimes con artists prefer to take the risk to get closer to a targeted person to look over his shoulder and read what is written on the screen or observe the keyboard as this person types. Screen filters placed over a monitor can deter prying eyes. Also, password masking – i.e., displaying asterisks instead of the actual password characters – is always a good idea. As to typing safely, just type important things such as passwords while you cover your typing arm with the palm of your free hand. Other tips that may impede shoulder surfing: do not use corporate computers in public areas, sit with your back against the wall, angle your device or keyboard, and lean a bit toward the device or keyboard when you type something sensitive.
Physical Security Awareness Program
Importance
Most awareness programs tend to overlook physical security education for some reason or another. Physical security awareness, however, is essential in cases of some social engineering attacks as well as educating employees about best security practices, such as upholding visitor policies, workstation locking, encryption of (mobile) devices & USB flash drives, and maintenance of a clear desk (See the image below).
“Oh, security is not my responsibility, I’m not technical.” Well, this excuse could not be more wrong, because security is everyone’s responsibility, and, by extension, physical security is everyone’s responsibility. The duty of physical responsibility should not be imposed only on the security personnel since physical security encompasses every person who inhabits certain corporate facilities. Hence, all employees should participate in such security awareness sessions.
One of the main objectives of every security awareness program is to educate employees on reporting suspicious activities and behavior to the security staff, not to be security professionals themselves. The majority of workers have more than enough duties, and nobody should expect from them to become versed security professionals, but it is realistic to expect from them to understand the threat when they are taught about it and report it.
Tips
“Poor security awareness is the single biggest obstacle to defending against cyber-attacks. Moreover, poor security awareness training is rife,” writes lexi, the author of .
Below are some best practices with respect to physical security awareness that may be useful to you:
- Explain the intersection with cyber security – After all, we are discussing physical security in the context of information technology. For that reason, the meaning of the word ‘physical’ may transcend the traditional boundaries. Consider, for instance, a worker walking away from his desk. Locking or turning off his computer is a physical security concern since it has already been emphasized that one should “keep everything valuable under lock and key.”
http://www.lbmcinformationsecurity.com
- Make the content interesting, entertaining, and relevant to your staff. (Example: Keep your mobile phone with you at all times! (number b)) vs. Someone stole a mobile phone from a colleague of ours while he was refilling his Diet Dr. Pepper at Wendy’s! He said he had left it on the table for like 30 seconds only.) It is advisable to create your training plan in a more interactive way so that it will be engaging to the employees as well as educating. The security awareness training in many organizations comes down to merely going through a series of outdated slides sent via email. Served in such a fashion, the security awareness training becomes just a mundane box ticking exercise.
Do not generalize. Bring things back to the individual level. Evoke trainees’ emotional side – People tend to remember those things that may affect them personally, so make what is included in the physical security awareness program more about them. - Repeat the basics every now and then – Rehearse the core principles through numerous means: emails, phone calls, stickers, posters, ongoing training, etc.
- Perform penetration testing of your organization’s physical security – This is as practical as it can get. Have your organization tested by a real would-be invader. He can choose to test your employees about things mentioned in your physical security awareness program and add even more security-related challenges.
- To be effective, a security awareness program should go beyond compliance requirements.
- Again, stress the importance of physical security. Convince the people you will train that physical security is a very important matter. If they view the training as a waste of their time, it will be a waste of time, your time, money, and effort.
Reference List
Abernathy, R and Mcmillan, T. (2013). CISSP Cert Guide. Available at https://books.google.bg/books?id=TGYlDAAAQBAJ&pg=PT268&lpg=PT268&dq=data+retention+cissp&source=bl&ots=70xzZI3KMG&sig=fOqRJkXQvTjBiMrezfwVypJc8yw&hl=en&sa=X&ved=0ahUKEwi30qCau5HQAhVF0hoKHd7wAQEQ6AEIPzAH#v=onepage&q=data%20retention%20cissp&f=false (31/01/2017)
Bonnema, J. (2016). Nontechnical and Physical Security. Available at http://www.thesecurityawarenesscompany.com/2016/07/07/nontechnical-and-physical-security/ (31/01/2017)
Carthy, M. (2016). 7 Essential Security Awareness Training Topics. Available at https://www.linkedin.com/pulse/7-essential-security-awareness-training-topics-mike-carthy (31/01/2017)
Cobb, M. (2016). Physical security. Available at http://searchsecurity.techtarget.com/definition/physical-security (31/01/2017)
Emory University. Information Security Awareness Message - Physical security. Available at http://it.emory.edu/security/security_awareness/physical_security.html (31/01/2017)
Gardner, B. & Thomas, V. (2014). Building an Information Security Awareness Program: Defending Against Social Engineering and Technical Threats. Available at http://www.sciencedirect.com/science/book/9780124199675 (31/01/2017)
Gregg, M. CISSP Exam Cram. Available at https://books.google.bg/books?id=2UzODAAAQBAJ&pg=PT74&lpg=PT74&dq=scoping+and+tailoring+privacy&source=bl&ots=Se48Y2tn1w&sig=RCtlfF8gBupaZgr08uj1OkSV-M0&hl=bg&sa=X&ved=0ahUKEwjrtcHDlu_PAhWGXRQKHTEBCFkQ6AEIPzAD#v=onepage&q=scoping%20and%20tailoring%20privacy&f=false (31/01/2017)
Hutter, D. (2016). Physical Security and Why It Is Important. Available at https://www.sans.org/reading-room/whitepapers/physical/physical-security-important-37120 (31/01/2017)
InfoSec Institute (2014). Managing Physical Security: Part 1. Available at http://www.business2community.com/travel-leisure/managing-physical-security-part-1-2-0926723 (31/01/2017)
InfoSight, Inc. Social Engineering & Physical Security. Available at http://www.infosightinc.com/solutions/advisory-services/social-engineering.php (31/01/2017)
kellyk (2016). Designing Physical Security Awareness Training (That Won’t Be Forgotten in Five Minutes). Available at https://www.tracesecurity.com/blog/designing-physical-security-awareness-training-that-wont-be-forgotten-in-five-minutes (31/01/2017)
LBMC Family of Companies (2014). Developing an Effective Security Awareness Program: Physical Security, Password Security, and Phishing. Available at http://www.lbmcinformationsecurity.com/blog/developing-an-effective-security-awareness-program-physical-security-password-security-and-phishing (31/01/2017)
lexi (2015). How to Develop Security Awareness Training That Works. Available at https://www.tracesecurity.com/blog/how-to-develop-security-awareness-training-that-works#.V9GQB_krJhF (31/01/2017)
Piran. G. Managing Physical Security Systems & Information In A Multi-Building Campus. Available at https://us.sourcesecurity.com/news/articles/co-2784-ga.9150.html (31/01/2017)
See Infosec IQ in action
Stewart, J., Chapple, M., Gibson, D. (2015). Certified Information Systems Security Professional Study Guide (7th Edition)