Evolution of Banking Malwares, Part 1
Introduction
Why are malware authors so interested in banking malware? Simply because this is where the money is! Nowadays, banking malware, specifically banking Trojans, are reaching alarming new levels of sophistication. Each day, new names and new variations are constantly being introduced into the wild to thwart detection by antivirus software on the victim's PC and steal the user's cash.
Like always, a cat and mouse game between attackers and security guys:
On one side, financial institutions and AV companies have been fighting these malware that target online banking for years, and banks have evolved their security measures to protect online transactions from fraud. But in many situations, many of these security implementations are ineffective at protecting against the modern banking Trojan.
On the other side, cybercriminals who are motivated by financial reward are using these advanced Trojans to commit large scale financial fraud. These attackers avoid targeting the servers of these financial institutions, which are highly protected with multiple layers of security, but these cybercriminals instead attack online banking users by exploiting human weaknesses.
This article examines the current advanced state of banking malware in general. We will cover form/http grabbers, web injects, and PoS (Point of Sale) malware to automated online banking fraud ATS (Automatic Transfer System) and ATM (Automated Teller Machine) malwares.
Infection Life Cycle
There are various methods of spreading malware from a computer to another: malware authors were using mainly USB devices, email attachments, and instant messaging applications like MSN Messenger and P2P / warez networks like eMule where you can find cracks and keygens that contain malicious code. We have seen also drive-by downloads that contain fake codes, and Java Applet browser extensions that lead to malware.
Over the last few years, botnet owners need mass infections and have looked for a more valuable way of infecting millions of victims, so they made some automation apps and kits to facilitate its creation and distribution: exploit kits. These kits allow cybercriminals to easily scale their operations and evolve quickly to the changing infection vector landscape.
An exploit kit is a web application developed mostly in PHP, backed with a MySQL database that contains a number of exploits, rarely zero-days targeting mainly the browser (Firefox, IE …), Java, PDF and SWF applications. These exploit kits mostly come with a control panel that displays statistics, configuration and an installer, and also some features like blacklisting, AV scanning, etc.
Blackhole, Nuclear Pack, Sakura, and Redkit are a few well-known exploit kits' names.
When one of the previously mentioned apps is vulnerable, the EK automatically installs the malware in the victim's computer. Let's have a quick look at the infection lifecycle:
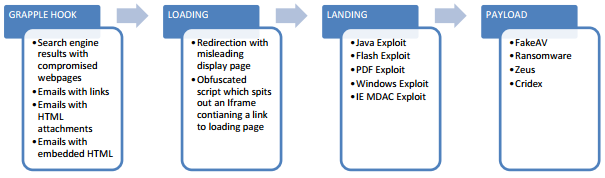
Using some tactics of social engineering attacks, innocent users usually click on a link: from a social network (likejacking and clickjacking tricks), phishing emails with links, a compromised web page or legitimate web page that has some malicious ads banner (malvertising), and then the user is redirected to the exploit kit servers that display a misleading web page. Redirection can be done simply via a server side redirection, flash based redirection, HTTP header redirection, an obfuscated script which spits out an iframe, or through advanced use of a Traffic Direction System (TDS). After the redirection, it lands to some sort of exploit that when successfully executed generates the payload, which installs the malware.
The Evolution of Financial Malware
In 2007, the arrival of Zeus heralded a breakthrough for fraudsters. This is where the majority banking Trojans comes from! The Trojan's ability to bypass multifactor authentication allowed criminals to hijack a fully authenticated session and then divert funds from compromised accounts.
According to Symantec, the number of infections of the most common financial Trojans grew by 337% in the first nine month of 2013. This represents nearly half a million infected computers per month that are susceptible to fraud. Let's have a look at banking malwares seen in 2013:
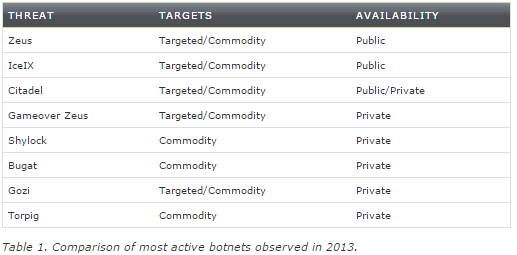
The distribution of these malwares is sometimes local and sometimes global. For instance, the Shylock botnet was mostly active in UK, Carberp in Russia, Tinba in Turkey and Bebloh in Germany.
Another point that must also be considered is that attackers preferred to target commercial banks, credit unions, and other financial institutions in developed countries with wealthy residents, because its people have more likelihood to have more cash in their account.
Furthermore, attackers tend to avoid countries where international transactions are more difficult and require local intervention to launder the money. Though most campaigns in 2013 focused on traditional banking websites, targets also included institutions that facilitate high-volume, high-value transactions, such as Automated Clearing House (ACH) or Single Euro Payments Area (SEPA) credit transfers. Many campaigns targeted corporate bank accounts and payroll systems.
Finally, banking Trojans are like rats: you kick a trashcan and six of them go scurrying off in every direction. Most of them you'll read about once and never again. Let me show you some work done by Wontok:
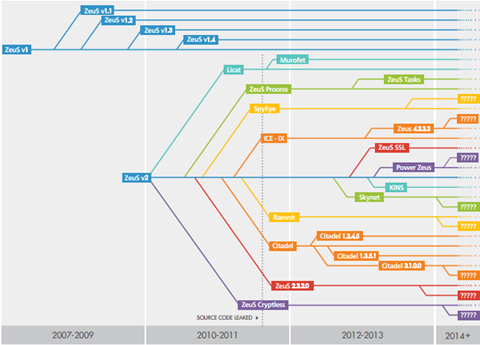
But there is a big four of sorts that just never seem to go away: Carberp, Citadel, SpyEye, and especially Zeus.
Now, I will provide you with a brief explanation of the features of these malwares. Later we are going to reverse engineer the banking part of the malware to understand technically how they work.
Carberp
The original version of Carberp was something of a typical Trojan. It was designed to steal users' sensitive data, like online banking credentials or username-password combinations for other high-value sites. Carberp relayed the information it stole back to a command and control (C&C) server under its creator's control. Simple and straightforward. The only tricky component was the complicated rootkit functionality, allowing the Trojan to remain unnoticed on the victim's system. The next generation of Carberp added plug-ins: one that removed anti-malware software from infected machines, and another that tried to kill off other pieces of malware should they exist.
Things got more interesting when its maintainers gave their Trojan the ability to encrypt stolen data as it passed between affected machines and their C&C server. According to researchers, Carberp represented the first time that a piece of malware used a randomly generated cryptographic cipher rather than a static key.
At one point, Carberp started working in conjunction with the most-notorious Blackhole exploit kit, generating an enormous uptick in infections. All was going well for Carberp and its authors. They had even managed to develop a Carberp module on Facebook that tried to trick users into handing over e-cash vouchers as part of a ransomware-type scam.
From there, things went downhill a bit. Russian authorities nabbed eight men believed to be responsible for controlling the malware, but Carberp did not die. Since then there has been no shortage of Carberp sabotage attempts and arrests. At one point, criminals seeking to deploy the tool would have to pay $40,000 for access to it until its source code was released last year, giving nearly anyone with enough know-how access to the Trojan.
Citadel
The Citadel Trojan is a variation of the king of financial malware, Zeus. It emerged, along with a number of other one-off Trojans, after the Zeus Trojan's source code leaked in 2011. Citadel's initial noteworthiness has a lot to do with its creator's novel adoption of the open-source development model that let anyone review its code and improve upon it (make it worse).
The group or groups of criminals responsible for Citadel developed a community of customers and contributors around the globe that would suggest new features for the malware, contributing code and modules as part of a criminal social network of sorts. Some of the most fascinating capabilities included AES encryption of configuration files and communications with the C&C server, an ability to evade tracking sites, the capacity to block access to security sites on victim machines, and a functionality that could record videos of victim activities.
The network of Citadel contributors continued adding newer and more dynamic features to the Trojan, making it more adaptive and faster, until it became utilitarian that criminals began using it for all stripes of credential theft.
Citadel saw big success until Microsoft and a coalition of other companies launched an operation that would eventually disable some 88 percent of its infections.
SpyEye
The SpyEye Trojan was supposed to be the banking Trojan that would come to compete with Zeus. In the end, SpyEye was like all men who are said to be heirs to Michael Jordan's greatness. They had hype, they had potential, but they couldn't take down the king. Zeus is the king, no doubt, but SpyEye made a fast disappearing splash.
At one point, parts of SpyEye botnet operation merged with Zeus's into a mega banking botnet, but it would ultimately burn out without living up to the hype. It had its successes though. Attackers deployed SpyEye in an attack targeting Verizon's online billing page, pilfering users' sensitive personal and financial information for more than a week without notice. It showed up on Amazon's Simple Storage Service, using the cloud provider as a platform for attacks. It showed up on Android devices at one point, but a series of arrests and perhaps just a lack of effectiveness ended SpyEye's run.
Three Baltic men were arrested in the summer of 2012 for using SpyEye to operate a highly organized banking information theft operation. In May of this year, an alleged SpyEye developer was arrested in Thailand and extradited to the United States, where he faces more than thirty counts of botnet and bank fraud related charge.
Since then, we haven't heard a whole lot about SpyEye.
Zeus
And then there was Zeus. Aptly named for the king of the Grecian Gods, Zeus is unparalleled in scope, use, and effectiveness. Since its source code was leaked in 2011, it seems that nearly every banking Trojan has flavors of Zeus built into it. Among these, only Zeus is notorious enough to have its own Wikipedia page. There are 22 pages, each containing ten stories, on Threatpost (the site where all these hyperlinks go to) making reference to the Zeus Trojan. You could write a Leo Tolstoy or Marcel Proust length novel about the shenanigans of the Zeus Trojan, so it's nearly impossible to briefly synopsize the threat, but we'll throw out some highlights.
Zeus burst onto the scene in 2007 after it was used in a credential-theft attack targeting the United States Department of Transportation. Since then Zeus has infected tens of millions of machines and resulted in the theft of hundreds of millions of dollars until its creator reportedly called it quits in 2011, publishing the malware's source code online. Many hundreds of individuals served or are serving jail time for their involvement in Zeus-related scams.
It was among the first pieces of malware sold via license. Until its source code was made public, Zeus was the scourge of banks and corporations alike. The list of its victims is too long to list, but includes prominent banks, corporations, and government agencies.
Zeus is also known for innovative usage of mobile "younger brother" called ZitMo to circumvent popular two-factor authentication schemes with a security code being provided via text message. SpyEye and Carberp developed their respective mobile counterparts as well.
Banking malware aside, the Zeus Trojan is among the most notorious of all malware, second only perhaps to Stuxnet.
Form grabbing and man-in-the-browser (MITB) attack
Form grabbing is a technique that allows the attacker to intercept the HTTP POST/GET data from the browser. Form grabbing steals data in HTTP POST/GET requests issued by a browser when an HTML form is submitted to a server.
Form grabbing uses two basic methods to steal the information:
-
All the GET/POST data is sniffed from the outgoing data using PCAP (Packet Capture). However, this technique only works for unencrypted communication (i.e. it doesn't work if SSL/TLS is implemented over HTTP).
-
Robust form grabbing uses hooking. In this approach, malware residing on the victim's machine hooks the browser's Dynamic Link Libraries (DLLs) in order to steal the content before it is sent to the server. If done correctly, the content can be stolen before it is encrypted. This theft can be accomplished by a variety of hooking mechanisms – a malicious browser add-on is one example (BHO, Browser Helper Object). A variety of hooking techniques can be applied such as inline hooking, Import Address Table (IAT) hooking or the Create Remote Thread (CRT) method, etc. Generally, browser hooking is done in user mode.
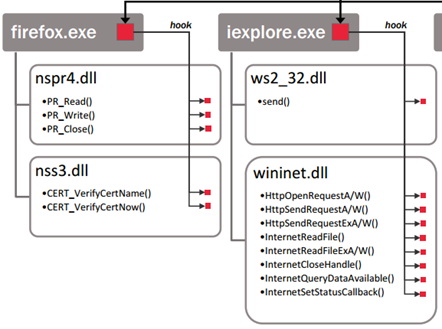
As you can see for example, Internet Explorer uses wininet.dll / ws2_32.dlll and Mozilla Firefox uses nspr4.dll / nss3.dll, these DLLs contain APIs to communicate with the sockets interface. For instance, the pr_write function is used to handle the data that should be written to a buffer before transmitting to the server. By hooking this API, you could read all the data written to the buffer when the form is submitted. Well known banking Trojans like Zeus and SpyEye first implemented form grabbing by hooking web browser APIs.

Become a certified reverse engineer!
Finally, this technique provides a major advantage over key-logging, because the data stolen through form grabbing is more readable, which reduces the amount of work that the malware author has to perform to clean unwanted elements.







