How Harmful Can a Data Breach Be?
There is this belief that businesses that have suffered a data security breach very often do not recover. But is that really so? What does it take to actually destroy a company with a data breach?
Before we go to the analysis, let's just have a quick look at some statistics first:
Learn Incident Response
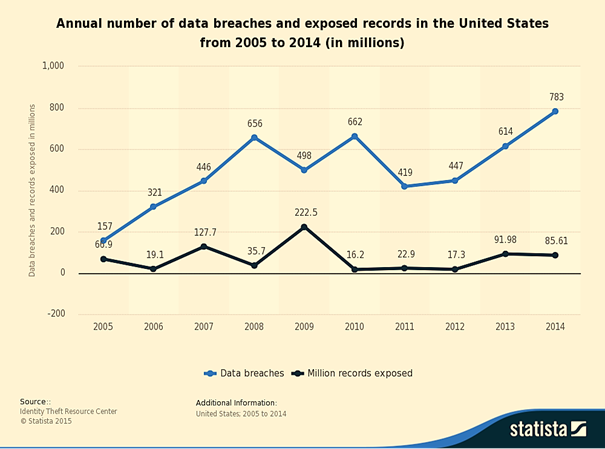
According to an annual research report made by Ponemon Institute and IBM:
- In 2015, the average cost of a data breach has increased by 23% since 2013 to reach $3.8 million.
- In 2014, the most expensive case resulted in $31 million worth of damages and the least expensive in $750,000.
-
The average cost per stolen record worldwide has increased from $136 in 2013 to $145 in 2014, and to $154 in 2015. Also, there is a dramatic increase in the retail sector where this amount went from $105 last year to $165, but the healthcare sector leads the ranking of the average highest cost by stolen record ($363).

Moreover:
- In the high-profile data breaches that cost up to $20 million, cyber-insurance amounts to $3 million, which leaves some $4 million gap because of the fact that frequently damages to a brand's reputation and "future lost sales" are generally not included in the coverage. Moreover, despite being a good safety-net solution, only as much as 8% of U.S. and 4% worldwide companies buy coverage.
Impact on Big Corporations
The media swamp readers with news about massive data leaks. While these kinds of cyber attacks undoubtedly affect many people, they are not necessarily fatal for the businesses under attack. As one article concluded, "the Home Depot hacking barely made a dent." Calculations showed that the net expenses related to the breach in question are $28 million, which ultimately "represents less than 0.01% of Home Depot's sales for 2014." Similarly, Target incurred $105 million in cyber breach-related expenses, but this amount is only 0.1% of their 2014 sales. It should be noted, however, the key metric used in this analysis is revenues rather than perhaps more appropriate data such as profit analysis: "It can make a lot of difference to management if an attack consumes a big chunk of your profit or, worse, pushes you from the green into the red side of the ledger [opinion of the Intel's information security strategist Matthew Rosenquist]."
It may seem surprising how large organizations struck by an information leakage shake off the funk inter alia surprisingly quickly, sometimes reacting as if nothing significant happened. Kaspersky Lab, for instance, despite being a worldwide company that creates security products, reported in June 2015 that it was subjected to a surreptitious cyber-exploitation campaign, presumably led by government agencies. The security vendor issued a statement providing more details about the case, in which is mentioned that security breaches nowadays are common, sophisticated cyber-attacks are difficult to fend off, and maybe the whole thing was something beneficial to the company and its customers, because it tested how good the detection capabilities of Kaspersky's new products are and gave at the same time useful intelligence for developing more effective ones. You may call it brazen, but the owners of Ashley Madison launched a statement as well that announced how everything is going on almost as normal as it was before the scandal. Truth be told, the indirect damages of a data breach are oftentimes not immediately visible and may linger on for a long time after the media fuss subsides.
Sony Pictures Entertainment Data Breach: Direct vs. Hidden Costs
Aon estimated that the majority of such kind of data security incidents, 80 %, results in less than $1 million in direct costs and damages. What is included in this category are legal expenses (e.g., legal settlements), business outage costs, fees for digital investigation and forensic services, remediation of information infrastructure, identity fraud alert services, payments for crisis communication (i.e., data breach notification obligations) and other specialized services. $35 million for the full fiscal year is the figure designated as an expenditure associated with the infamous security incident that happened to Sony Pictures in the end of 2014, as reported by the senior general manager Kazuhiko Takeda.

Yet in lasting nuisances like an information leakage, hidden costs should be taken into account. These are, for example, sinking customer trust and goodwill, damage caused to third parties, rising insurance premiums, etc. Putting a price on data is something that should be made on case-by-case basis. The Sony data breach in particular is not gruesome because of failing to protect customer trust, so there will be no payments for stolen customer records. Nevertheless, hundreds of files containing staff login details were stolen, which may entail changing login credentials and reconfiguration of every server – an arduous task that analysts at Macquarie Research predict to amount to some $83 million. Losses originating directly from the security incident are not a major financial setback to Sony, given their operating profit of $501 million generated for the fiscal year through March. And even though the Sony's CEO Kazuo Hurai attested that the financial results for this year will be unaffected by the security breach, experts deem that soon or later the less-obvious costs will add to the overall tab.
The challenges Sony faces are related more to reputation damage control than to dealing with direct, immediate costs, and it will certainly feel the repercussions of what was revealed for years to come. Not only was the company's dirty laundry washed in public by divulging what Sony executives think of several movie stars they worked with, or the revelation of some witty, slightly racial jokes addressing the U.S. President, but what can add up as well to the swollen expenses surrounding this cyber incident is the heavy loss of intellectual property and details on company's strategy in virtually every contract negotiation performed during recent years. The likelihood of this bad publicity to impede future business dealings in which the company is involved is undoubtedly great.
One thing is sure: All these costs are difficult to measure because of the intangible character of reputation, but when the brand is damaged, its intrinsic value decreases, the customers, investors, and business partners may sever ties, and replacing them may prove difficult. That is why Kowsik Guruswamy, CTO of the stealth startup Menlo Security, asserts: "The real cost to Sony's reputation in the industry is probably in the hundreds of millions, perhaps even $1 billion plus." In the same spirit, Mark Rasch, a former federal cybercrimes prosecutor, posed interesting questions: "Will they be able to attract high-name stars if those stars believe their personal information will not be protected? How do you know what business opportunities are lost? It's hard to put a dollar figure on it."

Impact on Small and Mid-Size Companies

Source: Hidden costs of Sony's data breach... by Mike Wheatley
Many organizations of a various size have to operate these days with valuable information about customers or employees. The reality shows that no matter how big an organization is, it is often unprepared to meet the exigencies of a post-data breach crisis.
Companies with less market power should expect a difficult time ahead of them. Some facts on the correlation between small businesses/startups and data breaches:
- 60% of those surveyed reported falling a victim to such an event;
- One in ten had to change the nature of business they conduct in order to restore their damaged reputation. Presumably, reputation is essential for small businesses/startups. The brand value is often so fragile that one blow is enough to cause irreversible harm;
- Expenses have doubled from the previous year.
For the sake of comparison, small businesses are even more unprepared for a cyber-breach than larger corporations, partly because they falsely believe they are too tiny to target, thus automatically dropping beneath the cyber crooks' radar, and partly because most of them are really cornered by the lack of a strong financial backbone. Furthermore, a 2013 study shows that only 33% of small businesses under attack notified the people affected. Some owners do not know that they are (most likely) obliged by law to report events as data breaches, or they might even believe that the laws do not apply to small firms; other owners simply ignore the happening.
By all means, failing to comply may entail greater risks as hefty fines or/and penalties, lawsuits, really bad publicity, long-term distrust among clients and investors, etc. Unlike mighty corporations that can rely on their really deep pockets or cross-subsidizing inefficiencies, for instance, to make it through these tough times, not so powerful ones may not stand their Golgotha.
The truth is that organizations, irrespective of their size, might not be incentivized to prioritize security. When CEOs consider cost savings, cutting the security budget may seem a tempting choice. A lack of effective legislation and incentive structure are reasons behind the abdication of responsibilities for a cyber-leakage on the part of companies, according to the CUNA President and CEO Jim Nussie. In the end, most of the merchants do not want to willingly take the plunge and invest substantial sums in more secure, cutting-edge technologies. Spending funds for security solutions requires a cost-benefit analysis just like anything else on companies' agenda. Owing to the fact that embedding in place more effective security measures takes up money, time, and efforts, one question often pops out – what is in fact the worth of not having to implement strong IT security? With this in mind, the words of Jason Spaltro, the former executive director of information security at Sony Pictures Entertainment, uttered in 2005 are sort of emblematic (knowing what happened 9 years later) : "[I]t's a valid business decision to accept the risk" of a security breach. I will not invest $10 million to avoid a possible $1 million loss [.]"
Source: Your Guide To Good-Enough Compliance by Allan Holmes
Yet in reality, most of those decision-makers notice in this situation only the tip of the iceberg, unsuspecting that under the surface looms something much bigger, which may wreck their business and professional partnership.
Destroyed by a Data Breach
Now let's have a look at three real-life cases of a business failure as a direct result of a data breach:
- The Dutch certificate authority DigiNotar suffered a fatal security breach in 2011. The compromise was facilitated by poor network segmentation and firewall misconfiguration: "An internal and external demilitarized zone (DMZ) separated most segments of the internal network from the Internet. The zones were not strictly described or enforced and the firewall contained many rules that specified exceptions for network traffic between the various segments," according to the security company Fox-IT.
- It all began in July the same year when the malicious intruder(s) used his unauthorized access to issue hundreds of corrupt digital certificates for high-profile domains, including google.com. A man-in-the-middle attack with the help of these certificates allowed the attacker to launch a massive surveillance operation against Internet users in Iran. Despite DigiNotar hiding the breach for a month or so, not long after the story became public, browser and operating system developers and the Dutch government revoked their trust in the company's products and DigiNotar filed for bankruptcy.
- Taking into consideration the bankruptcy filings made by Impairment Resources LLC, its doom was a direct result of a New Year's Eve burglary at its San Diego office. Two computer hard drives containing medical information of about 14,000 persons were among the items stolen. $150,000 in mitigation efforts plus $2.5 million estimate of regulatory fines and penalties was a dead weight for Impairment Resources. The company could have prevented the data breach in the first place if it had had an information security policy that would have required encrypting all personal data. In addition, Impairment Resources should have examined more carefully their cyber insurance policy in order to establish whether it would have been enough to cover the full extent of such a data breach.
- Altegrity Inc. is a privately held government contractor that had activities related to risk solutions, security, data recovery and employment screening. Its business collapsed following a data breach in 2013. Under attack was one of the departments of Altegrity Inc., US Investigations Services (USIS). This case raised alarms, since the personal details of approximately 25,000 employees of the Department of Homeland Security, the U.S. Customs and Border Protection agency, and U.S. Immigrations and Customs Enforcement were exposed. It should be noted that other factors contributed as well – the Department of Justice had already pressed some charges in January 2014 concerning improper background checks. Also, the Office of Personnel Management (OPM) declared publicly that it would not extend its partnership with USIS past the end of the contracts on September 30, 2014.
Conclusion
An interesting opinion is expressed by the Iain McLaren blog that, although data breaches today are embarrassing for the victims, they are not crippling. Iain McLaren argues that consequences of cyber breaches will be really grievous once anonymous digital currencies such as Bitcoin become mainstream. Now hackers' loot is credit card information, among other things. Unlike digital currencies, traditional banking cards are easy to cancel and money transfers can be traced down. Hence, introducing digital currencies backed by national governments will facilitate money laundry operations following data breaches targeting making payments.
As we can see, however, the consequences of a data breach can be detrimental, especially to smaller companies that are yet to begin gaining profits and consumer trust. Although they are most endangered, hidden costs of divulging valuable information (as in the Sony Pictures case) are like the iceberg that sunk the Titanic – it may take up some time but the bitter end is inevitable.
Some lessons to be learned from this analysis can be summarized in these quotations:
"Efficient response to the breach and containment of the damage has been shown to reduce cost of breach significantly…companies whose data is not protected are not only facing expensive direct costs from cleaning up a data breach, but also a loss in customer confidence that has long lasting ramifications."
"Regardless of the way we measure it, or whether we look forward or backward, we agree on the central point that companies need to invest in information security."





Reference List
Ackerly, J. (2014). 3 Lessons From Sony Pictures Cautionary Tale. Available at http://www.entrepreneur.com/article/241240 (21/09/2015)
Ausick, P. (2015). 140 Million Records Exposed in 533 Data Breaches to Date in 2015. Available at http://247wallst.com/technology-3/2015/09/02/140-million-records-exposed-in-533-data-breaches-to-date-in-2015/ (21/09/2015)
Burke, K. (2015). 'Free credit monitoring' after data breaches is more sucker than succor. Available at http://www.marketwatch.com/story/free-credit-monitoring-after-data-breaches-is-more-sucker-than-succor-2015-06-10 (21/09/2015)
Constantin, L. (2012). One year after DigiNotar breach, Fox-IT details extent of compromise. Available at http://www.computerworld.com/article/2493095/data-center/one-year-after-diginotar-breach--fox-it-details-extent-of-compromise.html (21/09/2015)
Iain McLaren. Why large companies don't invest in security. Available at http://iainmclaren.com/2015/01/19/databreach/ (21/09/2015)
Hackett, R. (2015). How much do data breaches cost big companies? Shockingly little. Available at http://fortune.com/2015/03/27/how-much-do-data-breaches-actually-cost-big-companies-shockingly-little/ (21/09/2015)
Kaspersky, E. (2015). Kaspersky Lab investigates hacker attack on its own network. Available at https://blog.kaspersky.co.uk/kaspersky-statement-duqu-attack/ (21/09/2015)
Sandler, L & Tan, A. (2015). Altegrity Files Bankruptcy After 'State-Sponsored' Breach. Available at http://www.bloomberg.com/news/articles/2015-02-09/altegrity-files-for-bankruptcy-after-losing-vetting-contracts (21/09/2015)
SMLRadmin (2013). Privacy Law Alert: Data Breach Leads to Bankruptcy. Available at http://smlrgroup.com/privacy-law-alert-data-breach-leads-to-bankruptcy/ (21/09/2015)
Ponemon Institute and IBM (2015). 2015 Cost of Data Breach Study. Available at http://www-03.ibm.com/security/data-breach/ (21/09/2015)
Rauber, C. (2015). This is how much a data breach will cost your company. Available at http://www.bizjournals.com/sanfrancisco/blog/2015/03/data-breach-cost-insurance-cyber-security-aon.html (21/09/2015)
Wheatley, M. (2015). Hidden costs of Sony's data breach will add up for years, experts say. Available at http://siliconangle.com/blog/2015/02/20/hidden-costs-of-sonys-data-breach-will-add-up-for-years-experts-say/ (21/09/2015)
Learn Incident Response
Workman, D. (2014). 5 myths about credit card security after a retail data breach. Available at http://canada.creditcards.com/credit-card-news/5-myths-about-credit-card-security-after-a-retail-data-breach-1264.php (21/09/2015)



