Phishing Attacks on Individuals
Phishing Attacks on Individuals
Industries
- Financial Phishing
- Government and Military Phishing
- Healthcare Phishing
- Retail Phishing
- Phishing Individuals

Two year's worth of NIST-aligned training
Deliver a comprehensive security awareness program using this series' 1- or 2-year program plans.
Individuals are the biggest targets for phishing attacks, and the number of phishers and phishing emails has risen precipitously in the last year. According to the most recent quarterly report by the Anti-Phishing Working Group (APWG), the number of observed phishing attacks in Q1 2016 was at a 12-year high, with a horrific 6.3 million more phishing emails in this quarter, including a huge focus on ransomware. You are not just a target, but the cost of unwariness could be financially ruinous.
Why Do Attackers Focus on Individuals?
Individuals are a target because they are the most susceptible to phishing attacks. They are the most susceptible because many aren’t experienced with IT security and the security-savvy tools of the trade. They usually have a credit card or bank account that is valuable to the attacker. Financial information is the biggest target, because this information earns the attacker money for his efforts.
A phishing attack targets all manner of sensitive information from the individual. Credit cards, social security numbers, banking information (including PayPal), or even corporate credentials are valuable to the attacker. The attacker mainly goes for information that he can use behind the scenes to steal money or personal information from the user.
Consider someone who gets his email password phished. The attacker is able to trick him into sending an email password, so now the attacker has access to email. The attacker reads the victim’s email, finds clues to standard accounts such as ecommerce, banking, and even medical sites. The attacker can then use the victim’s email to reset passwords. He can even reset security questions or gain access to security question answers. He logs into the victim’s banking account and sends the victim’s money to an offshore account. This is just one way an attacker can ruin someone’s financial security.
If this sounds impossible, or if you’re imagining that you’re too savvy to fall for such obvious tricks, consider the case of Kevin Roose, the host of Fusion’s documentary series Real Future. He attended DefCon, a yearly hacker convention in Las Vegas, daring them to try to hack him and cause as much damage as possible using only a phone and an internet connection. One hacker called Roose’s phone provider, posing as his wife, playing a YouTube clip of a crying baby in the background during the call to add authenticity. The phone company fell for it, allowing Roose’s “wife” to take over the account, even changing his password to restrict his own access. Another hacker created a sufficiently subtle spear-phishing campaign that even Roose, who was clearly on the lookout for hackers, still fell for it. The hacker, Dan Tentler, announced the successful phish with a chilling message to Roose: “I could have left you homeless and penniless.”
How Phishing Works
Phishing first starts with a target. Generally, attackers build up an email list with several targets. They scrape the Internet for random targets or build a list from research they perform on the Internet. (See our article on Phishing Networks to see how networks of phishers collaborate with one another, trading victim emails and vital information for maximum destruction.)
Once the attacker has a list of emails, he can then initiate a phishing attack. First, an email is created that looks official. For instance, many attackers use PayPal to build a phishing email. They take the PayPal logo and official verbiage and apply it to the email template. They then add their own content to the phishing email, usually asking for the user’s user name and password. The email is built with a sense of urgency, so the user feels like they will lose the account or money within the account if they don’t comply immediately with the request to go to directly to the website and enter their user name and password.
The phishing site is hosted on an attacker’s website. The link looks as if it’s for the PayPal site (or another official institution), but it’s actually a URL to the phisher’s website. The user clicks the link and sees what looks like an official login page for PayPal. If the user doesn’t notice the URL, they are tricked into entering their user name and password information. Soon after the information is entered, the attacker logs in to a website using the user’s credentials and can do anything that the user is capable of doing, including withdrawing funds and locking the victim out of their own account by changing the password.
There are several signs of a phishing attack. Most email providers filter these attacks from ever reaching the user’s inbox, but some still get through.
The first sign is that the email is from a domain other than the official source. The sender address can be spoofed, so users should still take note of the email content.
Hovering the mouse over the link in the email usually displays the true URL address behind the link. If a different URL displays when hovering over the link, then the user should avoid clicking the link.
If the user clicks the link, then take note of the URL in the browser. If it’s different from the official institution, don’t enter any information. The best route is to type the URL of the official institution into the browser and log in as you normally would. You will likely find that your account is waiting for you, safe and sound, under no threat of immediate cancellation or dispersal of funds.
Defending Against Phishing Attacks
For individuals in an enterprise environment, the enterprise should use email filters specifically designed for phishing attacks. Email filters greatly reduce the number of phishing emails that reach the user’s inbox. Filters send them directly to a quarantine section where the user doesn’t even see the malicious attacks, effectively neutralizing the threat.
For individuals working outside an enterprise environment or just using email for personal reasons, the best defense is to know the signs. Also, be sure to use an email provider that actively filters phishing emails. Some providers have aggressive phishing filters that either delete the email before they ever reach your inbox or send them to the spam folder. Good providers keep up-to-date on the latest spam techniques and actively monitor for any changes in the environment.
Always be suspicious of emails that ask for a user name and password. Website owners should never ask for your user name and password through a link in an email. Banking or financial institutions will never ask for any private information such as a password. The user can log directly into the website and also call the institution to verify that the email is legitimate if unsure.
[cta id="1470253732174" post="35901"]
The best way to avoid phishing attacks is to know the signs and avoid clicking any links in a suspicious email. Even with advanced filters, some phishing emails are able to pass to the user’s inbox. At this point, the user must be able to identify the phishing attempt and either delete it, report it, or move it to a junk folder. where it will be deleted after a few days.
Testing Individuals for Security Awareness
One issue with security is that security awareness is not inborn and it’s not always intuitive – it must be learned through trial and (hopefully not too much) error. An experienced professional can usually spot these fraudulent emails (although they sometimes get fooled as well), but end-users aren’t as experienced in spotting the red flags. The best way to learn is to make a mistake, and then learn from that mistake. To be sure, nobody wants to learn from a mistake that could cost you your credit rating, your savings account, and the destruction of your most valuable information. Is there a safer way? There is.
Infosec’s Infosec IQ site includes a program called PhishSim. The program can simulate a wholly realistic (but harmless) phishing attack. With PhishSim, you can attempt to fool your friends and family with realistic looking phishing emails. If they take the bait, there’s no harm done – they’ll be directed to the AwareEd website, where they can watch an interactive video aimed at increasing their security awareness.
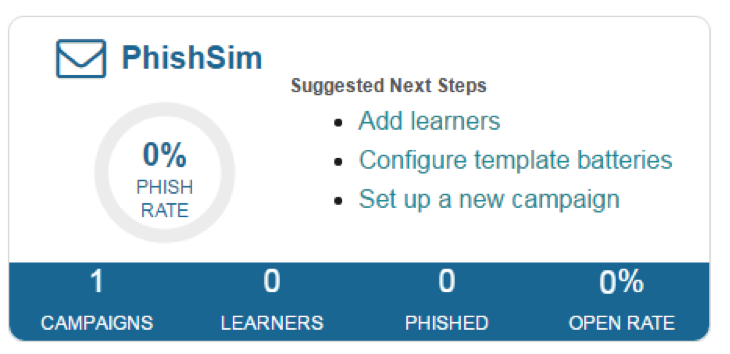
Let’s take a look at your InfoSec Security IQ dashboard.
With this simulation test, you can set up and track campaigns, keep track of learners (aka your “victims”) and get a snapshot of successful campaigns. The Phished number tells you the number of users who fell for the attack, and the Open Rate shows the percentage of people who opened the email.
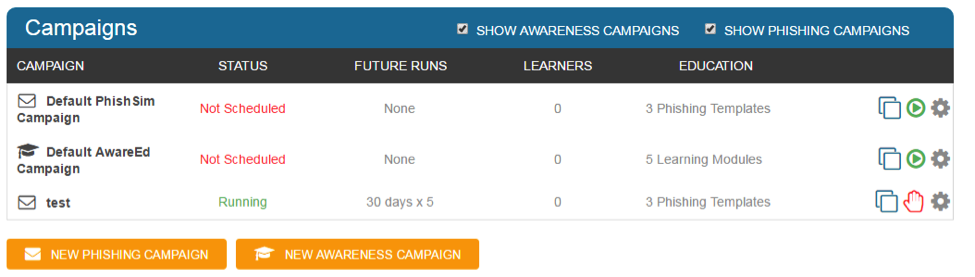
You can set up campaigns with templates and get a quick snapshot of your spear phishing targets:
Spear-phishing is when hackers target specific people, using information that would apply only to that user. Spear-phishing is much more effective for the hacker than using a long list of random emails, and has a much higher success rate.
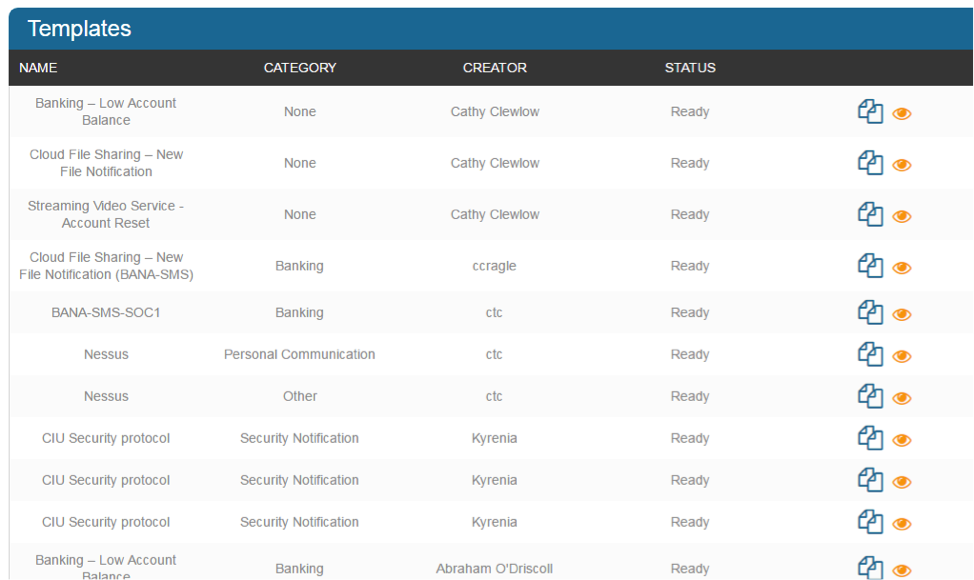
You can start your fake-phishing campaign by first registering for an account and then setting up an email template. PhishSim has created dozens of pre-made templates that you can use to simulate different types of phishing attacks. Simply go to the PhishSim section, click “templates,” and click the tab marked “contributed” to see a list of over 100 unique and realistic templates. Or make your own!
If you look at the image above, notice that there are several different types of templates. The first one is a phishing attack that replicates a notice on the user’s bank account. The next one bases its verbiage on cloud file sharing notifications. The next one tricks the user by pretending that an account needs a password reset.
Because so many phishing victims are non-enterprise individuals, you should use PhishSim to attempt to “phish your friends” and see who is vulnerable to a phishing scam. PhishSim lets you create your own templates. The trickier, the better. You can set up a template to trick your friends and see who falls for the bait. This will help them better understand phishing and the importance of being defensive when someone asks them for their personal information or passwords. It just takes one mistake and hackers can gain access to numerous private resources.
If you want to phish your friends, think of something you all do together, something that might require a change in plans, and create a phishing campaign based on it. Are you in school and have a study group? Create a phishing campaign in which there’s a change in schedule for your weekly meeting, with a request to “click here to change the date in Google Calendar.” Maybe you and your friends are going to a movie on Thursday. Send them a campaign from the movie theater saying that the film has been cancelled due to electrical failure at the theater, and unless they click this link immediately, their tickets won’t be refunded for the full amount. Use your imagination and see how many ideas you can come up with!
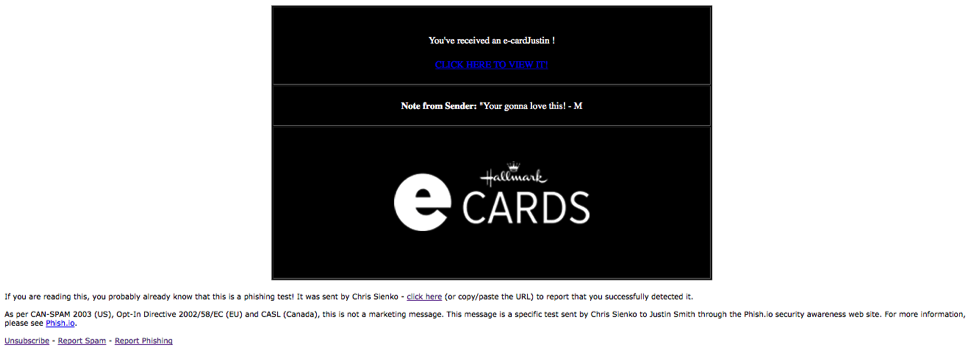
Or send them an “e-card”! Our e-card template uses the Hallmark logo and will look realistic enough for your friend to click through before they realize what they’re doing.
Above: an actual template available in the Infosec IQ template collection
Conclusion
All of these fake-phishing emails have one common goal: They attempt to trick the user into clicking the link. If the user clicks the link, your report shows this as an “Opened” email success. If the user enters a password, the phishing attack was successful and you’ll receive confirmation. The user will receive a notification that they’ve been “phished,” but that no damage has occurred. They’ll then be instructed to watch a short, interactive video explaining what to do differently the next time this occurs.

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
Phishing is one of the most common attacks and the most successful for attackers. When a phishing attack is successful, it can be devastating for both businesses and individuals. For the individual, it only takes one successful attack to lose it all – your money, your credit rating, your entire life. Make sure you protect yourself, and your friends, too, through ongoing phishing-awareness campaigns. It’s no risk, and all reward.