Quantum Cryptography
"Quantum cryptography uses photons and physics to generate cryptographic keys"
What is quantum cryptography?
Learn Applied Cryptography
Quantum cryptography is NOT a new algorithm to encrypt and decrypt data. Rather it is a technique of using photons to generate a cryptographic key and transmit it to a receiver using a suitable communication channel. A cryptographic key plays the most important role in cryptography; it is used to encrypt/decrypt data.
Types of cryptography
There are two types of cryptography:
-
Symmetric Cryptography
-
Asymmetric Cryptography
Symmetric Key Cryptography is also known as Secret Key Cryptography (SKC) where a key (any text, numbers, etc.) is used to encrypt data, and the same key is used to decrypt that data. The smallest change in the secret key will fail to decrypt an encrypted message. For example, text that is encrypted using AES encryption with key Infosec will fail to decrypt another cipher text which was encrypted using key INFOSEC.
Asymmetric Key Cryptography is also known as Public Key Cryptography (PKC) where two sets of keys are generated. One is called a public key and other is called a private key. A public key is used to encrypt data whereas a private key is used to decrypt that data. Similar to symmetric cryptography, the smallest change in any of the two keys will make them useless to get the original data. A benefit of asymmetric cryptography is that you can share the public key with the whole world so that they can use it to send you encrypted data. And the private key is stored safely with the owner and is used for decryption. One disadvantage of this type of cryptography is that if your private key is lost or leaked then you will have to generate a new pair of public and private keys.
Why do we need quantum cryptography?
Every new solution is made because of some problem we have with the current solution. The case is no different with this one. Let us see the problem first.
The problem with symmetric cryptography is that the same key is used to both encrypt and decrypt the messages. If for some reason that key is leaked to some third party, then it can be used to decrypt communication between two trusted devices or persons. In the worst case, the communication can be intercepted and altered. Today's huge computing power (these days even Xbox and PlayStation at homes have huge power) can be used to crack a key used in symmetric cryptography. Another major problem with this type of cryptography is how to decide which key to use and how to share between trusted devices or persons. Imagine a key has to be shared between India and America, then that communication too has to be secured before sharing the key.
Coming to the problem of asymmetric cryptography, it is not something we are facing right now, but seeing the pace of changing technology, we will be facing it soon. Most of the keys used in public key cryptography are at least 128-bit keys which are considered to be very strong. An attacker can easily get hold of the public key because it is shared by the user. But to generate a private key for that public key involves huge amounts of calculations with permutations and combinations. At present a supercomputer is what you need to crack a PKC and many years to complete it. But it will become pretty much possible with the use of quantum computers which use quantum physics to operate and have very high efficiency and computation speed. A quantum computer is a theoretical concept right now and will utilize atoms and molecules to perform computing at a very high speed.
According to Moore's Law, in an integrated circuit the number of transistors doubles every 2 years. It means that the speed of computing will increase to a very high level every two years. Right now Intel i7 processor integrated circuit has 1.4 billion transistors. Clearly, in the coming decades computing speed will increase and the age of quantum computers will become a reality.
Now from our above discussion it is very clear that the biggest problem with the current cryptographic techniques is keys and their security in transmission.
How does quantum cryptography work?
In quantum cryptography, the source sends a key to the receiver, and this key can be used to decrypt any future messages that are to be sent. When the key has been successfully sent and received, the next step is to send encrypted data to the receiver and let it decrypt and process that data.
Important: the key is the main part of cryptography and should be sent in a very secure manner.
Quantum cryptography has a different way of sending the key to the receiver. It uses photons to send a key.
What is a photon, and how it is used?
A photon is the smallest particle of light. It has three types of spins:
-
Horizontal
-
Vertical
-
Diagonal (Right and Left)
A photon has the capability to spin in all three states at the same time. How do we use it in cryptography? Another part of physics and photons is polarization. Polarization can be used to polarize (pass through a filter) a photon so that it has a particular spin, vertical or horizontal or diagonal. Polarization of a photon is performed using polarization filters.
Now comes Heisenberg's Uncertainty Principle, which states that it is impossible to measure together the speed and position of a particle with highest accuracy, and its state will change when measured. In other words, if an eavesdropper intercepts the transmitted photons and passes it through its polarizer, if it is wrong it will make the receiver get the wrong photon. Hence the interception of communication will get detected.
It means that if a photon is polarized using say X filter (Diagonal Polarization), then to get the original spin of the photon only X filter can be used. If a + filter (Rectilinear Polarization) is used on the photon, then it will either be absorbed by the filter or the polarized photon, will be of different spin than the original photon. For example, a horizontal spinning photon when passed through a wrong filter will lead to diagonal spin, which is incorrect.
The below table shows output spin for used polarization:
Polarization
Output Spin
How to send data using photons
One of the major concerns before using quantum cryptography is how to associate data with photons. This problem can be easily solved by assigning the spin of every photon as 0 or 1. Please see the sample table below:
Horizontal Spin
(--)
Vertical Spin
(|)
Left Diagonal Spin
()
Right Diagonal Spin
(/)
0
1
0
1
Imagine Alice applies polarizations on photons and gets the spin and keeps a note of it. Every spin has a value associated with it. Please refer to the table below:

Do note that Alice is able to find the spin of photon after polarization using four detectors (horizontal, vertical, right diagonal, left diagonal).
Now the key in binary format is: 0101100110101011
This binary data can be converted into other formats like string and integer, depending upon choice of the users involved in the communication. Let us assume Alice wants the key to be in integer format, so the key will be:

In real world implementation, the key should not be this short in length.
How to share and verify the key
In the above section, Alice applied polarization and calculated the value of the key, which will be transmitted to Bob. Note that transmission of these photons takes place in optical fiber cables.
Alice sends the polarized photons to Bob using a suitable communication channel. Bob is listening for incoming photons and randomly applies any polarization (rectilinear or diagonal) and keeps a note of applied polarization, spin and its value.
Now when the transmission has completed, Alice and Bob communicate on a public channel which needs not be encrypted. Bob tells Alice only the polarizations (not the spin or value) he applied in the exactly same sequence, and Alice only says YES/NO. This communication will be something like this:
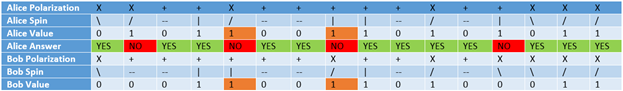
In the above communication, Bob gets to know the wrong polarizations. But do note that we have a problem here which is highlighted in orange color. See that Alice said polarization applied is wrong but the spin Bob received had the same bit value (1) as Alice's. But Bob has no way to find what value Alice has so he has no other way but to discard his results for wrong polarization.
After successful key transmission and fixing of wrong polarization, encrypted data can be sent and decrypted when received.
Communication interception
If a user is intercepting the communication between sender and receiver, then he will have to randomly apply polarization on the photons sent. After polarization, he will forward it to the original sender. But it is impossible for the eavesdropper to guess all polarizations correctly. So when Bob and Alice validate the polarizations, and Bob fails to decrypt the data, then the interception of communication will get detected.
Conclusion
Privacy and data security is right now of utmost importance to people. With quantum cryptography, secure transmission of data is possible, and chances of it being intercepted and altered are very low. This technology has been implemented in some areas. But is still under deeper research before being widely implemented.
Learn Applied Cryptography
Reference: http://science.howstuffworks.com/science-vs-myth/everyday-myths/quantum-cryptology.htm



