Improving the Human Firewall
Learn the best practices for developing a security awareness training program that is engaging. Engaging awareness programs have been shown to change more users' behavior and are seen as an asset for your organization instead of annoyance.

Two year's worth of NIST-aligned training
Deliver a comprehensive security awareness program using this series' 1- or 2-year program plans.
-----------------------------------------------------------------------------------------------
Introduction
Most likely you will agree that security education is the thing that needs enhancement the most in companies worldwide – it is pointless to expend millions of dollars on the most recent software and hardware to defend the corporate networks against all kinds of internal and external threats only to get your systems exposed because an employee was tricked into divulging his credentials, just as Kevin Mitnick stated. The saying goes: "A chain is only as strong as its weakest link" and it is tightly related to information security as attackers test all possible points of access for vulnerabilities and usually choose the least resistant one.
A report from Wisegate, a peer-based IT knowledge service, states that the threat from inner computer users is one of the biggest concerns when it comes to protecting corporate data. Furthermore, Wisegate claim that user security awareness was a top concern in 2013. Most companies already do training and have a relatively high expenditure on computer-based training programs. These trainings just do not prove as efficient as they are planned to be. The key issue here is to differentiate between training and education – training employees involves actions while educating them involves results. The main goal of security awareness programs has to be aimed not at training the staff but at educating them and making them aware of the ways human psychology can be exploited. Hence, you need to bring effective results on the table instead of performing more and more actions.
To achieve these results you need to make your staff grasp the concepts you are teaching them to the extent that it permits them to act properly when confronted with new situations. This means that your staff has to internalize the knowledge and information provided by your security awareness program. This cannot be achieved merely by conducting training, leaving notes and hanging up posters.
Isn't the average Internet user already aware of the security issues that he might be confronted with?
To illustrate our point, we looked at the trends in Google search for the following keywords:
The following results were shown:
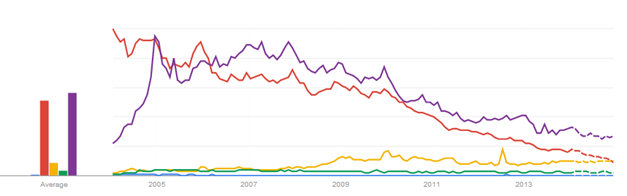
The results show that the trend of the search volumes for malware and phishing is highly inelastic (static). Compared to the search queries for keygens and torrents, the relative search volume of phishing and malware is quite small between 2004 and 2007. There is no data for the word social engineering for most periods due to its low demand. We see from the red and purple curve above that between 2004 and 2007 many Internet users demanded keygens and torrents to get illegal access to paid software (at a generally declining rate) but their awareness of possible implications of keygens such as malware and social engineering remained relatively stagnant. From year 2008 up to now we see a slight increase in the search tendency for malware and phishing while the query tendency for keygen and torrents have been falling at an increasing rate and the forecast is that the queries for keygens and maybe torrents are going to fall below those of malware and phishing. Still, we can see that security awareness has had some impact on the behavior of Internet users, making them stray from the dark side of the Internet. Nonetheless, this decline of piracy and risky behavior is also due to other reasons such as better enforcement of copyright laws, removal of access to websites with illegal contents by ISPs, closure of online businesses operating in the grey market by governments, inter alia.
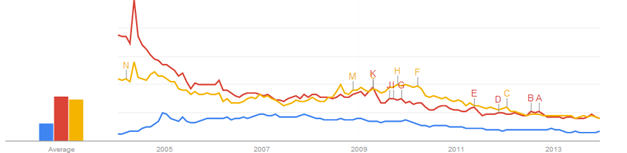
However, if we compare the queries for torrents with the queries for virus and antivirus we get a pretty interesting picture. It appears that nowadays antivirus is as demanded a keyword as virus and more demanded than keygen, torrents, social engineering, phishing, malware. It appears that the end-users rely not on prevention but on post-infection treatment as a safety mechanism. Also, the keywords virus and anti-virus are more trending than torrents and multiple times more popular than social engineering, phishing and malware which pinpoints the low safety precautionms of the average Internet user as responsibilities for Web safety appear to end with installing anti-virus software and ignoring the safe use of the Internet. Related queries for "virus" appear to be "anti virus", "virus download", "antivirus", "virus scan", "free anti virus", "avg", "avg virus", "virus removal", "virus protection", among others which show the overall direction of the users' input in terms of the keyword "virus".
We can conclude from the above illustrations that the need for Web safety and security awareness is as high as ever pinpointing the need for ameliorating the current security awareness programs that companies undertake.
If I have to educate and not train, what should I change?
Firstly, you should start by organizing group lunches with a security-oriented purpose. Each employee would appreciate a good lunch and/or dessert so the attendance of such meetings will be high. Such an informal meeting is a great way to get your staff together and talk about security issues. Most likely, organizing lunches once or twice a week for different groups will raise the security awareness of your staff without having to resort to dry lectures but by resorting to overall participation and group-wide discussion instead. In these lunches, you can begin to sort out regular attendees who have the potential to become champions within the different work groups and who can later on help educate the other employees in their group.
Secondly, you can try to bring in outside security professionals as they are usually eager to get CPEs (continuing professional education) credits, even more if you add some goodwill gesture. The local security pros may present security issues or discuss security with your employees.
Thirdly, you should provide your employees information on maintaining Internet safety at home. Such discussions are always well-attended, even more so if you show them something relevant to them such as how to keep kids safe at home. The information must really affect them personally and they must find it relevant to make them focused and engaged so that they can absorb it. Links, whitepapers and any kind of training on such topics would be well-accepted.
Fourthly, you should make appointments with business unit leaders to discuss security issues and topics relevant to their area. It does not have to be in the office, more informal settings are also beneficial. The point here is that it is important to show them that you are pondering over their problems and attempting to remedy them, in this way they can understand and help with your concerns as well.
Fifthly, the old way of hanging posters on the wall and dispersing newsletters can also be efficient. The posters have to be attention-grabbing and have to be replaced frequently. A column in a newsletter would be beneficial if it is interesting and relevant. Tips are usually not interesting and relevant as they are self-serving unless they provide some advice on safety at home which automatically makes them relevant.
Sixthly, anecdotes and metaphors may help spread the word. For instance, you can rely on the story of Ali Baba to teach the staff about password security, strength and shoulder surfing.
Seventhly, create a security mentoring/tutoring option. It is possible that nobody sign up for it but if someone does you should enable him to take advantage of such an option. The mentoring may include one-on-one sessions and would help in pinpointing gifted employees as regards to security awareness and would help shape a champion among your employees who would educate the others during the course of work.
Eightly, you should offer your employees ride-alongs whereby you give them the opportunity to take a look at how the IT or security program actually looks like from the inside. The opposite should be done as well – making IT and security staff take a glimpse of how a day in the workplace of the employees looks like may also be useful.
Finally, you should strive to create an environment of teamwork as it is proven that good teamwork has several positive features that come with it, such as:
-
Better problem solving capabilities
-
Quicker completion of tasks
-
Competition which leads personnel to excel at what they do
-
Bringing a combination of different unique qualities on the table may lead to better efficiency in the employees' decision-making (references as regards these four features can be found at the bottom of the article)
As Henry Ford once said "Coming together is a beginning. Keeping together is progress. Working together is success."
Testing the human firewall
Testing the human firewall is easy so you can effortlessly track the company's progress. The first and most employed way to test the human firewall is through written tests which come in the form of online multiple-choice tests and usually take place after a computer-based learning session. Alternatively, you can test the human firewall with a seemingly real social engineering attack. You have various techniques at your disposal for the attack: pretexting, phishing, theft with diversion, tailgating, quid pro quo or any combination of these. You can resort to websites such as phishme.com to fake a phishing campaign against your company, do the attack yourself or hire external security professionals to raise the bar even higher.
Below are 3 sample questions that may be used in multiple-choice tests and 3 open questions that require written answer. Similar questions can be used when testing your personnel's security awareness.

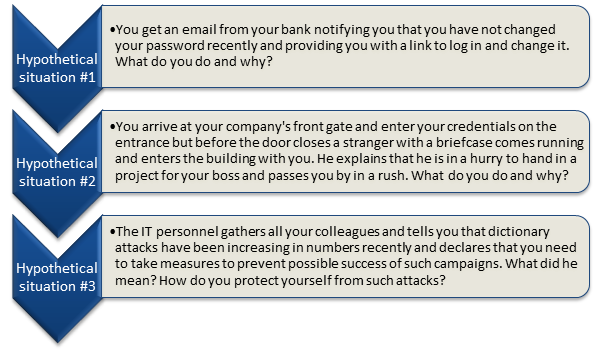
What are some important tips when it comes to improving the human firewall?
-
Simple labels that classify data as protected and unprotected such as "confidential" and "public" are a great place to start.
-
Prohibiting password reuse and teaching the human firewall good password habits is crucial.
-
The security staff has to become more accessible to the employees. This, on its own, will motivate the latter to share their problems and ask questions, on the one hand, and will aid the security staff in assessing the efficiency of their security programs, on the other hand.
-
When reporting the results from security awareness tests, it is preferable to share them either anonymously or statistically. Though, if negative trends arise from particular employees or groups of employees, share those results with the proper persons and attempt to solve those issues without putting any blame on the people who fall behind with their security education.
-
Teach employees not to store any company data on their smartphone
-
Teach personnel not to connect USB drives, external hard disks or any writeable media to the workplace computer
To reduce social engineering attacks against your employees, limit the information that can be gathered about your employees during the reconnaissance stage of the attack (this involves educating them not to divulge too much about information about themselves in the public domain)
-
Remove any organization charts which reveal the employees names, job positions and photos from the company's public website.
-
Teach the personnel to handle external contacts properly through systematic training.
-
Teach the personnel not to respond to accusations instantaneously but to turn to colleagues, legal staff, etc. before handling complaints.
-
Teach personnel to limit the information they provide in social networks and other public domain sources such as Facebook.
Conclusion
It can be concluded from our discussion above that attempts at improving the human firewall have already started worldwide. Their success varies depending on factors such as the preliminary awareness of the factors, the enforceability and rigidity of the laws in the particular country, inter alia. Most methods of improving the human firewall involve modifying strategies that are already taking place in the companies such as transforming the type of information delivered to employees into a way that makes it relevant to the employees and that makes it affect them personally or transforming posters and newsletters in a way that excludes any tips and includes anecdotes and metaphors which will encourage the employees to read these advices and ease them in remembering the rules, whereas some involve a totally new strategy for some companies – like performing ride-alongs so the IT staff can better understand the other employees and vice-versa.
We have also seen that testing the results from such security awareness education does not take a lot of effort but it is highly valuable as it can reveal the weak spots or the weakest links of your human firewall.
Finally, we have provided some advices that resolve relatively recent issues that have emerged as regards to the operation of the human firewall. For instance, prohibiting the storage of company data on smartphones is a one possible solution to the BYOD problem that has emerged only recently.

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
References:
- Richard O'Hanley, James S. Tiller and others, 'Information Security Management Handbook, 6th edition, Volume 7'
- Munir Kotadia, "'Human firewall' a crucial defence: Mitnick", Apr 14, 2005, Available at: http://www.zdnet.com/human-firewall-a-crucial-defence-mitnick-1139188313/
- Laneye, 'Managers under attack', Available at: http://www.laneye.com/intrusion/social-engineering/managers-under-attack.htm
- Business Wire, 'New Research from Wisegate Reveals Why Security Awareness is Top Concern of CISOs in 2013', Jan 23, 2013, Available at: http://www.businesswire.com/news/home/20130123005846/en/Research-Wisegate-Reveals-Security-Awareness-Top-Concern#.Ur6dhNJdVMI
- University of California, MERCED, 'Security Self-Test: Questions and Scenarios', Available at: http://it.ucmerced.edu/security/information-security-awareness-training/security-self-test-questions-and-scenarios
- Ken Hess, 'The second most important BYOD security defense: user awareness', Feb 25, 2013, Available at: http://www.zdnet.com/the-second-most-important-byod-security-defense-user-awareness-7000011738/
- LePine, Jeffery A., Ronald F. Piccolo, Christine L. Jackson, John E. Mathieu, and Jessica R. Saul (2008). "A Meta-Analysis of Teamwork Processes: Tests of a Multidimensional Model and Relationships with Team Effectiveness Criteria". Personnel Psychology 61 (2): 273–307.
- Hoegl, Martin, and Hans Georg Gemuenden (2001). "Teamwork Quality and the Success of Innovative Projects: a Theoretical Concept and Empirical Evidence".Organization Science 12 (4): 435–449




