Dropbox Phishing Attacks- Templates and Examples
Dropbox, the handy Cloud based storage for files, has been one of those amazing tech success stories. As of May 2016, Dropbox had over 500 million registered users with around 1.2 billion files uploaded to Dropbox every day. Dropbox is also a collaborative tool, with 3.3 billion shared connections. Dropbox has its extended fingers right across the planet, both as a tool for individuals and for business.
This all makes Dropbox a familiar presence. It has, since its inception in 2007, entered our working lives, many of us using it daily, to augment our communications and store our documents and files. Dropbox has a hand outwards from our computer into the Cloud and beyond. Dropbox as a company has done something very special. It has created a sense of trust between the Cloud repository, that is Dropbox, and ourselves - the consumers of that repository. Consequently, we trust Dropbox with some of our most sensitive and personal data. I addition to this, we allow Dropbox to be a conduit for communication of those files with other parties.
See Infosec IQ in action
This heightened profile and prolific presence throughout our personal and working lives means that Dropbox has entered the sights of the cybercriminal. Couple this with our trust in the Dropbox brand, the fact that Dropbox communicates with us directly into our email inbox, as well as communicate to contacts via Dropbox, and you have the perfect storm for phishing. Below are some of the ways that Dropbox has, and is, being used for phishing.
A Box, Within a Box
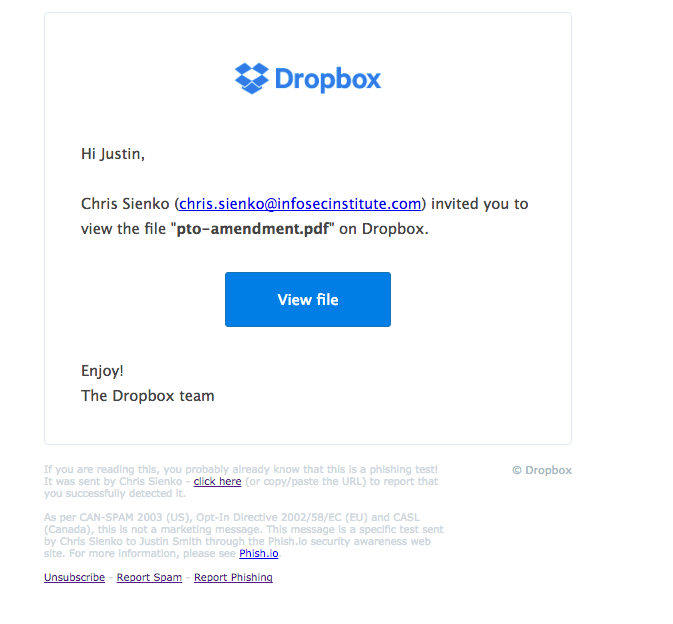
In this phishing scam, first reported by Symantec, a user receives an email which looks very much like it is from Dropbox support. The email usually warns that a file has been sent to them, which is too big to email. It directs the user to ‘click on a link’ to access the file in Dropbox.
Once the user clicks on the link, they are taken to a spoof Dropbox page. Ironically, this is hosted within Dropbox itself. The spoof page request that you login. If you enter your credentials, they are then stolen by the cybercriminal behind the attack. In some attacks, the hacker also offers login using social sites like Google and Outlook, hoping to harvest other login credentials. Once they have these credentials, they then have a user’s Dropbox (or another platform) access. In the meantime, the user is redirected to the real Dropbox login.
This type of phishing exercise relies on several things:
- Your familiarity with the brand of Dropbox
- Your trust in the brand of Dropbox
- Your curiosity in wanting to know what the mystery file is
- Often a sense of urgency will be built into the email message too
Many phishing scams rely on this mix of trust and curiosity to get you to click on a link, or download a malicious attachment. The cybercriminal using our own psychology against us to trick us into behaving in a certain way.
Using a Dropbox Phishing Rod
Another scam, based on Dropbox but again employing trust as the lever to perform the phishing, is based on using another trusted company to elicit specific user behavior. An example of this scam was the recent phishing attack which was based on a spoof version of the Better Business Bureau site. The site sent emails out to individuals which looked exactly like they were sent from the FBI (another trusted organization in the loop). The email asked the user to click on a link, which took them to a spoof Dropbox site. The file on the site contains malware, most recently this has been ransomware, and if downloaded, can install on the user's computer.
Variations on a Theme
Phishing does not use a static approach. Cybercriminals will create new variations on a successful theme. For example, the phisher knows that adding a degree of urgency into a spoof email is more likely to get a user to click on a link. If they mix this urgency with fear, such as financial loss, or compromise of an account, even better. Add to this a well-known and trusted brand, and you have created the perfect landscape to spoof an individual. Dropbox phishing uses all of these tricks within a number of mixed themes. Examples could be a Dropbox phishing campaign that asked users to click on a link to download ‘urgent and highly sensitive’ documents. Another may be a simple Dropbox share alert. Whichever theme they chose to use, they will always look like legitimate Dropbox emails. It is this mastery of design that sets aside a successful phishing email, from a highly successful phishing email.
Being able to distinguish between a legitimate Dropbox email and a spoof Dropbox email is something that can be taught. Security and phishing awareness is one of the best ways to mitigate the risk of credential loss and malware infection. Infosec has created a phishing awareness and training tool called ‘PhishSim’.
This easy to use Cloud-based tool gives you the ability to create your own Dropbox phishing simulation to train your users to recognize spoof Dropbox emails. This helps your organization to prevent malware infection and stop the loss of Dropbox and other social media login credentials.
See Infosec IQ in action
Visit Infosec IQ today, get your free username, and start using PhishSim's Dropbox template (as well as our library of dozens of pre-made templates) and start increasing your security awareness now.