File Decoys for Endpoints
In a typical scenario, threat actors try to gather as much information as possible (such as sensitive documents like credit card numbers, SSN details, and passwords stored in unprotected text files, etc.) about their targets after a successful exfiltration.
It is possible to detect such malicious attempts by deploying file decoys or baits on endpoints or emails. If an attacker tries to access such a decoy, an alert is triggered and logged into a centralized system.

What should you learn next?
In this document, we will be getting our hands dirty on creating the decoys using readily available tools at our disposal (PS: no macros). This document will cover the following:
- How the decoys work
- Creating image beacons for decoys using Python
- Creating file decoys and setting up unique identifiers
- Monitoring malicious attempts
Perquisites: Python 2.x, Apache server, MS Office Suite
Let's get started!
1. File Decoys – Understanding the Background
So, to understand the working of file decoys, first, we need to understand how HTTP works.
Below is a basic HTTP request and response model:

Below is the workflow describing how the decoys work.

In case of an HTTP request/response mode, a web-browser initiates a request for certain content. The web server locates the requested content and serves it as a part of response back to the browser. The browser then interprets the content and finally renders it. Initially, when the request reaches the web server, a log entry is made in the logs (e.g., access.log) depicting the origin, user-agent, timestamp, etc.
Similarly, in case of the workflow for decoys, a similar approach is followed. A word document is embedded with a linked image which is stored on the web server. Whenever the document is accessed/opened; the document tries to load the image from the remote location (i.e., web server), this, in turn, sends an HTTP request to the server. The server looks up for the image and delivers it to be embedded into the document. A log entry is created for this inbound request as well. In a real scenario, an adversary will try to get sensitive data from a system. A decoy will be placed with a lucrative name such as password-list.docx within the directory. Once the adversary tries to open the file, a request will be fired to the web server, and a log entry will be generated depicting that someone has infiltrated the system and is trying to steal away sensitive information.
2. Creating Image Beacons Using Python
Let's create an image beacon which will be linked in our decoys. The beacon will be 1x1 pixel by size with full transparency. Due to the miniature size of the pixel, it would not be easily spotted by the naked eye once the decoys are opened.
We will use python along with Python Image Library (PIL) module to generate a beacon:
from PIL import Image
img = Image.new('RGBA', (1,1), (0,0,0,0))
img.save('beacon.gif', "GIF", transparency=0)
This will create an image file beacon.gif. Save this file in the /var/www/ directory of your Linux web server. Now on the Linux box, start the apache service (service apache2 start) and check if the default page appears in the browser (http://localhost/).
3. Creating File Decoys and Setting Up Unique Identifiers
Once the beacon is ready, we need to embed the remotely deployed beacon into the office document file. Following steps will walk you through linking beacons for MS Word 2013.
Step 1. Open a word document > Click Insert
Step 2. Select Quick Parts > Click Field…
Step 3. Select IncludePicture and enter the path for beacon > Check Data not stored with Document
Step 4. Click Okay.
In an organization where file decoys need to be placed at multiple endpoints like the CEO's computer, the CFO's laptop, etc. it can become tedious to identify the source of the attack just based on the IP address of the system.
To overcome this shortcoming, we can append unique identifiers to the URL path for the beacon in Step 3. Let's assume we need to add two systems – CEO's desktop and the Head of Marketing's laptop; we will introduce distinct identifiers in the URL path by including pseudo parameters.
-
CEO's desktop
http://<server-IP>/beacon.gif?Pos=CEO&Name=UserName&Dept=Null&Origin=Dsk
-
Head of Marketing's laptop
http://<server-IP>/beacon.gif?Pos=HoM&Name=UserName2&Dept=Mkt&Origin=Lpt
So, when you run through the access logs looking for malicious attempts, it will be easier to differentiate as to whose system was infiltrated. After successfully embedding the beacon, it is time to fill up the document file with data which look lucrative for the adversary such as fake password details, credit card numbers, SSN, so on and so forth. It is mandatory that such data is entered to deceive the adversary. Additionally, rename the file such as password-list.docx or similar
to trick the adversary into believing that he has actually hit the jackpot.
4. Monitoring Malicious Attempts
This will be the last piece where we will monitor if an adversary has gained access to the system and tried to steal away and access our decoy.
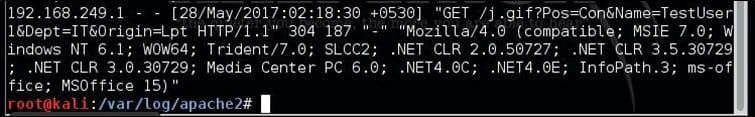
Go to the /var/log/apache2/ directory and open the access.log file using your favorite log viewer or text editor.
Deploy the decoys on the endpoint systems. Once the document is opened on the endpoint, it will send an HTTP request to our web server. You should be able to view an entry similar to the one below in the Apache's access log:

What should you learn next?
Where to deploy the decoys?
The decoys can be deployed anywhere, ranging from laptops, servers, desktops, emails, mobile phones, etc. Generally, the decoys can be deployed on HVT's (High-Value Targets) systems.




