“There’s never been a better time to learn cybersecurity,” says Infosec Skills instructor Keatron Evans
The cybersecurity education landscape was quite different when longtime Infosec instructor Keatron Evans began teaching in 2007. The general public mostly wasn’t aware of hackers, and cybersecurity was more than a decade away from becoming the $120 billion a year industry it is today.
As hacking and other cybersecurity threats evolved, so has the way we teach the skills needed to stay ahead of cybercriminals.
FREE role-guided training plans

Getting started in cybersecurity
“In the very early days, 85% of the students attending classes were already familiar with pentesting and incident response,” Keatron said. “Because the demand for cybersecurity professionals grew so rapidly, today’s students tend to have much less experience coming into the field.”
But that’s not a bad thing, Keatron said. It’s the natural progression of a burgeoning industry.
“Cybersecurity knowledge is much more freely available now, and resources like Infosec Skills provide opportunities for professionals of all levels to become faster and deeper learners.”
Learn incident response with hands-on training
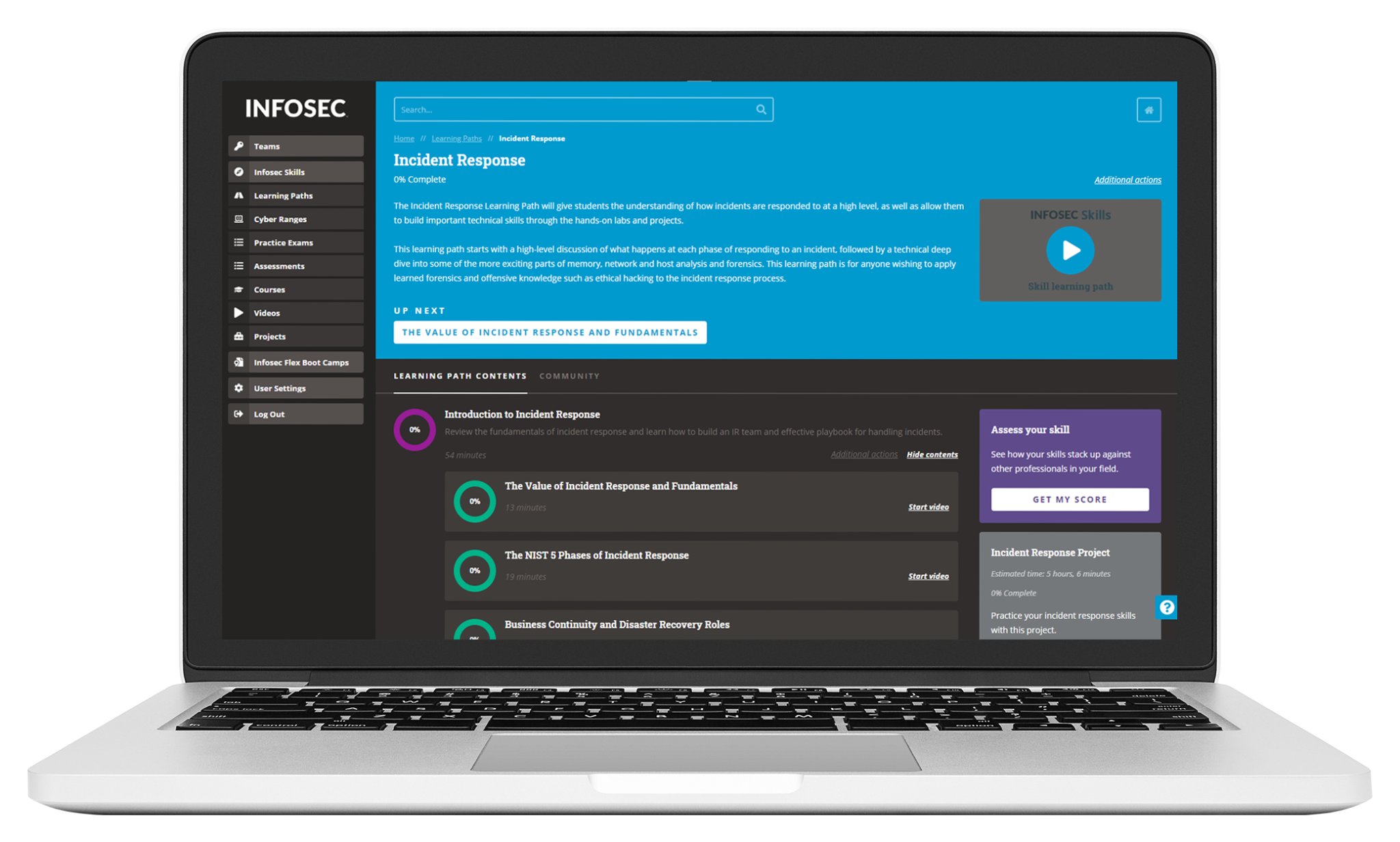
Keatron’s long-time expertise is evident in his new Incident Response Learning Path. It’s designed to give students an understanding of how to respond to an incident at a high level, while also building important technical skills through hands-on labs and projects.
“In the learning path we combine the high-level policy and procedural section of incident response with getting your hands dirty,” Keatron said. “We dig into the technical aspects of responding to an incident. It’s one thing to have a policy that outlines what you should do after a breach, but we dive in and see what happens and what that response actually looks like.”
The learning path follows the natural stages of incident response, including:
- Preparation
- Identification
- Containment
- Investigation
- Eradication
- Recovery
- Lessons learned
Students then get a technical deep dive into various tools of the trade for incident responders, including Zeek, Wireshark and Volatility, and test their skills with a hands-on Incident Response Project.
“We’re really excited about the material in these courses,” Keatron said. “Learners will do deep packet analysis from actual traffic pulled from an infected machine. They’ll use Wireshark and Zeke to dig into a network. So this will be serious network and packet forensics, serious memory forensics and hard drive forensics. It’s a lot of fun.”
Incident response and pentesting careers
Penetration testing is the foundation Keatron’s business, KM Cyber Security LLC. Keatron said that experience has led to a deep passion for both incident response and cyber threat hunting, which are natural outgrowths of pentesting.
“Pentesters make great incident responders and threat hunters because it provides a solid background for that work,” Keatron said. “Having a good understanding of forensics is essential if you want to do it well.”
“Look at the latest headlines. Big companies are getting breached every day. A big part of my job is going into these high-tension situations and being a calming presence. My goal is to figure out a measured strategy for attacking the problem so they’re in a better position after we leave.”
Building your incident response skills
Keatron worked hard to make the material in his Incident Response Learning Path accessible to a broad range of cybersecurity practitioners. He said incident responders and security operations center (SOC) managers will get a leg up with different approaches, tools and ideologies that are not commonplace in the industry yet.
Ethical hackers and pentesters will benefit from learning how malicious actors cover their tracks. The courses will also help develop an understanding of what type of information incident responders seek during their investigations. Cyber threat hunters will find the information useful as well, Keatron said, as there is a lot of overlap in what incident responders and cyber threat hunters investigate.
“The way we've structured the courses, even people with minimal cybersecurity experience will be able to learn and get through the exercises,” Keatron explained. “It’s going to be exciting, informative and challenging, but the main thing is you will come out of this training with a solid, foundational knowledge of cybersecurity incident response — plus the hands-on experience needed to put that knowledge into action.”
What should you learn next?

Check out Keatron's new Infosec Skills courses below:
About Keatron Evans
Keatron Evans is regularly engaged in training, consulting, penetration testing and incident response for government, Fortune 50 and small business. In addition to being the lead author of the best selling book, Chained Exploits: Advanced Hacking Attacks from Start to Finish, you will see Keatron on major news outlets such as CNN, Fox News and others on a regular basis as a featured analyst concerning cybersecurity events and issues.
For years, Keatron has worked regularly as both an employee and consultant for several intelligence community organizations on breaches and offensive cybersecurity and attack development. Keatron also provides world class training for the top training organizations in the industry, including Infosec Skills live boot camps and subscription training courses.


