The Future is Now: Car Hacking
Preface: "Modern Cars"
As Dr. Charlie Miller & Chris Valasek stated in their research paper Adventures in Automotive Networks and Control Units, "Automobiles are no longer just mechanical devices. Today's automobiles contain a number of different electronic components networked together that as a whole are responsible for monitoring the state of the vehicle." The concept of self-driving cars is already in vogue, and car manufacturers predict that by 2020 automobiles will become autonomous.
Learn ICS/SCADA Security
Hideki Okano, a Mazda staff manager, riveted the attention of curious journalists to the fact that "in the US market, infotainment and connectivity is becoming a major decision-making factor for car buying. It is also growing in other markets."
An Always-Connected Car
The good thing is that 3G and 4G-based telematics cost as little as a couple of hundred dollars, nothing compared to the revenue from wireless devices today estimated at $2.5 billion and expected to increase tenfold by 2025.
To look at the bright side of things, interconnectedness may considerably improve road safety through technology as Vehicle-to-Vehicle communication (V2V). A wireless and ad-hoc network is formed between vehicles as they travel next to each other based on the use of 802.11p subset of Wi-Fi protocols (See Diagram 1a). As a result, if one of the cars changes its direction or brakes abruptly, this car will project messages into the V2V network, thus alerting the rest of the vehicles in the vicinity (See Diagram 1b).
Diagram 1a Diagram 1b
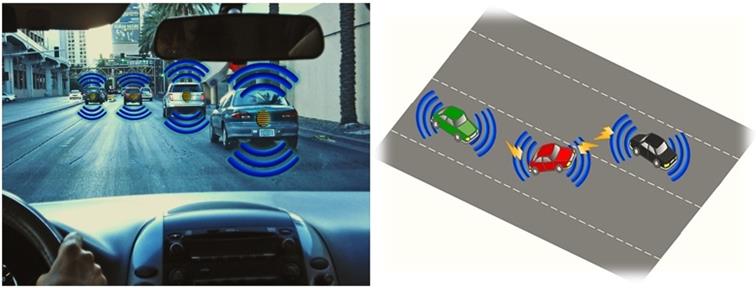
Under these circumstances, it is perfectly understandable why the tech titans Microsoft, Google and Apple are at war to get a good grip of the market intended to deliver operating systems, apps, navigation, and other similar services for vehicles.
So yes, turning cars into devices plugged to the Internet seems like a great idea (an invariable part of the Internet of Things concept, so to speak). However, the downside is that connectivity amounts to security issues that every end of the global network may experience. And as you will see, cars may become the next tempting target for black hat hackers.
I. Controller Area Network (CAN) Bus and Electronic Control Units (ECUs)
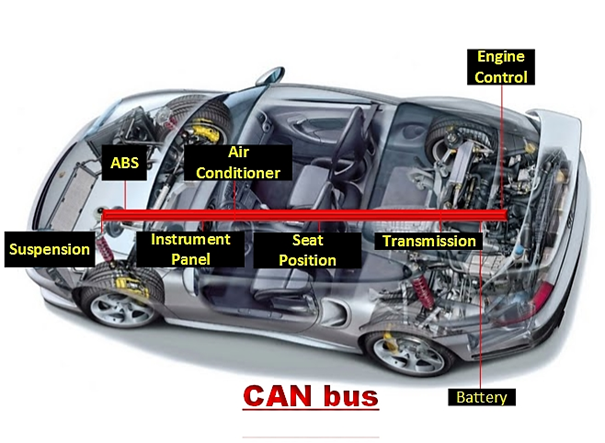
In the mid-1990s, cars progressively evolved to integrate a complex network of powerful electronic control units (ECUs) – independent computers, for all intents and purposes, with up to 100MB of binary code, which maintain a particular part, a series of components, or a process within a car and can introduce peripheral devices into the automobile such as Bluetooth or GM's OnStar system. Nowadays, ECUs control and tune a vast array of substantial functions, including breaking, steering, acceleration, and displays on a dashboard. The most essential ECUs communicate via a vehicle's wiring system called CAN bus, an engineering standard that has come into mass use again in the mid-90s.
Distinguishing itself with simplicity, especially compared to the World Wide Web, CAN is rather simple and low-level. Nevertheless, transferring data among distributed electronic modules through a serial data bus is a vital part of in-vehicle networking. CAN is a 2-wire network, and most vehicles have two or three separate CAN buses operating at speeda from 125Kbps for low and medium level to 500Kbps for high level.
Diagram 2
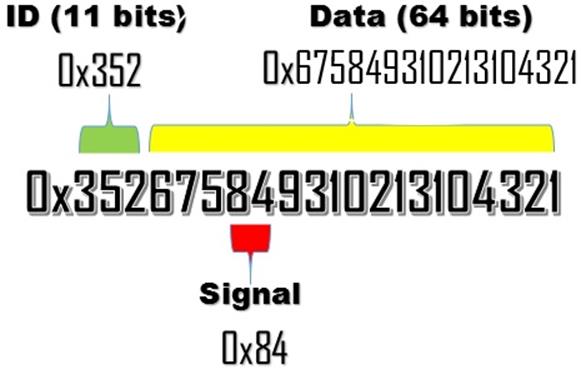
CAN Data Format
CAN network traffic flows into frames or messages consisting of:
- standardly framed an 11 bit identifier
- up to 64 bits of data
It's important to note that the 64 bits of data of each CAN message contains multiple data points associated with some function within the automobile (e.g., the center position of the steering wheel). These bit fields represent a CAN signal.
Diagram 3
The type of communication is performed through a dedicated wire through point-to-point connections.
The CAN controller is the heart of a CAN bus, and it is connected to every component on the network via the low speed and high speed CAN wires. Even though all network nodes constantly see all of the data circulating from one point to another, each network node responds to messages assigned to its unique identifier. Nodes are handled on a priority basis from a safety point of view, meaning that processes such as engine controls, brakes and airbags are seen as critical and will be actioned first and via the high-speed bus. Just for comparison, navigation and audio devices are of medium priority, and lighting activation is of lowest. It should be emphasized again that "the data on one of the three networks is available to the other two networks through gateways to enable, for example, the transmission to get data from the engine management system and vice versa."
According to the SAE Classification, there are three main categories of in-vehicle networks when considering values as speed and functions:
Class A
- Low Speed (<10K bits/second)
- Convenience features (entertainment, audio, trip computer, etc.)
Class B
- Medium Speed (10K b/s to 125K b/s)
- General information transfer (instrument cluster, vehicle speed, legislated emissions data, etc.)
Class C
- High Speed (125K b/s to 1M b/s or greater)
- Real-time control (powertrain control, vehicle dynamics, brake by wire, etc.)
Source: http://roadwarrior.free-man.com/can/
The CAN Hacking Tool (CHT)
Recently, security researchers Alberto Garcia Illera and Javier Vazquez-Vidal presented the CAN Hacking Tool (CHT), a $20 smartphone-sized apparatus that can compromise an automobile's computer system. In order fora hacker to do that, however, he needs physical access to the car. The CHT has four wires that go into several outputs of an auto's CAN. A cheap computer chipset bypasses encryption on the car prior to reading/writing data from vehicle's memory residing in its engine control unit. After that, it can wirelessly control vital car's functionalities as steering and brakes. The words of Vazquez-Vidal attested to the simplicity of the process: "It can take five minutes or less to hook it up and then walk away. We could then trigger it to do whatever we have programmed it to do."
II. Compromising a Vehicle
Diagram 4
"Entry Points"
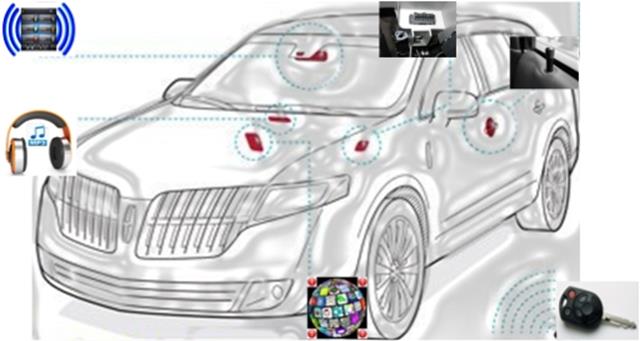
In essence, there are two main conduits through which a hacker can overcome a car's security: physical channels and wireless communication units.
a) Indirect Physical Channels
Today's automobiles provide a number of physical interfaces for easy access to the car's networks.

DOOR LOCKS
In modern automobiles, the power-locking system is interconnected to other car mechanisms in order for doors to lock automatically when a car is in drive, for instance, or unlock in case the airbags have been released or the car keys are forgotten inside.

MP3 MALWARE: iPod, Disc, and USB.
Virtually all manufacturers integrate media devices into their products. Researchers proved that malicious input can be delivered by encoding it into an MP3 file or a CD. As a result, an adversary may deceive the user or recourse to social engineering techniques just to prompt him into playing a CD or a song file that has a malicious code. Alternatively, compromising user's phone or iPod with a malware that insidiously engages the automobile's media system when connection takes place, is another viable modus operandi. If you think that taking over a CD player system alone is not a pervasive threat, think again of the how CAN bus is interconnected in such a style so as to even media systems not be standalone units. Furthermore, corrupted audio files of such a nature may spread in a worm-like manner if the user under attack decides to share them through peer-to-peer networks, for instance.

Source: Wikipedia
OBD-II
Federally mandated in the U.S., the OBD-II port used typically for diagnostics is the most direct way to hack a car, because it launches a code directly to the CAN bus. In harmony with this observation, student researcher at the University of Washington Franziska Roesner reported on the basis of many studies she and her colleagues had conducted that the OBD-II port is the most significant automotive interface for hacking purposes, among other things.
Providing a direct outlet to the vehicle's key CAN bus components that in turn give enough access to the full range of automotive systems may prove perilous, and that is why her research advises car owners to consider carefully to whom access is given.
And yet service personnel that perform diagnostics are permitted to access the OBD-II diagnostic ports as part of their duties. Dedicated Windows-based "scan" tools can access cars through the OBD-II port and gather information or program particular ECUs.
In the U.S., all new cars support a SAR J2534 "PassThru" standard, which is a Windows API that establishes an interface to communicate with the buses inside the car. Implemented usually as a Windows DDL, this connection with the car can be either over a wired or wireless network in pursuit of correct diagnostics or reprogramming. Once plugged into the OBD-II, the PassThru device can communicate with the car's internal network under the software commands of J2534 API.
According to a group of researchers from the University of Washington, PassThru device can be a conduit for malware since "the attacker on the same WiFi network as the PassThru device can easily connect to it and, if the PassThru device is also connected to a car, obtain control over the car's reprogramming." Moreover, they also deem it possible "to compromise the PassThru device itself, implant malicious code, and thereby affect a far greater number vehicles." It should be stressed that these vulnerabilities are in the PassThru device itself, since they can be reached via their WiFi connectivity or directly via Ethernet, and cracked via shell injection that installs malicious binary code, which in turn will send pre-programmed messages through the CAN bus every time a technician connects the PassThru device to a vehicle (See Diagram 5. Malware is being installed onto the car's telematics unit, and this malware remains dormant, waiting for an exact environmental trigger – for example, specific time and date.)
Diagram 5
"Shell-injection scenario on a Pass Thru device"
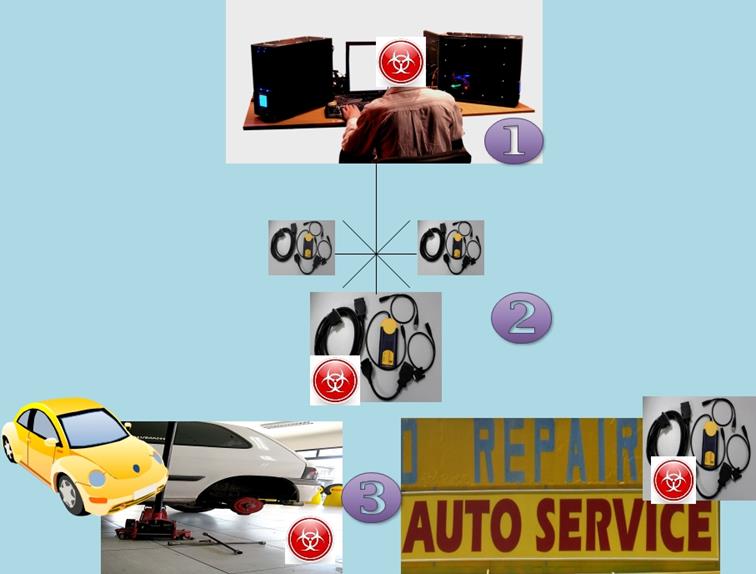
- Getting access to service center network;
- Compromising one of the Pass Thru devices with a virus, which is being activated on a certain date, when given event occurs, or a condition is met;
- The Pass Thru device can spread viruses to cars and other Pass Thru devices even in other car shops.
Specifically for electric autos is the proviso that they can communicate with external charging devices through a charging cable. Consequently, a wrongdoer only need to break into the external charging infrastructure to leverage that access to further attack any connected car.

b) Remote Hacking Wireless Communication Units
Every wireless network is potentially dangerous because a person can never know if someone is lurking in the dark, preparing to intercept his data. The good news is that: firstly, WiFi range may be limited in distance; secondly, utilizing a Wi-Fi/Bluetooth signal blocker may prove sufficient to black out any wireless connections, trustful or corrupt, around your car.
Troels Oerting, the director of the Europe's Cybercrime Centre, opines that car hacking might be a real security concern very soon: "Wireless technology is integrated into practically everything nowadays and if there's wireless access to anything there's a possibility to remotely control it."
In the same spirit is the opinion of Roesner: "Cars are not only becoming more computerized internally, but that they are becoming increasingly connected to the outside world. Automobiles most at risk include those with more components under computer control and without manual overrides, and those that are more connected to the outside world via the Internet or wirelessly." She further defines this trend in interconnectedness as "concerning".

UNAUTHORIZED APPS
Similarly to the smartphone business in which a multitude of programs is developed by third-party enterprises and contractors, carmakers are forced by the advent of the digitalisation era to expand their infotainment services and provide downloadable software to their clients. Unfortunately, there are always rogue apps that contain viruses or malware, which can contaminate your car without you having a clue about it. What may give you comfort is the fact that carmakers usually very strictly select app developers and permit only a handful of preapproved programs. Besides, the number of apps available for infotainment systems is far less than those envisaged for smartphone users.
Short-range Wireless Access
Devices under attack in this category are Bluetooth, WiFi, Keyless Entry, RFIDs, ShortRange and Tire Pressure Monitoring Systems. For a successful attack, researchers assume that an adversary will need to place a wireless transmitter within 5 and 300 meters from the car's receiver, depending on the channel.

KEY FOB
A wireless key fob is used by a car owner to unlock and start the car when they utilize the device in close proximity to the car. Swiss researchers, however, figured out how to intercept the signal within a radius of 30 feet with gadgets that cost less than $100.
If there is a vulnerability in the ECU software entrusted with parsing messages through channels, then the evildoer may exploit the ECU, and by extension, the integrity of the entire vehicle plainly by transmitting malware content from a short-range distance.

Let's review the Bluetooth technology built into a car's telematics. Researchers testify that they "gained access to the telematics ECU'S Unix-like operating system and identified the particular program responsible for handling Bluetooth functionality."
In addition, the subsystem supported by the Bluetooth is specifically designed to facilitate hands-free calling and therefore can be paired with smartphone(s). Under the presupposition that one of these smartphones can be compromised independently, an attacker can use these mobile devices as a plunge-board for breaking into the car's telematics structure, and from there to all critical ECUs on the car.
Long-range Wireless Access
TELEMATICS SYSTEM
Long-range here means a distance of digital access greater than 1km. The last word in science and technology cars are equipped with a plethora of long-range signal broadcast receivers—Global Positioning System (GPS), Digital Radio, Satellite Radio, Radio Data Systems (RDS) and Traffic Message Channel (TMC) signals.
The long-range wireless attack surface is under exposure by the remote telematics systems, such as GM's OnStar, Ford's Sync, Lexus' Enform, Toyota's SafetyConnect, Mercedes-Benz' mbrace, and BMW's BMW Assist, which establish connectivity via data networks and cellular voice. On top of that, all these system are responsible for a variety of features starting with safety crash reporting, diagnostics and alert of mechanical problems, remote track and disable with respect to anti-theft, and ending with hands-free data access for convenient and safe drive. Therefore, gaining access to the telematics system also gives control to the systems connected to the CAN bus. Well, it happened to an $80 million yacht, why wouldn't happen to a car that costs 1000 times less?
By the contrivance of the cellular channels, the attackers have many advantages on their side. Namely, access over arbitrary distance due to the vast coverage of cellular infrastructure, anonymity, relatively high bandwidth, and two-way channels that can be addressed individually.
Telematics connectivity has a wide coverage, since many cars are equipped with a cell phone menu, which supports voice, 3 or 4G data, and SMS. The 3/4G data channel is for several of Internet-based functions (e.g., location and navigation services), whilst the voice channel is appointed for critical functions like crash notification. With regard to the voice channel, scholars from the University of Washington have found vulnerabilities in their car's telematics unit, more specifically the aqLink code that controls both cellular communication and voice. "There is a discrepancy between the set of packet sizes supported by the aqLink software and the buffer allocated by the telematics client code." Hence, a remote exploitation through reverse engineering the aqLink protocol is possible. To exploit this vulnerability, however, a proper authentication is needed in order to adjust the "call time value long enough to deliver a sufficient long payload.
The research team assessed that "this is possible due to a logic flaw in the unit's authentication system that allows an attacker to blindly satisfy the authentication challenge after approximately 128 calls."
III. Real Life Car Hacking?
Except for several studies conducted in a lab environment, there are not many empirical cases of car hacking. Perhaps the most notable such happened in Austin, TX in 2010 when a disgruntled former Texas Auto Center employee exploited the remote immobilization system to remotely disable or tamper with more than 100 cars.
On June 18, 2013 at about 4:25 AM, the journalist Michael Hastings died in a horrific car accident after his 2013 Mercedes-Benz C250 hit a palm tree at maximum speed and almost instantly bursted into a ball of flames. Hastings was famous for his relentless journalistic investigations resulting in stories that no people in power would ever want to be publicly brought up. After his revealing report about General Stanley McCrystal, the latter had to resign. Rumour has it that Michael Hastings was a thorn in the flesh of Army Brass and intelligence services.
As it is known that the Department of Defense has been researching cars remote controlling through hacking for quite a while now, many consider Michael Hastings a victim of such deadly digital plot.
Richard Clarke, a prominent counterterrorism figure with more than 20 years of experience in the upper echelons of the U.S. government, said with respect to Hastings' death that if one takes into account some of the details surrounding the event, as the fact that it is a single-vehicle crash, one may conclude that the incident is a look-alike cyber attack. Clarke pointed out that "intelligence agencies for major powers – including the United States – know how to remotely seize control of a car."
A close friend of Hastings testified that high-ranked militaries had threatened him upon his reporting that led to General McChrystal's resignation: "If we don't like what you write, we will hunt you down and kill you."
Gar Smith in his article "On the Strange Death of Michael Hastings: Was the Reporter Car-Hacked or Bombed?" throws some very credible and, at the same time, odd facts that lean towards the conspiracy theory – Michael Hastings was assassinated. Those are as follows:
- There are no skid marks around the spot of the accident.
- Local residents give reports about hearing loud explosion (A car bomb?).
- There is a plenty of video material showing that the car looks like a burning torch, something uncommon for gasoline-induced fire.
- The engine was found 100 feet from the flaming remains of the car.
- The front half of the car remained enshrouded after Hasting's body was removed for no particular reason (except to hide the view from the press and the public).
- There was water springing from an otherwise undamaged fire hydrant. "Something had apparently caused a portion of the buried waterlines to rupture underground," concluded Gar Smith.
- By mysterious chance, a professional photographer snapped Hasting's vehicle on one of the streets not far from the place of his death. The car passed a red light at the speed of sound, without being chased by anyone.
Because the fire was so consuming, the coroner needed two days to identify Hastings' body. Even if everything inside the coupe hadn't melted, including the on-board computers, Clarke thinks a cyber attack would have been almost impossible to trace due to the fact that all signs of it can be wiped out with ease. Unfortunately, that is a good real-life example of why car-hacking is a convenient choice for perpetrating a crime.
Conclusion: Is car hacking a threat?
Well, although cars are computerized, they do not function like PCs or smartphones. Hackers need to put a lot more effort to assume control of a vehicle than, for example, to steal someone's banking credentials and siphon off his money. Cars are not built to take randomly forced in commands, and even if that works, the effect would only remain for that intended car. The motives? They vary from a reputation showing off to more serious crimes like erasing information from in-car event data recorders, theft, kidnapping, and assassination.
Despite the fact that there are no significant real life cases of car hacking to date, the threat is scientifically proven and it is out there for gifted but malevolent minds to exploit.
Europol's Oerting thinks that car manufacturers are aware of the vulnerabilities and they will be liable for any security incidents that may lead to unauthorized hacking of their products. He said that "it's important that consumer and carmakers are aware of the downside to technological developments," and then added that now "drivers and passengers are strictly at the mercy of the code running in their automobiles..."
Reference List
Barry, K. (2011). Can Your Car Be Hacked? Retrieved on 10/03/2014 from http://www.caranddriver.com/features/can-your-car-be-hacked-feature
Departments of Computer Science and Engineering of University of Washington and University of California San Diego (2010). Experimental Security Analysis of a Modern Automobile. Retrieved on 10/03/2014 from http://www.autosec.org/pubs/cars-oakland2010.pdf
Departments of Computer Science and Engineering of University of Washington and University of California San Diego (2011). Comprehensive Experimental Analyses of Automotive Attack Surfaces. Retrieved on 10/03/2014 from http://www.autosec.org/pubs/cars-usenixsec2011.pdf
Dimov, D. (2013). Privacy Implications of the Internet of Things. Retrieved on 10/03/2014 from https://resources.infosecinstitute.com/privacy-implications-internet-things/
Edelstein, S. (2013). Can your car be hacked? From brakes to GPS, a look at what's vulnerable. Retrieved on 10/03/2014 from
http://www.digitaltrends.com/cars/can-your-car-be-hacked-car-hacking-threats-analyzed/
Ellyatt, H. (2013). Car hacking: The next global cybercrime? Retrieved on 10/03/2014 from http://www.cnbc.com/id/101123279
Gold, S. (2014). Wirelessly hack your enemy's car for under £15. Retrieved on 10/03/2014 from http://www.scmagazineuk.com/wirelessly-hack-your-enemys-car-for-under-15/article/332956/
Hastings, M. (2010). The Runaway General. Retrieved on 10/03/2014 from http://www.rollingstone.com/politics/news/the-runaway-general-20100622
Hogan, M. (2013). Was Michael Hastings' Car Hacked? Richard Clarke Says It's Possible. Retrieved on 10/03/2014 from http://www.huffingtonpost.com/2013/06/24/michael-hastings-car-hacked_n_3492339.html
Howard, B. (2014). CES 2014: 4G cars usher in the era of the seriously connected automobile. Retrieved on 10/03/2014 from http://www.extremetech.com/extreme/174287-ces-2014-4g-cars-usher-in-the-era-of-the-seriously-connected-automobile
Melone, L. (2012). Car-hacking: Remote access and other security issues. Retrieved on 10/03/2014 from http://www.computerworld.com/s/article/9229919/Car_hacking_Remote_access_and_other_security_issues?taxonomyId=17&pageNumber=1
Parker, A. Are modern cars vulnerable to hackers? Retrieved on 10/03/2014 from http://auto.howstuffworks.com/under-the-hood/trends-innovations/modern-cars-vulnerable-to-hackers.htm
Smith, G. (2013). On the Strange Death of Michael Hastings: Was the Reporter Car-Hacked or Bombed? Retrieved on 10/03/2014 from http://www.berkeleydailyplanet.com/issue/2013-08-09/article/41312
Spark Staff (2014). CES 2014: In-Car 4G LTE, Infotainment, and Beyond. Retrieved on 10/03/2014 from http://spark.qualcomm.com/blog/ces-2014-car-4g-lte-infotainment-and-beyond
Woollaston, V. (2014). The gadget that can hack any CAR: Terrifying £12 tool can remotely control headlights, locks, steering and even brakes. Retrieved on 10/03/2014 from http://www.forbes.com/sites/andygreenberg/2013/07/24/hackers-reveal-nasty-new-car-attacks-with-me-behind-the-wheel-video/
Diagrams
Diagram 2 is based on an image that can be found here. The SAE Classification Table can also be found there. Retrieved on 10/03/2014.
Diagram 3 is based on a graph that can be found here. Retrieved on 10/03/2014.
Diagram 4 is based on an image provided by Barry, K. in Can Your Car Be Hacked? Retrieved on 10/03/2014 from http://www.caranddriver.com/features/can-your-car-be-hacked-feature
Diagram 5 is based on Figure 2 in Comprehensive Experimental Analyses of Automotive Attack Surfaces by
Departments of Computer Science and Engineering of University of Washington and University of California San Diego that can be found on page 8. Retrieved on 10/03/2014 from http://www.autosec.org/pubs/cars-usenixsec2011.pdf
 Answers
Answers 
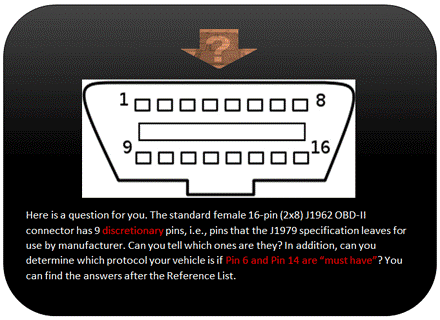
SAE J1962 defines the pinout of the connector as:
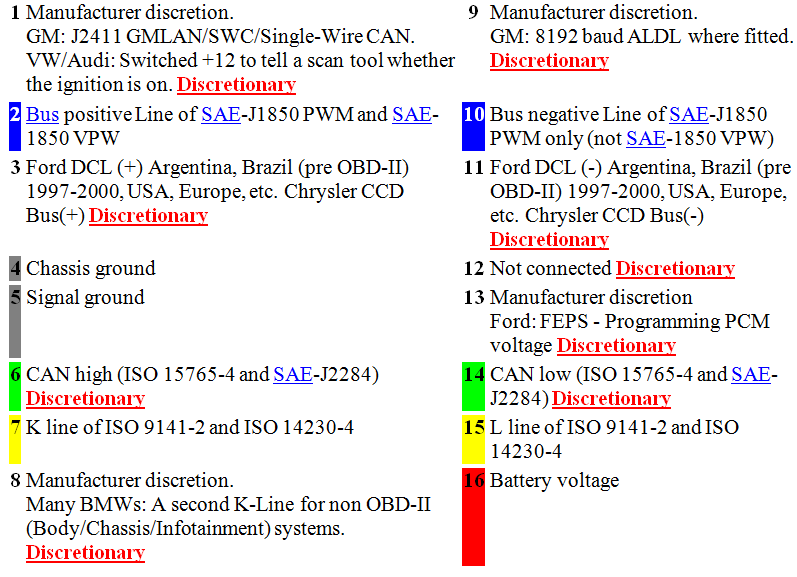
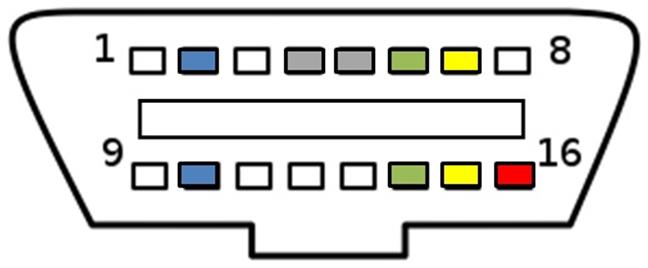
The assignment of unspecified pins is left to the vehicle manufacturer's discretion.
Source: Wikipedia On-Board Diagnostics and Intrepid Control Systems, Inc. OBDII / to neoVI Pin-out
Determining protocol from OBD-2 pinout
As a general rule, you can determine which protocol your vehicle is using by looking at the pinout of the OBD-II connector:
Standard
Pin 2
Pin 6
Pin 7
Pin 10
Pin 14
Pin 15
J1850 PWM
must have
-
-
must have
-
-
J1850 VPW
must have
-
-
-
-
-
ISO9141/14230
-
-
must have
-
-
optional
ISO15765 (CAN)
-
must have
-
-
must have
-
Please note that other pins may also be fitted. They usually connect to other (non-engine) ECUs or provide various signals. Generic OBD2 tools are not capable of "talking" to other ECUs than engine. For diagnosis of other control units such as ABS, airbag, audio or body modules you need vendor-specific software…
Learn ICS/SCADA Security
Source: OBDTester.com OBD-II Protocols


