How to Protect Your Right to Personal Identity in the Digital Era
As stated by the FBI's Internet Crime Complaint Center (IC3), identity theft "occurs when someone appropriates another's personal information without their knowledge to commit theft or fraud."
Identity theft is not a new occurrence. From biblical times people impersonate other people. The magnitude of identity theft nowadays, however, is astounding. Javelin Strategy & Research reported that more than 15.4 million American citizens fell victim to this outbreak in 2016 alone, with incurred costs of $16 billion.
Phishing simulations & training
While this article will mainly focus on the most effective ways to tackle the identity crimes, you will also have the opportunity to acquaint yourself with some real-life cases of identity theft, which will allow you to apprehend better the negative circumstances that ensue as a result of this crime.
I. Identity Theft: Types and Techniques
1.1 Most common variations of identity theft are:
Financial identity theft – criminals have illegal access to a victim's bank accounts or credit cards.
Popular ways to cash in on stolen identities is through purchase transactions performed online or via phone without the cardholder having to physically present the card to complete the purchase (40 % increase in 2016 compared to 2015).
Another method that cyber criminals use to convert identity information into gold is called account takeover fraud. The thieves merely use a victim's login information to access his accounts (rose 31% in 2016 compared to the previous year) or to open new accounts in his name (20 % increase in 2016 compared to 2015).
Tax-related identity theft – an impostor uses a stolen Social Security Number (SSN) to file a false tax return with the IRS (Internal Revenue Service).

Medical identity theft – a victim's personal information (e.g., health insurance member numbers) will facilitate the theft of medical services at the expense of the victim. Not surprisingly, the World Health Organization labels it in outspoken terms as "the information crime that can kill you."
Child identity theft – there are many cases of criminals misusing a child's SSN for fraudulent activities: to open bank accounts, apply for government benefits, you name it.
 A Pennsylvania man was charged with stealing the identity of a Texas baby who died in 1972.
A Pennsylvania man was charged with stealing the identity of a Texas baby who died in 1972. The Salt Lake City-based journalist Don Hudson tells a story of child identity theft, a story about an 8-year-old boy whose SSN showed a decent income earned throughout the first years of his life. The following quote is from his article: [The child's mother:] "They told me that wages were being reported to my 3-year-olds social security number. It took two and half years to find [the perpetrator]. "
The Salt Lake City-based journalist Don Hudson tells a story of child identity theft, a story about an 8-year-old boy whose SSN showed a decent income earned throughout the first years of his life. The following quote is from his article: [The child's mother:] "They told me that wages were being reported to my 3-year-olds social security number. It took two and half years to find [the perpetrator]. "A characteristic feature of this type of identity theft is the fact that the harm may remain unnoticed for a very long time. Furthermore, almost always the perpetrator of this kind of identity theft is a friend or a family member, which is a harsh reality of life you may have difficulties to come to terms with.
Senior identity theft – older adults are high on the list of preferred targets of all kinds of scams.
12,730 cases of identity fraud were registered with the Scamwatch website in 2016. Almost one-third of all people to report having their identity stolen are over the age of 55. Because senior citizens are often in contact with insurance providers and medical professionals, they may be used to divulge personal data. Also, they are more likely not to be familiar with the latest scamming methods.

Al Pascual is a senior vice president and research director for Javelin who is familiar with the tendencies in identity theft. In his opinion, tech-savvy consumers are more likely to notice some warning signs of a fraud quickly, thereby minimizing the financial damage.
Synthetic Identity Theft occurs when personal data of numerous victims is combined. While the new identity is not tied to any specific person, all the victims can be affected at once when it is used.
1.2 Methods and techniques to obtain personal data:
Shoulder surfing – the attacker is physically near the victim in hope of seeing (or overhearing) some sensitive personal information, for example, the moment the latter proceeds to use his credit card number or mention his SSN on the phone.
Dumpster diving – a pretty old-fashioned method by which the thief literally rummages in a victim's trash looking for discarded valuable pieces of information. It is hard to believe, yet people throw away important personal paperwork or financial documents (e.g., pre-approved credit card applications), either intentionally or by accident, without even bothering to shred these documents first.
Phishing – every regular user of email services has come across a myriad of unsolicited emails, with some of these emails being just what they are, "spam," let's use this notion, but others may be more cunning, prompting their recipients to reveal personal information.
Spear phishing represents a particular cause for concern when it comes to personal data because it is a highly targeted phishing attempt. Criminals hone the blade, so to speak, by collecting as much personal data about a specific person as possible before placing the spear phishing decoy.
II. Identity Theft Prevention
2.1 Services
Credit monitoring does not prevent identity theft, but what it does is to help in keeping a vigilant eye on credit reports for indications of fraud. In essence, this service is ideal for alerting the victim of potential problems so that he can take necessary steps to right the wrong as soon as possible.
Companies that undergo a data breach often offer their customers credit monitoring to compensate for losing their data. Credit monitoring may alert consumers even in cases where their personal data is seen on the dark web (being there usually for sale by thieves).
Each consumer is entitled to a free annual copy of his Experian, Equifax, and TransUnion credit report. Pay attention to your credit report for unauthorized inquiries or newly opened accounts in your name, as well as any irregularities in your credit score. Pay attention to bills.
On top of that, you could sign up for alerts with your financial institution. Depending on your bank's or credit card issuer's policy, you may have the opportunity to opt in for some sort of an alert system regarding unusual transactions (e.g., exceeding a particular dollar threshold, originating overseas, or made online, by phone or mail).
Identity monitoring is a service that tracks personal data of a customer by checking on all kinds of sources, from public records to illicit websites.
Fees for identity theft insurance range from $5 per month to as much as $30 each month. Insurance policies usually only cover petty expenses, such as fees for some services and costs related to replacing compromised documents (e.g., SSN, passports, driver's license, etc.).
2.2 Personal Safety Tips
Personal and Physical Security
- Never leave your wallet or important documents unattended (or all kinds of valuable belongings for that matter) in public places, such as on a table at a restaurant, and avoid leaving those even in your car
- Secure your mailbox
Detective B. Bennett from the Salt Lake City Police Financial Crimes Unit considers that two major sources of documents for identity thieves are among stolen items from mailboxes and car break-ins.
- Always mind your surroundings when you deal with private data or use login credentials
- Shred important paperwork and documents before throwing them away into public bins
Social Security Number /SSN/
When cyber crooks assume control of your SSN, they can use it to perform various illegal actions – for instance, to open credit card accounts or take out loans while pretending to be you. That is why you need to minimize your exposure to SSN-based scams.
- Carry important documents such as SSN as less as possible.
- Ask authorities to use a different number for your driver's license. Remember that your SSN may be on your insurance card or other identity documents, although institutions are gradually phasing out this practice.
- Disallow any usage of your SSN by an institution as an identifier for your account.
- Clark Howard is a personal financial expert who has one very straightforward advice: "Do not give a doctor's office, hospital, lab or any medical facility your Social Security number on any form. Leave it blank."
- Do not share SSN, personal financial details, and login information even with family members or close friends.

Photo by Identity Force / CC BY
General Cybersecurity
- Refrain from free Wi-Fi networks – Cellular networks or personal, password-protected networks are much more reliable. If you must connect to an open wireless network, use a VPN service. You can subscribe to one for as much as $5 per month
- Make sure that you connect with official and secure websites (Tip: look for the "https:" prefix)
- Install HTTPs Everywhere, an app which will secure your web searches by encrypting all of your online communications
- Do not install suspicious apps or apps originating from untrusty sources. Try to share with apps as little information as possible
Password Security
- "Our [password] hygiene is very poor, and criminals know it," Al Pascual says. He recommends consumers to enable two-factor authentication whenever is possible
- Have a different password for each of your accounts – use numbers, symbols, and a combination of uppercase and lowercase letters
- Use a password manager if you feel that you may need some extra assistance with your numerous passwords. This is software that not only stores your passwords, but it also organizes them in a manner that will make their usage easier
- Again, always mind your surroundings when you deal with private data or use login credentials

Photo by Identity Force / CC BY
Secure Banking
- Perform online banking activities only from a home computer that has anti-virus software that is kept up-to-date
John D. Farmer is a professor of criminology and criminal justice at the University of North Florida. He makes a comparison between credit cards and debit cards from a security point of view: "If your debit card gets compromised, a bad guy can drain your account. Whereas with a credit card, you do not have any of your money tied up in the process."
- Cancel inactive bank accounts and limit the number of bank cards
- Use a virtual debit card to cut off criminals from accessing your primary accounts. These cards can be set up to work on a single transaction basis or be applied to one website alone
- Always collect your credit/debit and ATM card receipts and do not dispose of them in a public trash container without shredding them first
- Notify your bank about stolen cheques
- Destroy all cheques upon closing a chequing account
- Notify the bank that you prefer to collect new checks personally from the branch rather than having them sent to your address via mail
- For the last time, mind your surroundings when you deal with private data or use login credentials
Criminals can access a banking app on a mobile phone through a bogus app that is unrelated to online banking
- If someone else is in control of your personal bank card or account, ask the bank to give you a new bank card and account number with a completely new password. Close the compromised account and cancel your card(s) if it is necessary
- "The single best practice consumers can adopt to prevent financial fraud is to balance their accounts every month. Know what is coming in and what's going out, and double check it," says Jill Vihtelic, a professor of business at St. Mary's College.
Phishing and Vishing
- Do not open attached documents or click on links embedded in the body of unsolicited emails. To open suspicious files or links is most of the time tantamount to open Pandora's box
- Avoid providing sensitive personal information via email or phone (unless you are absolutely sure that it is safe). Regard with suspicion callers that claim to work for the IRS, for example, demanding personal data or payment information
Social Networking Sites and Privacy
- Be careful with whom you connect on social networks, especially when you are not familiar with the person in question
- Make sure that the privacy settings on your social media profiles are set to the highest level
- If you share a lot of personal information online – such as children's name, pet's name, birthdays, university info, current city, etc. – you should know that cyber crooks might leverage it to guess your passwords or perform spear phishing attacks on you, among other things
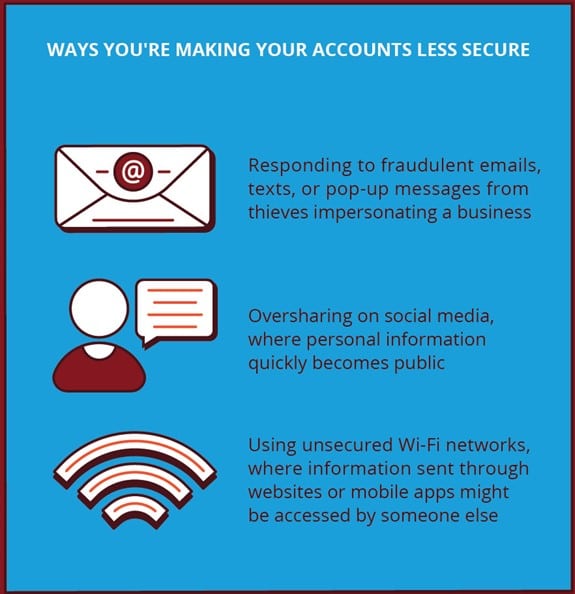
Photo by Identity Force / CC BY
- Are you an active participant in the selfie craze? If yes, you better hide those telltale fingers of yours

As the independent security researcher Troy Hunt says: "These days people are very frequently sharing things like birthdates, jobs, education history with any website that asks for it. The risk you run in giving every site that asks for it this sort of sensitive information is it is then spread around that much further, and it is then used by attackers to gain access to your other accounts."
 Lots of Amazon users have fallen victim to third-party seller fraud lately. Not only buyers will have to be careful when dealing with newly registered sellers, but they also have to proceed with caution seller accounts that have been on the platform for years. The reason again is identity fraud. Apparently, having taken advantage of username & password leaks from other places, the fraudsters assumed control over real but inactive seller accounts, and now are using their good name and positive ratings to lure buyers into purchasing goods that will never be shipped.
Lots of Amazon users have fallen victim to third-party seller fraud lately. Not only buyers will have to be careful when dealing with newly registered sellers, but they also have to proceed with caution seller accounts that have been on the platform for years. The reason again is identity fraud. Apparently, having taken advantage of username & password leaks from other places, the fraudsters assumed control over real but inactive seller accounts, and now are using their good name and positive ratings to lure buyers into purchasing goods that will never be shipped.According to the retail research site Marketplace Pulse, "[a]ll of these sellers are obviously no longer checking their selling accounts, and are likely ignoring Amazon emails too. So, they only notice this when their credit card gets charged, by which point it might take weeks to get this sorted out." So, if you have an Amazon account, check it regularly or close it if you do not intend to use it. On buyer protection, here is some advice by Ben Kuchera:
"
- Use common sense. If a price seems too good to be true, it likely is.
- Be very skeptical of any just-opened seller account.
- Make sure the seller's feedback is mostly positive, and the more successful transactions they have across a longer span of time, the better.
- Check out the shipping time. Why would a legit seller need to hang onto the system for a few weeks before selling it? Most individuals who have the Switch in-hand will be able to ship within a day or two of payment.
"
III. Recovery
"Unfortunately, it is impossible to prevent identity theft completely because so much of your data is outside of your control," explains Nick Clements, a Next Avenue Contributor. That is so true. Identity theft prevention is not enough, since third parties, not you, may fail to protect your personal data.

The Identity Theft Resource Center estimated that data breaches in 2016 are up 40% in comparison with 2015. More than 4 billion data records were stolen in 2016. In reality, a data breach that involves a loss of customer or employee personally identifiable information (PII) exposes this information directly to the prospect of being used for criminal purposes, including identity fraud.

The good news: In most cases of identity theft and fraud the negative effects can be reversed. Only a few cases are beyond remedy. In a way, the whole ordeal is similar to treating some kind of a dormant disease; the sooner you find it, the better your chances for full recovery are.
The Federal Trade Commission sees a direct correlation between identity theft and monetary damage on at least two-thirds of all victims. "Identity theft can affect the victim's ability to get a job, rent an apartment, buy insurance, get a mortgage or get a car loan," writes the USA Today reporter Steve Weisman. Consequently, despite the proposition of being harmless moneywise, the identity theft may eventually empty your pockets, especially if you leave this disease spread too much.
One of the most frightening aspects of identity thefts is the fact that it takes an average of 292 days for victims to find out that their personal data has been used for fraudulent purposes. Also, the repair of your identity is usually a very long process. According to a study by Experian's Victims of Fraud team, it can take 300 hours to set the record straight. Understandably, the entire process can take a lasting emotional toll on victims.

What to Do First?

Inform the appropriate organization – a credit card company, bank, the IRS, or health insurance provider. Ask the organization to close compromised accounts, or close immediately fraudulently opened accounts. This will close the tap through which the thieves siphon off money, stop them from gaining additional benefits, and prevent any further actions on their part.
Inform one of the three major credit bureaus (Equifax, Experian, and TransUnion) so that they can activate a fraud alert on their credit records.
If you notice that someone may exploit your credit information, you could have recourse to a service called credit freeze. What this procedure does is to prevent your credit score or a credit report from being assessed by any entity that does not have your PIN, which you select at the time of activating the service. Moreover, credit freeze staves off any attempts by malicious actors to obtain new credit or open new accounts in your name, regardless of whether they have your SSN or other personal information.
Submit a complaint with the Federal Trade Commission and file a police report. Ask for a complaint number.
Optional:
Come in contact with respected organizations that have experience in fighting identity frauds (e.g., the San Diego-based organization Identity Theft Resource Center).
***
The predominant part of this writing may seem to you like the paranoid's guide to identity protection, but that is simply the new digital reality. The Information Commissioner Timothy Pilgrim said his office had received a significant increase in reports of identity theft. Speaking from experience, he expressed his personal opinion on the impact of this crime: "Identity theft to me is one of the most invasive aspects of a breach of somebody's privacy and can have major ramifications for individuals."

***
Reference List
Adams, R.L. (2017). Identity Theft Protection: 10 Ways To Secure Your Personal Data. Available at https://www.forbes.com/sites/robertadams/2017/05/05/identity-theft-protection-10-ways-to-secure-your-personal-data/#70d015e362fd (25/05/2017)
Bainbridge, A. (2017). Over 55s hardest hit by 'invasive' identity theft, Scamwatch figures show. Available at http://www.abc.net.au/news/2017-01-18/over-55s-hardest-hit-by-invasive-identity-theft/8188904 (25/05/2017)
Beres, N. (2017). Police Investigate Extreme Case Of Identity Theft. Available at http://www.newschannel5.com/news/police-investigate-extreme-case-of-identity-theft (25/05/2017)
Carlisle, R. (2017). Massive identity theft ring uncovered in Salt Lake. Available at http://www.good4utah.com/news/local-wasatch-front-/massive-identity-theft-ring-uncovered-in-salt-lake/210691314 (25/05/2017)
Clements, N. (2016). Identity Theft: How To Protect Yourself Or Resolve It. Available at https://www.forbes.com/sites/nextavenue/2016/09/14/identity-theft-how-to-protect-yourself-or-resolve-it/#181336b433b4 (25/05/2017)
Egan, M. (2016). Wells Fargo investigated by California for possible identity theft. Available at http://money.cnn.com/2016/10/19/investing/wells-fargo-identity-theft-california/ (25/05/2017)
experian.co.uk. What is identity theft? Available at https://www.experian.co.uk/consumer/identity-theft.html (25/05/2017)
fbi.gov. Identity Theft. Available at https://www.fbi.gov/investigate/white-collar-crime/identity-theft (25/05/2017)
Grant, K. (2017). Identity theft, fraud cost consumers more than $16 billion. Available at http://www.cnbc.com/2017/02/01/consumers-lost-more-than-16b-to-fraud-and-identity-theft-last-year.html (25/05/2017)
Hudson, D. (2017). Child identity theft in Utah is growing, but you can protect your children. Available at http://www.good4utah.com/good4utah/child-identity-theft-in-utah-is-growing-but-you-can-protect-your-children/206403338 (25/05/2017)
inc.com (2017). How Vulnerable Are You to Identity Theft? Available at https://www.inc.com/identityguard/be-breach-ready.html (25/05/2017)
Mitnick, K. (2017). Who Has Your Data? Available at http://www.aarp.org/money/scams-fraud/info-2017/fraud-protection-identity-theft.html (25/05/2017)
O'Loughlin, E. (2016). Identity Theft and Social Media: How Are They Related? Available at https://securityintelligence.com/identity-theft-and-social-media-how-are-they-related/ (25/05/2017)
Papadimitriou, O. (2016). Identity Theft: What It Is, How It Happens & the Best Protection. Available at https://wallethub.com/edu/identity-theft/17120/ (25/05/2017)
practicalmoneyskills.com. Identity Theft. Available at https://www.practicalmoneyskills.com/learn/identity_theft (25/05/2017)
Reavy, P.(2017). 'Massive' identity theft ring could affect 1 in 20 Utahns, police say. Available at http://www.deseretnews.com/article/865673659/Massive-identity-theft-ring-could-affect-1-in-20-Utahns-police-say.html (25/05/2017)
Stroup, J. (2017). The Many Types of Identity Theft. Available at https://www.thebalance.com/the-8-types-of-identity-theft-1947176 (25/05/2017)
transunion.ca. Identity theft is a serious crime that happens more often that you might think. Available at https://www.transunion.ca/identity-theft (25/05/2017)
Teravainen, T. Identity Theft. Available at http://searchsecurity.techtarget.com/definition/identity-theft (25/05/2017)
U.S. Department of Justice. Identity Theft. Available at https://www.justice.gov/criminal-fraud/identity-theft/identity-theft-and-identity-fraud (25/05/2017)
Weisman, S. (2017). Is identity theft protection worth it? Available at https://www.usatoday.com/story/money/columnist/2017/04/22/identity-theft-protection-worth/100554362/ (25/05/2017)
Wells, D. (2017). Eight indicted in identity theft case involving thousands of current and former Utahns. Available at http://fox13now.com/2017/02/17/eight-indicted-in-identity-theft-case-involving-thousands-of-current-and-former-utahns/ (25/05/2017)

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
White, J. (2017). Identity Theft Protection vs. Credit Monitoring: What's the Difference? Available at https://www.lifelock.com/education/identity_theft_protection_vs_credit_monitoring/ (25/05/2017)





