Social Media use in the Military Sector
Introduction
Social media has assumed a fundamental role in today's society. It is a technology with the highest penetration level, as billions of people are connected through the principal global platforms by sharing experiences, documents and media.
An audience this large is exposed daily to all kinds of cyber threats, and represents a paradise for attackers due to the low level of awareness and the possibility to hit a large number of users at the same time.

FREE role-guided training plans
Typically, the attacks exploit the concept of trust, which is considered the pillar of social network platforms. A majority of attacks implements social engineering techniques which are more or less sophisticated. Phishing attacks, malware-based attacks and APT are just a few examples of cyber threats.
The diffusion of mobile devices has contributed to the increase of social media popularity. Mobile users have discovered the possibility of being able to share their experiences on social networks on the go.
To better understand the diffusion of social networks, examine the following data:
The data confirms the high diffusion of the platforms and demonstrate that their use isn't a prerogative of youngsters. "Be social" is an imperative that involves people of any age and of any social abstraction. Users spend a lot of time on these platforms unaware of the possibilities that they offer to attackers. The data related to the professional use of social networks is also meaningful: millions of professionals and business managers linked through these platforms and who share, in many cases, sensitive information too superficially, expose themselves and their companies to serious risks.
The figures introduced demonstrate the impact of social media platforms on society, that make them interesting for governments and intelligence agencies that include their use in cyber strategies by exploring the possibility of adopting social media use as a military option.
Governments have soon discovered that using social media platforms is possible in conducting efficient cyber espionage campaigns or in attacks against foreign governments. Events such as the 2011 Arab Spring revolutions in North Africa and the Middle East, for example, were sustained and organized through social media platforms that allowed social exchanges on the web.
Social media in military sector
The large diffusion of social media makes them ideal for many activities of interest for governments and intelligence agencies. The potentialities of these platforms are enormous and their control, monitoring and use are a must.
Modern social media networks are actively used by governments all around the world. US, China and Russia are the countries that are most active in this field, but authorities from Iran and Syria have also demonstrated some interest for different purposes.
Governments are mainly attracted by social media due to the possibility of being able to support military operations such as:
- Psychological Operations (PsyOps)
- OSInt
- Cyber espionage
- Offensive purposes
Using social media militias could enable a cyber-offensive act against foreign governments. Let's say, for example, a cyber-espionage campaign for the diffusion of specific crafted malware, but with powerful social platforms, this could also be used to influence the global sentiment of a population in countries feeding such dissent against the central authorities.
Another alternative use of social network is for propaganda to spread a religion or an ideology widely and efficiently.
Many governments are promoting the growth of internal cyber units composed by specialists who analyze in real time the principal source of interest to monitor a global situation from cyber space, like a cyber-eye on the real world.
These teams are also working on the definition of a new generation of instruments that could be used for real time analysis of so large a quantity of information with the specific intent of providing early warning on situations of interest.
The US Department of Defense for example has created a dedicated web portal to provide any kind of information related to the use of Social Media for militaries and, more in general, for any citizens who desire to better understand these platforms.
Figure 1 - DoD Social Media Space
The portal is a demonstration of the opening of the US Government to social media as described by the following statements:
"Attention all Facebookers, Twitter tweeters and YouTubers: a new Defense Department policy authorizes you to access these and other Web 2.0 platforms from non classified government computers, as long as it doesn't compromise operational security or involve prohibited activities or Web sites."
The web site is designed to help the DoD community to use social media and other Internet-based Capabilities (IbC) responsibly and effectively. According to the last report from ENISA titled "Threat Landscape report," social media is one of the sectors most targeted by cyber threats according to current threat trends for emerging areas of Information Technology. The report proposes the following top emerging threats for social technology:
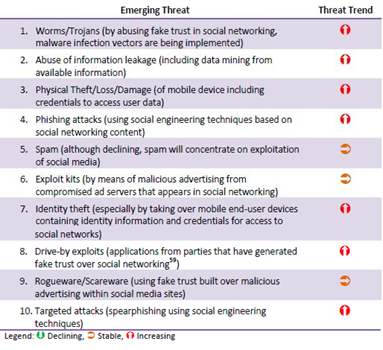
Figure 2 - Emerging Threat and their trends in the area of Social Technology (ENISA)
Due to the diffusion of social technologies, attackers will continue to develop new techniques to attack and exploit social media platforms. The situation is very serious if we consider the increasing interconnections with other sectors such as the Internet of Thinks, healthcare or education.
"Existing functions of social media can be used to achieve misinformation and eventually control political expression." Through the exploitation of social networks, it is possible to conduct cyber espionage campaigns infiltrating, for example, a limited number of individuals belonging to specific groups.
Psychological Operations (PsyOps)
Social media networks are privileged channels to adopt for psychological operations, also known as PsyOps, which are organized media operations to broadcast information to influence the "sentiment" (e.g. emotions, motives, objective reasoning) of large masses, such as a population or the politics of governments.
PsyOps is defined by the U.S. military as, "planned operations to convey selected truthful information and indicators to foreign audiences to influence their emotions, motives, objective reasoning, and ultimately, the behavior of their governments, organizations, groups, and individuals."
Social media gives governments a powerful instrument to reach critical masses instantly. Let's remind governments to consider PsyOps an important part of diplomatic, military and economic activities.
Distinguished theorists like Sun Tzu have highlighted the importance of waging psychological warfare:
"One need not destroy one's enemy. One only needs to destroy his willingness to engage…"
"For to win one hundred victories in one hundred battles is not the acme of skill. To subdue the enemy without fighting is the supreme excellence." - Sun Tzu
Different cyber technologies can be used to modify the sentiment on specific topics, such as web sites, virtual reality, blogs, video games, chat bots and of course social network platforms. The mission for PSYOP professionals is to take advantage of these cyber technologies exactly like their adversaries do to influence individuals to support their cause and to create an atmosphere of fear. For example, propaganda operations of cyber terrorists can use social media to recruit individuals and provide instruction on the operation to the followers.
To influence common sentiment of specific topics, intelligence agencies could arrange political and geopolitical campaigns using impressive amounts of data to induce information, fake or not, on masses. Social media networks are flooded with particularly crafted content and numerous discussions are opened to involve an increasing number of users. The discussions are structured with ad hoc comments and posts are used to sensitize and influence the user's perception of events.
In warfare scenarios, PsyOps are an essential component of information operations, having the specific goal of influencing adversarial human and automated decision process. Use of social networks allows the attacker to create anonymous or targeted profiles of real persons and publish material without any moderation and enables conducting PsyOps on targeted geographical regions or political parties. Let's consider also that modern cyber technologies provide efficient instruments to anonymize connection, making it impossible to distinguish government operations from voluntary contributions.
In summary, the principal advantages of using social media for PsyOps operations are:
- Social media could reach individuals difficult to reach in other ways.
- Flexible and persuasive technologies are interactive and make it possible for an attacker to tailor operations for highly dynamic situations.
- Cyber and persuasive technologies can grant anonymity.
- Automated PsyOps on social media are more persistent and efficient than humans.
- The information being presented to influence can be easily modified and changed in the cyber domain to address the target audience.
OSINT
Social media is correctly considered a powerful support to intelligence operations particularly because their analysis makes it possible to conduct Open-source intelligence (OSINT) operations to gather information. In the military sector, it's possible to collect information publicly available on strategic targets.
Last year, a representative of DARPA (Defense Advanced Research Projects Agency) declared:
"Understanding what affects such online behavior is needed for trend forecasting."
The use of social media platforms is also essential in composing complex analysis based on public data. Principal obstacles to OSINT activities are privacy and platform restrictions implemented to preserve privacy of individuals. Of course, OSINT techniques are useful only if the information on targets is available; if the desired information was never shared and it is not in the public domain, OSINT has no hope of discovering it.
Blogs, social-network sites, Wikis and any other information aggregators are rich mines of information publicly available and intelligence agencies constantly monitor them. The CIA and many other agencies use solutions daily to collect data from various social media outlets and news sources. They are generally referred with the term social media listening platforms. These solutions are very useful and allow the monitoring of billions of conversations and generating text analytics based on predefined criteria. Most advanced listening applications could determine the sentiment of the participants to a discussion with respect to some topic.
In 2010, the U.S. Department of Homeland Security discovered that Jihad and Mujahideen terrorist groups increasingly use Facebook for propaganda purposes and as a platform for exchanging tactical information such as reconnaissance targeting. Terrorist groups also used Facebook to provide links to outside radical forums that give instructions on the use of anonymizing services such as Tor to mask true identities.
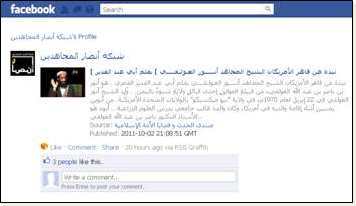
Figure 3 - Use of Facebook for propaganda by Jihad and Mujahideen terrorist groups
Chinese, Russian and US governments are massively investing in monitoring technology. The NSA is building the country's biggest spy center, named Utah Data Center, with the purpose of intercepting, deciphering, and analyzing the world's communications using every kind of transmission. The center will have a final cost of $2 billion and should be operational in September 2013. The Pentagon is searching for software that will automatically sift social media platforms to implement early warning mechanisms. Monitoring of social media for OSINT purposes is not so simple; we must consider that social media users are very dynamic and each individual usually has different profiles on various platforms making cross analysis much harder.
Data mining in social media
The data mining of social media is an activity often conducted by intelligence circles and militias. Many free services can help military analysts to see trends in different countries for specific events and news, like protests and social movements.
Everything on the Internet could be subject to data mining practices and social networks represent a relevant portion of data circulating on the web, making them sources of great interest for any kind of analysis. Social media in many cases not only provide raw data for investigation, but also relationships between subsets of information, simplifying mining activities.
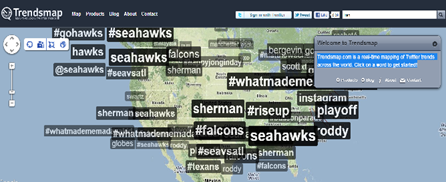
One example of this is Trendsmap.com, a real-time mapping of Twitter trends across the world.


Services such as www.recordedfuture.com can help the military to analyze data with so called prediction by mining big data collected from multiple open sources including social media. This could be very useful for intelligence gathering and prediction (especially, for example, when one political leader visits another country and etc).
Malware-based cyber attacks
Malware authors are very interested on the use of social media platforms mainly because they could spread malicious code to a wide audience who have low awareness on principal cyber threats.
In a military context, the use of social media could allow attackers to recruit a large number of bots to conduct a successful offensive against critical targets (e.g. critical infrastructures). Another advantage in exploiting social media platforms is the possibility to target groups of individuals of a selected community who share particular attitudes and habits, typically for cyber espionage purposes. According to the IBM X-Force 2012 Mid-year Trend and Risk Report, social networks have been the dominant targets of email phishing for more than two years, and drive-by downloads are becoming the principal method of infection.
In the last couple of years, specially crafted malware have been spread through social media allowing large scale attacks as well as APT attacks. Social network platforms have been used for bot recruiting and also for hiding the command and control infrastructure and related traffic.
Malicious codes that hit social media could be grouped into the following categories:
- Social network account-stealing malware propose fake authentication forms for cyber espionage purposes. In many cases, so simple a schema is enough for gathering account credentials and other personal information such as e-mail info and phone numbers.
- Binary/scripting malware on 3rd party web-sites for distribution of targeted malware are like backdoors through the vulnerabilities in internet browser plugins.
Both categories are very common and largely used by cyber criminals, but they could also be implemented by groups of state-sponsored hackers to infect large number of machines, to build up a botnet to involve in a cyber-attack such as a DDoS or to conduct an APT attack.
The most popular example of social malware that could be analyzed to understand the schema of attack on a social network is Koobface, a multi-platform malware that targeted users of the social networking websites Facebook, MySpace and Twitter. Koobface propagates through popular social networking sites by spamming the platforms with a lot of infected URLs that point to compromised sites. When users click on those links, proposed for example through a platform message, he is redirected to a compromised site used to exploit a vulnerability in his browser and allow malware downloading on the victim's PC.
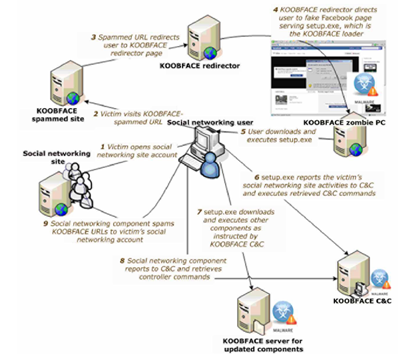
Figure 6 - Koobface schema
Social media to host C&C server
What about hiding malware control structure inside social networks?
Despite IRC networks having been surely the most common malware command-and-control model, recently many bootmasters are beginning to use social networks such as Facebook and Twitter as C&C. The choice is a winner and makes it hard to detect botnet activities. The interactions with social networking sites can be easily automated and "malicious" traffic directed to social media platforms is hard to identify due to large volumes. Attackers can set up a network of fake profiles on a social network and use them to post a specific set of encrypted commands to malware. The infected machine queries the "bootmaster" profile for new commands, but botnet having C&C in social media is extremely resilient and allows malware to run for long periods of time.
The attackers have improved their control techniques over time. Some malicious agents in fact don't limit their activity to just interpreting messages from social networking but also receive commands hidden inside a picture posted by a profile related to the bootmaster.
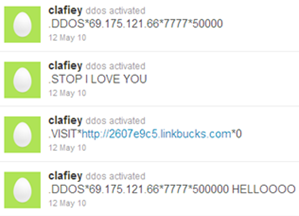
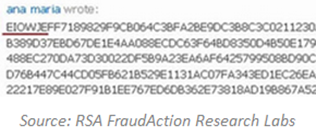
Figure 7 - Example Botnet based on Social Networks
Cyber espionage
One of the principal military use of social media is cyber espionage. Most popular techniques include:
- Replacement of identity: the ability to impersonate another user to acquire information.
- Identity spoofing: the creation of a fake profile that does not match any existing person.
- Malware-based attacks: use of malicious code to compromise a victim's machine and steal sensitive information. Sharing a link on a compromised website could allow an attacker to exploit vulnerability in a user's browser to gain control of its PC.
Cyber espionage through social media (facts, statistics, and technologies) is essentially based on data mining through the linked networks of contacts. The use of social media can be useful for cyber espionage and cyber intelligence in the preparation stage for PSYOPS/CYBEROPS, for reconnaissance (intelligence), and for targeted regions (like a group of persons, or political party, journalists and etc., or the employees of a targeted company and etc.).
Services such as Twitter are already commonly used for geopolitical analysis of so called "protest activities" in different countries, a very useful military segment. Adopting data mining techniques for contacts and connections analysis makes it possible to establish the relationship between different persons as a part of cyber intelligence operation. It also helps to gather private contacts of different persons who publish it only to a very close group of people. The following are two of the most interesting cases of cyber espionage conducted using social media platforms:
- NATO'S most senior commander was at the center of a major security alert when a series of his colleagues fell for a fake Facebook account opened in his name - apparently by Chinese spies. (The Telegraph)
- In May 2012, a few days before the second round of the presidential election won by Hollande, the President's office was infected by Flame malware. The attack against the President's office was of a spear phishing type that used the popular social network Facebook to spread the malware. The attackers shared a link to an infected website that was a replica of the Elysee's intranet, and used it to infect the machines and also to gather user credentials. All the machines that were part of the presidential network, including a number of Sarkozy's closest collaborators, were infected by the Flame agent.
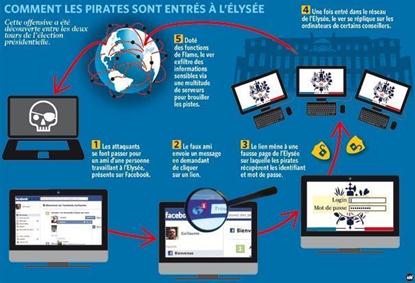
Figure 8 - Attack to President's office occurred in May 2012
Conclusions
Social media platforms have assumed a fundamental role in our society. Every day, billions of people share information, documents and any kind of content through these platforms. It is natural that they have become an object of interest for cyber criminals and intelligence agencies.
Undoubtedly, social media is of strategic importance for military sectors, as they offer a mine of information that could be analyzed using different axes of analysis providing efficient and reliable instruments for the study of realities of interest. Both defense and offense could take advantage of social media introduction. Social media could be, in fact, used as powerful tool for information gathering, cyber espionage and also as an active component in a botnet infrastructure.
Though social media is also a resource to preserve from attacks, its military use inevitably leads to a widening of the attack surface. Quite differently from other domains, the military has to deal with an area without perimeter that is difficult to protect.
Rapid technological evolution makes surveillance systems obsolete in a short time. It is necessary to spend a greater effort for the establishment of early warning and security intelligence systems to identify cyber threats, but other improvements must take place first.
The military needs an opening to social media, but it has to be consciously made. Military personnel and their families must be instructed on how to manage their exposure to social platforms. Social media platforms are powerful resources that can carry with them an incredible number of threats, so it's best to never let your guard down.
References
http://www.flintstudio.com/blog/social-media-stats-2012/#.UP21YCd2SSo
http://www.defense.gov/home/features/2009/0709_socialmedia/
http://www.dtic.mil/cgi-bin/GetTRDoc?AD=ADA519576






