PHP Lab: Prevent exposure of configuration/backup files from web root.
Introduction and background
A developer has created a web application in PHP, and the application makes use of configuration files from the config folder of the application. He also created a backup file for one of the configuration files within the config folder and forgot to remove it. The developer did not take any precautions to prevent directory listing of this folder. In this lab, we will discuss how an attacker attempts to gain access to sensitive data on the application using these minor mistakes.
Let's begin
The application is accessible from Kali Linux using the following URL.
Learn Secure Coding
http://192.168.56.101/webapps/environment/
When accessed from a web browser, it looks like this.

We do not have much detail on the web page to explore further. So, let us use a tool called Nikto to scan this application from this path.
Open a terminal in Kali Linux and scan the application as shown in the following screenshot.

As we can see in the above figure, Nikto has found some interesting information (Highlighted in Yellow).
Nikto found a folder named "config," and interestingly, directory indexing is not disabled.
Let's access this config folder in the web browser.

db.php.old appears to be a backup file for db.php. When db.old.php is accessed from a web browser, your PHP cannot parse it due to the change in extension. This file will be downloaded as shown below.

By default, Ice Weasel stores the downloaded files in the Downloads folder.
So, let's view the contents of this file using the following command.

This file has database connection details. If MySQL is exposed to other machines over the network, an attacker can connect remotely to the MySQL server and gain unauthorized access to the data.
Even if MySQL is not exposed over the network, an attacker who gains access to the machine where MySQL is running can still connect to the database using localhost as the server name.
How to avoid this?
We can make configuration changes to the Apache server and avoid directory indexing. This ensures that no user other than your application can access the files in the directory specified.
Switch to your Ubuntu server and run the following command with sudo as shown in the following figure.

Add an entry as highlighted in the following figure.
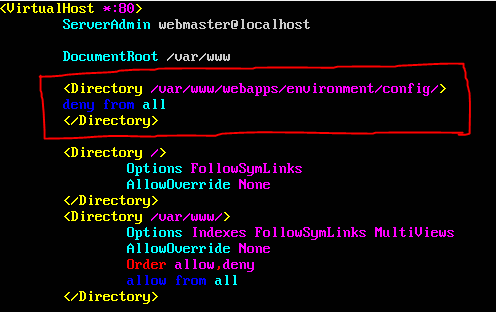
This ensures that config folder is protected.
Restart apache server using the following command for the changes to take place.
service apache2 restart
We can cross verify this by accessing the folder once again from Kali Linux as shown below.

We cannot access any files from config folder, but the application will run fine.
Learn Secure Coding



