Cyber Threats against the Aviation Industry
Introduction
The recent incident to the Malaysia Airlines Flight MH370 is fueling the discussion of whether would be possible to hack into an airplane and gain complete control control of on-board systems, excluding the pilots. In the past, we have seen many security experts present possible attack scenarios, but never has an attacker made them reality.
While the investigators still search for evidence that can provide more indications of what is really happened to the flight, some security experts also hypothesized that it could be the result of a cyber attack against the airplane. Some experts alerted to the possibility that it could be an attack against the in-flight entertainment system that allowed the hackers to infiltrate the security software. The theory was exposed by a British anti-terrorism expert who declared that similar attacks are possible due to the existence of specific exploits. The former scientific adviser to the UK's Home Office, Sally Leivesley, revealed Boeing 777 controls could be obtained with a radio signal sent from a small device.
Learn ICS/SCADA Security
The airplanes are very sophisticated systems. They are comparable to a complex network in which each system runs its software component that could be compromised exactly like the information exchanged by the parts.
Many investigators revealed that an attacker with a deep knowledge of the plane's system could intentionally cause serious problems with its normal operation.
"It might well be the world's first cyber hijack … This is a very early version of what I would call a smart plane, a fly-by-wire aircraft controlled by electronic signals … There appears to be an element of planning from someone with a very sophisticated systems engineering understanding … When the plane is air-side, you can insert a set of commands and codes that may initiate, on signal, a set of processes," said Leivesley.
An element that leads investigators to consider the possibility of a cyber attack is the silence of the plane's communication equipment.
Aircraft such as the Boeing 777 use many transponders to communicate their position to air traffic control. It is not simple to switch off all the transponders, and modern planes in fact are equipped with two other systems, the cockpit radios and a text-based system known as Aircraft Communications Addressing and Reporting System (ACARS), which can be used to send messages or information about the airplane.
In the case of the Malaysia Airlines Flight MH370, all the transponders appear to have been intentionally shut off, according NPR's Geoff Brumfiel.
Turning off the radios and ACARS would be more difficult. National Public Radio's (NPR) Geoff Brumfiel declared that pilots who collaborate with him confirmed that those systems are pretty hard-wired into a modern aircraft.
"Well, basically this Boeing 777 aircraft is equipped with a Satcom antenna, and so, a satellite orbiting way above the Earth was in contact with it. Every hour, the satellite would send a little signal going, are you still there? And the plane would send a signal back saying, yep, I'm here," said Brumfiel.
So how is it possible that the plane vanished?
U.S. government agencies are working with the Indian authorities to have access to radar data. The most plausible hypotheses are those about a hijacking, an event that, for the observed dynamics, would require careful preparation to disable all the controls and communication channels mentioned above.
"They [other pilots interviewed by NPR]said you'd have to go through big checklists, you'd have to possibly pull circuit breakers if you wanted to deactivate [all the communications equipment]," NPR's Geoff Brumfiel told
"All Things Considered" host Robert Siegel. "So, to do this, you'd have to have some degree of premeditation and a lot of knowledge of the aircraft."
New Scientist is reporting that the Malaysia Airlines jet sent out at least two bursts of technical data using the Aircraft Communications Addressing and Reporting System (ACARS) before it disappeared, a collection of useful engine data relates to critical flight systems and avionics.
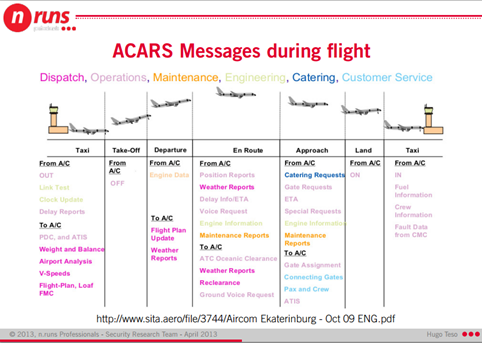
Figure - ACAR messages
Why has someone spoken about a possible cyber attack?
The hacking of critical systems in an airplane could not be totally excluded, as well as any other electronic system. A report filed on the US Federal Register website indicates that Boeing has implemented additional security measures on the 777 series of aircrafts five months ago to prevent onboard hacking of critical computer systems.
The improvements confirm the possibility that bad actors, under particular conditions, may harm the security of the flights. Boeing announced that it was upgrading the 777-200, 777-300 and 777-300ER series with the new security features.
"These special conditions are issued for the Boeing Model 777-200, -300, and -300ER series airplanes. These airplanes, as modified by the Boeing Company, will have novel or unusual design features associated with the architecture and connectivity of the passenger service computer network systems to the airplane critical systems and data networks. This onboard network system will be composed of a network file server, a network extension device, and additional interfaces configured by customer option. The applicable airworthiness regulations do not contain adequate or appropriate safety standards for this design feature. These special conditions contain the additional safety standards that the Administrator considers necessary to establish a level of safety equivalent to that established by the existing airworthiness standards," states the report.
As described in the above announcement, the experts at Boing were concerned about the possibility that the passenger inflight entertainment system would be connected to critical systems of the aircraft.
The "open door" for hackers are passenger seatback entertainment systems which have USB ports and come with Ethernet. Before the modifications mentioned, there was no "separation" between entertainment systems and the overall network of the aircraft. Boeing requested the Federal Aviation Administration the permission to add a "network extension device" to separate the various systems from each other. The design features designed for Boeing Model 777-200, -300, -300ER series airplanes include an on-board computer network system and a network extension device to improve the domain separation between the airplane information services domain and the aircraft control domain. The proposed architecture and network configuration may be used for, or interfaced with, a diverse set of functions, including:
-
Flight-safety related control and navigation systems
-
Operator business and administrative support (operator information services)
-
Passenger information systems
-
Access to internal airplane systems.

Figure - Passenger seatback entertainment systems
The modification requested and implemented by Boeing is a necessary improvement to prevent accidental or deliberate unauthorized access to any control system in the aircraft.
For now there isn't any regulation that specifically addresses the possibility to access to system architecture exploiting security vulnerabilities in peripheral systems.
"The existing regulations and guidance material did not anticipate this type of system architecture or electronic access to aircraft systems. Furthermore, regulations and current system safety assessment policy and techniques do not address potential security vulnerabilities, which could be caused by unauthorized access to aircraft data buses and servers."
The Federal Aviation Administration approved the license change the architecture for Boeing aircrafts assigning to the company the responsibility to ensure that adding the network extension would not have an impact on the aircraft's flying capability.
Airplane hacking with a smart device
Exactly one year ago, the security community was intrigued by the news regarding the possibility to hack the navigation system within an airplane with an Android Smartphone. The news was alarming because just by using a limited resource, a hacker is able to take control of the entire control system on-board, including plane navigation and cockpit systems. The researcher Hugo Teso, a security consultant at N.runs AG, Germany, with a passion for flying, demonstrated at The Black Box security conference in Amsterdam that just using an exploit framework, dubbed Simon, and an Android app it is possible to gain remote control system inside an airplane.
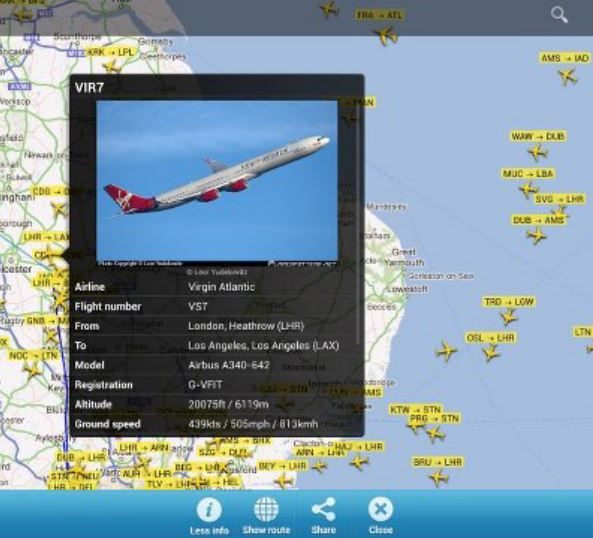
Figure - Teso's App
The application proposed by Teso was proof of a concept developed to alert the Federal Aviation Administration, European Aviation Safety Administration, and principal aircraft manufacturers, on the risk related to an attack. The risk is concrete according the researcher, and all principal actors in the aviation industry must consider security by design to avoid disturbing consequences.

Figure - Teso's presentation slide on SIMON
The researcher demonstrated that it is possible to hack the on-board components eavesdropping the system's communications over its 1MBps link and injecting specially crafted data.
"You can use this system to modify approximately everything related to the navigation of the plane," explained Teso.
The researcher remarked that by sending navigation commands via radio signals, it is possible to control the system of planes using a publicly available Flight Management System (FMS).
Flight Management Systems are exact copy of system on board. The researcher spent the last 3 years discovering the flaws in the standard system installed on the aircraft. He bought FMS hardware on eBay. Forbes magazine reported that FMS used "was advertised as containing some or all of the same code as the systems in real planes".

Figure - FMS 101 used by TESO
The researcher successfully hacked the principal system on-boards like the Automatic Dependent Surveillance-Broadcast (ADS-B) and Aircraft Communications Addressing and Report System (ACARS).
We have discussed ACARS before, so I desire to give you further information on ADS-B, also known as Automatic Dependent Surveillance-Broadcast, which is a cooperative surveillance technology for tracking aircraft. The aircraft provides its own position via GNSS and periodically broadcasts this via a radio frequency. It is able to manage traffic data, weather reports, a terrain overlay broadcast for pilots to view in the cockpit, and of course flight information.
"I expected them to have security issues but I did not expect them to be so easy to spot. I thought I would have to fight hard to get into them but it was not that difficult," Teso added.
A week after the Teso's presentation the Federal Aviation Administration (FAA), the European Aviation Safety Administration (EASA) and Honeywell, which provides the vulnerable cockpit application, have expressed their dissent to the researcher, denying any concrete risk for flight safety. FAA commented: "The described technique cannot engage or control the aircraft's autopilot system using the FMS or prevent a pilot from overriding the autopilot … [it] does not pose a flight safety concern because it does not work on certified flight hardware."

Figure - FAA denies alleged smartphone airplane hack can work on real planes
Other cyber threats to aviation industry
Many experts sustains that a Boeing 777 could be remotely reprogrammed from the ground. The autopilot has a crucial role to prevent terrorism acts and could be instructed to force the airplane landing in case of emergency.
The Boeing vehicle, exactly like the new generation of drones, is equipped with an emergency intervention system that would allow a remote operator to land the aircraft from the ground simply through the autopilot. According to official sources, the procedure was never used until today.
Hugo Teso isn't the only hacker to have hacked the critical system of an airplane. Despite FAA denial of any security flaw risky for passengers, a 33-year-old Canadian known as RenderMan (aka Haines) made an interesting presentation on the topic during the DerbyCon 2013 conference titled, "Attacking the Next Generation Air Traffic Control System."
http://www.youtube.com/watch?feature=player_embedded&v=1pVP2DhR9Us
Figure - RenderMan's Presentation
RenderMan declared that an attack on control system is surprisingly easy:
"Anyone can listen on this to find the location of a plane in real time," he said.
The NextGen system is used to track every plane in flight. It is a system based on GPS data rather than traditional radar, and it allows a refined tracking of aircrafts in respect to other systems.
RenderMan remarked that despite the fact that NextGen comes at a cost in the billions of dollars and is still under implementation, it may contain the same vulnerabilities exploited by Teso in its hack based on the Android app. Positioning information between plane and ground controls are not encrypted, and the communication is established without mutual authentication processes, an ideal condition for a potential attack.
RenderMan and the colleague Nick Foster have defined an attack strategy that consists of the insertion of dozens of false flights to the control system. Of course, the interferences influence the overall flight plans. RenderMan said that it is possible to create fake "ghost planes" by spoofing signals:
"If I can inject 50 extra flights onto an air traffic controller's screen, they are not going to know what is going on," he told NPR. "If you could introduce enough chaos into the system - for even an hour - that hour will ripple though the entire world's air traffic control."
Also in this case, Haines alerted the TCCA, Canada's version of the FAA, and the FAA itself. Many of you will be surprised why encryption is not largely adopted. Haines's findings revealed that data encrypting would be a management nightmare that could cause even more problems.
"You can use [these findings] to educate traffic controllers and pilots … Maybe we should build some protocols to flag things on the 'weirdo' meter. If you get 50 extra flights, that's probably not a technical glitch. It's someone attacking you. Call the guys with the jackboots and guns … For the longest time it was, oh it's too expensive, you need specialized hardware. Now with software-defined radios and technology that has come so far, I don't need half an airplane cockpit to talk to this this stuff," he told FoxNews.
Jamming Attacks against Next-Gen Flight Control System Vulnerable
Jamming attacks are among principal cyber threat against Next-gen control systems, Automatic Dependent Surveillance-Broadcast (ADS-B) systems are susceptible to jamming attacks. Recently, a group of researchers from the Kaiserslautern University of Technology in Germany, Swiss federal agency Armasuisse, and the University of Oxford in England, demonstrated that attackers using a wireless network and off-the-shelf equipment are able to create serious problems to the sophisticated components in the modern aviation industry.
As explained by the researchers, the ADS-S is designed to replace the outdated ground radar system for the airplane navigation in flight, and it will be mandatory worldwide in 2020.
The researchers presented their study last year at the Applied Cryptography and Network Security (ACNS 2013) conference. They analyzed the security of next generation air traffic surveillance technology based on Automatic Dependent Surveillance Broadcast (ADS-B). ADS-Bs are susceptible to different types of attacks, including spoofing attacks and jamming.
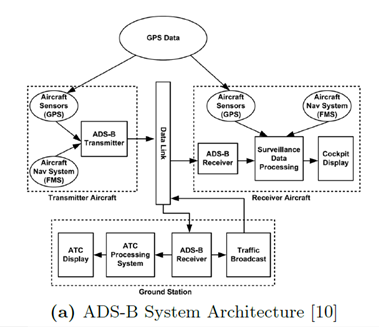
Figure - ADS-B System Architecture
In the previous paragraph it was explained how the attackers can inject a "ghost" flight into the next-gen control systems, alter the virtual trajectory of airplanes currently in flight, or delete the planes from the screens. This kind of attack is very dangerous because the attackers can compromise accuracy of information provided to the pilots (e.g. Location, direction and speed of other flights).
Another possibility for attackers is to expose ground stations to jamming attacks consisting in the intentional emission of radio frequency signals to interfere with the operation of a radar. The principal jamming types are:
-
Mechanical jamming realized in reflecting or re-reflecting the radar energy back to the source to produce false target returns on the operator's scope.
-
Electronic jamming where specific device jammers generate signals able to interfere with target's radar, blocking the receiver with highly concentrated energy signals. The principal methods are noise techniques and repeater techniques.
This type of attack against ground stations in radar systems represents a serious menace as explained by the researchers. The method of attack proposed by the team of researchers, dubbed Ground Station Flooding, consists of a series of jamming attacks on a ground sensor or aircraft causing the losses and deletion of messages. Loss of messages could force the adoption of less efficient or less accurate surveillance and control methods. In high density areas (e.g. Around major international airports) for example the failure of surveillance or collision avoidance could result in human failure with fatal consequences. In the Ground Station Flooding experiment conducted by researchers, the attacker emits a continuous white noise jamming waveform. This waveform caused complete deletion of all messages.
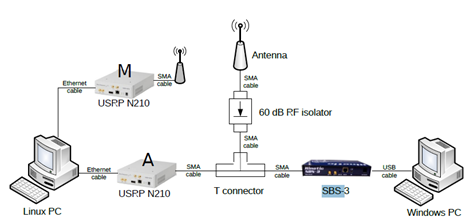
Figure - Test Lab configuration
The researchers demonstrated that an attack could produce fake alarms such as those an aircraft might transmit during an emergency or terrorist attack.
"Without appropriate countermeasures, critical air traffic management decision processes should not rely on ADS-B derived data," the researchers said. "We hope that the rule makers and regulators involved in the ADS- B standardization process will recognize the criticality of the described threats and include security as one of its key requirements in future releases," said a member of the team.
Conclusions
It's my opinion that a flight simulator or an FMS sold on the Internet, despite that it could be an excellent reproduction of the system in production, cannot represent an identical copy of a real environment. Modern aircraft are equipped with the most advanced technologies, and every single component has its own application that dialogues with others using an internal network. It's clear that in this complex scenario, the presence of a single bug could be exploited by attackers to gain control of critical components within the plane.
Security is fundamental for the aviation industry. Considering the availability of numerous tools on the market that could be exploited in a hypothetical attack against a plane, cyber security is becoming even more crucial. It's time to adopt for civil uses the same technologies designed for a military environment.
References
http://securityaffairs.co/wordpress/13625/hacking/hijacking-planes-navigation-system-with-android-reality-or-unnecessary-alarm.html?preview=true&preview_id=13625&preview_nonce=dab51d3d6a
http://en.wikipedia.org/wiki/Radar_jamming_and_deception
http://www.securitytube.net/video/8536
http://www.lenders.ch/publications/conferences/acns13.pdf
http://www.interferencetechnology.com/next-gen-flight-control-system-vulnerable-jamming-attacks/
http://theaviationist.com/2014/03/20/mh370-total-recap/
http://guardianlv.com/2014/03/boeing-777-could-have-been-reprogrammed-from-the-ground/
http://www.foxnews.com/tech/2013/04/12/hacking-in-flight-airplane-did-that-year-ago-hacker-says/
http://www.ibtimes.co.uk/malaysia-airlines-flight-mh370-could-jets-system-have-been-hacked-1439928
http://www.npr.org/2014/03/14/290242398/the-difficulty-of-making-a-modern-airplane-disappear
http://aviation.stackexchange.com/questions/2292/can-a-boeing-777-be-hacked
http://nakedsecurity.sophos.com/2013/04/16/airplane-hack-security-faa/
http://dailycaller.com/2013/04/11/faa-strongly-denies-alleged-smartphone-airplane-hack-is-a-problem/
http://blog.nknj.me/python-guide-to-hacking-on-an-airplane
http://www.interferencetechnology.com/next-gen-flight-control-system-vulnerable-jamming-attacks/
http://nats.aero/blog/2013/10/is-air-traffic-control-a-soft-target-for-hackers/
http://www.cnbc.com/id/100784103
Learn ICS/SCADA Security
http://www.aiaa.org/uploadedFiles/Issues_and_Advocacy/AIAA-Cyber-Framework-Final.pdf


