Everyone should learn the OWASP Top Ten, says John Wagnon
Infosec Skills instructor John Wagnon enjoys explaining technology and making it easy to understand, but learning those complex ideas as a computer engineering undergraduate wasn’t always easy.
“Some professors would try to explain stuff, and I'd go half the semester like, ‘Man, I don't understand a thing this dude is saying,’” John said. “Then it finally clicks. I would get mad because they could have explained it in this totally different way, and it would have made perfect sense.”
Get your free course catalog

It's a lesson he held onto while developing his new courses on the OWASP Top Ten critical web application security risks for Infosec Skills.
“A lot of this, it's really complex,” John said. “But if I can break it down to whet your appetite and get you hooked on the foundation, then we can go a bit further and understand the really deep details. That's what I try to do.”
The importance of the OWASP Top Ten
The OWASP Top Ten is naturally geared toward those in the web application world, but when asked who should take his new courses, John’s answer was simple: everyone.
“It's not like you can say, ‘I'm just going to live in a world where I don't deal with that stuff.’ If you do anything — if you do online banking, if you have an Amazon account, if you have a PayPal account, then welcome to the world,” John said. “I would rather know about it and get in the middle of it and figure it out than be like, man, I hope somebody has this thing under control.”
That’s particularly true for anyone working with technology — from network administrators to CISOs to CEOs.
“These are the top 10 risks out there,” John said. “Everyone should know what these things are, at least from a basic perspective.”
Understanding the most critical web application security risks
The first OWASP Top Ten list was published in 2003, and it's been updated every few years since, with the latest update in 2017.
“All of the risks deal with web applications, but they're not necessarily connected,” John said. “It's not like this one comes first and then this one after that. There are injection attacks, issues with authentication and access control, cross site scripting attacks — different types of risks.”
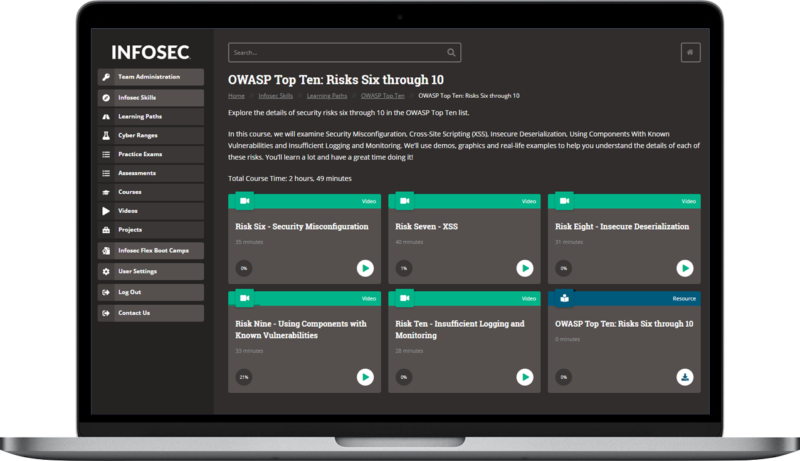
John’s courses walk through each of the OWASP Top Ten: what they are, what they look like and how to avoid them.
- Injection
- Broken authentication
- Sensitive data exposure
- XML external entities (XXE)
- Broken access control
- Security misconfigurations
- Cross site scripting (XSS)
- Insecure deserialization
- Using components with known vulnerabilities
- Insufficient logging and monitoring
Injection is the most well-known and dangerous risk, John said, but even these well-known risks remain a major issue for organizations.
“One of the top risks is people don't log properly,” John said. “Then beyond that, they don't monitor the logs they're supposed to create. If an attacker walks through the front door and steals credentials or whatever it is, you wouldn’t even notice. So that's a huge problem.”
The newest and least well-known issue on the list is insecure deserialization.
“It's brand new on the list, and it's kind of a niche thing,” John said. “So that may be the most difficult for some people to comprehend, unless you're really deep into programming and already understand serialization and deserialization and all of that.”
Everyone needs cybersecurity training
Cybersecurity is rapidly changing, and that means continuous education is important — for everyone.
“If you deal with web applications, host a website or deal with that world at all, it's important to know the world you're living in,” John said. “You need to know what these threats look like and if you're about to get hit with one.”
That’s why he recommends everyone take his OWASP Top Ten courses.
“Cybersecurity is getting bigger. It's getting crazier. No matter who you are, you can't get away from it.”
Learn more about John Wagnon’s Infosec Skills courses:
About John Wagnon
John Wagnon is a Senior Solution Developer for F5 Network’s DevCentral technical community where he utilizes the full spectrum of F5 technology to analyze and solve complex problems for F5 users all over the world. John is certified in several industry-relevant areas including CISSP, Certified Ethical Hacker and Six Sigma (Process Improvement).
Prior to his work at F5, John was a Communications Officer in the U.S. Air Force where he specialized in ground and satellite networks. After leaving the Air Force, he worked for a technology consulting firm where he analyzed cyber-attacks against U.S. Department of Defense computer systems and networks. John holds a Bachelor of Science in Computer Engineering and a Master of Science in Computer Networks.