Fitting cyber attacks to jus ad bellum — Consequence-based approach Part I
Introductory presentation
While still reviewing the instrument-based theory, there was a slight allusion at some point that oftentimes from practical reasons the gravity of acts occurring in the international medium is divided into various standards—a sign self-evidently speaking in favour of consequences criteria over the instrument one.

What should you learn next?
A bright example accounting for that inclination one could derive from the Nicaragua case where ICJ established that it is "necessary to distinguish the most grave forms of the use of force (armed attacks) from other less grave forms" (Nicaragua case, 1986, par. 191), like a "mere frontier incident". Assessment for possible differences between acts in terms of gravity should be based on the "scale and effects" of the force used by the aggressor.
Confirming the initial point made, Michael Schmitt, the Chairman of International Law Department at the United States Naval War College and most prominent proponent of the consequence-based scheme, opines that "it is therefore more useful and appropriate to focus on the qualitative nature of an action's consequences than on any ill-defined quantitative standards (Schmitt, 2012, p. 288)." Presumably, this 'golden' standard seeks to encompass acts that inflict grave consequences likely to produce death/injury to human beings or destruction/damage to tangible objects.
Hence, from the perspective of consequence-based approach, every cyber attack that falls within this range of "most grave forms of the use of forms" measured through the magnifying glass of 'scale and effects' would be deemed tantamount to 'armed attack' in accordance with Article 51 of the UN Charter. Moreover,
"…this approach would certainly be convincing in that it would liberated states from the prohibition on the use of (counter-) force as soon as cyber operations directed against them are likely to result in destructive effects equivalent to those normally caused by the use of kinetic, chemical, biological or nuclear weapons." (Melzer, 2011, p. 14)
The Intent
Except for the quantitative values conditioned by "scale and effects", the specific 'intent' is as well a precondition which distinguishes between less grave forms of the use of force and armed attacks. On the one hand, it constitutes a valuable indicator of the extent to which the political or military leadership of a state initiating cyber offensive is willing to violate another state's inherent right of sovereignty and, on the other hand, whether the act is not a deed of cyber terrorists, cyber criminals (i.e. inchoate malware activities), or it is inadvertently launched. Therefore, the availability of exactly determined 'intent' would preclude misjudgements where "the accidental spreading of malware" is to be qualified erroneously as "an armed attack based exclusively on the objective 'scale and effects' of the accident (Melzer, 2011)."
With regard to all said to this point, one scholar draws the following inference:
"…it is neither the designation of a device, nor its normal use, which make it a weapon but the intent with which it is used and its effect. The use of any device or number of devices, which results in a considerable loss of life and/or extensive destruction of property must therefore be deemed to fulfill the conditions of an 'armed attack'."(Zemanek 2010: para. 21)
Results-oriented approach
It is important to mention that although similar they might seem at first, consequence-based and results-oriented approaches are different.
Davis Brown's "results-oriented methodology" term refers to the work of Ian Brownlie, "International Law and the Use of Force by States" (1963). There Brownlie tried to explore the scope of an act and whether is a use of force by emphasizing on its consequences. For a leading point, he studied the chemical and biological weapons, concluding that they have the same result as the conventional ones—death and injury to civilians and military units.
Alike to the chemical, biological, and nuclear technology, cyber technology has a multitude of purposes. On the dark side of the coin, a cyber attack may cause a similar result as: "releasing flood waters by remotely opening a dam, causing a meltdown at a nuclear power plant, or rupturing an oil pipeline."(Brown, 2006, p. 187) Brown then concludes that "if an information attack achieves the same result that could have been achieved with bombs or bullets, then it has been conducted in the course of armed conflict (Brown, 2006, p.187)."
As a final proof, he examines a general denial-of-service attack under the results-oriented approach. By directing enormous amounts of artificially generated requests in order to disturb another computer's computational resources or network's bandwidth, the attacker attempts to incapacitate the adversary's assets and make them inoperative for the intended users. If the attempt is successful, then the technology is as useless as it is struck by kinetic force – "while no physical damage is inflicted on the system by a denial-of-service attack, the results is the same (Brown, 2006, p.188)."
Criticism
There are doubts based on the belief that Article 49 of Additional Protocol I to Geneva Conventions is not being taken into account and the focus is placed wrongly on the consequences instead of posing the question of whether or not the act is violent by nature as in Article 49. An effective methodology would try to promote the humanitarian principle that aim at less violent acts in favour of more violent ones, while the Brown's proposed one does not differentiate clearly (Walker, 2009).
As to the provided example, the juxtaposition of armed attack and DoS cyber attack would be considered improbable to sustain the result-oriented approach. Although users are deprived from access in this instance, there is no kinetic equivalent of act bearing violent consequences (Walker, 2009). Hence, here comes the logic question: Does a mere denying of computer services would legally warrant recourse to a full-fledged armed attack in self-defence (Article 51 UN Charter)? Using another example, would it be feasible for Estonia after being attacked by a massive DDoS to attack Russia (if the act is positively attributed to their government) with tanks, missiles, or nuclear weapon (if they had one)? Given the customary international law tenets of proportionality and necessity, a negative reply is almost always certain.
'Violent consequences' terminology in jus in bello
In order to dig deeper into the consequence-based approach, one must also look at the other foundational branch in the international law which regulates conflicts. Jus in bello or the Law of Armed Conflict may shed some light on the versatile character of the word 'consequences'.

Provision of interest:
The article to be referred to is again 49 (1) of Additional Protocol I, which provides a short explanation on the term "attacks", equalizing it with the expression "acts of violence". To discriminate between cyber attacks that cause mere nuisance or harassment and those that bring forth "human suffering", Schmitt uses the following articulation:
""Attacks" is a term of prescriptive shorthand intended to address specific consequences. It is clear that what the relevant provisions hope to accomplish is shielding protected individuals from injury or death and protected objects from damage or destruction. To the extent that the term "violence" is explicative, it must be considered in the sense of violent consequences rather than violent acts." (Schmitt, 2002, p. 377)
Hence, these "acts of violence" apparently do not necessitate the usage of kinetic violence, as far as the resulting aftermath is equipollent to that associated with kinetic physical violence, namely, death or injury of individuals or physical destruction or damage of objects (Melzer, 2011). As a result of this analysis, there can be concluded that under the consequence-based approach cyber attacks may fulfil the prescriptive requirements of Article 49(1) in the presence of three cumulative preconditions:
-
The consequences are not entailed by isolated, sporadic incidents
-
The consequences are desired and predictable to some extent
-
The consequences are intended to cause death/ injury or destruction/damage (i.e. violent consequences) (Kodar, 2012)
Inherent violence or violent nature argument
According to one theorist, "an act must be also one of inherent violence. Unlike pressing of a gun trigger, the outwardly innocent typing on an ordinary keyboard (a usual first step of IOA [cyber attack]) is not associated with inherent violence (Adler, 2011, p.3)."
She admits that these non-violent acts (typing on an ordinary keyboard) can "lead to all sort of violent outcomes" (Adler, 2011, p.3), but at the same time they cannot raise to an 'armed attack'.
This type of discourse, however, is rather contentious. Firstly, why we should limit our perspective of inherent violence to the design of the weapon of choice? Why the 'trigger' should have, so to say, more inherent violence than the 'button'? (See the images below) In the end, as children, we all played with toy guns having triggers that do not cause 'inherent violence'.
Secondly, in the light of the DDoS attacks against Estonia infrastructure in 2007 and the Stuxnet worm hit Iranian nuclear plant in 2010, the treatment above seems a bit groundless. In the first case, there was a death of civilian, and even though indirect, it is related to the cyber onslaught brought on the country, whereas in the second one, parts of the centrifuges in the nuclear factory at Natanz were destroyed.
The 'Grey Zone' in the consequence-based methodology
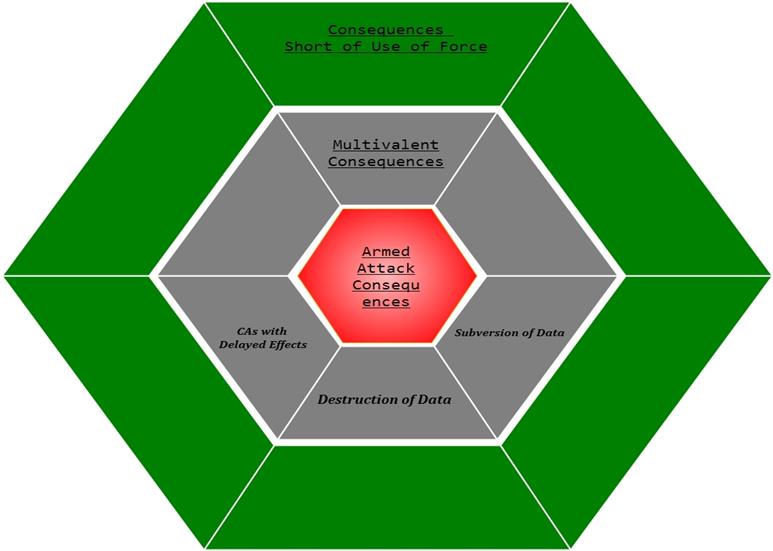
Fig.
"Grey Zone Consequences"
The 'Grey Zone' as concerns consequence-based approach refers to cyber operations which do not directly inflict violent consequences associated with a classic armed attack. In the article about the instrument-based approach, we discussed that the prohibition of 'force' does not cover the political pressure or economic coercion. Examined below are some activities conducted periodically in the cyber realm which theoretically fall short of force, thus belonging to this equivocal category.
Cyber Attacks in the Grey Zone:
Attacks with Delayed Effects
Those are, for example, logic bombs, Trojans, or trap doors which may produce negative effects long after their actual placement. Under the consequence-based approach, it would be arduous to make correct analysis on the distinction between uses of force, i.e. acts having instantaneous consequences, therefore reaching the threshold of force, and those kinds of coercion not reaching 'force' which need some time to blossom out (Barkham, 2001).
Destruction of Data
Another recurring aspect falling in the 'grey area' is the destruction of data such as formatting an enemy's command and control database. Prima facie, an action of that kind would constitute a 'destruction' of data, and 'destruction' is one of the violent consequences associated with kinetic force and their grievous impact on property (Kodar,2012). Apparently, a probable solution would require extension of the definition of property so as to embrace data (Barkham, 2001).
However, the main problem lays elsewhere. Viewed from the "scale and effects" standard determined by ICJ in the Nicaragua case, such an extension would most likely be too expansive — "…qualifying such action (the damage, destruction or manipulation of data) would dramatically lower the threshold at which States would enjoy a right to forcefully respond to actions directed at them…in the absence of authorization by the Security Council (Schmitt, 2012, p. 288)."
Subversion of data, Cyber Exploitation and Incursion
The use of IT means to gain initial access or alter/undermine data in a targeted system does not bring about damaging consequences to physical components in the traditional sense (Shackelford, 2009).
Harnessing their national intelligence capabilities, states could perform industrial cyber exploitation in attempt to promote their own infrastructure. As a result, the economy of the injured nation could be debilitated to the magnitude of violent consequences brought about on its society in causal chain of events beginning with an economy collapse, leading, in turn, to poverty and mass malnutrition, followed by death and injury of human beings (Barkham, 2001).
In spite of these gruesome images, the economic coercion is excluded from the competence of Article 2(4) of the UN Charter. Nevertheless, the 'attractive force' of consequence-based methodology would pin it down as a use of force (Barkham, 2001).
In addition, cyber incursion (e.g. Moonlight Maze), a.k.a. probing, does not outwardly look much different than cyber exploitation. Given the nature of these acts, there is often a great deal of confusion among the targeted personnel as to whether these activities have something to do with intelligence gathering or a cyber attack (Barkham, 2001).
Extending the consequence-based interpretation

Provision of interest:
The head of the ICRC's Legal Devision Knut Dörmann suggests broadening of the consequence-based interpretation in the event of a cyber operation so that the notion of force to include also the option to "neutralize" targets which constitute a military objective in the sense of Article 52 (2) of Additional Protocol I (Dörmann, 2004). The leading argument in favour of such an extension is that where the treaty enumerates which actions are legally permissible against objects offering a definite military advantage, the option of 'neutralization' is available alternative placed on the same level as 'total or partial destruction' (Melzer, 2011).
The opponents of such an expansion of the use of force invoke the interpretation of attacks as 'acts of violence' which entail either inherently violent acts or such producing violent consequences. Moreover, they stress that the proportionality principle tacitly excludes capture or neutralization, because is laid out in terms of attacks that cause solely "loss of life, injury to civilians, damage to civilian objects, or a combination thereof" (Melzer, 2011).
However, speaking in terms of empirical probabilities, perhaps it would scarcely be fair to omit the non-destructive incapacitation, so to say neutralization, of an opposing state's air traffic or defence system, for instance. Conversely, stretching the attack notion to any DoS against second-rated targets like telephone nodes, online shopping services, or social platforms, may seem not only exaggerated, but also perilous (Melzer, 2011).
On the other hand, if viewed from the perspective of offensive cyber operations, the 'neutralization' matter may provide a means to mitigate the negative impact on adversary's personnel and assets. In this regard, Dörmann opines that "when a nuclear electrical generating station constitutes a military objective, it could be attacked by means CNA (cyber attack) if the CNA only neutralizes the object without releasing dangerous forces in a way described by AP I (Dörmann, 2004, p. 8)." Hence, 'neutralization' of military object through offensive cyber operation could be a viable option at decision-maker's disposal, especially when attacking an object which strike may result in "releasing dangerous forces".
Conclusive apprehension
In conclusion, the jus ad bellum framework ultimately addresses only a small portion of the full-range of cyber attacks (Hathaway et al., 2012). Physical consequences touchstone, a foundation ingredient of this methodology, stands in direct correlation with the use of force as settled in the UN Charter. Many share the concern that this standard is too narrow. However, except for the fact that it represents the current lex lata, opening the ban on use of force wider may as well be equal to opening the Pandora's Box (Schmitt, 2012).
Reference List
Adler. H. (2011). Cyber Bellum? Retrieved from http://law.huji.ac.il/upload/AdlerHilaUpdated%281%29.pdf
Barkham, J. (2001). Information warfare and international law on the use of force. N.Y.U.J. INT'L L. & POL 57, 34.
Brownlie, I. (1963). International law and the use of force. Clarendon Press.
Brown, D. (2006). A Proposal for an International Convention To Regulate the Use of Information Systems in Armed Conflict. Harvard: Harv. Int'l L.J.
Dörmann, K. (2004). The applicability of the additional protocols to computer network attacks: an ICRC approach. In Bystrom, K. (Ed.), International Expert Conference on computer network attacks and the applicability of international humanitarian law: Proceeding of the Confrence. Stockholm: National Defence College.
ICRC (1977). Protocol Additional to the Geneva Conventions of 12 August 1949, and relating to the Protection of Victims of International Armed Conflicts (Protocol I). Retrieved from http://www.icrc.org/IHL.nsf/FULL/470
International Court of Justice (1985). Military and Paramilitary Activities in and against Nicaragua (Nicaragua v. United States of America). Retrieved from http://www.icj-cij.org/docket/index.php?p1=3&p2=3&k=66&case=70&code=nus&p3=90
Hathaway, O., Crootof, R., Levitz, P., Nix, H., Nowlan, A., Perdue, W., Spiegel, J. (2012).
California Law Review, 100 (4), 817-886.
Kodar, E. (2010). Applying The Law of Armed Conflict to Cyber Attacks: From The Martens Clause to Additional Protocol I. Retrieved on 02/07/2013 from http://www.ksk.edu.ee/wp-content/uploads/2012/12/KVUOA_Toimetised_15_5_Kodar.pdf
Melzer, N. (2011). Cyberwarfare and International Law. Retrieved on 02/07/2013 from http://www.unidir.org/files/publications/pdfs/cyberwarfare-and-international-law-382.pdf
Schmitt, M. (2002). Wired warfare: Computer network attack and international law. International Review of the Red Cross, 84 (846), 365-399.
Schmitt, M. (2012).
Shackelford, S. J. (2009). From Nuclear War to Net War: Analogizing Cyber Attacks in International Law. Retrieved on 02/07/2013 from http://papers.ssrn.com/sol3/papers.cfm?abstract_id=1396375
United Nations (1945). United Nations Charter. Retrieved from http://www.un.org/en/documents/charter/
Walker, P. (2009). Computer Network 'Attack': Implications for law and U.S. Doctrine. Journal of National Security Law & Policy, 33.
Zemanek, K. (2010). Armed attack. In Wolfrum R. (Ed.), Max Planck Encyclopedia of Public International Law. UK: Oxford University Press.





