Purple Teaming: A Security-Testing Collaborative
Introduction
The Red Tem term was born in the military environment to represent the highly specialized groups, able to play the role of opponents in contrast to the defensive team, which is named Blue Team. The Red Team were using their skills, knowledge, and tools to develop the real attacks, which had to be detected and mitigated by a defensive measure represented by the Blue Team. The ultimate goal was to improve their defensive capabilities against someone who acts like a real enemy. With these concepts, it also applied in the cyber security area to indicate those activities that test the resilience of an Organization against real attacks and to test the effective detection capabilities.

11 courses, 8+ hours of training
Considering the evolution and popularity of real world attacks, Organizations need to develop their own approaches to penetration testing, with the view to evaluating the effective resilience against cyber attacks and close the gap between testing infrastructure and real attack scenarios.
A typical penetration test is characterized by a semi-automated network and vulnerability scanning, then an exploitability of the identified weaknesses and flaws. This approach provides a broad overview of the vulnerabilities and preventive controls implemented by the Organization, however, it is not able to assess the effective resistance against the current attacks, since they lack the typical components of a real attacker, such as malware, social engineering, exfiltration of information and persistence.
Comparison with Penetration Testing
Red Teaming activities presents several differences compared to Penetration Testing engagements, in particular:
- Goal, as previously described, the aim of this activity is to test resilience against real attacks, instead of gain an oversight of technical vulnerabilities.
- Scope, in Red Teaming practices all access paths, are in scope instead of predefined subset or applications.
- Testing, the focus of testing is oriented on detection and response of organization, in order to test the resilience.
- Tools, in Red Teaming activities, can be used all TTPs (Tool, Tactics, and Procedures) available to a potential attacker, also included custom malware and social engineering attacks.
- Post-exploitation, which is focused on breach critical assets and exfiltration of sensible data and information.
- Positioning, generally is a periodical exercise, instead of Penetration Testing, which is generally part of the development lifecycle.
Red Teaming approach
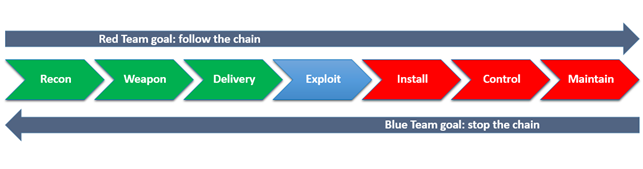
The Red Team has to be composed by the most skilled hackers and using state of the art technology to simulate real attackers. The approach used, should be oriented to the Cyber Kill Chain:
- Reconnaissance: footprinting and information gathering of the target (domains, email addresses, information, etc.) and determine attack methods.
- Weaponization: development phase of the attack methods selected, generally into deliverable malicious payload which contains the exploit and backdoor.
- Delivery: transmission of the attack via different attack vector (email, the web, social media, physical, etc.)
- Exploitation: exploiting of a technical or human vulnerability or misconfiguration.
- Installation: installing customized malware or backdoor, to gain the remote control of victim's system
- Control: establishing the C2 (Command & Control) channel throughout the network
- Maintenance: performing the actions to achieve actual goals inside the victim's network (lateral movement, exfiltration, etc.) and "make a persistence", to maintain the remote control.
Red + Blue = Purple Teaming
The Red Teaming activities are very useful to understand the real cyber resilience of an organization. However, there may be some inefficiencies. Typically, the two groups never speak: the red team is hired by the CSO (Chief Security Officer) or the equivalent of an organization with the goal to breach the infrastructure, without informing its own technical departments. After finishing this engagement, if the results and the follow-up of the walkthrough are not communicated to the blue team in a useful way, whenever the red team (or real cyber attacker) performs the analysis always succeed to break into the Organization.
To optimize the efficiency and effectiveness of effort by both groups, and provide valuable results of this activity, it has been defined a new concept, named Purple Teaming (the purple color is obtained by mixing blue and red colors). The goal of the Purple Teaming is the collaboration of offensive and defensive tactics: the offensive team should use all TTPs (Tactics, Techniques, and Procedures) available by the attacker and the defensive team should implement and improve their detection e response capabilities.
While the mission of Red Tem is to try to follow, through and through, the cyber kill chain, the Blue Team must be able to detect these intrusion attempts, in particular the lateral movement and privilege escalation events, with the aim to shorten the cyber kill chain in the earliest stage possible in order to avoid that the Red Team bring home the "crown jewels".
Generally, the defensive group is represented by incident responder, forensics analyst or SOC (Security Operation Center) analyst, which investigate on security events through a SIEM (Security Incident Event Management) and related security probes (IDS/IPS, Firewall, Anti-malware, etc.): it depends on the complexity of Organization and his implemented technologies.
The benefit of the Purple Teaming is in the synergy and mutual feedback of both groups, and the ability to engage the challenge, continually improving the detection capacity and response capabilities. Indeed, the cooperation should aim at continuous improvement, for the offensive and defensive tactics, and in particular, for the blue which should exploit this opportunity to expand their knowledge of the techniques used by the real cyber attackers (Tactics, Techniques, and Procedures).
Furthermore, it is one of the most important indicators of this exercise; it is represented by mensuration of mean time to detect (MTTD) and mean time to recovery (MTTR) for the defense team, which should be improved for each attack performed.
Conclusion
Over the past, they have grown almost exponentially new types of cyber-attacks, more complex, such as the new evasive malware or the famous "APT" (Advanced Persistence Threat) that can create and customize the attack vectors to be fully functioning with the target environment.
Nowadays, the simple activities of Vulnerability Assessment and Penetration Testing are not sufficient to meet and mitigate the threat of a cyber-attack, since in many cases the weakest link in the security chain is the human factor and the use of the technologies in a not secure way.
The Red Teaming activities, allow getting an insight into the Organization resilience against real cyber criminals attacks that are relevant to it and improvement of the detective and response capabilities of defense security team.

11 courses, 8+ hours of training
Finally, the activities of Red Teaming can evolve in Purple Teaming, collaborate two teams to optimize the effort of the groups and the results and evaluate the return on investments of an Organization about information security.



