“Robin Hood” Ransomware and Psychological Manipulation Techniques
1. Introduction
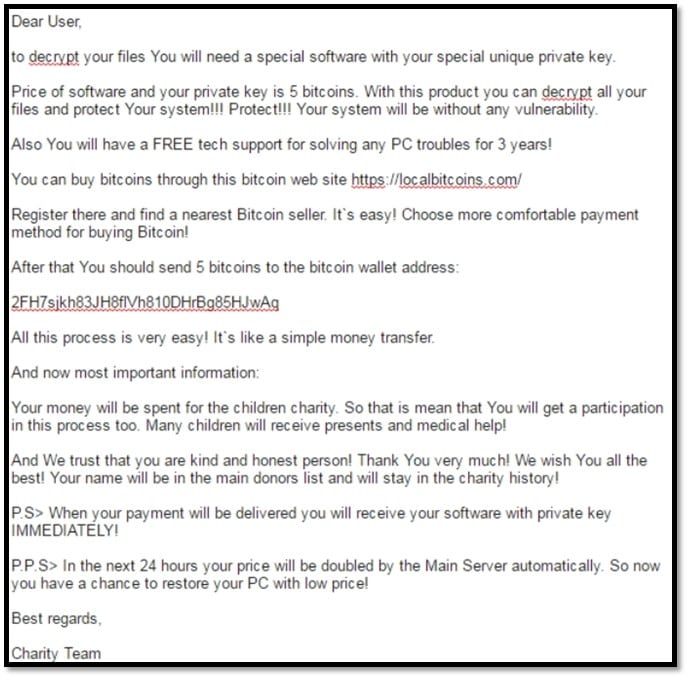
In 2016, the ransomware CryptMix gained popularity. CryptMix is based on source code of other infamous types of malware, such as CryptoWall 3.0, CryptoWall 4.0 and CryptXXX. In comparison with its predecessors, CryptMix claims that the collected ransom fees will be donated to children. More specifically, the ransomware states: "Many children will receive presents and medical help! And We trust that you are kind and honest person! Thank You very much! We wish You all the best! Your name will be in the main donors list and will stay in the charity history!" Below, you can see a screenshot of the entire message shown by CryptMix to the users of the computers affected by it.
Phishing simulations & training
In this article, we examine the reason for the appearance of "Robin Hood" ransomware (Section 2), discuss psychological manipulation techniques often used by ransomware creators (Section 3), and provide recommendations on how to prevent being infected with "Robin Hood" ransomware (see Section 4). Finally, a conclusion is drawn (see Section 5).
2. The reason for the appearance of "Robin Hood" ransomware
"Robin Hood" ransomware usually does not specify the name of charities allegedly benefiting from cyber-crimes. Hence, we cannot find out with certainty the reason for the appearance of this type of ransomware. However, it is highly unlikely that at least a part of the collected ransom will effectively be transferred to charities. In this regard, a representative of Heimdal Security (a Danish seller of cyber security software) noted: "While there's no way of telling the truth (at the moment), we can hardly trust cyber criminals to have a kind and generous side to them."
In our opinion, the reason for the appearance of "Robin Hood" ransomware is the reciprocity principle, i.e., a social rule that says that people should repay what they have received from other people. Sellers of various products and advertisers often utilize the reciprocity principle to sell their products. The usual trick is giving a free product to potential customers to persuade the customer to purchase another product.
The creators of "Robin Hood" ransomware ask their victims to reciprocate the "good intentions" of the fraudsters by paying the ransom. It is worth mentioning that many fraudsters use children for illicit purposes.
The World Health Organization reports that hundreds of millions of children experience psychological, sexual, or physical violence on a daily basis. Considering this information, one can normally doubt the good-heartedness of the crooks behind CryptMix.
"Robin Hood" ransomware uses not only the reciprocity principle but also other manipulative techniques, such as limited-time offers and the provision of non-existent extra value. For example, similarly to other types of malware, CryptMix states that the amount of the requested ransom will increase by 100% if the infected user does not pay the initially requested amount within a time period of 24 hours commencing on the date of the infection. Also, CryptMix offers three years of technical support to ransom-payers. It is hard to believe that criminals will provide technical support to their victims.
3. Psychological manipulation techniques
As shown in the previous section, creators of "Robin Hood" type of ransomware seem to be well aware of psychological manipulation techniques which can be used to persuade their victims to pay the ransom. In this section, we examine ten other manipulation techniques often employed by ransomware creators. Each of these techniques allows crooks to advance their interests at the expense of others.
A: Concealing aggressive behavior
By arguing that the ransom is collected for charity, fraudsters intend to mitigate the active intrusion in the personal space of the affected persons.
B: Knowing the vulnerabilities of the victim
Criminals know that they will hamper the normal operations of most organizations and individuals by restricting the access to their files or computers as most information nowadays is stored and processed digitally.
C: Superficial sympathy (also known as "crocodile tears")
Ransomware creators often show superficial sympathy aiming to mitigate the consequences of their aggressive behavior. For instance, CryptMix offers each victim the opportunity to decrypt one file free of charge.
D: Removing the victims from negative situations
Fraudsters know well that their victims will pay them for solutions, not for problems. That is why they create problems and simultaneously offer solutions to those problems. Such solutions may include decryption of encrypted files and access to blocked computers. It should be noted that creators of ransomware often do not fulfill their promises to decrypt the encrypted files. There are many online complaints of victims of CryptMix whose files were not decrypted although they paid substantial amounts of money (USD 5,000 – USD 10,000).
E: Creating a continuous situation of fear and doubt
Some ransomware programs aim to create a continuous situation of fear and doubt to encourage the victim to persist providing their creators with benefits. For example, ransomware creators may ask ransom for each file individually or set prices depending on their opinion about the value of the files. Thus, the victim will be transformed in a regular payer of ransom, constantly fearing loss of important information.
F: Punishment
Ransomware programs often threaten the users affected by them that, if they do not pay the requested ransom, they will never be able to gain access to their files. In this regard, CryptMix notes that the requested ransom sum will double if the victim does not pay it within a time period of 24 hours.
G: Establish dominance or superiority
Ransomware programs typically encrypt the files of the victims in such a way as to eliminate the possibility of recovery without paying the ransom. Thus, CryptMix informs the infected users that their files can be decrypted only with the help of the private key and a decrypt program owned by the creators of CryptMix. This statement is incorrect as there are publicly available decryption tools which allow the victims of CryptMix to decrypt their files free of charge.
H: Minimization
Manipulators often argue that their behavior is not harmful or irresponsible. By way of illustration, CryptMix claims that all files of the infected users were "protected by a strong encryption with RSA-2048" instead of informing them that their files were unlawfully made inaccessible.
I: Shaming
Fraudsters often use sarcasm to increase the self-doubt and fear in the victim. For example, CryptMix points out that: "So, there are two ways you can choose: wait for a miracle and get your price doubled, or start obtaining BITCOIN NOW! and restore your data easy way."
J: Bandwagon Effect
Ransomware creators may conform the victim by claiming that many people have paid the ransom and, therefore, he/she should pay it as well.
4. Recommendations on how to prevent being infected with "Robin Hood" ransomware
The following four steps may prevent individuals and organizations from being affected with "Robin Hood" type of ransomware.
A: Identifying phishing lures
Since the developers of "Robin Hood" ransomware are usually familiar with psychological manipulation techniques discussed above, they often invent highly successful lures to catch unwary users. In this context, it is worth mentioning that CryptMix infects computers of users who access malicious websites. Those websites target their visitors with exploit kits that leverage the vulnerabilities in their browsers.
B: Backup
As discussed in Section 3, one of the manipulation techniques commonly used by ransomware creators relies on the existence of vulnerabilities. By backing up important data, individuals and organizations can decrease their vulnerability to ransomware attacks. As Anup Ghosh, CEO of the security firm Invincea, states: "If the backups are done offline, and the backup is not reachable from the machine that is infected, then you're fine."
C: Use proper anti-ransomware software
In addition to visiting infected websites, ransomware is also often distributed through malicious attachments. There are many ways to check if a message containing an attachment is legitimate (e.g., verifying the origin of the sender, checking the links contained in the message, and assessing the content of the message). However, due to increased sophistication of malware, even security experts may overlook a malicious attachment. That is why the use of a proper anti-ransomware application is of utmost importance to prevent infection after a human mistake. In this regard, Mr. Ghosh wrote: "Users will open attachments, they will visit sites that are infected, and when that happens, you just need to make sure that your security technology protects you."
D: Disconnect the infected systems
Ransomware often spreads itself within the network of the infected computers. That is why organizations willing to mitigate the consequences of ransomware need to disconnect the infected computers as soon as possible. In his "Ransomware Hostage Rescue Manual," Adam Alessandrini suggests the following technique: "Immediately disconnect the infected computer from any network it is on. Turn off any wireless capabilities such as Wi-Fi or Bluetooth. Unplug any storage devices such as USB or external hard drives. Do not erase anything or "clean up" any files or antivirus. This is important for later steps. Simply unplug the computer from the network and any other storage devices."
5. Conclusions
Robin Hood is a legendary archer in English folklore who was "robbing from the rich and giving to the poor." Many centuries after the appearance of the legend of Robin Hood, new types of ransomware applications promise to give the collected ransom to charities. However, the intentions of the creators of such applications seem to be less benevolent than the intentions of the mythical English hero.
There is no evidence showing that ransom sums collected from "Robin Hood" ransomware go to charities. Taking into account the fact that the developers of such ransomware are aware of and apply various psychological manipulation techniques, one can reasonably doubt their good intentions.
Individuals and organizations willing to protect themselves against "Robin Hood" ransomware need to be aware of the manipulation techniques commonly used by fraudsters and the steps they can take to prevent ransomware infections.

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
Last but not least, persons who are seriously concerned about the consequences of ransomware attacks can purchase cyber-insurance policies. In general, they cover expenses related to forensic investigations, business losses, expenses for notifying clients about data breaches, legal expenses, and cyber extortion costs.
References
- '3,00,000 children across India are forced to beg by cartels: Report', DNA India, 1 June 2016. Available at http://www.dnaindia.com/india/report-300000-children-across-india-are-forced-to-beg-by-cartels-report-2218856.
- Alessandrini, A., 'Ransomware Hostage Rescue Manual', Wired. Available at https://www.wired.com/wp-content/uploads/2016/03/RansomwareManual-1.pdf.
- Cimpanu, C., 'New CryptMix Ransomware Promises to Give Money to a Children's Charity', Softpedia, 4 May 2016. Available at http://news.softpedia.com/news/new-cryptmix-ransomware-promises-to-give-money-to-a-children-s-charity-503688.shtml.
- Dimov, D., Juzenaite, R., 'Insurance Against Ransomware Threats', InfoSec Institute, 24 February 2017. Available at https://resources.infosecinstitute.com/insurance-ransomware-threats.
- 'CryptoMix: Avast adds a new free decryption tool to its collection'. Avast.com, 21 February 2017. Available at https://blog.avast.com/cryptomix-avast-adds-a-new-free-decryption-tool-to-its-collection.
- Ducklin, P., 'Data-stealing CryPy ransomware raises the spectre of variable pricing for files', Naked Security, 18 October 2016. Available at https://nakedsecurity.sophos.com/2016/10/18/data-stealing-crpy-ransomware.
- Dunn, J. E., 'The top 10 phishing lures of 2015', TechWorld, 17 July 2015. Available at http://www.techworld.com/security/top-10-phishing-lures-of-2015-3620099.
- GoldSparrow, 'CryptMix Ransomware', Enigma Software. Available at https://www.enigmasoftware.com/cryptmixransomware-removal.
- Green, J., 'This Computer Virus Claims Ransom but Its Purpose Is to Donate for Charity", The Tech News, 9 May 2016. Available at http://thetechnews.com/2016/05/09/this-computer-virus-claims-ransom-but-its-purpose-is-to-donate-for-charity.
- 'INSPIRE: Seven strategies for Ending Violence Against Children', a report published by the World Health Organization. Available at http://www.who.int/violence_injury_prevention/violence/inspire/en/.
- Leyden, J., 'Ransomware Grifters Offer to Donate Proceeds of Crime to Charity', The Register, 6 May 2016. Available at https://www.theregister.co.uk/2016/05/06/charity_ransomware_scam.
- Liska, A., Gallo, T., 'Ransomware: Defending Against Digital Extortion', O'Reilly Media, Inc, 2016.
- 'Psychological Manipulation', Wikipedia. Available at https://en.wikipedia.org/wiki/Psychological_manipulation.
- 'The Robin Hood Style Bitcoin Ransomware', AltCoinToday, 9 May 2016. Available at http://www.altcointoday.com/robin-hood-bitcoin-ransomware.
- Tuttle, B., 'Why 'For a Limited Time Only!' Drives Shoppers to Spend Like Crazy ', Time, 15 December 2010. Available at http://business.time.com/2010/12/15/why-for-a-limited-time-only-makes-shoppers-spend-like-crazy.
- 'Why is the child in hands of the beggar always sleeping?', BBN Community. Available at http://www.bbncommunity.com/dose-child-hands-beggar-always-sleeping-2.
-
Zetter, K., '4 Ways to Protect Against the Very Real Threat of Ransomware', Wired, 13 May 2016. Available at https://www.wired.com/2016/05/4-ways-protect-ransomware-youre-target.
Co-Author
 Rasa Juzenaite works as a project manager at Dimov Internet Law Consulting (www.dimov.pro), a legal consultancy based in Belgium. She has a background in digital culture with a focus on digital humanities, social media, and digitization. Currently, she is pursuing an advanced Master's degree in IP & ICT Law.
Rasa Juzenaite works as a project manager at Dimov Internet Law Consulting (www.dimov.pro), a legal consultancy based in Belgium. She has a background in digital culture with a focus on digital humanities, social media, and digitization. Currently, she is pursuing an advanced Master's degree in IP & ICT Law.






