Converting a PCAP into Zeek logs and investigating the data
Use case for analysis
Let's learn how to take a PCAP from the malware-traffic-analysis.net website and transform it into Zeek logs using Brim. We will then break down the log files to see what patterns we can find. You'll learn how to use data from Zeek (a tool we overviewed in previous articles) during an investigation. And, we'll comb through the different log files and discuss what they mean and why they are useful.
Get your free course catalog

Tools and websites used
Brim
- Brim has many different capabilities
- For this article, we will use the tool to transform PCAP data into Zeek logs
- Brim has a great UI to explore Zeek logs in a 'user-friendly' manner
Malware-Traffic-Analysis website
- A website devoted to hosting various network traffic exercises and PCAP files
- We will explore the data in the "2015-01-09 Traffic analysis exercise - Windows host visits a website, gets EK traffic" exercise for this article
Environment setup
First, we will need to download the appropriate tools and files for this use case. I'll start by pulling the PCAP file from the malware-traffic-analysis.net website.

After I downloaded the PCAP file safely, I downloaded Brim for MacOS. You can find all the versions and platforms Brim supports to use the tool yourself.
I then uploaded the PCAP file to the Brim system and received the below output.
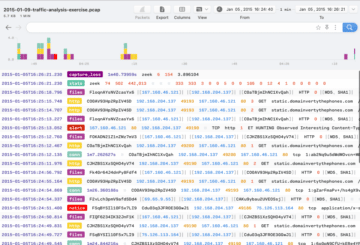
From here, we are now ready to explore the data. You can also use the questions provided on the malware-traffic-analysis.net website as a starting point if you wish to dive deeper into the data.
What does this data mean?
Brim took the PCAP and generated the associated Zeek log files from the data. We can see a breakdown of the type of activity seen in this capture from the above screenshot.
The below outlines the types of Zeek logs derived from this file that we care to look at:
- HTTP (contains HTTP requests and denies)
- files (results of file analysis, contains MD5s and SHA values)
- conn (records TCP/UDP/ICMP connections)
- notice (logs for activities that seem out of the ordinary)
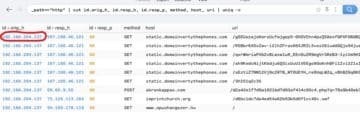
Now let’s dive into a few of the common files produced by Zeek (as seen in the Brim UI). By exploring the "HTTP" logs, we can see the IP address of the host machine associated with this activity.
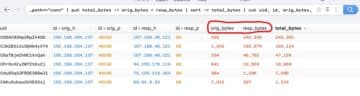
The "conn" log file shows us the data transferred between connection attempts. Looking at the overall number of bytes transferred to and from a system can help with baselining and identifying spikes in activity.
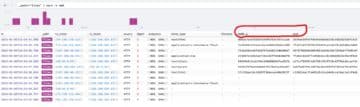
The "files" log file provides detailed information (MD5, SHA1, etc.) about files analyzed during Zeek’s analysis.
Zeek and Brim live demo
Our goal for this article was to show how to load a PCAP file into Brim and explore the various Zeek log files it creates. However, there are numerous websites and exercises available to practice your network traffic investigation skills if you’d like further practice.
In a recent Infosec Edge webcast, I walked through how to use data derived from a PCAP file to create Zeek logs (similar to what we did in this article) and then upload the data to an open-source SIEM (Elastic SIEM). Watch the Learn intrusion detection: Using Zeek and Elastic for incident response webinar below to learn more.
Want to learn more? Take my Advanced Intrusion Detection courses in Infosec Skills.




