Computer Forensics: Forensic Issues with Virtual Systems
What is Virtual System Forensics?
When something is virtual, it is almost the same as the original—but not quite. In computing, this emulation can be particularly handy, especially when it comes to experimenting with large, complex systems. In their many forms, virtual systems provide the same functionality as physical computers, OSs, applications, hardware, and software but without the possibility of failure. Why? Because all of their abilities—from booting up to shutting down—are just an imitation of what a real, tangible machine or system would do. And as such, they offer a tremendous opportunity for users to beat up different OSs, play around with suspicious applications, or hook up peripheral devices like USB flash drives without fear of negative consequences. If a problem comes up like a virus or a mismanagement of the network, a virtual system will behave just as a real system would. And as a result, they are the perfect tool for information security experimentation because they allow the user complete freedom to make mistakes, much like a child in a sandbox.
Because virtual machines can perform the same processes as actual systems, they are also able to track and record the activity trail of users. These capabilities makes them incredibly useful tools in the quest to learn more about digital forensics, as they can produce evidence to be used to enhance understanding and application. For example, Virtual Forensic Computing (VFC) was first launched by the tech community in 2007 and has become essential software for forensic investigators, as it allows for seamless recreation of a digital crime scene using real, discovered evidence. It is the go-to software for law enforcement who use it to take images from a suspect’s computer; launch a suspect machine in its native environment; take screenshots of key evidence, and view files and data in its natural state.
Learn Digital Forensics
What are the Types of Virtual Systems?
There are several different ways to engage in virtualization, each of which has a disparate effect on network security and forensics. Some of them focus on application-server virtualization, while others manage elements related to system networks. Users who employ virtualization of any kind should understand their current security procedures and where they might find gaps in security protocols. In this way, virtualization is customizable and available as a tool to help businesses grow, thrive, and boost their security at the same time. Virtualization is also key to forensic investigations because it allows authorities to view the digital environment in exactly the same way the suspect did. Although this may not be appropriate for every situation, an intruder who compromises a virtual system can likely compromise the host machine as well.
Through virtualization techniques, you can run multiple operating systems simultaneously on a single machine
Virtual Machines
Visualization of an OS or application environment is the most common form of virtualization, as it can save companies lots of money, resources, and time. Once installed on software, a virtual machine imitates dedicated hardware and offers users the same experience as a real, tangible computer.
This is one of the main benefits of a virtual machine, as their ability to operate on any underlying hardware and software configuration adds flexibility and creates an ease of sharing.
Because virtual machines are such an important part of today’s networks, they also play an important role in computer forensics. One of the best things about virtual hardware is the fact that it doesn’t fail, which means administrators can take advantage of virtual environments to hone a successful disaster recovery plan (DRP) and other such system administration tasks. This documented, structured approach allows users to respond more effectively to unplanned and problematic incidents related to breaches in cybersecurity, thereby minimizing the effects of a disaster and allowing organizations to continue with business as usual.
Service Based Systems
Service virtualization offers a way to mimic the workings of certain component-based applications and service-oriented architectures so as to remove constraints and increase development opportunities. As a virtual tool, it assists in software development and testing while extending across all communication components using common messaging protocols. And because this service can isolate specific behaviors testers want to examine more closely, it can virtualize those critical to disaster recovery and forensic analysis with great clarity. The cost and complexity associated with a real-world breach in security is greatly reduced by virtualization.
The Cloud
As software and services running on the internet, cloud services are accessed through a Web browser and allow users to access data on any device. Security is often cited as one of the biggest problems in cloud computing, mostly because it handles such a massive amount of data and is an attractive target for malicious actors. And this large amount of volatile data held on the cloud is often what make it such a forensic headache. The goal is to stop these breaches before they become reality so remedial action can be adopted before real damage is done. The use of Forensic Virtual Machines (FVMs) allow investigators to run numerous instances to find symptoms of hacking while potentially limiting attack vectors.
What are the Types of Virtual System Architectures?
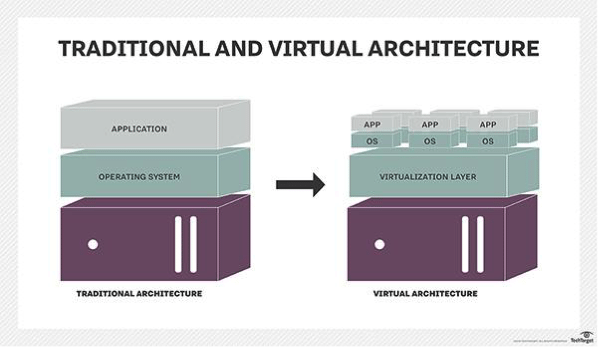
Most computers have multiple layers of both hardware and software that operate together as one system. These resources usually include a central processor, display, storage, networking, and other peripheral devices. A virtualization architecture is typically based on hypervisor software which can isolate OSs and applications from the host computer so it can run on multiple virtual machines, sharing resources, memory space, network bandwidth, and so on. Virtual architecture differs from that of traditional computing in that it can run several OSes on top of the virtualization layer—something exclusive device ownership does not allow. Virtual machine technology compensates for this limitation by redirecting interactions with device resources to lower system levels in a way that higher-level application layers not not affected. But forensic investigators must know how to analyze the hypervisor software associated with virtual machines using their architectural features. While testing software on physical machines requires a flattening of the hard drive and a rebuilding of the system—a process that is both laborious and expensive—hypervisor software can be replicated in a short amount of time. This means organizations can feasibly use machines within virtual systems as evidence in a larger forensic tool box.
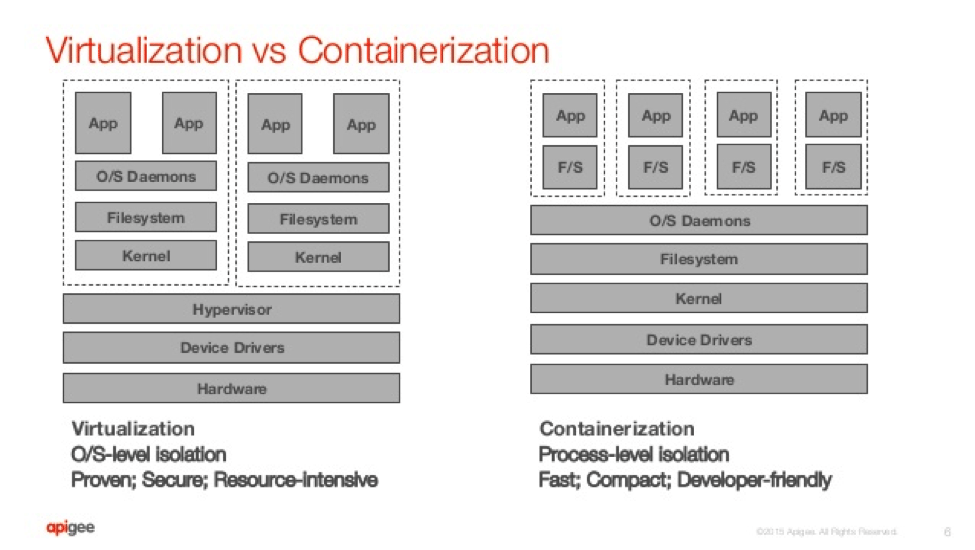
Type 1 hypervisors (also known as “bare-metal") run right on top of the host system hardware and offer high availability and resource management. This architecture fosters better performance, scalability, and stability.
Type II hypervisors (also known as “hosted") are installed on top of the host OS which eases system configuration and simplifies management. That said, the addition of the OS layer can feasibly limit performance and reveal potential security flaws in the OS.
Containerization (also known as “container-based”) is the main alternative to hypervisor-based virtualization. It functions on the OS level and runs distributed applications without the need to launch an entire virtual machine for each one. Instead, it runs multiple isolated systems—fittingly known as containers—on a single control host while accessing a single kernel.
What are some Forensic Issues with Virtual Systems?
There are two common types of investigative analysis involved in digital forensics: live and dead. The former happens while a machine is running and often focuses on things like open files, running processes, network connections, and volatile malware. In many cases, systems need to continue running for as long as possible to provide the insight authorities need to find evidence. Dead analysis, on the other hand, occurs while the machine is turned off and an identical image of the machine’s storage media is created and analyzed for relevant findings. This reduces the possibility of source contamination and makes investigating static data from a system easier. Both approaches have inherent strengths in the way they approach and retrieve evidence in the form of data—but they also have a few weakness to keep in mind.
For example, when a forensic investigator accesses a live system to gather information, they use third-party or built-in forensic tools that can make interpretation more challenging because the native OS PI’s are not available. That means information must be gathered by locating and looking at the internal data structures of the in-guest application programming interface (API). This inability to get what is needed is known as the semantic gap problem, and it characterizes the difference between two descriptions of the same thing—in this case, the data on the screen. In other words, it can get lost in translation. But fear not, there are some solutions available.
VirtualBox
This cross-platform virtualization software can be installed on existing Intel or AMD-based computers, regardless of their OS. It helps users simultaneously run multiple OSes on existing computers, essentially creating a special environment where multiple virtual machines can run on a single physical machine. This tools helps with learning, testing, and getting the most out of computer performance.
VMware
With this type of server virtualization, multiple virtual machines can run on the same physical server by installing a hypervisor on the main device, each of which runs its own OS. This means many OSs can run on one physical server, thereby allowing virtual machines to share resources such as RAM. The most recent 2017 version, vSphere 6.5, offers networking and security management tools, and comes in three editions: standard, enterprise, and enterprise plus.
Interested in taking a technical computer forensics course? Check out InfoSec Institute's course offerings by filling out the brief form below.
What are the Forensic Process Steps?
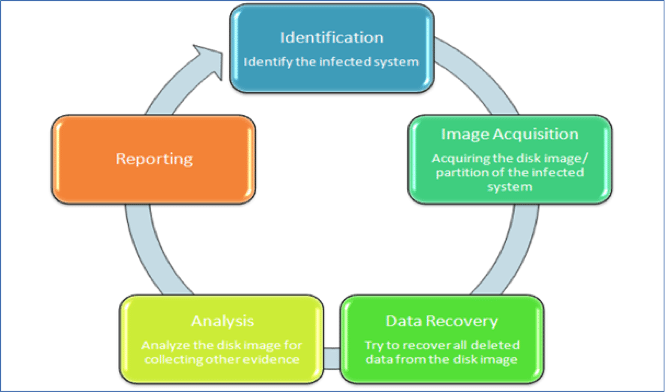
As law enforcement and legal entities continue to realize just how valuable IT professionals can be in digital forensics, the field has grown into a valuable tool for protecting public and private entities. As well as government and national security. The ability to track the digital movements during an attack has provided physical evidence in criminal cases and allowed authorities to uncover the forces behind many, many cyber-crimes. The success of these efforts is based on a the integrity of five main steps:
Learn Digital Forensics
- Policy and Procedure Development
Much like traditional evidence, digital findings can be delicate and highly sensitive, which means cybersecurity professionals must handle them properly if they want to maintain the integrity of the investigation. Strict guidelines and procedures must be followed regarding timing of recovery, authorization, evidence retrieval, storage, and documentation. Best practices must be continually updating using recent findings, and rigorous training programs must accompany all professional efforts. This governance is essential to the integrity and efficacy of digital forensics and remains an integral part of all investigative policies. - Evidence Acquisition
Arguably the most critical step in computer forensics, acquiring evidence requires a robust and detailed plan. There must be extensive documentation before, during, and after the investigation, and all details must be recorded and preserved—in this case, possibly hardware, software, or any related systems. General guidelines for keeping evidence safe includes a physical removal of storage devices, retrieving sensitive data using controlled boot discs, and taking proper steps to copy and move evidence to the authority’s system. - Evidence Assessment
Any evidence found during an forensic investigation must be properly assessed to gain a clear understanding of the case and its many details. This includes targeting the computer zones where crime-related evidence is likely to exist, like social networking, email, and personal files. Before the crime can be analyzed and hopefully solved, the types of evidence presented must be well defined and preserved. - Evidence Examination
Digital findings in a criminal investigation are valuable, which is why they must be retrieved, copied, and stored within the appropriate databases. Typically, this data is analyzed from designated archives using a bunch of different methods and approaches. This step involves knowing how to search massive archives for specific keywords or file types and retrieving anything that has been recently deleted. Data tagged with dates and times is particularly useful in these efforts, as are suspicious files and programs than have been intentionally hidden or encrypted. - Documenting and Reporting
This is the frosting on the forensic cake because it means evidence has been successfully found, retrieved, and stored. Investigators must keep a clear record of all the activity related to the effort, including the methods used, actions taken, and examinations performed. This demonstrates integrity and ensure all policies have been properly followed. If this step does not happen correctly, it is entirely possible that evidence presented in a court of law will be dismissed due to a compromise in its validity.