Phishing Attacks in the Telecommunications Industry
Of late, the telecom companies have been battling to stay up to speed with the security challenges as they operate in a highly risk-laden environment, especially when millions of their customers are signing up for Internet, mobile phone and data center services. There are significant threats due to the wide range of services offered by the telecom industry and the nature of the industry itself. These progressive threats need to be dealt with effectively and discreetly.
Why Phish the Telecommunications Industry?
The industry keeps the entire world connected in a complex infrastructure of data and voice transmissions. The vast amount of data that these operators hold makes them desirable targets for cyberattacks.
Phishing simulations & training
The potential consequences of a successful phishing attack on a Telco would mean phone and Internet services interrupted for myriad subscribers, businesses experiencing huge downtime and, frighteningly, possible leakage of sensitive customer information.
How Are Telecommunications Companies Phished?
Phishing is one of the most popular forms of hacking, attempting to acquire account information and user credential details by posing as a directive coming from a legitimate source and an authority like a trustworthy company or organization. Phishing emails are also one of the easiest and most commonly-used methods. Also, SMS phishing, often known as smishing, operates in a similar manner, in which fraudsters use text messages to bait victims.
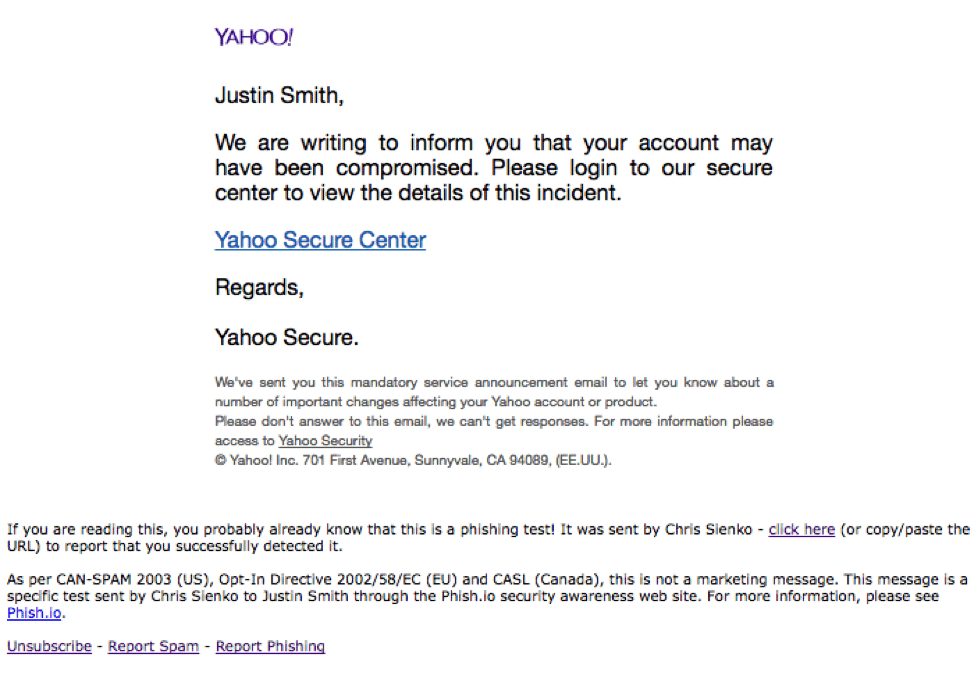
In that moment between initial panic and a rational response, a moment of fear could cause you to click through a realistic phishing email like this one and compromise your valuable data
One of the biggest reasons hackers are using phishing and ransomware attacks to target telecom companies is to bypass their network security so they can access piles of customer-sensitive data. It also saves them from coming up with sophisticated ways of breaking into complex security setups when they just simply need to trick employees in order to have access to the data.
There are many more types of frauds that hit the Telecom sector, one of which targets the telecom provider itself with simulated traffic and regulatory loopholes. Another type of fraud includes the most common ones of defrauding subscribers through phone fraud and various other methods.
In the event of security incident, the loss figures and corrective measures are often kept confidential. Due to this, the telecom sector businesses are now transforming into technology companies.
Phishing Statistics and Facts
McAfee Labs revealed that a decade ago it would encounter only 25 threats a day as compared to the 500,000 daily alerts it analyses today.
Telecommunications phishing attack stories are everywhere. Telefonica, Spain’s telecommunications giant, was recently targeted by a ransomware attack, according to several reports from May of 2017. Portugal Telecom was also hit by a cyberattack. Russian telecommunications company Megafon reported a cyberattack that affected its call centers. In April of this year, fraudsters sent BT customers fake bills of exorbitant amounts in a new email scam attempting to incite them to click a dodgy link. Vodafone also encountered such attacks. These attacks are on the rise and make it crucial for organizations with sensitive personal data to be vigilant.
Phishing is the biggest attack vector today and humans are the weakest link. The recent move by Google in introducing an anti-phishing mechanisms for the iPhone users for the Gmail application is a great defensive mechanism. By applying machine learning expertise to identify suspicious emails, this development will help prevent a high percentage of debacles, but the learning itself takes time.
BakerHostetler, a leading national law firm, consigned its incident response team to do a detailed analysis of the 450 data security incidents handled in 2016; the top causes identified across industries were phishing and ransomware, 43%; employee actions and mistakes, 32%; lost stolen devices and records, 18%; and constituted criminal acts and internal thefts, 7%.^1
According to a recent announcement by Forbes, 2016 saw almost 85% of companies hit by phishing attacks, with 90% of those attacks containing ransomware. Google claims that almost 70% of emails that pass through Gmail are spam in nature even though their detection system has achieved a 99.9% detection score, which is a large concern.
Three Steps for Preventing Telecommunications Phishing
Education and Training
All Telecom companies in the public and private sectors need to be made aware of the latest cyber threats and their repercussions along with the counter measures. Their best defense would be a security program that can fathom and withstand all kinds of threats, by covering threat detection, prevention measures, incident response methods and investigation resources.
Testing and Evaluation
The frequency of phishing attacks has increased with no respite in sight for telecom companies. Their best defense is to accept the problem and constantly safeguard of their systems, people and customers.
The government needs to formulate stringent regulations countering cyberterrorism and enterprises will have to plan regular mock drills to access their security posture and defense mechanism. Such initiatives should also be undertaken by other sector companies, such as power, transport, energy, IT/ITeS, and defense.
US-CERT has partnered with the Anti-Phishing Working Group (APWG) to gather phishing email messages and website locations to help enterprises avoid becoming victims of phishing scam.
Reporting
The recognition of this problem is the first step toward fighting phishing threats. Educating users to identify phishing SMSs and emails lessens the chances of them actually falling into a phishing trap. The users should be educated and encouraged to report such attempts whenever they encounter them. It is easy to do so in a large organization for employees but the same education and awareness is difficult to impart to the general public.
Technology alone cannot solve phishing problems, as the number of breach attributes are only increasing. Just failing to address the user awareness component of data protection strategy can negate even the country’s cyber defense efforts.
Conclusion
Enterprises need to inherit security considerations by design and not at a later stage as add-ons. Meeting the hacker’s demands is in no way a solution; on the contrary, it makes the enterprise a preferred and convenient target for them in the future.
It is high time that security is taken as a procedural safeguard that encompasses threat detection, prevention, prediction, and investigation. Multilayer security is the need of the hour, along with strong vigilance; however technology cannot play the only role here, as collaboration with shared intelligence and employee awareness needs to be part of the rigor too.
References
https://www.us-cert.gov/report-phishing
See Infosec IQ in action
https://www.thesun.co.uk/news/3323719/bt-fake-email-scam-warning-phony-bills-fraud/