How the NSA Monitors Target Computers with Radar Wave Devices
Introduction
Germany's Der Spiegel has published a couple of disturbing articles on the NSA surveillance activities. The media agency has focused its articles on the Advanced/Access Network Technology (ANT) division of the NSA's Tailored Access Operations (TAO) elite hacker unit, and the capabilities of the division in the development of advanced tools to infiltrate practically every technology.
Der Spiegel published an internal NSA catalog that offers spies backdoors into a wide range of equipment from major IT vendors. The document includes backdoors for hard drives from Western Digital, Seagate, Maxtor and Samsung, for Juniper Networks firewalls, networking appliances from Cisco and Huawei, and unspecified equipment from Dell. The products listed in the catalog are designed by the Advanced/Access Network Technology (ANT), the agency has built capabilities to compromise any kind of device, They're also able to infect BIOS firmware of targeted systems for long-term cyber espionage.

What should you learn next?
The catalog includes many tools and their prices, for example, a base station for fooling mobile networks and cell phones is $40,000, bugs disguised as USB plugs are $20,000, and there are also cheaper rigged monitor cables for spying on targets' monitors.
"The catalog even lists the prices for these electronic break-in tools, with costs ranging from free to $250,000. In the case of Juniper, the name of this particular digital lock pick is FEEDTROUGH. This malware burrows into Juniper firewalls and makes it possible to smuggle other NSA programs into mainframe computers. Thanks to FEEDTROUGH, these implants can, by design, even survive "across reboots and software upgrades. In this way, US government spies can secure themselves a permanent presence in computer networks. The catalog states that FEEDTROUGH has been deployed on many target platforms."
The articles also reveal how the NSA and its allies tapped major undersea cables analyzing bulk internet traffic. The leaked documents report that, on Feb. 13, 2013, TAO "successfully collected network management information for the SEA-Me-We Undersea Cable Systems (SMW-4)." With the help of a "website masquerade operation," the agency was able to "gain access to the consortium's management website and collected Layer 2 network information that shows the circuit mapping for significant portions of the network."
"One document labeled top secret and not for foreigners describes the NSA's success in spying on the SEA-ME-WE-4 cable system. This massive underwater cable bundle connects Europe with North Africa and the Gulf states and then continues on through Pakistan and India, all the way to Malaysia and Thailand. The cable system originates in southern France, near Marseille. Among the companies that hold ownership stakes in it are France Telecom, now known as Orange and still partly government-owned, and Telecom Italia Sparkle."
To Protect and Infect
The story starts when the popular cryptographer and activist Jacob Appelbaum took to Der Speigel the pages of a catalog of backdoors, monitoring programs and many other spying tool-kits.
Appelbaum made an interesting speech at the 30th Chaos Communication Congress on the militarization of the internet, exposing the content of the precious NSA catalog. Appelbaum confirmed to have received the top-secret documents by Edward Snowden. They're more evidence of the scale of surveillance operated by the NSA worldwide.
"Their goal is to have total surveillance of everything they're interested in. There really is no boundary to what they want to do. There is only sometimes a boundary of what they are funded to do and the amount of things they are able to do at scale. They seem to do (those things) without thinking too much about it. And there are specific tactical things where they have to target a group or individual, and those things seem limited either by budgets or simply by their time. The NSA has retarded the process by which we secure the Internet because it has established a hegemony of power in secret to do these things."
Appelbaum described the internal organization of the NSA, in particular of the existence of an elite team of hackers known as the agency's Tailored Access and Operations unit, or TAO. The cyber security expert described their major products, including deep-packet inspection (e.g.TURMOIL) and a series of off-the-shelf or zero-day exploits ready to be injected into a data stream to compromise a vulnerable machine.
What's nteresting is the proof of concept on the FoxAcid infrastructure proposed by Appelbaum. Let's remember that the system was able to make a real time analysis of targets choosing the most efficient exploits. Appelbaum revealed the existence of QUANTUM-X tools which includes a set of zero days, man-on-the-side attacks and much more.
Of course, the NSA also has the best technology for internet monitoring and mobile surveillance, anything could be intercepted.
Digging in the Catalog
In the days after the disclosure of the NSA catalog, many websites reported the news, focusing their posts on the spyware codenamed DROPOUTJEEP. That spyware was designed by the intelligence agency to spy on every Apple iPhone, but the pages of the catalog are a mine of interesting information. I decided to focus my attention on those products, still not analyzed by the media, that appear to be powerful tools for cyber espionage and surveillance.
What I've found very interesting is a set of components designed by the NSA to spy on computer screens, fax/printers, audio devices, keyboards and mice, by not even having to install an agent on the target machine. The systems are based on continuous wave irradiation. The tools belong to the ANGRYNEIGHBOR family of bugs. The series of bugs implemented as RF retro reflectors communicate with the use of an external radar wave generator such as CTX4000 or PHOTOANGLO. Appelbaum at the Chaos Communication Congress confirmed the existence of the device (CTX4000 or PHOTOANGLO), described as a portable continuous wave generator. He added that it's remote controllable and works in combination with tiny electronic implants to bounce waves of energy off monitors, keyboards and printers to analyze what has been respectively viewed, typed and printed.
The ANGRYNEIGHBOR family of bugs is considerably revolutionary, because it works even if the target device isn't online, enlarging the possibility of an attack for NSA agents.
"This (CTX4000) is a continuous wave generator or continuous wave radar unit. You can detect its use because it's used between one and two gigahertz, and its bandwidth is up to 45 megahertz, user-adjustable, two watts. Using an internal amplifier, external amplifier, makes it possible to go up to one kilowatt."
The VAGRANT collection requires a continuous RF generator such as the CTX4000 or PHOTOANGLO. Meanwhile, the returned signals are processed and displayed by components like NIGHTWATCH, GOTHAM, LS-2 (with an external monitor) and VIEWPLATE.
The signals are processed by specific systems, depending on the nature of the spying devices. The VIEWPLATE unit was used for VAGRANT video signal analysis, LOUDAUTO for ambient audio interception, DROPMIRE for printer and fax scanning, RAGEMASTER for video capturing and SURLYSPAWN to tap keyboards and mice used by the target.
In the image below, I tried to figure out the entire collection of NSA radar wave devices that were disclosed recently.
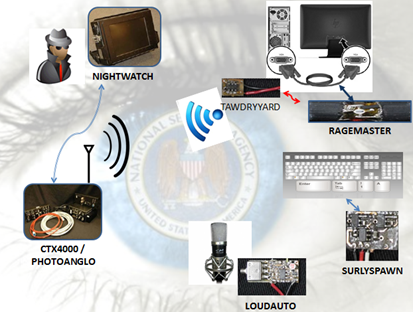
Figure - NSA Radar wave devices
The CTX 4000 and PHOTOANGLO
The CTX is a portable continuous wave radar that can be used to illuminate a target system to extract information even if it's offline. The tool is a powerful "weapon" to collect signals that are extremely difficult to analyze in other ways. The device, as reported in the catalog, is primarily designed to work with the VAGRANT and DROPMIRE collection, and it's remote controllable.
According to a list of NSA Exploit Tools released by Le Monde:
- VAGRANT: Collects from computer screens (this is present at the French mission to the UN.) It's able to collect data from open computer screens. According to the Indian The Hindu publication, the NSA planted bugs at Indian missions in Washington D.C. And the U.N. This building was on the list of NSA "targets," for the operation, the use of the Highlands and Vagrant tools have been documented, to collect data from implants, and computer screens respectively. The NSA was interested in India's space program, as reported by The Hindu, due to that reason, strategic Indian offices and agencies were tapped.
-
DROPMIRE: A passive collection of emanations using an antenna. It's basic TEMPEST stuff, so it's part of the methods of investigation and study of compromising emanations (CE.) It could be a small antenna hidden nearby, maybe even in a "bug," or a larger and better antenna offsite. Dropmire is the codename for a secret surveillance program of the National Security Agency, geared to the surveillance of foreign embassies and diplomatic staff. At least 38 foreign embassies were controlled since 2007. Dropmire was the "bugging" method implanted on the Cryptofax at the EU embassy, D.C., according to a 2007 document partially published by The Guardian. An image included in the document was presumably taken from a transmission traveling over a targeted device.

Figure - ANT CTX4000
The scenario of attack is very attractive. A spy could intercept data from a laptop by simply targeting it with the above instruments. CTX4000 and NIGHTSTAND could be used to access personal computers of which it's not possible to directly access.
The CTX4000 was in phase-out in 2008, to be substituted by PHOTOANGLO system, a joint project made by NSA and the British GCHQ. The new device has limited dimensions. It could be fitted into a slim briefcase, and its weight is less than 10 lbs.
PHOTOANGLO is able to generate an un-modulated, continuous wave signal. The system amplifies a signal, and sends it out to an RF connector, where it's directed to an antenna. The antenna allows the attacker to illuminate the system to spy on. The price of PHOTOANGLO is $40,000 USD.
The NSA's offerings include a family of bugs implemented as RF retro reflectors. The devices communicate with the use of an external radar wave generator (CTX4000 or PHOTOANGLO). The signals are then processed by other components. such as VIEWPLATE (for the VAGRANT video signal.) The intelligence agency used different devices. depending on the nature of the target:
- LOUDAUTO for ambient audio spying
- DROPMIRE for printer/fax analysis
- RAGEMASTER for video spying
- SURLYSPAWN for keyboard/mouse spying
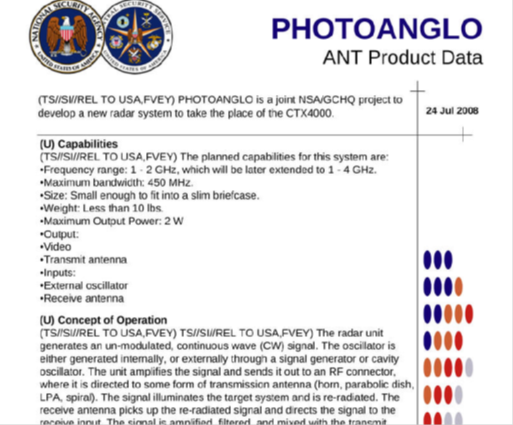
Figure - PhotoAnglo Tool
RAGEMASTER
Ragemaster is considered to be an essential component for video spying. As reported in the catalog, it's an RF retro reflector, usually hidden in a normal VGA cable between the video card and the video monitor. Ragemaster is an enhanced radar cross-section, and is installed in the ferrite of a video cable. The unit is very cheap, it costs $30. It's an essential component in VAGRANT video signal analysis. It represents the target that's flooded for the analysis of the returned signal. The Ragemaster unit taps the red video line in the signal, between the victim's computer and its monitor. The processor on the attacker side is able to recreate the horizontal and vertical sync of the targeted display, allowing the viewing of content on the victim's monitor.
Using Vagrant video signal analysis, an attacker could reconstruct the content displayed on the victim's video simply by illuminating the Ragemaster by a radar unit. The illuminating signal is modulated with red video information. When the information returns to the radar unit, it's demodulated and processed by external monitor such as GOTHAM, NIGHTWATCH and VIEWPLATE.

Figure - RAGEMASTER component
NIGHTWATCH
NIGHTWATCH is an essential component of the overall architecture. It's a portable computer specifically designed to process progressive-scan VAGRANT signals. It has specialized hardware, with an armored case equipped with PCI digitizing, and clock cards to support the accurate reconstruction of the video signals that are captured. The system provides video output, to allow the spies to view the content of targeted displays.
The video output comes from radar units like CTX4000 and PHOTOANGLO, or generally from any other receiver. The unit has a "Sync Lock" feature, and frame averaging to improve the readability of a targeted monitor. NIGHTWATCH is in phase-out, the system is being replaced by the VIEWPLATE system.

Figure -NIGHTWATCH Tool
SURLYSPAWN
SURLYSPAWN is a data RF retro-reflector. It's used to return modulated signals from targeted systems when they're illuminated by a radar unit. Its primary use it to collect keystrokes on the target without installing any malicious software to spy on them. It only needs the targeted system to be touched once.
The device taps into a data line from the keyboard to the processor. The work procedures are very simple and efficient. The board generates a square wave oscillating at a preset frequency. The unit is able to modify by acting on the frequency in the function of the signal. When the targeted device is illumined by a CW Radar Unit, the signal is re-radiated to the radar, where it's demodulated to recover the keystrokes intercepted. SURLYSPAWN could be used to collect keystrokes from both PS/2 keyboards or USB. The catalog announces that future version of the device will be able to capture signals also from laptop keyboards.
SURLYSPAWN is insidious, thanks to its shape and design. It allows the form factor to be tailored to respond to any specific need. Also, this system appears to be very cheap, just $30 for each item.

Figure - The SURLYSPAWN Tool
TAWDRYYARD
TAWDRYYARD is a beacon RF retro reflector, used to provide a return signal when it's illuminated with radar. It provides the vague positional location of RAGEMASTER units. It's easily localizable within a 50° radius of the radar system being used to illuminate it. The system could be powered for many months by a standard lithium battery with a count cell format. making the unit ideal for any operational need.
When TAWDRYYARD is illuminated with a CW signal, the signal is re-radiated and captured by the radar that transfers it to the unit that processes it to recover the clock signal. All the components of TAWDRYYARD are commercial, off-the-shelf, and aren't the result of specific NSA designs. The overall unit costs around $30.
The catalog anticipates that future versions of TAWDRYYARD will provide GPS coordinates of the target and its ID, to allow an automatic scan process of an area of interest.

Figure - The TAWDRYYARD Tool
Conclusions
As reported in the content of this article, "Radar Wave" monitoring is a reality, a collection of powerful devices that exploit radio waves to spy on targets, instead of using malware or directly tapping on communication cables.
In my opinion, these devices are the last frontier of technology for espionage purposes. We've read about them many times, but never has an official document confirmed their existence.
The catalog by Snowden illustrates the capabilities of the NSA in the surveillance field. The agency has developed all kinds of tools and has the knowledge to exploit practically every technology.
Let's think of the numerous times the agency has already used the technology present in the catalog for covert operations. The power of the NSA is difficult to imagine at this moment. The only way to limit it, unfortunately, is with a technical and political resolution as confirmed by Appelbaum.
"Encrypting the Internet ends it all in a sense, but it will come back in another sense. We need a marriage of a technical and political solution. We don't have those two things yet so we're stuck here. At the moment, I feel the NSA has more power than any one person or agency in the world."
References
http://cryptome.org/2013/12/nsa-ant-raumuber.pdf
http://cryptome.org/2013/12/nsa-catalog-appelbaum.pdf
http://www.democracynow.org/2013/12/31/jacob_appelbaum_futuristic_sounding_radar_wave
https://leaksource.wordpress.com/2013/12/30/
http://securityaffairs.co/wordpress/20819/intelligence/tao-nsa-backdoor-catalog.html





