Phishing Attacks in the Recreation Industry
Introduction
When it comes to phishing schemes, the world of recreation may appear safer than more finance-oriented pursuits like banking, cloud storage, and payment enterprises. But the reality is, the business of radio, television, video games, print, streaming content, and film is a $2 trillion industry which renders it an equally attractive target to hackers. This massive market, including heavy hitters like Netflix, Amazon, and Hulu, is one of the most powerful in the world, which also means it is a natural target for phishing expeditions of all kinds. The U.S. recreation and media market alone generates around $632 billion each year, which represents close to 30 percent of global revenue. And as this lucrative giant continues to grow at a rate of five percent a year, so do the digital threats to its livelihood.
To breach the media websites and internal networks of this industry demands a certain knowledge of the inherent systems and the ability to find digital security weaknesses. In general, phisher-men in this realm are either looking for publicity or the opportunity to disrupt the existing landscape of media by absconding new releases or holding projects for ransom. These threats can also take the form of state-sponsored attacks seeking to spy on or steal sensitive information. Because the recreation industry must work with a broad range of vendors and smaller international companies, they invariably invite less secure entities into their landscape who do not have extensive experience with cybersecurity. This can translate into vulnerabilities for the larger industry, especially as it relates to monitoring and compliance.

Two year's worth of NIST-aligned training
Deliver a comprehensive security awareness program using this series' 1- or 2-year program plans.
The most famous example of this reality happened in 2014 when a hacker group by the name of “Guardians of Peace” leaked the release of confidential information from the mega-film studio Sony Pictures. Although the details of the breach remain unclear, it is believed the use of phishing-like malware provided the initial access opportunity. Through this exploit window, hackers were able to claim over 100 terabytes of data from the company, which was then used to compromise the personal information of Sony employees, including salary details, family contacts, email contents, and even copies of unreleased films. The hackers then went on to employ a modular computer virus that wiped Sony’s entire computer infrastructure. Not only did this breach put the safety of the people involved at risk, but it ultimately forced Sony to pull the screening of a new movie based on the terrorist threats, thereby offering a digital release in lieu of a formal premier.
Why Phish the Recreation Industry?
The real question is, why wouldn’t a hacker phish the recreation industry? As a major superpower in the business world, they clearly manage a mind-boggling amount of revenue while employing practices that invariably put them at risk for cyber threats. Their financial reach and public visibility make them an ideal target for those looking to tout the theft of these high-profile digital assets. Further, any successful attempt to steal data then becomes a powerful bargaining chip for hackers who can use them as leverage against their victims. This type of ransomware can force media companies into all sorts of compromising positions, including sizeable payments, unsanctioned content releases, internal financial information, embarrassing images, industry secrets, and private industry communications.
While the standard phishing strategies are well known in the industry, experts suggest these attacks are still managing to find willing victims, putting the global attack rate up 65 percent since last year. Because this exploit has the ability to skirt security and technology through targeting human emotion, it has become somewhat of a digital epidemic. The recreation industry employs a high number of contractors, freelancers working on certain projects, and small offshore production facilities with limited IT and security staff—not to mention minimal budget for such prevention— and so it offers hackers a lot of opportunity. This reality has inundated the industry with ransomware and credential theft attacks, creating several high-profile exploits like the one experienced by Sony Pictures. This has led to explosive headlines, public embarrassment, lost revenue, and even lost reputations and careers.
How are Recreation Industries Phished?
Just as it is with real fisherman, digital phishing expeditions love nothing more than netting a big fish. And unfortunately for the recreation industry, their bulky profits and high profile nature make them a particularly attractive and visible catch. Depending on the goal of the cybercriminal, companies in the recreation industry can be phished in a few different ways, all of which exploit the notion of basic trust. Phishing attempts can appear in various forms—from email to text to social media—which all aim to collect data for fraudulent purposes.
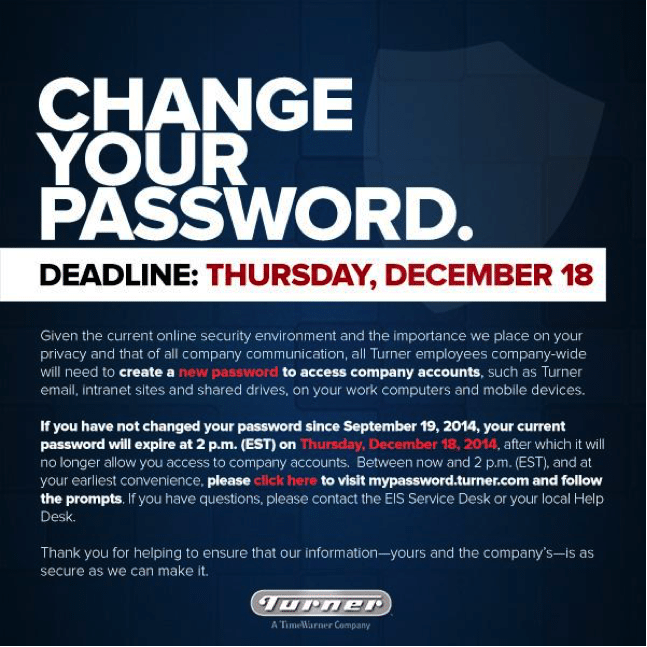
Because media companies must work with such a broad range of employees and vendors, their day to day email traffic is exceptionally high. This presents great opportunity for hackers who send links to random email accounts with some sort of urgent message from a seemingly authoritative source. As an example, the email might ask users to reset a password, at which point they can scrape the information and hack the account. However, these fake communications actually contain dangerous links which lead users to faux websites where their credentials are collected and sent directly to the attacker.
From there, the cybercriminal can continue to exploit this data through even larger campaigns. Once a user’s credentials have been snatched, attackers can easily penetrate the network; steal movies, shows, or games at any stage of development; delete materials from the company’s network; or hold it for ransom. Even worse, hackers can download terabytes of data with salary information, financials, and all internal and external email communications.
 Click the image to see SecurityIQ's phishing template library
Click the image to see SecurityIQ's phishing template library
Top Two Methods to Prevent Recreation Phishing
Isolation
Because the recreation industry is such a juicy target for hackers, companies looking to protect themselves must employ some sort of isolation platform which reduces the attack surface on user devices. This safeguards employees, contractors, studios, production houses, and post-production facilities from the popular use of ransomware, phishing and spear-phishing, malware, credential theft, drive-by exploits, watering hole attacks, and more.
On the most basic level, any information that comes in must be deemed either good or bad—if it’s good it’s allowed entrance, and if it’s bad, it’s blocked. By running all web content in a container on the cloud, or on a network appliance, an organization’s systems are essentially isolated from the internet and the need to make this choice. This allows any browser to interact with the web content without affecting a user’s experience or software. This technology is particularly effective with phishing exploits using email because it doesn’t matter if a website is serving up malware or not—everything is executed in the cloud with no way for bad stuff to reach the endpoint.
Skepticism & Simulation
When it comes to self-preservation and protection, there’s nothing better than a healthy dose of skepticism. Reminding employees and associated parties to always ensure the source of communications before responding in any way should be vital part of any training program. Making everyone aware of how to engage in positive skepticism through educational course with interactive options and real-life scenarios is a great way to boost this vigilance and teach people how to protect their information—and that of the company—on a real and practical level.
InfoSec Institute has created such a program called Security IQ, which has an educational component designed to inform professional how to stay safe. These courses can be administered remotely and customized to suit the individual needs of different recreation companies. Drills and test situations can also be completed using PhishSim, the automated phishing simulation program designed to educative everyone from directors to producers to creative contributors.

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
Conclusion
In the technological world, the biggest weakness comes in human form. For this reason, phishing exploits which prey on the emotional reactions and fears of people have become particularly popular in recent years, as they tend to reap more rewards than purely technical exploits. These threats come in many forms—from mass phishing to spear-phishing to whaling—and work to divulge confidential company data. But the good news is, a concerted effort to control the natural curiosity and gullibility of users is really all it takes to block a phisher-men’s best efforts.