Introduction to RFID Security
1. Introduction
Radio Frequency Identification, also known as RFID, is a technology that was created by Léon Theremin in1945 and later patented by Mario Cardullo in 1973. It was first developed by Léon Theremin as a spy device for the Soviet Union government. The device itself could transmit a sound within a radiowave. The device itself was an early example of RFID technology, even though it worked as a passive spy device and not as an ID.

What should you learn next?
RFID is classified as passive, active and semi-passive. Active RFID uses a battery and can operate in a range of about10 m, and passive RFID can operate in a range of about 20 cm. This is an example of a passive RFID card that was used as a public transport ticket.

Picture 1. Internals of passive 13.56 MHz Mifare RFID ticket.
The picture above is an RFID tag which has had the cover removed using acetone. You could see the internal device consisting of a coil and a tiny integrated circuit. The table below contains a couple of frequently used RFID tags and their frequency:
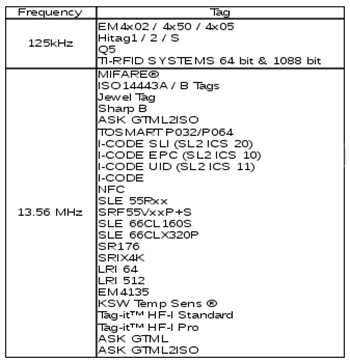
Picture 2. RFID tags and their working frequency.
2. Modulation
Most RFID tags were using ASK (Amplitude Shift Keying), FSK (Frequency Shift Keying) and PSK (Phase Shift Keying) for its analog modulation.
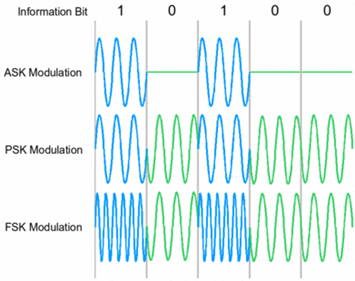
Picture 3. RFID modulation.
For encoding, most of them are using NRZ, Manchester, Unipolar RZ, DBP (Differential Bi-Phase), Miller and Differential Coding on PP Coding.
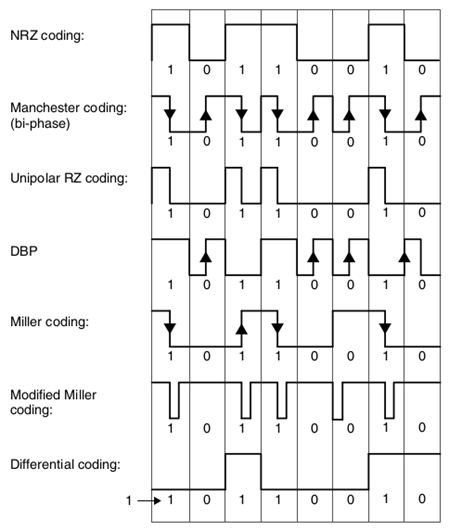
Picture 4. RFID encoding.
3. Problem
The main problem with RFID is related to its frequency. Someone with specific tools and enough knowledge on RFID (including complete documentation) could analyze the working frequency of an RFID tag and then decode the data or perform an attack such as cloning the RFID or doing a Denial-of-Service attack.
4. Attack
4.1 Cloning an RFID Tag

Before you could clone an RFID tag, first you should know its working frequency. For this demonstration, I will use the EM4xx tag, whose working frequency is 125 kHz.
Picture 5. RFID tag that will be cloned.
We are sniffing the packet in order to know the data being sent by the RFID tag. First, we should know the working frequency of the target RFID tag using an oscilloscope. This is what the signal looks like between the card and the reader:
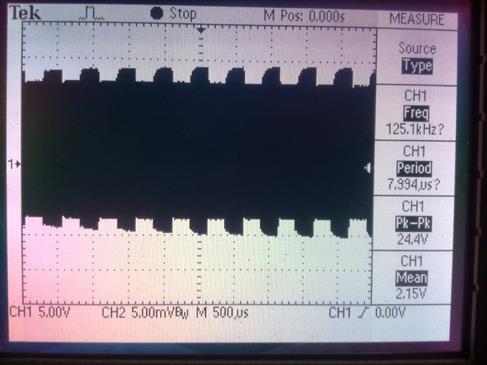
Picture 6. Using an oscilloscope to get the RFID working frequency.
From the picture above, we know that the target RFID tag working frequency is 125 kHz with ASK modulation. Next, we should filter out and separate the carrier and the data. Because the ASK modulation is using amplitude, the filter that we build should also work as an envelope detector. After packets go through the filter, it should look like this:
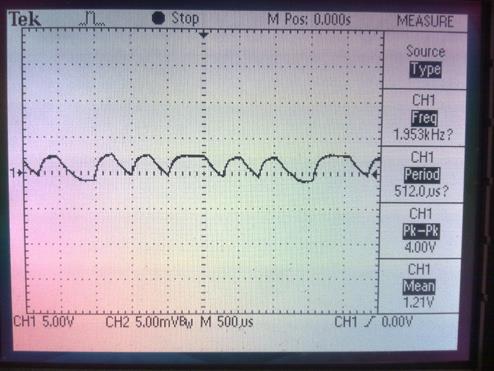
Picture 7. Analog signal data from EM4xx RFID tag.
The picture above shows the data signal that has been separated from its carrier signal. We could also see that the signal is still in analog. Next, we should convert that analog signal into digital signal so it could be easy for further processing and analysis. For this to work, we are going to use a comparator and amplifier circuit. When then signal goes through this comparator and amplifier circuit, it will be converted into a digital signal that could be fed into a microcontroller for further processing. That digital signal looks like the picture below:
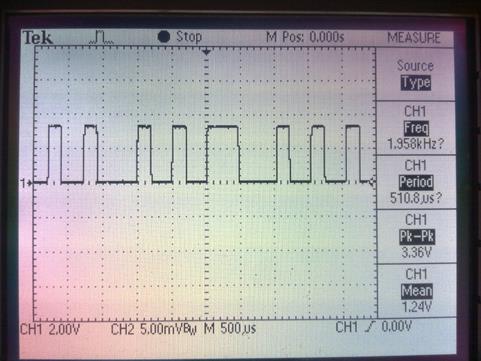
Picture 8. Digital signal data from EM4xx RFID tag.
Even if we have converted the analog signal to digital signal, it is still difficult to know when the data was sent, because our oscilloscope didn't have support for that kind of analysis. We are going to use a logic analyzer for analysis in order to know the pattern of that digital signal. This is what the digital signal captured during that process looks like:
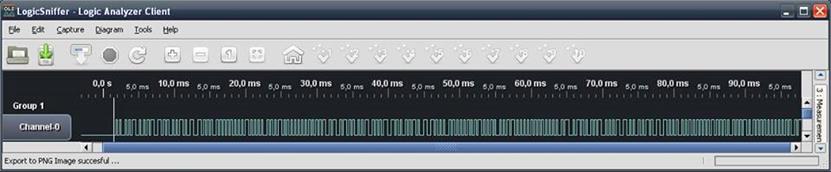
Picture 9. Sniffing packets using a logic analyzer.
As shown in above picture, data transmission started at 15 ms and ended at 47 ms. From a couple of documentations, we could see that the data above is using manchester encoding. And because the signal came from an EM4xx tag, we can see that the signal begins with nine logic "1". We could now calculate the start and the end of that signal, but before we continue and build a manchester encoder application to process the data, we should first analyze every byte in the data. Because the logic analyzer doesn't have a feature for decoding, we should decode it manually as in the picture below:
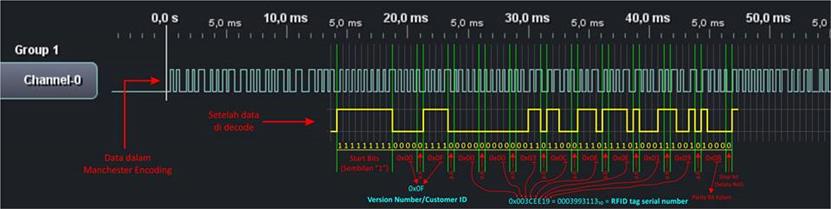
Picture 10. Decoding the packet manually.
-
Header
The header consists of nine bit logic with value of "1". It is quite easy to spot the header because of the consistent bit value.
-
Version Number or Customer ID
This part and the next that follows could be easily decoded because we have already found the header part. The version number or customer ID part is right after the header. It consists of 10 bit which is divided into two parts. The first part is 1 high nibble with 1 bit parity and 1 low nibble with 1 bit parity. On this case, we found that the customer ID value is 0x0F.
-
Data Bits or Serial Number
Data bits is located right after the customer ID part. This data bits consist of a 32 bit value which is then divided with each 4 bit followed by an even parity bit, so the total size of the data bits is 42 bits.
-
Column Parity Bits and Stop Bit
The last part is column parity bits, which consists of 10 lines of data (2 lines of customer ID and 8 lines of data bits) and ends with a stop bit where its value always set to logic "0". The total size of this part is 5 bits.
After successful decoding, we finally build a standalone device (which later is named "Berdikari – Standalone RFID Reader & Emulator") that could automate the process of reading a tag and then working as an emulator. This device still under development:
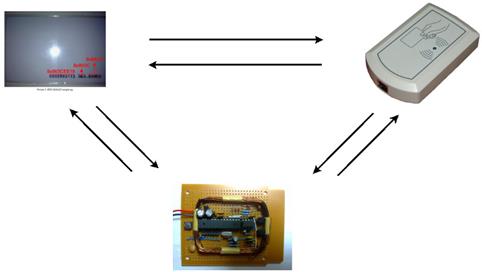
Picture 11. Using "Berdikari" for reading and as emulator.
4.2 RFID Denial-of-Service
This kind of attack is actually just flooding the RFID reader with lots of traffic. This could be accomplished by using a device that works in the same frequency as the RFID reader and transmitting data over and over again (flooding), thus preventing other tags from accessing the RFID reader. This is an illustration of such an attack:

Picture 12. RFID Denial-of-Service.
5. Conclusion
From the above examples, we could conclude that RFID technology still has some security holes, including data manipulation, that could be exploited by attackers.





