SkyDog Con CTF - Catch Me If You Can

In this challenge there are eight flags are in the form of flag {MD5 Hash} such as flag{1a79a4d60de6718e8e5b326e338ae533}. We hosted the VM in virtualbox disabled USB 2.0 before booting up the VM.

What should you learn next?
We ran nmap on the target IP and found 3 open ports on it.
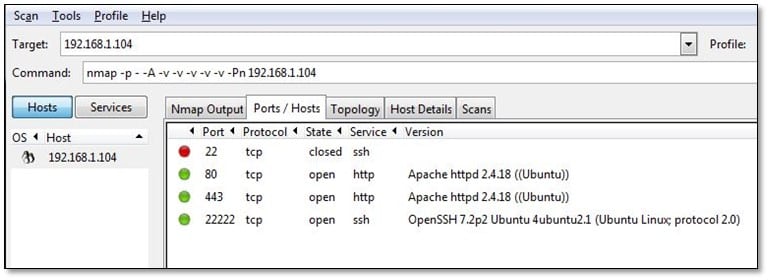
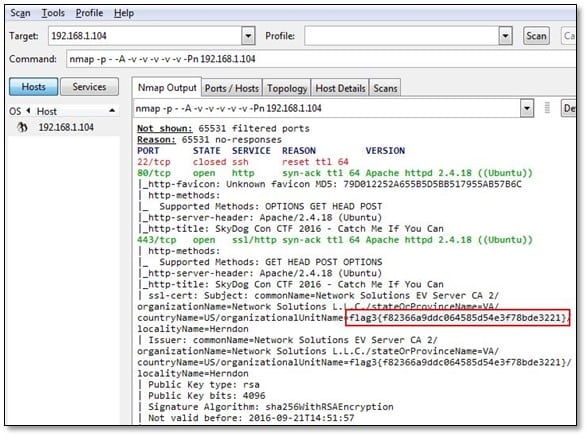
We noticed in the ssl certificate we found flag number 3 so we are not going to investigate this one we will start from flag 1 challenge.
Flag #1 Don't go Home Frank! There's a Hex on Your House.
We opened the IP from the browser, and we found web page over there. As it is mentioned in the challenge, there is a hex, so we start looking for a hex value on the web page.

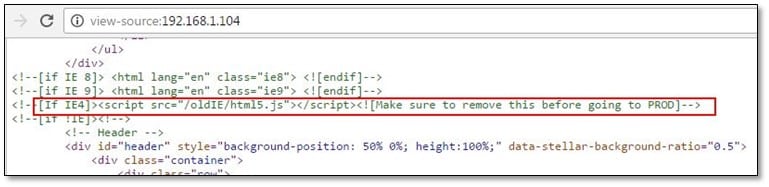
After looking into the view source of the web page, we found a commented js file where it was mentioned that to remove the js files before deploying it on the production server.
After opening the js file location from the browser, we found the hex which was commented in the js file.
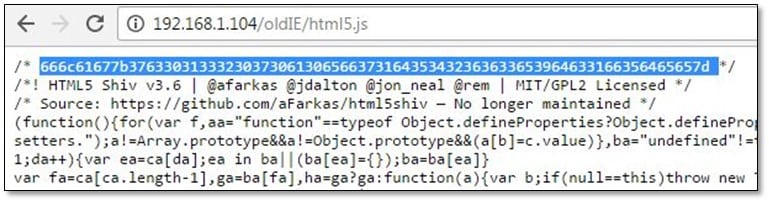
We decoded the hex into asci text, and we got our first flag.
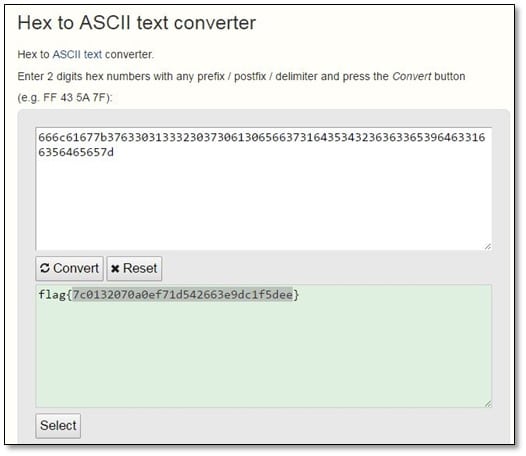
We cracked the md5 value from the flag, and we found the result was nmap.
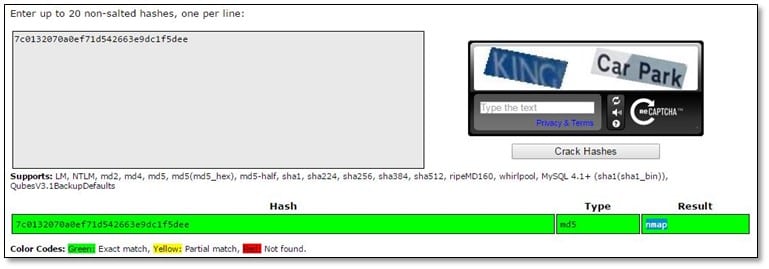
Flag #2 Obscurity or Security?
During the nmap scan we found SSH was running on port 22222 so tried to connect with it as root user and we found the second flag in the SSH banner.
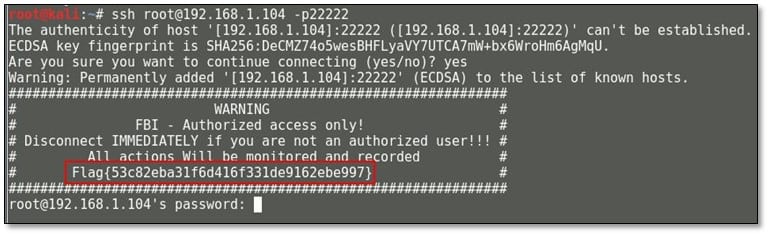
Ok so now we know the importance of looking up the MD5 hashes for additional clues. So 53c82eba31f6d416f331de9162ebe997 = "encrypt".
Flag #3 Be Careful Agent, Frank Has Been Known to Intercept Traffic Our Traffic.
So flag 3 we have already found in SSL certificate in our nmap scan, and now we will decrypt the md5 value of that flag, and the output was "personnel."
Flag #4 A Good Agent is Hard to Find.
From the clue which we have found from flag 3 we used it as a directory in the URL and we got access denied error and it was saying that resource was not accessed from FBI workstation.
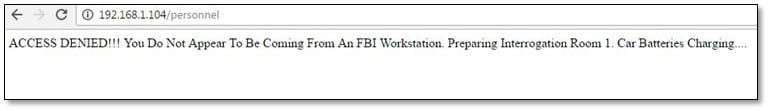
After spending some time on directory enumeration, we didn't found anything from that directory, and again we start looking that js file from where we have found the first flag, and we start finding the FBI keyword from that js file, and we found something interesting from there.
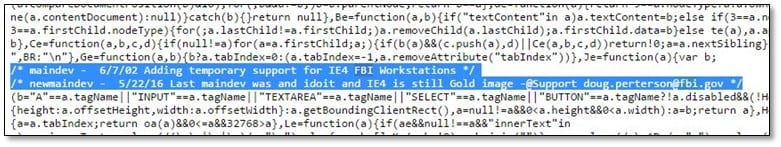
We found that IE4 was mentioned over there and also we found an FBI user email address. Now by using burp we changed the user-agent value with IE4's value and then tried to access the personnel directory, and it was accessible.
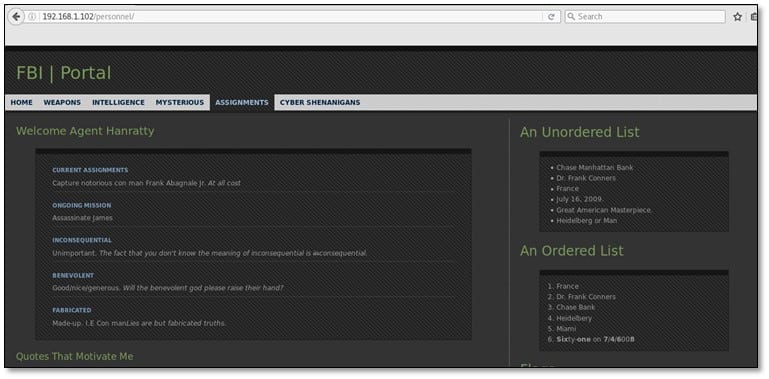
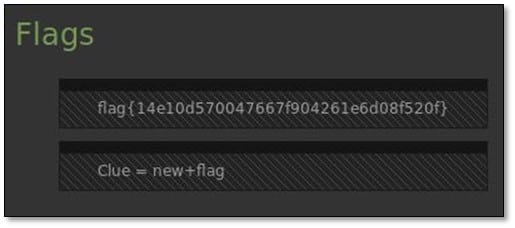
We found the 4th flag on the same page and also hint for our next flag which was clue=new+flag. So after decoding the md5 value we got the output which was "evidence," so the clue will be new+evidence.
Flag#5 – "The Devil is in the Details – Or is it Dialogue? Either Way, if it's Simple, Guessable, or Personal it Goes Against Best Practices."
The clue "newevidence" which we got from flag 4 we tried to access it as a directory from the URL and it was asking for HTTP authentication.
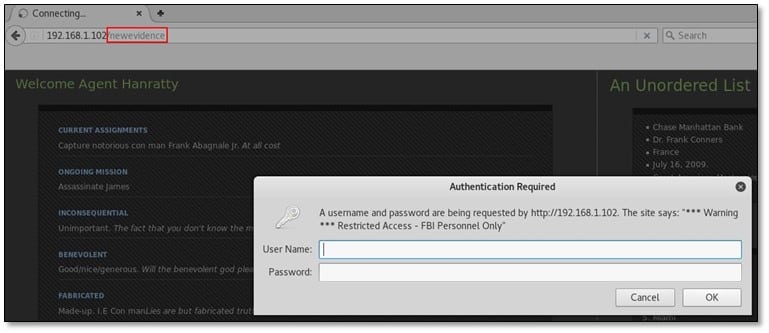
The Personnel page welcome in as Agent Hanratty, and IMDB tells me that character's first name was Carl, so given the username above we know the user will be carl.hanratty we guessed this username format from the FBI user which we have found from the js file. The password is hinted to be personal info, but there's nothing on the page we just unlocked, so we searched on Google, but that character was only based on a real person, so I watched the film and pretty much typed in anything he said that might help.
Eventually, it worked, with his daughter's name "Grace" being the password. I later searched for the name to see if I could've saved time watching the film, and it was indeed in the IMDB trivia section, but watching it helped me a lot more in a later flag.
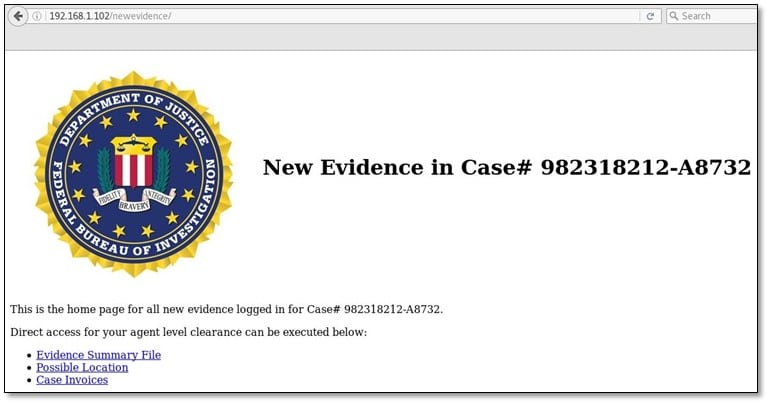
After clicking the evidence summary file we got our 5th flag and the md5 value after decoding was "panam."
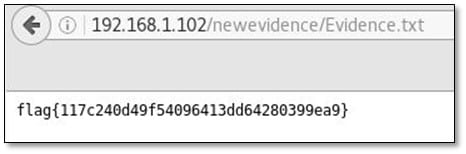
Flag#6 – "Where in the World is Frank?"
We got an image from the new evidence file and saved the image in our system.
And we got a pdf invoice file from case invoice link.
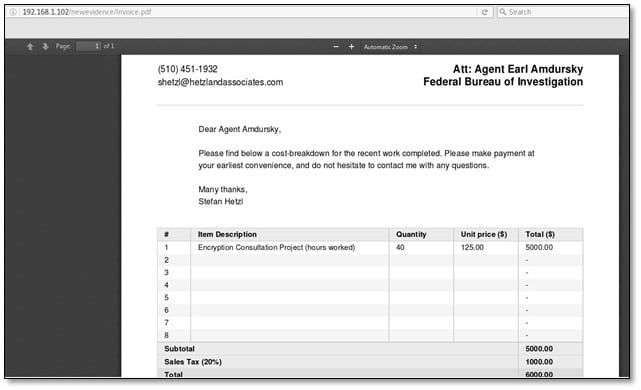
After looking at the Invoice.pdf a little closer. So the invoice is for an "Encryption Consultation Project" from someone named Stefan Hetzl. A Google search for "stefan hetzl encryption" reveals that Stefan Hetzl is the author of Steghide. We used steghide tool for extracting information from an image file, and it was asking for a password, so we used the 5th flag hash output as password which was "panam."
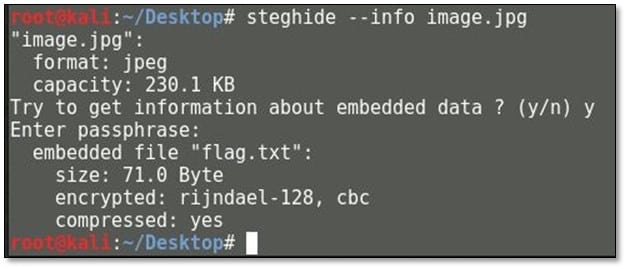
Steghide shows that there's a file flag.txt embedded in the image. So now it's time to extract it.
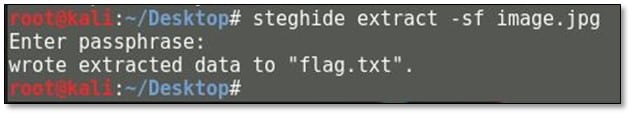
We got our 6th flag and a clue from the extracted text file.
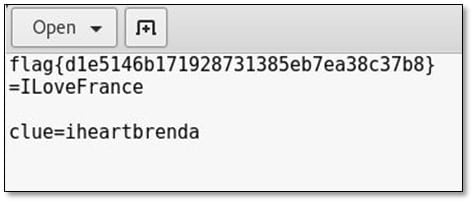
Flag#7 – "Frank Was Caught on Camera Cashing Checks and Yelling – I'm The Fastest Man Alive!"
Google search showed that the 'fastest man alive' clue was potentially talking about the Flash, also known as Barry Allen. Google further turned up that Barry Allen was an alias used by Frank Abagnale in the movie to trick the FBI agent tracking him. So we created a list of usernames such as theflash, flash, barry, barryallen, flashbarry etc. and used the clue "iheartbrenda" as the password for login in into the ssh and fortunately, the correct username was barryallen.
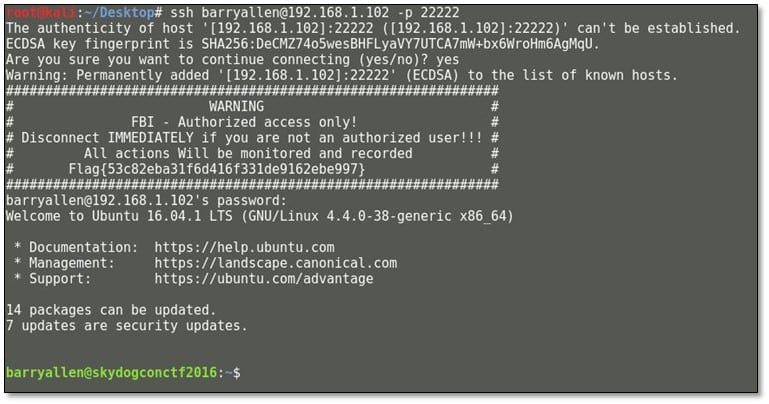
After login, we browsed the directory, and we found our 7th flag there. The md5 output was "theflash."
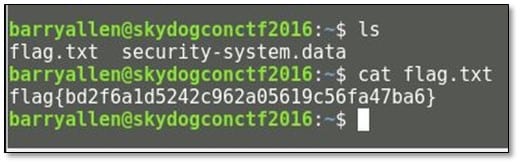
In that same directory, we noticed there was one more file with data extension, and we downloaded that file by using SCP tool.
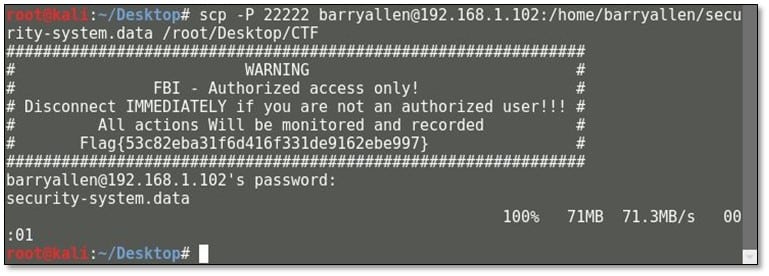
We changed the file extension to zip and extracted the file by using unzip tool.
After unzipping the file, we found a memory dump, so we used volatility memory forensic framework for analyzing the dump file.
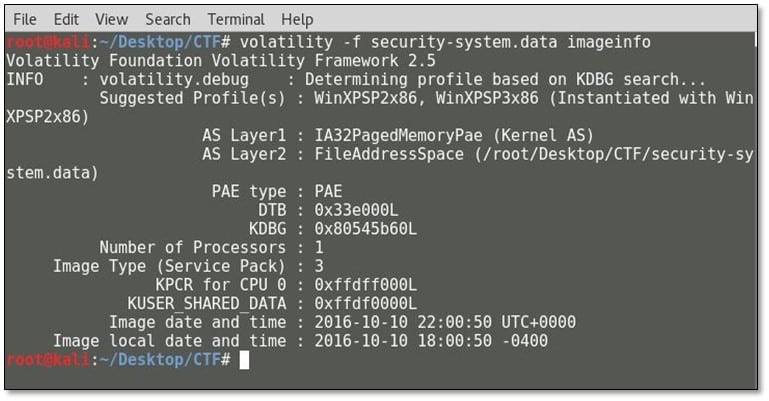
By using the imageinfo plugin, it revealed some interesting information such as it is suggesting OS profile Windows XP SP2. We again ran the tool with the suggested profile with iehistory profile which will reveal the browsing history.
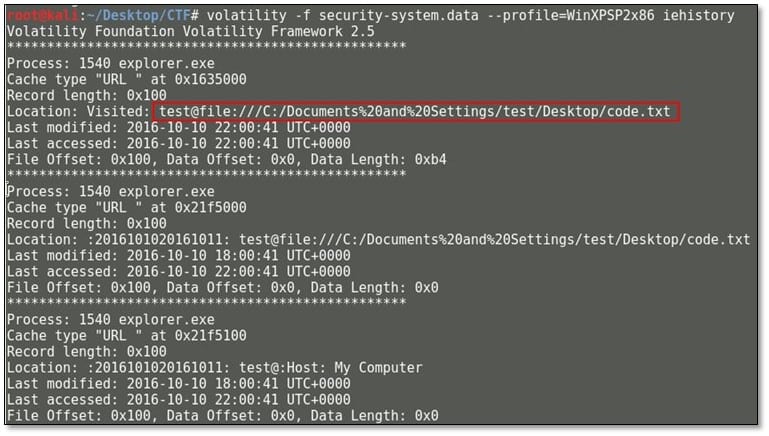
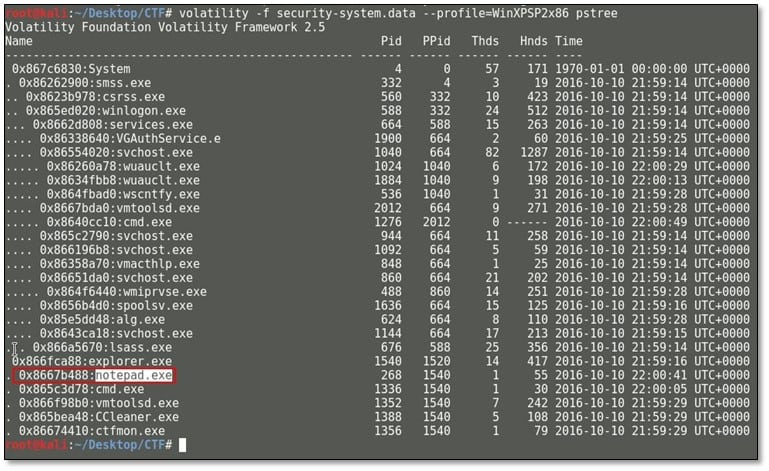
In the visited location section, we noticed that code.txt file was accessed from Desktop. So for editing the text file user must have opened it from notepad which can be extracted from the running process. By using the pstree plugin, we found all running processes where we have found the notepad.exe was running.
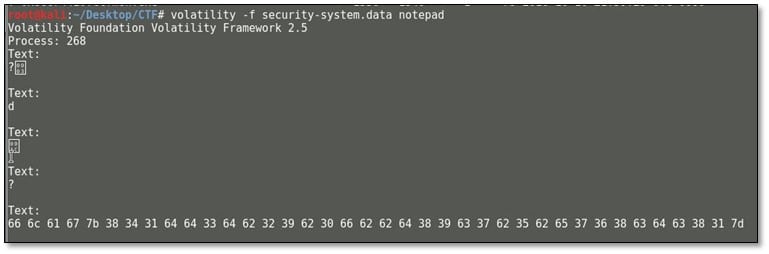
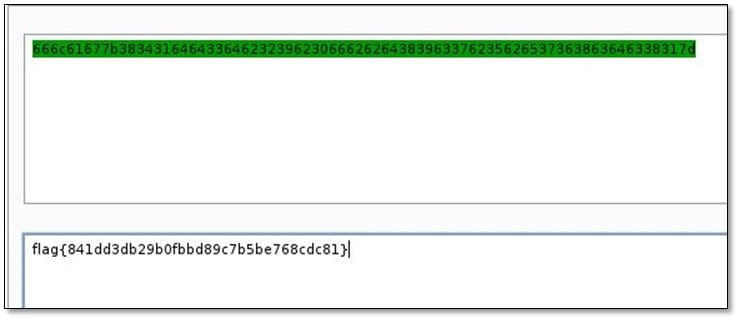
Again ran the tool with notepad switch and found the hex in the text. Decoded the hex in text format and we got our last 8th flag.

What should you learn next?
References: https://www.vulnhub.com/entry/skydog-2016-catch-me-if-you-can,166/



