The Mechanics of Metasploit
Metasploit is exquisitely prevalent amongst penetration testers and especially hackers because it makes it very easy to develop and launch exploits for software vulnerabilities. This paper exclusively demonstrates how to configure and practice Metasploit, which is a penetration testing platform for developing and launching exploits. This research paper primarily offers specification for subsequent contents:
- Introduction
- Prerequisite
- Metasploit Core
- Launch Pad Configuration
- Metasploit Modules
- Metasploit Utilities
- Importing Exploits to Metasploit
- Exploit Repository
- Synopsis
In 2003, a storm called Metasploit entirely changed the cyber security atmosphere because everyone, even computer security laymen, started detecting vulnerabilities in existing systems and became hackers by exploiting them. Metasploit is a free, open-source tool designed to developed exploits for various operating systems and frameworks. However, today it is more used especially by both penetration testers and hackers to assess loopholes. Metasploit could be referred to as a separate hacking operating system itself; it contains sophisticated commands to manipulate exploits and even has a couple of diverse interfaces. So this article guides the aspiring penetration tester in how to use its commands, how to determine which exploit works, how to add new exploits in the database, and how to launch an exploit.

What should you learn next?
Prerequisite
We'll spend the majority of this article showing Metasploit examples. The aspirant should be proficient in configuring a penetration testing lab, which includes all significant tools. Apart from tools, he must have a good understanding of Ruby Programming Language and network configuration skills, because we are going to confront with a majority of network-related operations. This article lab also assumes reasonable familiarity with Linux, as well as with the following tools and technology:
- BackTrack 5
- Metasploit Modules
- Network Connectivity
- Ruby Programming
- Windows OS (Optional)
Metasploit Core
The Metasploit framework is a unified exploit database with an easy update mechanism. Because it is open source in nature, we can easily manipulate it to suit our needs; for instance we can write our own code to exploit vulnerabilities and could deploy that newly compiled exploit into an existing Metasploit database.
The framework was written in the Ruby language and includes various components written in Perl Scripting, C, Assembler, and Python. It is basically designed for Linux operating systems, thus its command structure has a close resemblance with the Linux command shell, but nowadays, it supports all major operating systems such as Windows, Solaris and Mac. It has a consistent interface for configuring options and executing exploits and isolating exploits from payloads. Metasploit uses the following terminology to carry out a specific type of attack and make the act of exploitation portable:
Exploit
Exploits are typically piece of malicious code that manipulates a particular vulnerability in a computer system. Metasploit provides masses of exploits across multiple operating systems and applications, giving you many ways to attempt to breach a computer. Vulnerability can be detected by running a couple of scanning tools like Nessus and Nmap, which are exploitable by employing Metasploit. In the case that we identify a specific vulnerability and are unable to find its corresponding exploit definition in the existing Metasploit database, then www.exploit-db.com proves to be a great resource or database of updated exploit where we can download the updated exploit source code and later we can port it as a module in the Metasploit database.
Payloads
Once we have identified the vulnerability and are ready to exploit it, the next step is to set up a payload which determines what happens once the exploit succeeds. The payloads are essentially used to get access to the remote computer reverse shell and penetrate it to implant malicious code into the victim computer.
Encoders
It is not guaranteed that every exploit that you fire from Metasploit will surely work. It is likely that some victim computers would have been configured with filtering mechanism such as firewall, antivirus and IPS. The moment any exploit tries to penetrate the remote computer, such filtering mechanisms would deny such unrecognizable communication. So the encoder basically needs to encode the exploit definition in order to bypass or thwart the remote computer IDA, IPS, and antivirus.
Options
Each exploit and payload has some in-built parameters such remote host IP, local host IP, LPORT, RPORT, server path, username, etc., which need to be configure before exploiting. These options could be confirmed by the SHOW OPTIONS commands in the Metasploit.
Zero Day
Hackers exploit particular loopholes in the software or system to penetrate it, and the vendor of such products in reaction finds the patch against exploitable vulnerabilities in order to thwart future penetration. It is not necessary that they release a patch for every vulnerability, because some exploits are still undetected or not disclosed yet. Such special exploits are considered to be Zero day exploits.
Launch Pad Configuration
Metasploit can be launched either from Windows or Linux sperating systems separately or via an integrated tool called BackTrack. It is recommended that Metasploit should be run from Backtrack, which mandates some initial configuration services in order to implement the exploitation properly. After logging in to the BackTrack 5 using root as user name and toor as password, we are going to configure and start these services and packages as following.
Update BackTrack 5
It is recommended to update the existing BackTrack in order to get new or updated specification about the tools and exploit. Thus, we can update BackTrack using this command:
# sudo apt-get update
Starting Networking Service
After login into BackTrack, the IP address is usually not assigned automatically. We have to fire these commands in order to start or stop networking services:
# service networking start
# service networking stop
Apart from that, we can also use the following commands to start networking services, because subsequent commands always work accurately, unlike earlier as:
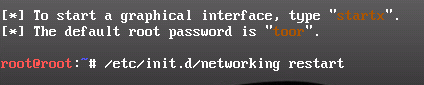
You may find that after rebooting your BackTrack machine, the networking service needs to be started again. To make the networking service start automatically, you can give the following command:
# update-rc.d networking defaults
Setting Network Connection
In case the aforesaid commands won't work, then we have to set up the network connection manually in order to resume communication, which is an important step because we are performing penetration testing to a remote computer. So, it is mandatory that both victim and hacker machines must at least ping each other properly. Typically, we can assign IP address either by DHCP or through manual process (Static IP Address). We can obtain an IP address using DHCP through this command:
# dhcpcd eth0
If a dhcpcd package is not present, then install it from this command:
# sudo apt-get install dhcpcd
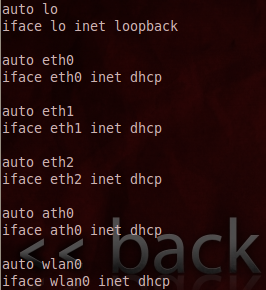
BackTrack has couple of interfaces for wired network, loopback and wireless networks, and assigns them different names. We can double-check through vi
/etc/networking/interfaces commands to confirm which one obtains the IP address from DHCP.
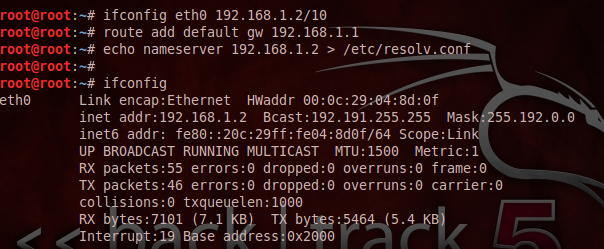
If DHCP malfunctioned due to some reason, then we can assign a static IP address using the following procedure, where we are manually assigning the IP address as 192.168.1.2, the default gateway and DNS server to the system.
Refreshing Network Interfaces
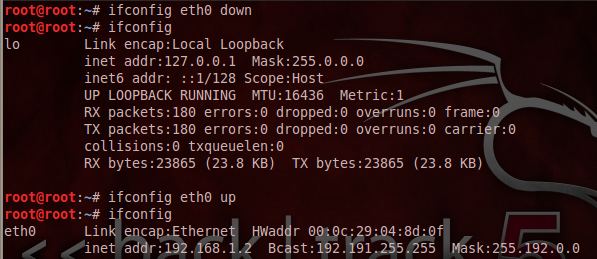
Occasionally, we can refresh various network interfaces such as both wired and wireless using these commands as in following figure where we first down the wired eth0 interface and then up it again:
Wireless Connection
We can use wicd program to connect to a wireless access point. We can start wireless networking services using these commands:
# /etc/init.d wicd start
FTP services
Sometimes, we need to transfer files or data to the victim machine back and forth or plant a backdoor like netcat.exe in the victim computer, which runs as a covert process to maintain access. Thus, Tftpd daemon is very useful in such situation. First, install this server using apt-get command and do rest of the configuration as follows:
# atftpd --deamon --port 69 /tmp
HTTP Server Configuration
It is required to configure a web server in order to host files or to target web-based exploits. BackTrack has an in-built installed Apache server which just needs to be started as:
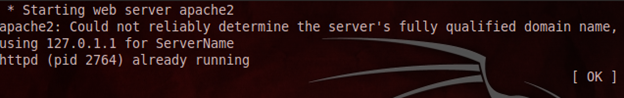
Metasploit Modules
Metasploit typically has three interface modules to execute any exploit: Console, Command Line and Web. It actually doesn't make much difference which modules you have chosen to exploit the computer, but in general, the console is the most fully featured and powerful among the three. BackTrack has a separate segment where all exploits reside, and we can even run Metasploit modules from there.
It is highly recommended to update the existing Metasploit exploit database before executing exploitation, as it is changed time to time. We need a working Internet connection and to fire this command as follows:
# ./msfupdate
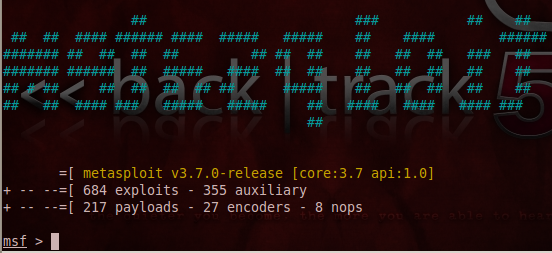
Msfconsole
Msfconsole is the most competent, powerful, and all-in-one centralized interface infrastructure for penetration testers to make the best use of the exploitation framework. We can consume msfconsole to launch an exploit, load auxiliary modules, perform enumeration, create listeners, or run mass exploitation against an entire network. To access "msfconsole", go to BackTrack | Exploitation Tools | Network Exploitation Tools | Metasploit Framework | Msfconsole, or use the terminal to execute the following commands:
# cd /pentest/exploits/framework3/
# ./msfconsole
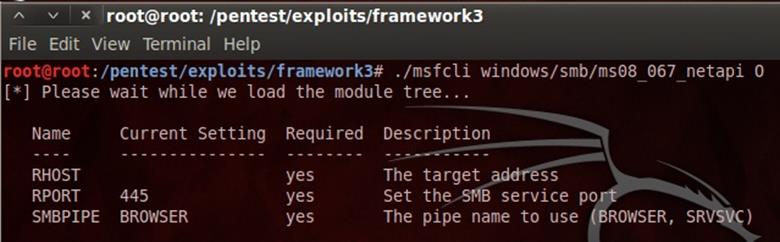
Msfcli
Msfcli is a command-line interface that renders an extensive range of modules that can be launched at any one instance collectively. It is different from msfconsole in many ways because it puts the priority on scripting and interpretability with other console-based tools, while msfconsole provides an interactive way to access all features in a user-friendly manner. However, it is substandard and lacks some of the advanced automation features when compared to msfconsole. To access msfcli, go to BackTrack | Exploitation Tools | Network Exploitation Tools | Metasploit Framework | Msfcli, or use the terminal to execute the following commands:
# cd /pentest/exploits/framework3/
# ./msfcli
This will display all the available modes similar to that of the MSFConsole and use instructions for selecting the particular module and set its parameters as follows:
Msfweb
This is another module of Metasploit for penetration testing. Everything like exploits and payloads comes as a form of GUI interface and makes the pen tester's job easy. Mfsgui starts a Metasploit web server on 127.0.0.1 port 55553 when its services starts from the console. We can start this interface by following commands as:
# cd /pentest/exploits/framework3/
# ./msfgui
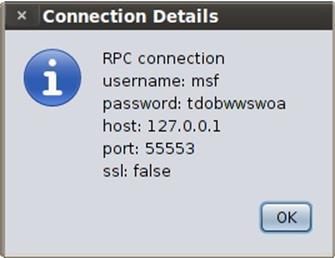
We can confirm the login credential from File menu, by which msfgui logged in as follows:
Metasploit Utilities
Metasploit utilities are candid interfaces to particular characteristics of the framework that can be advantageous in specific situations, especially in exploit development. Metasploit offers these special utilities as:
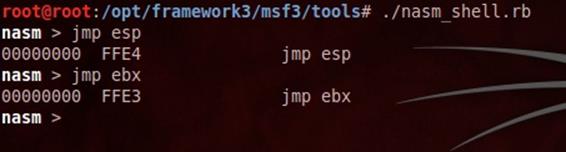
NASM
This utility could be useful when you're directly confronting with assembly code, especially if, during exploit development, you need to recognize the opcodes (the assembly instructions) for a given assembly command. NASM is just a Ruby Programming made file which can be found in the framwork3 | msf3 |tools directory and put in the scenario as follows:
Msfencoder
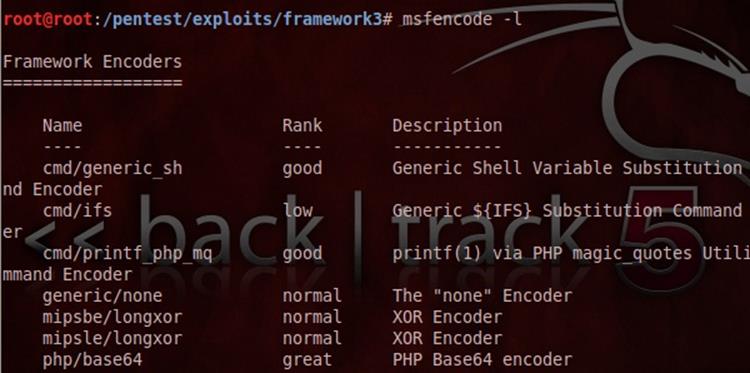
Metasploit comprises a number of different encoders for specific situations. They contains null characters that, when interpreted by many programs, signify the end of a string, and this will cause the code to terminate before completion. Metasploit assists you to avoid bad characters and evade firewall, antivirus and IDSs by encoding the original payload in a way that does not include "bad" characters such as xoo and xff, which terminate the payload. We can go through with msfencode option with msfencode –h command and list the available encoders as follows:
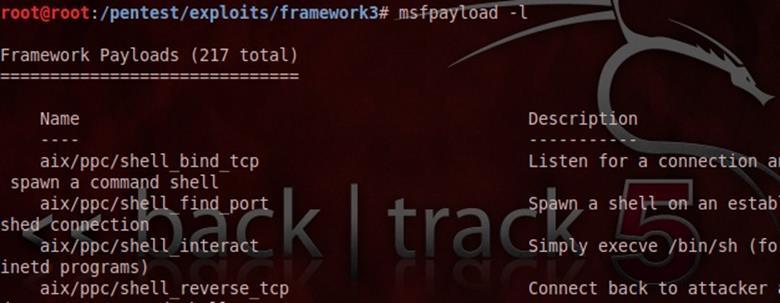
Msfpayload
The msfpayload allows you to generate shell-code, executable, and much more in order to import exploits outside of the framework. Shell-code typically can be generated in many formats including C, Ruby, and Visual Basic for Applications. Each output format will be useful in specific circumstances.
Importing Exploits to Metasploit
We are not limited to rely only on built-in exploits of the Metasploit framework. We can create our own custom exploit by using C, Ruby, Python and Perl programming languages, or even directly import the exploit from the third party resources and later add them into the existing Metasploit exploit database. We can view the list of available exploits in the pentest | exploits | frameowrk3 | modules | exploits directory, where exploits are categorized according to their platform as follows:
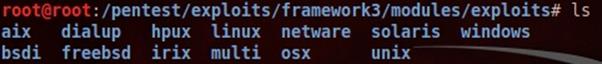
But in the BackTrack 5 initial version, we won't be successful to update the existing exploit database, even if we add new exploit definition. We can however do this properly in the BackTrack 5 Service Pack 2 version, where we have to create a directory in the opt | Metasploit | msf3 | modules | exploit and put the exploit code file over there. Later, run the msfupdate command to make changes in the exploit database.
It is not necessary that you place the newly devised exploit source code in the Metasploit exploit database folder. You can run them directly instead.
Exploit Repository
Vulnerabilities have been disclosed time to time with the proof-of-concept exploit code to demonstrate the feasibility and viability of a loophole detected in the specific software or operating system, but many still remain unaddressed. Publicly available exploit and vulnerability information makes it easier for penetration testers to quickly search and retrieve the best available exploit that may suit their target system's environment. We have provided a combined set of online repositories that may help us to track down any vulnerability information or its exploit by searching through them. The following table represents some of resources of exploit databases:
URL
We can also access a majority of exploits in the exploit-db.com database in BackTrack itself. Here is the procedure:
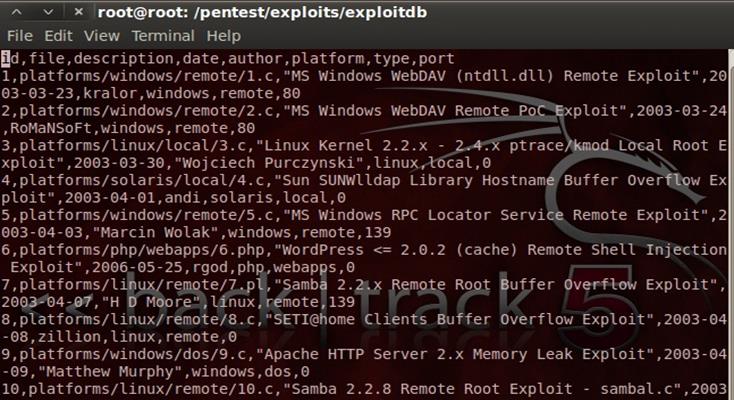
# cd /pentest/exploits/exploitdb/
# vim files.csv
The vim interface produces an overview of all resided exploits in .csv file format as follows:
Synopsis
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
We have encountered the basics of Metasploit and were overwhelmed by its many interfaces, options, utilities, variables, and modules. This paper briefly covers the operations of various Metasploit special tools such as msfencode and Nasm shell, and demonstrates how to launch an exploit to penetrate a remote computer using various user interfaces that Metasploit has to offer such as msfcli, msfconsole and msfgui. We will dive much deeper into msfconsole, msfcli, msfpaylods and other interesting concepts of Metasploit as we explore exploit development in later papers of this series.






