Beginner’s Guide to Pentesting IoT Architecture/Network and Setting Up IoT Pentesting Lab - Part 1
In this post, I will explain how to pentest an IoT Network/Architecture. Also, I will explain how to set up an IoT Pentesting lab for getting started with IoT Pentesting. Since the post is too long, to make it digestible, it will be split into two parts.
Let' start….

Earn two pentesting certifications at once!
Enroll in one boot camp to earn both your Certified Ethical Hacker (CEH) and CompTIA PenTest+ certifications — backed with an Exam Pass Guarantee.
Before setting up an IoT lab or learning how to pentest an IoT Network, let's understand how a typical IoT network looks like, what components are involved and how various components share and exchange data with each other. Once the basics are clear and you have a better understanding of various components involved and the communication flow between the components, it will become easy to setup IoT pentesting lab and pentest an IoT Network.
Let's have a look at sample IoT architecture as shown below –
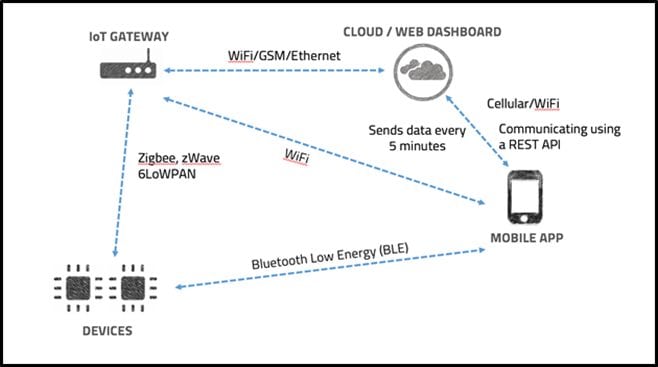
As shown in the above diagram, there are four components involved. They are -
- IoT Device - Can be seen in the diagram termed as DEVICES. The device can be anything, for example, a Smart fan.
- Mobile - Mobile has a mobile application installed on it. The mobile application is needed for controlling the IoT device and sending commands to the cloud.
- Cloud/Web Dashboard - Cloud service for remotely accessing the IoT device.
- IoT gateway - It can be anything. In our case, it's simply a router which provides internet connection to IoT device and Mobile.
Thus, a typical IoT network involves four components. There can be, but chances of coming across these four components are high.
Now let's try to understand the communication flow. For the sake of understanding let's assume that the IoT device is Fan. Also, I am assuming all the components (Mobile, IoT device henceforth Fan, cloud service) are configured and connected with each other for sharing and exchanging the data.
Here's how the various device will communicate -
-
The fan should be connected to mobile and cloud. The mobile application installed on the mobile devoce will control and issue commands to the IoT Device. Example – Turning on/off the Fan. If the owner of the device is near to the Fan, he will directly talk to the device using mobile application else he will make use of Cloud interface for connecting and talking to the device remotely. Thus, a Fan should be configured to talk to mobile application and cloud.
In the diagram, we have a router termed IoT Gateway which will provide internet connection to Fan for connecting to the cloud service. The fan uses a protocol such as Zigbee, zWave, 6LowPan, etc. for connecting to the router and connection between the Mobile application and the Fan locally can be done using a protocol such as Bluetooth as shown in the diagram.
- Mobile application should be connected to the cloud and Fan. The mobile application can use Cellular data or wireless connection (provided by IoT Gateway) for connecting to the cloud, and the communication between mobile application and Fan happens over Bluetooth as said.
- The last component, i.e., Cloud needs to be connected to Mobile Application and Fan, and we have already described the connection in point 2 and three above.
This is how various components need to be configured and connected to each other for sharing and exchanging the data. I hope the communication flow is clear.
Now we have the clear understanding of what an IoT architecture looks like and how various components communicate, share and exchange data, it's easy for us to Pentest an IoT architecture and set up our own IoT Pentesting Lab.
General Steps to be followed for Pentesting an IoT Network -
Pentesting an IoT Environment/Network is no rocket science. It's easy if you follow these steps –
- List all the components involved in the given scope.
- Make an architecture (like the one made above) connecting all the components with each other.
-
Mark how various components communicate with each other and what protocols do they make use of.
You may come across various protocols like ZigBee, Bluetooth, CoAP, MQTT, etc.
- Once the architecture and communication flow is ready, pentest each component independently.
-
After pentesting the components independently, pentest the communication protocol between 2 or more component.
Example - Pentesting Wi-Fi, Bluetooth, ZigBee protocol, etc.
The above steps may feel daunting, but it will be easy to understand since I will be covering each step with the example in the next section.
That's for this post. In the next post, I will explain all the above mentioned using an example, and we will set our own IoT Pentesting lab.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
References –
https://resources.infosecinstitute.com/getting-started-with-iot-security-mapping-the-attack-surface/




