Basic Updated Guide to Recon-ng plus New Modules Rundown
The Recon-ng Framework has undergone some major updates that has improved its functionality and its usage,as well as new modules that were added to the framework. Thanks to Tim Tomes a.k.a LaNMaSteR53 for the updates to the framework!
Because of the new updates and the new commands for working with the framework, I decided to write another tutorial about it because my previous articles entitled 'Awesome Modules of Recon-ng Used for Web Recon Testing' and 'The Recon-ng Framework : Automated Information Gathering' covers the old organization of the modules (Auxiliary, Contacts, Output, Hosts, and Pwnedlist) and how to show all the modules. I do apologize for the outdated tutorial about working with the modules used for web reconnaissance testing because by the time the article was published, the new updates were released.

Earn two pentesting certifications at once!
Enroll in one boot camp to earn both your Certified Ethical Hacker (CEH) and CompTIA PenTest+ certifications — backed with an Exam Pass Guarantee.
Modules are now organized into separate module branches within the module tree for each methodology steps, namely: Reconnaissance, Discovery, and Reporting which are steps one, two and four of the Web Application Penetration Testing Methodology. Tim Tomes explains that "each of these steps has their own branch in the module tree. It is important to understand the difference between Reconnaissance and Discovery. Reconnaissance is the use of open sources to gain information about a target, commonly referred to as 'passive reconnaissance'. Discovery, commonly referred to as 'active reconnaissance', occurs when packets are explicitly sent to the target network in an attempt to 'discover' vulnerabilities. While Recon-ng is a reconnaissance framework, elements from the other steps of the methodology will be included as a convenient place to leverage the power of Python on a penetration test."
Now let's fire up the Recon-ng Framework and list all the modules by typing show modules:
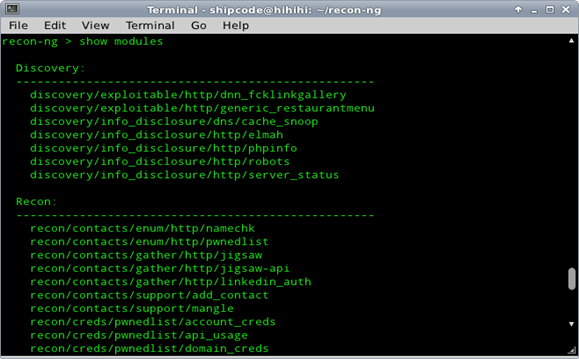
Discovery:
---------------------------------------------------
discovery/exploitable/http/dnn_fcklinkgallery
discovery/exploitable/http/generic_restaurantmenu
discovery/info_disclosure/dns/cache_snoop
discovery/info_disclosure/http/elmah
discovery/info_disclosure/http/phpinfo
discovery/info_disclosure/http/robots
discovery/info_disclosure/http/server_status
Recon:
---------------------------------------------------
recon/contacts/enum/http/namechk
recon/contacts/enum/http/pwnedlist
recon/contacts/gather/http/jigsaw
recon/contacts/gather/http/jigsaw-api
recon/contacts/gather/http/linkedin_auth
recon/contacts/support/add_contact
recon/contacts/support/mangle
recon/creds/pwnedlist/account_creds
recon/creds/pwnedlist/api_usage
recon/creds/pwnedlist/domain_creds
recon/creds/pwnedlist/domain_ispwned
recon/creds/pwnedlist/leak_lookup
recon/creds/support/googli
recon/creds/support/noisette
recon/hosts/enum/dns/resolve
recon/hosts/enum/http/builtwith
recon/hosts/enum/http/ip_neighbor
recon/hosts/enum/http/mywot
recon/hosts/enum/http/netcraft_history
recon/hosts/enum/http/server_enum
recon/hosts/enum/http/siteadvisor_summary
recon/hosts/enum/http/urlvoid
recon/hosts/enum/http/whatweb
recon/hosts/enum/http/xssed
recon/hosts/gather/dns/brute_force
recon/hosts/gather/http/baidu
recon/hosts/gather/http/bing
recon/hosts/gather/http/google
recon/hosts/gather/http/mcafee/mcafee_affil
recon/hosts/gather/http/mcafee/mcafee_dns
recon/hosts/gather/http/mcafee/mcafee_mail
recon/hosts/gather/http/netcraft
recon/hosts/gather/http/shodan
recon/hosts/gather/http/yahoo
recon/hosts/support/add_host
Reporting:
---------------------------------------------------
reporting/csv_file
reporting/html_report
Take note that you need to clone the latest repository to your local system withgit clone https://LaNMaSteR53@bitbucket.org/LaNMaSteR53/recon-ng.git in order to have the latest framework and updated modules. My suggestion is to follow the main repository in order to keep up with the latest updates because of the passion of the contributors and developers in making new pull requests.
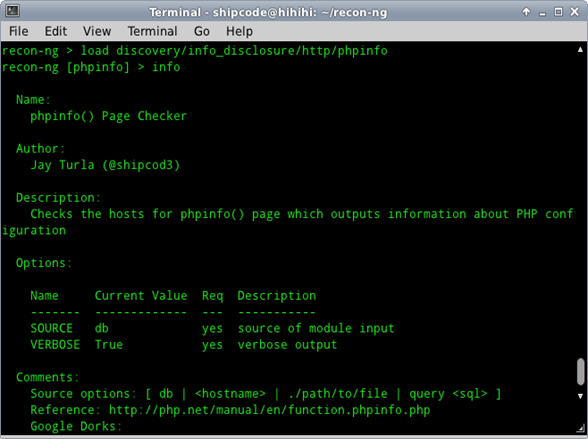
The show and help commands should help you in working with the framework further. Just a heads up to all the new users: the numbers and module types you see after you load the framework and its banner after launching it is just a summary of the modules loaded into the framework. Loading a certain module is easy;For example, you may want to use the discovery/info_disclosure/http/phpinfo module, you can just use the command load discovery/info_disclosure/http/phpinfo.
To check the information and the options of the discovery/info_disclosure/http/phpinfo module, just use the command info discovery/info_disclosure/http/phpinfoor just info if the module has been loaded already.
The query command queries the database and allows the user to interact with the database. Refer to the command show schema for assistance in building SQL queries.
To search for a specific module, use the command search, for example:
recon-ng> search phpinfo
[*] Searching for 'phpinfo'...
Discovery:
----------------------------------------
discovery/info_disclosure/http/phpinfo
For more information on how to use this framework, you can also refer to its wiki guide in Bitbucket. Now, let's move on with the new modules that wererecently added to this framework, which you may find interesting.
GenericRestaurantMenu Vulnerability Page Finder and Validator
The GenericRestaurantMenu Vulnerability Page Finder and Validator is one of the modules that I contributed for recon-ng, which is a discovery module that checks the hosts for possible GenericRestaurantMenu vulnerabilities like the Menu Categories Admin Editor Page, SQL query information disclosure, and possible SQL Injection (boolean-based blind) vulnerabilities.
Sample Usage:
recon-ng> load discovery/exploitable/http/generic_restaurantmenu
recon-ng [generic_restaurantmenu] > set source target.com
SOURCE => target.com
recon-ng [generic_restaurantmenu] > run
[*] http://target.com/Menu/admin/ => 200. Menu Categories Editor Page Found!
[*] http://target.com/menu/view.cfm?category_ID=1' => 500. SQL Query Info Disclosure and Possible SQLi (boolean-based blind) Vulnerability Found!
[*] https://target.com/Menu/admin/ => 404
[*] 2 possibly vulnerable pages found!
This module does not exploit the host but only verifies the host if it is possibly vulnerable for SQL Injections; most websites that use the GenericRestaurantMenu plugin are vulnerable to a boolean-based blind kind of SQL Injection.
phpinfo() Page Checker
phpinfo() Page Checker is another discovery module I contributed to which checks the hosts for possible and known phpinfo() pages, which outputs information about the PHP configuration such as thesystem name, kernel information, configuration file (php.ini) path, PHP version, Apache version, Apache API Version, loaded modules, hashing engines supported and many more.
Sample Usage:
recon-ng> load discovery/info_disclosure/http/phpinfo
recon-ng [phpinfo] > set source target.com
SOURCE => target.com
recon-ng [phpinfo] > run
[*] http://target.com/phpinfo.php => 404
[*] http://target.com/test.php => 200. phpinfo() page found!
[*] https://target.com/phpinfo.php => Error
[*] https://target.com/test.php => Error
[*] 1 phpinfo() pages found
My-IP-Neighbors Lookup
My-IP-Neighbors Lookup is a recon module contributed by Micah Hoffman which checks and leverages my-ip-neighbors.com site for other hosts hosted on the same server.
Sample Usage:
recon-ng> load recon/hosts/enum/http/ip_neighbor
recon-ng [ip_neighbor] > set host infosecinstitute.com
HOST => infosecinstitute.com
recon-ng [ip_neighbor] > run
[*] URL being retrieved: http://www.my-ip-neighbors.com/?domain=infosecinstitute.com
+-------------------------+
| Other Hosts Found |
+-------------------------+
| infosecinstitute.com |
+-------------------------+
Based on the result above, infosecinstitute.com is the only host that is hosted on the server.
Host Adder
Host adder is a support module categorized under the recon module contributed by Drumm which allows users to manually add a host.
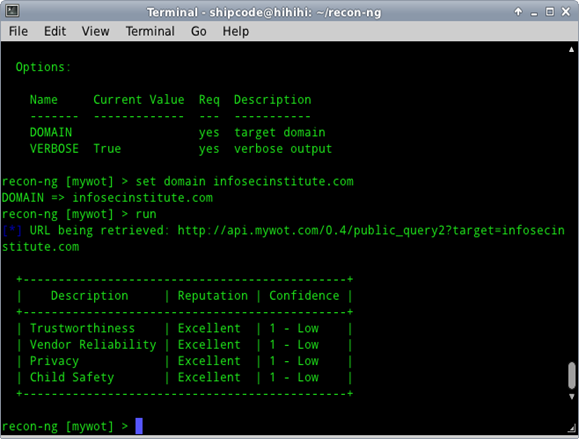
MyWOT Domain Lookup
MyWOT Domain Lookup or Web of Trust Domain Lookup is another recon module contributed by Micah Hoffman which checks and leverages the mywot.com site for information about the security and the trustworthiness of a domain or website. According to WOT's About Us page, "WOT calculates the reputation for websites, using traffic light-style icons displayed via search results, social media platforms, webmail, and many popular sites".
Sample Usage:
recon-ng> load recon/hosts/enum/http/mywot
recon-ng [mywot] > set domain infosecinstitute.com
DOMAIN => infosecinstitute.com
recon-ng [mywot] > run
[*] URL being retrieved: http://api.mywot.com/0.4/public_query2?target=infosecinstitute.com
McAfee SiteAdvisor Lookup
McAfee SiteAdvisor Lookup is a recon module contributed again by Micah Hoffman which checks the siteadvisor.com site for links, third-party cookies, email tests and other information with domains.
Sample Usage:
recon-ng> load recon/hosts/enum/http/siteadvisor_summary
recon-ng [siteadvisor_summary] > set domain google.com
DOMAIN => google.com
recon-ng [siteadvisor_summary] > run
[*] URL being retrieved: http://www.siteadvisor.com/sites/google.com
[*] Country: United States
[*] Visitors: Lots of users
[*] After entering our e-mail address on this site, we received less than 1 e-mail per month.
+----------------------------------+
| Linked to... |
+----------------------------------+
blogger.com
chillingeffects.org
gmailblog.blogspot.com
googleenterprise.blogspot.com
orkut.com
picasaweb.google.com/home
picasaweb.google.com/photos.jobs
youtube.com
URLVoid Domain Lookup
URLVoid Domain Lookup is a recon module contributed by Micah Hoffman which leverages and checks the urlvoid.com site for information such as website reputation, blacklist check, possible malicious codes, page rank, Alexa rank, detection ration, Google page rank and the security of the domain.
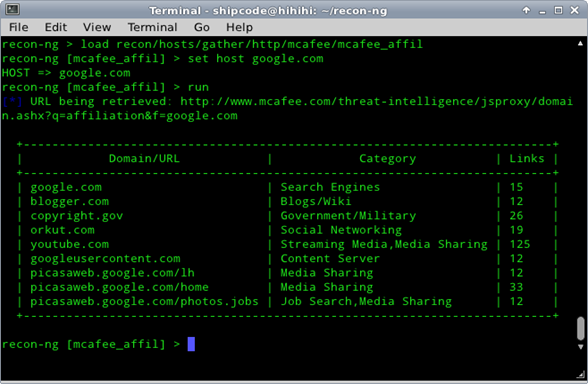
McAfee Domain Affiliation Lookup
McAfee Domain Affiliation Lookup is a recon module contributed by Micah Hoffman which leverages and checks the mcafee.com site for other domains affiliated with a domain.
Sample Usage:
recon-ng> load recon/hosts/gather/http/mcafee/mcafee_affil
recon-ng [mcafee_affil] > set host google.com
HOST => google.com
recon-ng [mcafee_affil] > run
[*] URL being retrieved: http://www.mcafee.com/threat-intelligence/jsproxy/domain.ashx?q=affiliation&f=google.com
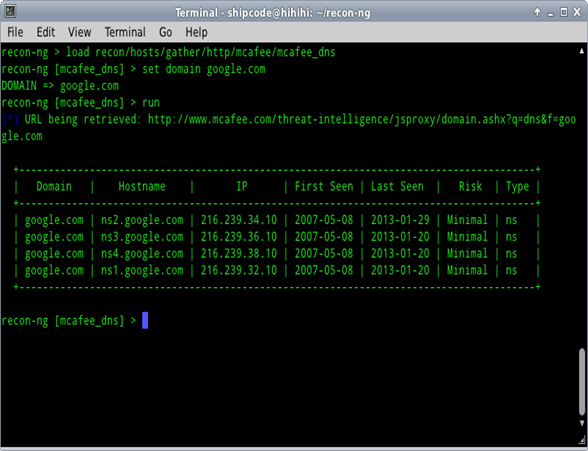
McAfee Domain DNS Lookup
McAfee Domain DNS Lookup is a recon module contributed by Micah Hoffman which leverages and checks mcafee.com site for the DNS information ofa domain.
Sample Usage:
recon-ng> load recon/hosts/gather/http/mcafee/mcafee_dns
recon-ng [mcafee_dns] > set domain google.com
DOMAIN => google.com
recon-ng [mcafee_dns] > run
[*] URL being retrieved: http://www.mcafee.com/threat-intelligence/jsproxy/domain.ashx?q=dns&f=google.com
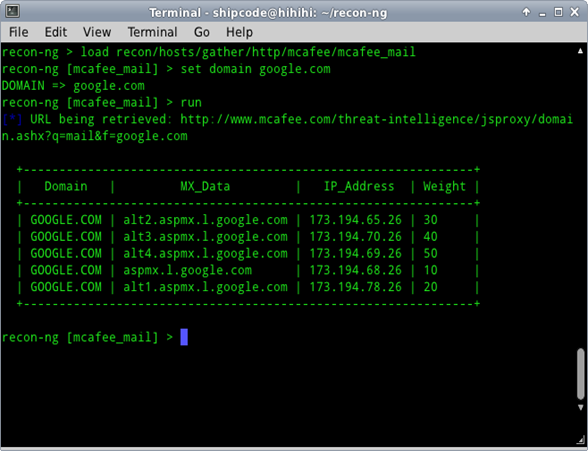
McAfee Mail Host Lookup
McAfee Mail Host Lookup is a recon module contributed by Micah Hoffman which leverages and checks the mcafee.com site for mail servers for a given domain.
Sample Usage:
recon-ng> load recon/hosts/gather/http/mcafee/mcafee_mail
recon-ng [mcafee_mail] > set domain google.cm
DOMAIN => google.cm
recon-ng [mcafee_mail] > set domain google.com
DOMAIN => google.com
recon-ng [mcafee_mail] > run
[*] URL being retrieved: http://www.mcafee.com/threat-intelligence/jsproxy/domain.ashx?q=mail&f=google.com
Final Words:
As of this writing, new pull requests have been submitted to the framework, so don't forget to follow the main repository. As one of the contributors of the Recon-ng framework, I invite you guys to help build this framework by adding new modules which you think can help and improve the function of Recon-ng. See yah!
Resources:
https://bitbucket.org/LaNMaSteR53/recon-ng/wiki/Home
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.






