How Did the Russian Abuse Twitter as C&C in Hammertoss Malware? Python Answers
Today, we will replicate a technique which has been used by recent, sophisticated and hard to trace a Russian malware called Hammertoss, the creators of this malware has abused multiple well-known sites like Twitter and Github to defeat modern firewalls and torture whoever tracing their tracks.
In a nutshell, instead of getting a direct reverse connection back to the C&C server similar to what traditional malware does, this smart malware will jump between third party servers to perform its malicious activity, please take two minutes and watch this [https://www.fireeye.com/blog/threat-research/2015/07/hammertoss_stealthy.html/] short explanatory video from FireEye so you will get a quick overview how the malware works.

What should you learn next?
All right, so the first stage of Hammertoss was to connect to a Twitter looking for a tweet created by the hackers which contains a URL for an image and hashtag as a part of an encryption key. Technically speaking, you don't need to login into Twitter to parse someone's tweet, so in this case, we just need to figure out the account URL to navigate and the HTML tags which contains the actual tweet, Keep in mind you can add other Twitter accounts to hide the original one (which belongs to the hacker).
Obviously, you should have never your personal account while doing similar stuff; that's why I created a new account holding my name and here's is the link to my Twitter homepage
https://twitter.com/HussamKhrais
Now from my Kali machine, I made a tweet saying "Hello from Kali python" then I logged out, at this point once we click on the above URL, we should see something similar to this output
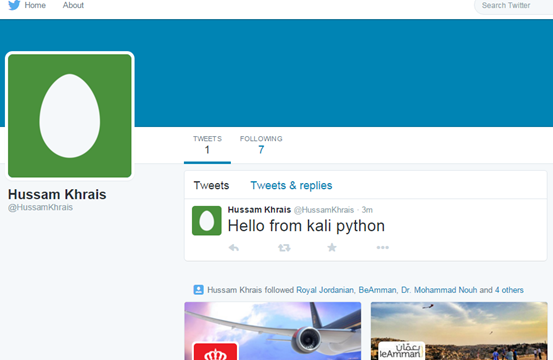
Now using your browser you can view the HTML source code of this page, in Chrome just do a right-click anywhere on the page and select "View page source" or Ctrl+U for short, in the HTML if we search for our tweet, we will get the below HTML line:-
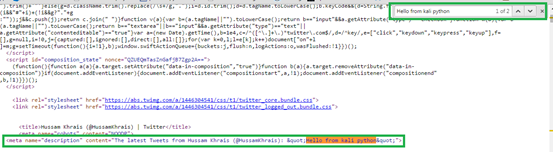
So technically if we code a simple script that will navigate to https://twitter.com/HussamKhrais
And retrieve the HTML page, then inside the HTML if we searched for meta tag called name that has a value of description and asked for the value of content, then we should be able to grab our tweet.
Let's translate this action into code:-
-
from BeautifulSoup import BeautifulSoup as soupy #1
-
import urllib #2
-
html = urllib.urlopen('https://twitter.com/HussamKhrais').read() #3
-
soup = soupy(html) #4
-
x = soup.find("meta", {"name":"description"})['content'] #5
-
print x
#6
- Import soupy function from BeautifulSoup library, we will use this function to search for the HTML tags
- Import urllib which will be used to navigate to our twitter page and grab the HTML for us
- Navigate to my twitter home page HussamKhrais stores the HTML page into HTML variable
- Pass it to soupy function so we can parse it
- Here we search for the HTML meta tags
- Print the result out
The output for running the script would be
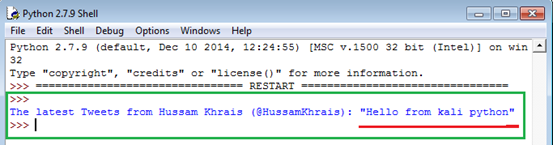
At this point, since we are only interested in having the string between the quotation marks, we can filter it out using regular expression, and that exactly what the below script will do for us
-
import re
-
filter = re.findall(r'"(.*?)"',x)
-
tweet = filter[0]
-
print tweet
The final function will grab the string between the " and store it in a list data type called filter. Finally, we print the exact tweet.
After putting all the script pieces together, we got the below result
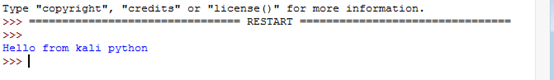
Now think about it for a second, can we use Twitter to replace DDNS? Well, what will happen if we replace "Hello from Kali Python" with the public attacker IP, and each time the attacker IP changes, all that he needs to do is to send a tweet with the new IP to get the reverse connection for his victim!
A question for you…

FREE role-guided training plans
After reading this article, do you think that can you code in Python a complete AV free remote shell and exfiltrate data without even having a single direct connection with your target? Please share your thoughts.






