Botnets, how do they work? Architectures and case studies – Part 2
In the first part of this of this mini-series on the botnet cyber threat, we have shown the current scenario and the technological evolution in security landscape. Malicious architectures are increasingly becoming one of the principal problems for security experts. Click here to see previous article.
Various researches conducted by principal security firms have revealed the use of botnets for different purposes. The most interesting architectures are designed for the following scope:

What should you learn next?
Computer frauds and scams – cybercriminals are deploying malicious structures with the primary intent to monetize their efforts in illegal activities. The principal purpose is the acquisition of banking credentials to steal money from the victims. Typically, the criminals issue malware with the specific intent of infecting victims and collecting payment information. Zeus and ZeroAccess are two of the most interesting malicious code used with this specific purpose. ZeroAccess is the world's fastest-growing botnet detected in 2012. It infected millions of computers with the primary intent to commit large-scale click fraud and Bitcoin mining. The Zeus botnet is a banking Trojan. Both agents cause millions of dollars in loss to victims by siphoning money from their online bank accounts. Recently the soaring of the value of Bitcoin has attracted the cybercrime industry that is proposing new malware able to compromise victims and use their computational resources to mine the virtual currency.
Cyber-attacks and hacking services renting – botnets are largely used also to conduct cyber-attacks against various targets for different purposes such as hacktivism or offensive actions (e.g. A company that hit services of its competitors.) A growing number of organizations in the underground offer all that is necessary to build a botnet and conduct a cyber-attack. It is easy to find criminals that rent entire architectures or that sell hacking services such as DDoS attacks. The model of sale is efficient, and services provided various as cheap. The model of sale dubbed "malware as service" is attracting many criminal groups even if they haven't particular skills.
Cyber warfare and cyber espionage – recent events have demonstrated the high interest of a state-sponsored entity to operate cyber warfare and cyber espionage operations. In many cases, sophisticated malware has been designed with specific intent to steal sensitive information and intellectual property. Governments such as China, Russia and Korea are considered persistent collectors. Their efforts are known and is considered a dangerous menace for governments and private business. Also in this case, the botnet represents the optimal solution —millions of "soldiers" enrolled behind the enemy lines and able to silently act from the inside of target countries. Botnets allow attacker to remain anonymous during the campaigns, state sponsored botnet are quite different from others due the large use of zero day exploits that request bigger effort in term of research.
The trend observed by principal security firms is an increase of the level of complexity used by botnet authors that are exploring new ways to avoid the detection of defense system security watchdogs spread in the networks by security firms. In the following paragraphs, we will analyze some of most interesting and singular architectures implemented by botnets authors to improve their creations, the great diffusion of malware in th cybercrime underground has been accompanied by the providing of various services offered to customize the most popular malicious code according clients request. In many cases the source code of the malware was published on internet underground, giving the opportunity to third-party criminal organizations to modify it —implementing according the needs expressed by a growing demand.
Peer to Peer botnets
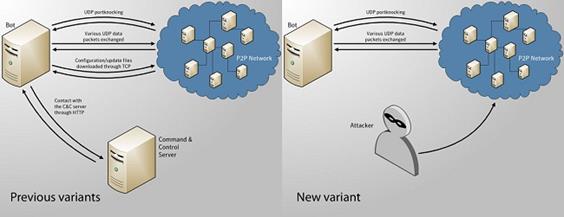
The security industry has monitored since its beginnings the evolution of the Zeus malware. It is considered the longest-running malicious code that raged for months, appearing in various forms on the web thanks to the various improvements made by the cybercrime industry. During the investigation, researchers at Symantec discovered at the end of 2011 a new variant of the popular malware that attracted their attention because itdoes not rely on command and control (C&C) servers for receiving commands.
Zeus variant uses P2P communication to transfer commands from compromised hosts belonging botnet infrastructure, security experts believe that P2P communication has been implemented as backup system in case the C&C servers are not reachable. In similar structures, each node can operate as a slave or as master giving orders to other bots and exchanging information acquired illegally from the victims.
The variant detected by Symantec appears really complex because doesn't use C&C servers implementing an autonomous botnet that dispenses from the presence of dedicated control servers, the security researcher Andrea Lelli declared:
"Every peer in the botnet can act as a C&C server, while none of them really are one,"
"Bots are now capable of downloading commands, configuration files, and executable from other bots — every compromised computer is capable of providing data to the other bots,"
Figure 1 - Peer 2 Peer Botnet Architecture
Each bot is able to work as a client that executes orders as a command server due the presence of a light web server such as nGinx that equips the malware, the communications between the nodes in the network is based on HTTP protocol.
The principal advantage of P2P architecture is the resistance to mitigation measures, in ordinary botnet C&C servers represent a point of failure that normally are attacked by security firms in the eradication of malicious architectures, meanwhile in these structure the absence of an explicit point of failure represents a serious obstacle to botnet tracking.
Tracking of Peer to Peer botnets requires the complete node enumeration, while in ordinary botnets it is necessary to find only the C&C servers. The security community has been trying to identify the infected machines in this way, collecting the IP addresses of the participating nodes. The collected items can be used by security defense systems to identify sources of infection, but it's very hard because in many cases, bots are behind firewalls or NAT devices. A commonly used technique to enumerate the compromised host is recursive crawling. A well-crafted crawler in fact could be designed to recursive get-peerlist lookup requests sent to newly discovered IP addresses of infected hosts. The methods fail for those machines that are behind firewalls or NAT devices. Another alternative method that could overcome that limitation is known as Passive P2P Monitor (PPM), which can enumerate the infected hosts regardless whether or not they are behind a firewall or NAT.
Botnet authors don't limit themselves to implementing alternative infrastructures. To avoid tracking and dumping of traffic they adopt UDP protocols for their communication instead of the TCP protocol that is easily detectable. In the case detected by Symantec, the bot doesn't perform any authentication of the packets exchanged, so anyone can impersonate a bot and successfully communicate with other infected machines, downloading stuff like configuration data. This was an Achilles heel that could be used to exploit the malicious network.
The handshake phase between bots is possible using a homemade UDP. After successful connection, the nodes start to exchange TCP data (e.g. Configuration files, list of other peers, etc.).
Despite how many P2P botnets have been already detected, in many cases researchers haven't identified how information is received by C&C node. Nodes are physically transferred to the botmaster. Preliminary researches suggest that stolen information is still transmitted back to botmasters using classic methods rather than relayed through the P2P network.
The Zeus case is not isolated. Kaspersky Lab, in collaboration with the CrowdStrike Intelligence Team, Dell SecureWorks and members of the Honeynet Project, dismantled the second Hlux botnet (aka Kelihos), a malicious infrastructure three times larger than the first botnet Hlux / Kelihos dismantled in September 2011. The new variants of malware incorporate P2P technology to eliminate the need for a C&C server, avoiding detection and the immunization campaigns to decapitate the malicious networks. Another interesting example of P2P botnet is Alureon / TLD4, a malicious botnet that can survive indefinitely in the absence of its C&C servers making difficult their detection.
Botnet based on Tor Networks
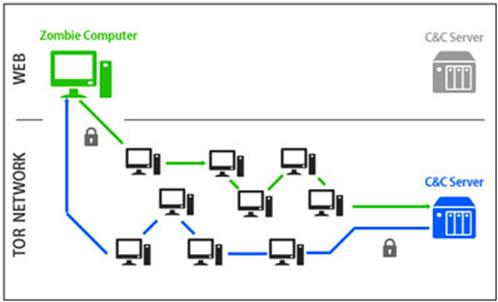
Tor Network is very popular within the cybercrime community that uses it to hide malicious services and sell any kind of product, including drugs and weapons, in total anonymity. In September 2012 the German security firm G Data Software detected a botnet controlled from an Internet Relay Chat (IRC) server running as a hidden service of the Tor.
Figure 2 - Botnet C&C in Tor Network
As expected, the principal advantage to using a botnet with a C&C server located in the Deep Web is that it is difficult to locate them due to the encryption of the connections interior to the Tor network and the unpredictability of the routing of the information.
The security engineer Dennis Brown, during the Defcon Conference in 2010, explained how it is possible to implement botnet architecture having C&C servers hosted in the Tor network.
The principal advantages of adoption of hidden service in a botnet architecture are::
- Availability of Authenticated Hidden Services.
- Availability Private Tor Networks
- Possibility of Exit Node Flooding
Considering that the mechanism used by IDS is based on the detection of known signatures available for the principal botnet agents, the analysis of the data transmitted by bots is essential to discover operations of malicious architectures. Using the Tor network, traffic routed is encrypted making hard the process of analysis, moreover he has hidden services in the Tor network can be accessed only from within the Tor network knowing the assigned .onion address.
Principal security firms use traffic analysis to detect botnet activities and to localize the control servers, typically Intrusion Detection Systems and network analyzers are adopted for the purpose.
Once detected, the botnet to decapitate it use different methods such as:
- IP of C&C server obscuration
- Cleaning of server hosting botnet and of compromised hosts
- Domain name revocation
- Hosting provider de-peered
Dennis Brown proposed a couple of solutions to use Tor network for botnet infrastructure:
- "Tor2Web proxy based model"
- "Proxy-aware Malware over Tor network"
"Tor2Web proxy based model"
The preparation operation for this type of botnets is quite easy due to the large availability of web servers that are easy to set up as hidden services on the Deep Web, and the possibility to retrieve botnet components practically everywhere.
In the solution based on the Tor2Web proxy traffic model, the traffic leaves the Tor network using Tor2Web proxy to redirect .onion web traffic, tor2web allows the access to resources located in Tor network using common browser by changing the domain suffix .onion of any hidden service host to .tor2web.org.
The protocol prefix http:// can also be changed into https:// to use an encrypted connection to the tor2web proxy server in order to provide additional privacy. For example http://eqt5g4fuenphqinx.onion/ would become https://eqt5g4fuenphqinx.tor2web.org/
The scripts to run Command and Control works via Tor2Web so that the bot has to connect to the hidden service passing through the proxy pointing to an address:
http://tor2web.org/fiewfh9sfh2fj
The traffic is redirected by the proxy to the Hidden Service identified by an .onion address. This allows it to maintain secretly the Command & Control servers making tracking them down impossible. The principal weaknesses of this solution relate to the simplicity to filter Tor2Web traffic and the considerable latencies of Tor network that make unresponsive a botnet build with this approach.
"Proxy-aware Malware over Tor network"
A second solution does not use Tor2Web, but makes use of proxy-aware malware that runs Tor on infected hosts. The main difference with respect to the first solution is in the requirements for the bot agents and their configuration. Infected machines need to have SOCKS5 support to be able to connect through Tor to .onion addresses loading Tor on the victim's system.
The approach is more secure than "Tor2Web proxy based model" because traffic isn't routed through a proxy and is entirely within the Tor network due the direct connection between bots and C&C, avoiding the possibility of intercepting data from exit nodes that are not used for this scenario.
This solution is more complex because each bot needs SOCKS5 support, and of course it is necessary that Tor must work properly to maintain the synchronization within the infected PC of the botnet. From a defense point of view, the presence of Tor traffic within a network may indicate the presence of a similar botnet architecture that can be so detected using network anomaly detection methods.
Regarding the possibility of implementing a botnet having C&C servers located in Tor network security experts at G Data declared:
"In other words: Tor tends to be slow and unreliable, and inherits these flaws to underlying botnets."
In the last months, security experts from security firm Rapid7 have detected a botnet controlled by servers located in the Tor network. The botnet, named Skynet, can fulfill different tasks such as mining bitcoin, or to provide bot agents to involve cyber-attacks such as DDoS attacks or spamming. To do this, it includes several components such an IRC-controlled bot, a Tor client for Windows, a Bitcoin mining application and a variant of the famous Zeus malware to steal banking credentials.
Bots are able to receive commands submitted through the IRC channels they connect to. The IRC server is provided as a Tor Hidden Service, and each bot becomes itself a Tor relay increasing the size of the network and increasing the maximum sustainable load.
Resuming the principal advantages of botnets based on Tor are:
- The botnet traffic is encrypted, which helps prevent detection by network monitors.
- By running as a Hidden Service, the origin, location, and nature of the C&C are concealed and therefore not exposed to possible takedowns. In addition, since Hidden Services do not rely on public-facing IP addresses, they can be hosted behind firewalls or NAT-enabled devices such as home computers.
- Hidden Services provides a Tor-specific .onion pseudo top-level domain, which is not exposed to possible sinkholing.
- The operator can easily move around the C&C servers just by re-using the generated private key for the Hidden Service.
The choice of the Tor network appears efficient despite the fact that the Tor network has a great disadvantage in its latency and instability. It must be considered that during the ordinary exercise, bots receive from C&C server little information that consists of command and control messages, in this optic Tor works well enough.
Social network botnet
The primary intent of cybercriminals and botmasters is to reach a wide audience of users remaining hidden to principal security firms, it's natural that they are exploring the possibility to exploit social media platforms.
Social networks have monopolized the majority of user's internet experience; the principal factor of attraction for cyber criminals is the huge number of services —from gaming to payments, that are developing for these platforms that could be exploited to realize more or less complex fraud schemas.
The relationship between social networks and botnet is strict. Social networks could have an active part for bot recruiting, for example, malicious links could be shared to infect the victims transforming them as zombie, and also to host command and control structures.
This second scenario is becoming very common, botnet authors are using various social network platforms to control the infected machines, typically the create fake accounts that send encrypted messages to malware on victims. The principal advantage of this approach is that the traffic related to botnet based on a social network is very hard to detect.
Social network as bot "recruiter"
Many intelligence agencies and Law Enforcement organizations such as the FBI are working to develop a new generation of tools to investigate fraudulent activities that abuse social media platforms to infect a large number of victims. Recently, the U.S. Department of Justice announced the arrest of 10 individuals suspected of having created a botnet that infected more than 11 million PCs all over the world causing financial loss of more than USD 850 million.
The case was noisy, the cyber criminals arrested are accused to have actively participated in the realization of one of the most profitable botnet in the modern history, the botnet Butterfly, also known as Mariposa. In 2008 botnet Butterfly infected 12 million machines worldwide. It was designed to provide illegal services such as spamming and phishing services, denial of service attacks, and stealing of sensitive information.
The cyber criminals used instant messaging platforms and file-sharing platforms to spread the malicious code, another example is provided by the popular Yahos that stole financial information from over 800,000 victims. The malware uses social networks and instant messaging platforms, such as AIM and Yahoo! Messenger, to send "infected links" to the victims that once link to it allow the downloading of botnet exploits.
FBI press release states:
"Facebook's security team provided assistance to law enforcement throughout the investigation by helping to identify the root cause, the perpetrators, and those affected by the malware. Yahos targeted Facebook users from 2010 to October 2012, and security systems were able to detect affected accounts and provide tools to remove these threats."
Another example of use of Social network platforms to spread malware for botnet constitutions is provided by popular Koobface virus, it was one of the first to use them as vehicle of infection.
Koobface, unlike other malware propagated through social networking, uses an "active approach to its spread," infecting each host and then propagate into the network, regardless of user awareness that in some cases deliberately share content with friends.
The most common infection method implemented by Koobface is based on the sharing of malicious content on compromised web site. It is sufficient to click on one of the links which Koobface has posted on this web site. Attackers make large use of social engineering methods to attract users, proposing the download of cool video or applications that hide installer for the Koobface virus. Fortunately this type of malware is identified with little difficulty by the leading antivirus software on the market.
In early 2012 another virus hit Facebook. It was named Ramnit, and it has stolen the usernames and passwords of more than 45,000 users —mainly from France and the UK, according to a bulletin issued by security researchers at Seculert.
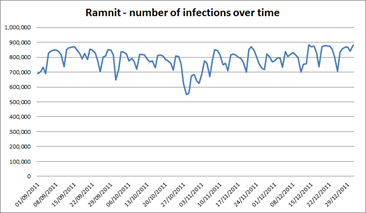
Figure 3 - Ramnit botnet - infections over time
To prevent the spread of malicious agents it is fundamental that users adopt proper behavior and use updated security defense systems, as suggested by the FBI's release.
Social network used to "command and control" infrastructure
The idea to hiding command and control infrastructures within social networks is not new and it's very efficient. Various botmasters are beginning to abuse social network platforms such as Facebook and Twitter as C&C with the purpose of making it difficult to detect malicious architecture and their activities. As described in a previous article, the interactions with social networking sites can be easily automated —hiding "malicious" traffic directed to social media platforms in the large volume of data managed by the platforms. The job is essentially done by a network of fake accounts that post a specific set of encrypted commands destined to malware. The victims query the "bootmaster" profile searching for new command. Botnet architectures having C&C in social media are extremely resilient and allows malware to run for long periods of time. Security experts also noted that malicious infrastructures are becoming even more complex. For example, some of them implemented a steganography engine able to steal commands within images and video posted on social networks by compromised accounts, in this case zombies are able to interpret hidden commands.
Botnets and cyber warfare
Once we have described the principal variants of botnets, let's conclude this second part of the miniseries explaining the use of botnets in a cyber-warfare context. Botnets are a powerful instrument for state-sponsored hackers to conduct cyber offensive or arrange lengthy cyber espionage campaigns. Due this reason botnet creation is considered a military option.
Botnets could be used to attack critical infrastructure of foreign states, and in the majority of cases remaining hidden and avoiding counter offensives. The US government is taking in serious consideration the cyber threat related to the botnets Recently, administrative officials belonging to U.S. President Barack Obama's team declared that the government had started IBG (Industry Botnet Group) —a coordinated project that involves private enterprise and trade units. The mission of the program is increasing the level of awareness of the botnet world through the cooperation of government and private sector. White House Cybersecurity Coordinator Howard Schmidt has deep knowledge of the problem. For this reason, he's convening federal agencies, law enforcement and private companies to define a common strategy to deal with the threat. The principal advantage of botnet is the absence of a good collocation, its components could be distributed everywhere in the world making the identification of the attackers impossible.
During the McAfee Public Sector summit in Arlington, VA, on April 11, 2012, Schmidt declared:
"There's been a lot of discussion about botnets…trying to identify how many are out there, what they're doing, what they could do and what the impact could be. I've asked my office to engage in a private-public partnership to enhance the nation's cyber security by fighting against bot networks,"
"We're teaming U.S. internet service providers, search engines, internet vendors, privacy rights advocates and groups and trade associations to tackle this on all fronts. We're working on developing best practices and an industry code of conduct within the next 90 days."
The group , led by Schmidt, is spending a sensible effort in the battle, working to reach the following four main goals:
- To develop principles for addressing the botnets.
- To establish high-level strategies to increase public awareness on the botnets.
- Leverage available consumer-focused information tools and resources to prevent the botnets from the beginning.
- Identify ways of measuring progress.
The groups constantly analyze the diffusion of principle cyber threats defining methods to measure of the extent of spread of the principal botnets elaborating a set of indicators, globally recognized, that can provide a status on the evolution of the phenomenon. Another key to fighting the proliferation of botnets is to be able to increase the level of awareness of the threat in each sector while also providing the tools necessary to tackle the problem.
According to Schmidt it is necessary to act immediately due the diffused offensive of botnet chat that represents a serious threat for both military and private sectors threatening the security of the nations. What most worries the U.S. government is the high rate of spread of malware in the private sector.It is not easy to counteract the phenomenon. It has-been estimated one in ten Americans has some kind of malicious software on their devices.
"We're looking at what [botnets] might do to a business's infrastructure, to personally identifiable information – identity theft, credit card fraud, et cetera – but it goes beyond that. What we're beginning to see is about 4 million new botnet infections every month…it's a moving target,"
"One of the clear issues we won't be doing anymore is to just sit back and admire the problem. We've done that for too long. We've written strategy after strategy…it's time to move beyond the strategies and actually move into an environment where we're executing on these strategies,"
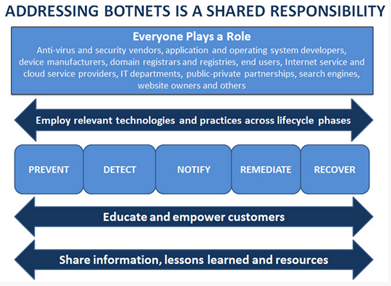
Figure 5 - Industry Botnet Group
Conclusion
In the meantime, worldwide security experts are searching for a common strategy to decapitate the botnets, the cybercrime industry and also state sponsored hackers are designing new complex architecture sable to elude common defense systems, the fight is becoming and need a shared effort to mitigate the threat on a global scale.
In the next, and last, article of the series I'll present you the technologies for botnets hunting … stay tuned!
References
http://www.industrybotnetgroup.org/
https://resources.infosecinstitute.com/botnets-and-cybercrime-introduction/
http://securityaffairs.co/wordpress/6545/cyber-crime/on-new-generation-of-p2p-botnets.html
https://resources.infosecinstitute.com/social-media-use-in-the-military-sector/
http://www.symantec.com/connect/blogs/zeusbotspyeye-p2p-updated-fortifying-botnet
http://blogs.technet.com/b/mmpc/archive/2013/03/14/ramnit-the-renewed-bot-in-town.aspx
http://www-users.cs.umn.edu/~hopper/p2pbot_asiaccs09.pdf
http://www.symantec.com/connect/blogs/zeusbotspyeye-p2p-updated-fortifying-botnet
https://resources.infosecinstitute.com/phishing-dangerous-cyber-threat/

What should you learn next?