Human Factors in Information Security Management Systems
It is hard to accept that nowadays, organizations get along without having an astute and decisive information system. Providing a reliable and coherence information system requires a solid security framework that ensures confidentiality, integrity, availability, and authenticity of the critical organizational assets.
Information Security Management System (ISMS) defines to setup a solid security framework and regulates systematic way which information technology can use resources. But technical advancements of ISMS do not always guarantee to secure overall organizational environment. Human factors play a significant role for information security.

FREE role-guided training plans
In particular, human characteristics behaviour impacts information security and ultimately associated risks. This article provides an overview of our research for analysing the human factors and their influence for an effective information security management system.
Research uses force field analysis to understand driving and restraining forces of human issues and consider these forces as goals and obstacles of information security. Then the research will model the human factors whilst attempting to understand the current ISMS situation of an organization and its improvement considering ideal situation. It will provide measures for investment in factors that fulfill the goals of ISMS.
Introduction
Increasingly, information security incidents result from interactions among people who work across organizations in dealing with ISMS. This has major implications for the role of human factors and challenging their roles in the process of information security.
Technology is quite an essential part relating to securing information assets but people are responsible for design, implementation and operation of these technological tools (Lacey 2009; Islam2008). Technology evolved enormously in terms of its advancement, but IS incidents still happen and this can be translated to the failure of ISMS.
As result, the ISMS guidelines and standards face a serious credibility threat. Recent studies concluded various technical, non-technical, and regulatory related issues for the failure of ISMS (D’Arcy et al. 2009; Herzog 2010; Lim et al. 2010). It has been noted that 92% of large organizations admitted, they had information security incidents, which increased 72% in 2010 comparing to 2008 (Deloitte, 2011).
According to this report and as far as this study concerns, UK financial organizations face a real threat from information security risks. Information security studies were primarily focused on the effects of security on computer abuse and misuse without providing any quantification which could assist Chief Information Security Officers (CISO) to make decisions on resource allocations to deal with security threats (Lee et al. 2004, D’Arcy et al. 2009, Kankanhalli et al. 2003).
IS risks have adverse consequences on organizational operations and assets. Security systems do not depend solely on preventing technical problems, but rather, they also depend on humans who use the systems and behave in “a certain way” in the system environment (Alavi et al, 2013). The real challenges are from non-technical forces, i.e., human and organizational issues. Therefore it is necessary to understand and address the issues relating to human factors.
This research proposes a model for analyzing human factors using force field analysis. For this purpose, human factors are considered from author’s previous work, and will be mapping with force field analysis and goal-driven risk management model. This model contemplated human factors into two categories, driving and restraining forces, whilst driving forces promotes goals as objective and expectation from the information security and restraining forces deemed as obstacles as a consequence of ineffective ISMS.
Then the approach identifies current and ideal situation of ISMS in organizations. Finally, the study provides a quantification of human factors in which control actions countermeasure risks, the effectiveness of the actions and possible emerge of new risks. This quantification can be demonstrated in Excel, using responses, which received from interviews in previous study.
Force Filed Analysis (FFA)
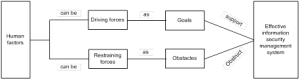
Force field analysis (FFA) has been widely used for management changes in organizations (McMahon, 2010). This technique was developed and introduced by Kurt Lewin (1947). Lewin’s analysis model assesses the impact of all elements and forces, which influence change. These factors can be categorized into two parts, driving forces and restraining forces as presented in figure 1.
Figure 1: Force Field Analysis
This figure provides an overview of FFA in which driving forces verses retraining forces for fulfillment of the effectiveness of ISMS goal.
Driving forces are all forces that coerce for and elevate change. Senior management’s support and mandate is an evident example of driving forces (Marilynn and Bozak 2003).
In contrast, the restraining forces are forces that functioning to hold back the driving forces and prevent a change from happening by creating obstacles and risks. For example, concerns over individual errors could be an obstacle in change goal ISMS strategy.
Strengthening driving forces whilst the elimination of restraining forces, ensures succession of ISMS goals, which is preventing risks by providing cost effective control measures. The human factors concerning FFA are a very subjective matter that requires a measurement in order to be quantified and visualized.
For this purpose, each factor can be assigned with a numerical impact scale. This quantification resulted from interviews conducted in our previous study in two financial organizations which IS incidents occurred.
Force Field Analysis (FFA) and ISMS
It has been widely noted that human factors are subjective matters and require methods to be quantified (Alavi, et al 2012). Using force field analysis (FFA) enables the quantification of human factors in order to assist senior management to make decisions on the allocation of organizational resources for achieving ISMS goals.
The identification of driving forces, which promote IS goals and objectives of organizations will follow with the identification of restraining forces. Every single force will be allocated a numerical scale based on responses that received from people who interviewed in organizations in our last study.
This numerical scale measures the impact factor of each force. Change in the direction of ISMS will be defined by elimination of restraining forces and capitalization on driving forces.
This figure defines a status of the both forces and the direction which organizations must move to achieve an effective ISMS. Modelling this relationship based on force field analysis requires firstly, to understand and to define the current state of ISMS (Marilynn and Bozak, 2003).
The current situation prevents positive changes (obstacles) to stop ISMS moves towards an ideal situation (goals) in order to keep the status quo. Obstacles promote risks and goals boost the integrity of ISMS.
Goal Driven Risk Management Model
Figure 2. Overview of goal-driven risk management model levels
Goal-driven risk management model effectively address the risks that obstruct the successful project outcomes (Islam, 2011; Islam et al., 2010). The approach explicitly models the relations between the goals with the risk factors that obstruct these goals. Risks are then assessed and suitable control actions are selected to mitigate the risks so that the project can attain its goals.
Goals are the objectives, expectations and constraints of a specific system context and its surrounding environment as prescriptive statements of intents whose satisfaction contributes to the overall project success. The risks are obstacles that have consequences raise the chance of single or multiple undesirable circumstances that obstruct the goals and certainly reduce the likelihood of the project success.
The reason for choosing goal-modelling language is that goals and risks are complementary entities of a software project. A risk is usually defined as negation to a single or multiple goals or a loss of attainment of some corresponding objectives. Risks always shadow the goals and certain goals may be risky.
The model supports different levels of abstraction from goal to obstacle and finally to the treatment, as shown in Figure 2. On the top, there are the goals, i.e., objectives, expectations and constraints of the development components.
In the middle are the risk factors that directly or indirectly obstruct the goal to fulfill and incur problems within the system context. At the bottom part, there are the control actions that obstruct the risks and their consequences and contribute to attain the goals.
The proposed work attempts to analyze the human factors in a proactive way for an effective information security management system. We adopt a combination of force field analysis method and goal-driven risk management model to support modelling the human factors. The aim is to understand what should be an ideal situation for an organization considering human issues for overall IS matters.
Figure 3 above shows the concepts used for modelling human factors. This model consists of three levels. Human factors compromise the first level and represent the important factors which identified based on our last study on the IS incidents. This level can be easily recognized as part of the outcome of conducted interviews. The second level compromises driving and restraining forces.
They are devised by outcome of SWOT analysis and employees’ prioritization in the questionnaires. Third level of this model defines by goal driven approach where driving forces support the goal of ISMS and restraining forces perform as obstacles in fulfillment of ISMS objectives.
Driving Factors as Goals
The driving forces, which promote changes in a way human factors are managed and dealt with, are varied and extremely difficult to be identified. Goals in this paper are the objective, and requirements that need to address effective considering human factors such as errors and apathy. In this article we used the outcome of the SWOT analysis to identify the driving and restraining forces for achievement of ISMS goals.
In that respect the Awareness, Management Support, Budget and Security Culture have been identified as driving forces. Based on discussed IS incidents these factors were promoting ISMS goals (Alavi et al, 2013).
Some of both direct and indirect human factors can be categorized as driving forces. Whilst their natures are different, they can be advocate alteration in the process of design, implementation and evaluation of an ISMS in order to be effective and efficient. These forces, however, must be validated and to be prioritized. Also, the state of their criticality must be determined.
Restraining Forces as Obstacles
Obstacles in this study are the restraining forces, which prevent changes and consequently creating risks and unable the system to fulfill the goals. For example, human stress preventing people to adopt changes that ensure ISMS performs effectively. People in organizations are skeptical of ISMS measures and guidelines and may resist learning to use new principals and procedures which enhancing efficiency of ISMS.
Identifying their reluctance and planning strategies to work through these obstacles is the key to implementing effective ISMS in organization. As change becomes an increasingly common occurrence in a way information is managed by technology, understanding human factors offers a view of the dynamic interaction between individuals and ISMS to understand resisting forces to change.
Based on SWOT analysis some direct and indirect factors were weaknesses of the system, which can be translated to the restraining forces, opposing change in a way ISMS handled. Therefore, the resisting forces are Errors, lack of Experience, Apathy, Negligence, Stress, lack of Communication, and lack of Security Policy Enforcement.
Understanding Organizational ISMS Situation
Force field analysis methodology requires an understanding of the current and ideal situation of ISMS, enabling an identification of driving and restraining forces. This section compromises the current and ideal general state of ISMS, linking up the goals and obstacles in effective ISMS process. The goal of ISMS is to fulfill a situation where risks are minimized by encouraging constant positive changes to the system. This goal is an ideal situation.
However, obstacles or restraining forces working to keep the status quo and preventing any changes to ISMS. This would be a current situation. Therefore the current situation advocates risks when the resisting forces building up information security vulnerabilities. Understanding of ideal situation enables organizations to identify driving forces to attain right control measures to meet ISMS goals. Without understanding of these two situations organizations are unable to make any improvements in control measures, concerning risks and possible new risks arising within ISMS weak countermeasure tools.
Ideal Situation for ISMS
In contrast to the current state of ISMS in organizations, ideal situation would be a desirable situation of organizations considering ISMS. An ideal situation could have different statues in various organizations, concerning the IS culture, practices and guidelines.
However, information security standards provided an overview of an ideal situation. For example, ISO/IEC 27001 that is one of the well-known standards released by the International Organization for Standardization in October 2005 specifies a certain requirements of an ideal situation of ISMS as following:
- A consistent framework of IS controls, ISMS policy, appropriate risk management procedures concerning risks that are considered unacceptable.
- A routine scrutiny of an organization’s risks, with consideration of threats, vulnerabilities, and impacts of those risks.
- A constant review of ISMS policies and controls to ensure the corrective and preventive actions are in place.
It is expected that ISMS taking care of IS leadership, organizational frameworks and processes which protect information. However, this ideal role challenges regularly in the reality of organizational activities. Despite this clear direction and guidelines, organizations do fail to fulfil these requirements. This is clearly is the goal of ISMS and driving forces that promote this goal by introducing constant positive changes.
Current Situation in ISMS
Defining current situation assists to determine how currently an organization deals with ISMS goals. Current situation resisting against changes and would prevent any effective changes in assisting ISMS to achieve its goals. Restraining forces are promoted in the current situation and risks are accumulated.
Consequences of the Continuation of Current Situation
Information security incidents are rising. These incidents have impacts on organizations in various ways. The most common types of impact on organizations that must be considered in a information security profile are; financial cost, legal liabilities, business status (reputation), theft, vandalism, damaged intellectual property, employees and customer moral and confidence.
These impacts hampering the system when resisting forces creating obstacles for changes to keep the current status of ISMS untouched. This happens whilst driving forces push for changes to promote better and ideal situation in which risks are downgraded and decreased.
To explain the situation, we use force field analysis that defines the interaction of two conflicting groups of forces, those endeavoring to promote change, the driving forces and those seeking to maintain the status quo that called restraining forces (Lewin, 1947).
The equilibrium or current situation must be disrupted for change to happen which can be achieved by supporting favorable conditions to the change and eliminating resisting forces. Based on the FFA model whenever driving forces are stronger than restraining forces, the status quo or equilibrium will change and organizations move from current status to a better place which is closer to an ideal situation of system.
Outcome of the Force Field Analysis
The analysis of all forces show that driving forces are required to be supported and decisions must be made by information security senior management team to eliminate restraining forces. The status quo or current ISMS situation will be stand unchanged, as resisting forces are stronger than driving forces for change. This is clearly averting organizations’ efforts from moving towards goals of ISMS that is a better and safer situation.
In case of stalling at the same situation, organizations will face risks, which increase vulnerabilities, and accumulate risks. Senior manager must address very important individual concerns as resisting forces such as apathy, negligence, and stress whilst providing better facilities to enhance communication, security enforcement policy, and minimizing errors by introducing training programs.
The important aspect of the outcome emphasizes on the individual characteristics of human factors as the resisting forces of change. Factors such as apathy, error and stress have received high scores.
Conclusion
This article provides a summary of an undertaken research which underlines the importance of understanding of driving and restraining forces for positive changes for an effective ISMS practice. The proposed human factors model employed a combination of force field analysis and goal driven approach. The human factors categorized to two distinct forces, driving and restraining forces. Driving forces are supportive of ISMS goals by promoting changes.
On the other hand restraining forces constitute barriers in order to stop positive changes. The outcome demonstrates the relationship between the security of an organization and the potential impact that people could make when it comes to very individual issues such as stress and apathy. We believe restraining factors create a situation where information system vulnerability increased and risks factors escalate. These risks put organizations in extremely difficult legal and financial situation.
We are convinced that this research can provide a constructive quantification insight of the roles of human factors in information security change management. However, we need to validate the approach. We are currently working to deploy the model within an organizational context as case study to understand the applicability of the approach.
Reza Alavi (@SecurityVPeople) is currently conducting his research in the School of Architecture, Computing and Engineering (ACE) in the University of East London. His research topic is: “Modeling a Human-Centric Approach For An Effective Information Security Management System (ISMS) – British Financial Institutions Perspective”. His research interests are the role of people and organizations in Information Security Management System (ISMS) with special interest in Information Assurance (IA). Reza has been working in various IT and business management positions such as Networking, IT Audit, and Sales and Marketing Management for the last 23 years.

What should you learn next?
Cross Posted from Tripwire's State of Security