How to Prevent a Domain Name Theft
1. Introduction
The domain names may cost far more than a real estate. For instance, Facebook paid USD 8.5 million to buy fb.com. The high prices of the domain names attract not only businesses, but also thieves. The domain name theft can be huge trouble for companies because it effects their brand and reputation. This is because a stolen domain name can be used in relation to activities such as dissemination of pornographic materials, downloads of malware, and submission of spam. In this regard, one of the former ICANN's CEO stated, "a domain hijacking is not as obvious a threat as spam and spyware, but it can be just as disruptive to the business and operations of name holders; in extreme cases, a domain hijacking can have a lasting impact on an organization."

FREE role-guided training plans
In general, criminals use three methods for conducting a domain name theft: phishing, identity theft, and fraudulent purchase of domain names. These three methods, and the preventive measures against them, are examined in detail in the following sections.
Before proceeding with the examination of those measures, it is necessary to provide general advice on how to avoid domain name theft. Firstly, it is preferable to use the services of reputable domain name registrars. Some unknown registrars may not provide their clients with assistance in case of domain name theft. Moreover, some registrars may be actively involved in domain name theft. Secondly, it is desirable to use the "locking" feature provided by most domain name registrars. Thirdly, the regular monitoring of a domain name portfolio ensures a quick reaction in case of a theft, which in turn, may lead to the successful recovery of a stolen domain name.
2. Phishing
The term phishing refers to the process by which an attacker sends emails or other correspondence purporting to be sent by a legitimate authority with the aim to lure individuals into disclosing confidential information. Such information may include, for example, credit card details, passwords, and passport numbers.
One common way of stealing a domain name through phishing is the submission of fake messages purported to be sent by the domain name registrar. The message may state that the domain name holder needs to reactivate his account on the website of the domain name registrar. The below-mentioned image is a screenshot of an actual email sent by a criminal to an individual whose name will be kept in confidentiality. The individual did not understand that the email was fraudulent and provided his personal data to the criminal who committed a domain name theft. Afterwards, the criminal "sold" the domain name to a buyer in China who argued that he legitimately purchased the domain name and is not familiar with any illegal activities.
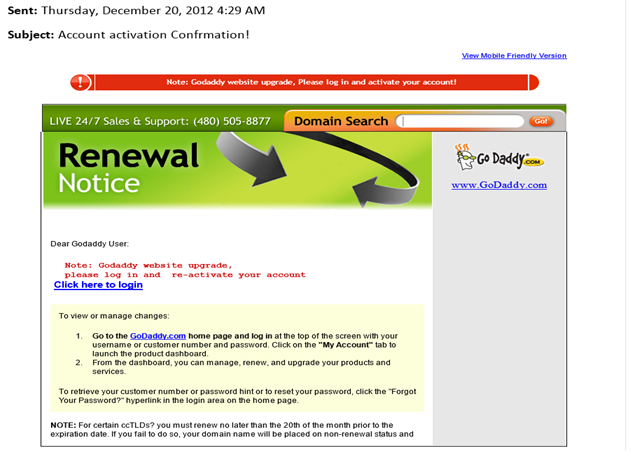
Hence, the prevention of a domain name theft requires caution in relation to any messages requesting a submission of personal data. In general, phishing emails can be identified on the basis of four elements, namely, (1) having an unofficial "from" address, (2) generic greeting, (3) link to a fake website, and (4) presence of mix of legitimate and fake links.
Pertaining to the first element, it should be noted that scammers are very inventive and often use methods allowing them to send emails that appear to be sent from official addresses. For instance, the aforementioned phishing email appeared to be sent by support@godaddy.com . Nevertheless, in many cases, the scammers send phishing emails from addresses which are suspicious. For example, if you receive an email from support@godaddy1.com, you can reasonably believe that the email may be fraudulent.
Concerning the second element, phishing emails do not usually containing personal greetings because fraudsters send thousands of such emails per day. By way of illustration, the phishing email discussed above contains the greeting "Dear Goddady User".
As for the third element, the scammers often use a link to an IP address instead of a link to a domain name in order to avoid any suspicion in relation to the link. The victims may accept the IP address as a normal feature of a legitimate website.
Concerning the fourth element, phishing emails usually contain authentic links that serve to persuade the victim that the email is legitimate. All links in the aforementioned email are legitimate with the exception of the link "Click here to login".
3. Identity theft
A domain name thief may obtain confidential data about the victim by using methods different from phishing. Such methods may include access to paper documents, finding publicly available private information, guessing a weak password, or "shoulder surfing". The latter term refers to observing people while they are using their computers, ATM, or other electronic device. After obtaining the personal data of the victim, the fraudster may directly enter into victim's domain name account.
In order to avoid identity theft, one needs to perform multiple steps, including, but not limited to, using strong passwords, not publishing personal information on the Internet, activating the privacy setting of social network accounts, and using a paper shredder before disposing any papers containing personal information.
If a fraudster uses the personal information of a domain name owner to steal a domain name, the registrar will probably disclaim all responsibility in relation to the theft. For example, GoDaddy's terms of service state that: "You are solely responsible for the activity that occurs on your Account, whether authorized by you or not, and you must keep your Account information secure, including without limitation your customer number/login, password, Payment Method(s) (as defined below), and shopper PIN."
A victim of a domain name theft may learn that even the law enforcement authorities can do little to recover his domain name. Robert Morgester, a deputy attorney general in California, stated that arrests for domain name theft occur rarely. Nevertheless, a New Jersey court case from 2011 indicates that the judicial authorities realize the need to take measures against domain name theft. In the case, a domain name thief was sentenced to five years for stealing the domain name P2P.com and reselling it to eBay.com for USD 121,000. One of the partners of the domain name owner stated in relation to the recovery of the stolen domain name:
"In our effort to redress the injuries inflicted on us, we came to appreciate how undeveloped this area of the law is, and how victims of domain theft face an unmarked and totally uphill battle to get a remedy. Today's sentencing helps to define a path for other victims and law enforcers to follow, and reinforces the likelihood that the theft of a domain can and will be prosecuted."
4. Fraudulent purchase of domain names
In some cases, fraudsters contact the owners of domain names and request to purchase their domain names. In order to lure the owners, the scammers may offer very attractive prices. When the owner of the domain name agrees to sell his domain name, the fraudster agrees to pay after the receiving the domain name. If the seller also agrees, the fraudster gets the domain name and suddenly disappears. Often, the stolen domain name is resold to multiple buyers, which complicates the recovery of the domain name.
In order to prevent fraudulent purchase of domain names, one needs to use the services of reliable escrow providers. Such providers collect, hold, and release the funds related to domain name transactions. Thus, the purchaser of the domain name will receive the domain name only after the seller receives the promised price.
Escrow.com is a popular provider of escrow services for e-commerce companies, such as GoDaddy and eBay. The registration of an account at Escrow.com is relatively easy even for a newcomer. It should be noted that Escrow.com provides a special escrow service for transactions related to sales of domain names.
5. Conclusion
Although the domain name theft is a major issue in the field of e-commerce, the recovery of a stolen domain name may be expensive and often impossible. To illustrate, the owner of an advertising agency spent roughly USD 15,000 and 19 months in order to recover the stolen domain name MLA.com which was transferred to a registrar in the Bahamas in May 2013. The company lost significant revenue because the clients had difficulties reaching it. In another case, the owner of ShadesDaddy.com lost USD 50,000 in revenue as a result of a domain name theft. The owner, who was also forced to lay off six of his eight employees, stated: "It's like your house got stolen".
Hence, the ICANN and national governmental institutions need to find out a way to facilitate the recovery of stolen domains. One such way may be the introduction of an online dispute resolution procedure, similar to ICANN's Uniform Domain-Name Dispute-Resolution Policy (UDRP), which will apply specifically to the resolution of disputes related to domain name theft. Such a procedure will allow the domain name owners to recover their domain names without the need to commence litigation proceedings. Another, even more innovative, approach is the introduction of a crowdsourced online dispute resolution, similar to the eBay's Community Court, in relation to stolen domains. eBay's Community Court allowed the members of the eBay's community to act as jurors and resolve disputes related to sellers' ratings posted on eBay. The idea used by eBay's Community Court can be implemented in the context of disputes related to domain theft by allowing representatives of the domain name registrars to resolve collectively such disputes.
Until the introduction of a new and innovative method of dispute resolution concerning domain name theft, the prevention remains the most efficient mean to retain the ownership in a domain name. This article indicated that the prevention measures can be grouped in three categories, namely, prevention measures against phishing, prevention measures against identity theft, and prevention measures against fraudulent purchases of domain name. Thorough understanding of these measures will allow the domain name owners to escape the traps of the fraudsters and use their domain names for a long time.
References
1. Cyger, M., 'Understand and Prevent Domain Name Theft - With Dr. Bruce Tonkin', DomainSherpa, 30 September, 2013.
2. Dimov, D., 'Domain theft and the possibilities for recovery of the stolen domain names', InfoSec Institute, 3 December, 2012.
3. DN Journal, 'It's Official - Domain Thief Daniel Concalves Sentenced to 5 Years in Prison in Precedent Setting Case', DN Journal, 22 July 2011.
4. Harris, D., 'How to Stop China-Based Domain Name Theft', ChinaLawBlog, 9 November, 2011. Available at http://www.chinalawblog.com/2011/11/how_to_stop_china-based_domain_name_theft.html .
5. ICANN, 'Domain Name Hijacking: Incidents, Threats, Risks, and Remedial Actions', a Report from the ICANN Security and Stability Advisory Committee, 12 July 2005. Available at http://archive.icann.org/en/announcements/hijacking-report-12jul05.pdf .
5. Komaitis, K., 'The Current State of Domain Name Regulation: Domain Names as Second Class Citizens in a Mark-Dominated World', Routledge, 2010.
6. Lewis, B., 'Help! My Domain Name Has Been Hijacked!', CircleID, 12 January, 2007.
7. Northcutt, S., Madden, C., Welti, C., 'IT Ethics Handbook: Right and Wrong for IT Professionals', Elsevier, 2004.
8. Lindsay, D., 'International Domain Name Law: ICANN and the UDRP', Bloomsbury Publishing, 2007.
9. National Crime Prevention Council, a webpage entitled 'Tips to Prevent Identity Theft' (last checked 14 May 2015). Available at http://www.ncpc.org/topics/fraud-and-identity-theft/tips-to-prevent-identity-theft .
10. Reid, J., 'Blogger Pulls Off $30,000 Sting to Get Her Stolen Site Back', Mashable, 2 April 2014. Available at http://mashable.com/2014/04/02/ramshackle-glam-hacking/ .
11. Rutenbeck, J., 'Tech Terms: What Every Telecommunications and Digital Media Professional Should Know', CRC Press, 12 November 2012.
12. Sfetcu, N., 'The Business of Domain Names', Nicolae Sfetcu, 2014.
13. Simon, R., 'Cybercriminals Are Misappropriating Businesses' Web Address', Wall Street Journal, 11 March 2015.
14. Smith, G., 'When Hackers Steal a Web Address, Few Owners Ever Get it Back', Huffington Post, 29 September 2014. Available at http://www.huffingtonpost.com/2014/09/29/domain-theft_n_5877510.html .

FREE role-guided training plans
15. Van den Herik, J. and Dimov, D., 'Towards Crowdsourced Online Dispute Resolution', In: 'LAW ACROSS NATIONS: GOVERNANCE, POLICY & STATUTES', pp. 244-257, International Association of IT Lawyers (IAITL), September 2011.




