Alternative Wi-Fi Cracking
Wi-Fi : "WiFi" is the short form for Wireless Fidelity. It is a high speed internet and network connection without the use of wires or cables. It means a type of wireless networking protocol that allows devices to communicate and transfer data wirelessly without cords or cables. Wi-Fi is the registered trademark of Wi-Fi Alliance organization who own it. It defines any wireless local area network which is based on Institute of Electrical and Electronics Engineers (IEEE) 802.11 standards.

Earn two pentesting certifications at once!
Enroll in one boot camp to earn both your Certified Ethical Hacker (CEH) and CompTIA PenTest+ certifications — backed with an Exam Pass Guarantee.
Devices like video game consoles, camera, mobile etc. which have Wi-Fi functionality can connect to internet by using any wireless access point. Such an access point has a range of about 20 meters (65 feet) indoors and a greater range outdoors. Below is an example of an outdoor wireless access point.

Wi-Fi KEYS : Now the question arises why we are using keys and what is the use of the keys? The simple answer is for security, encryption or for locking. So wireless keys are used for encryption which enhances the wireless security of the network. There are two types of standard wireless key support WEP and WPA encryption. For setting up a wireless key on any network first the administrator will have to select an encryption key WEP or WPA on the router. Then, the administrator sets the same value on each wireless device connecting to the router. Wireless keys are hexadecimal numbers that vary in length (but are typically between 128 and 256 bits long) depending on the encryption method used.

-
WEP : The term WEP refers for Wired Equivalent privacy, It is used as a security code for securing wireless networks.
It is a simple sequence of hexadecimal digits which includes the numbers 0-9 and the letters A-F.
The length of a WEP key depends on the type of WEP security utilized:
i) 40-/64bit WEP: 10 digit key
ii) 104-/128bit WEP: 26 digit key
iii) 256bit WEP: 26 digit key
-
WPA :
WPA is a short term for Wi-Fi Protected Access was developed by the networking industry in response to the weaknesses of WEP.
WPA is called the secure encryption method the reason behind this is that WPA has a function of message integrity check which prevents an attacker from capturing, altering or resending data packets.
WPA provides stronger encryption than WEP through use of either of two standard technologies: Temporal Key Integrity Protocol (TKIP) and Advanced Encryption Standard (AES).
A variation of WPA designed for use on home networks is called WPA Pre Shared Key or WPA-PSK for short. WPA-PSK is a simplified but still powerful form of WPA. Now WPA has been replaced by WPA2 which is more secure and reliable.

TUTORIAL : Mainly we noticed that whenever we are going to crack the Wireless WEP key we always use backtrack and it's tools. In this tutorial here I am going to show you how to crack WEP keys without using Backtrack and its tools in Windows platform.
Tools required: 1] CommView for Wi-Fi
2] Aircrack-ng (Windows based)
Now open your "CommView" for Wifi and go to "file option" and click on "file capture" like shown in the figure below:
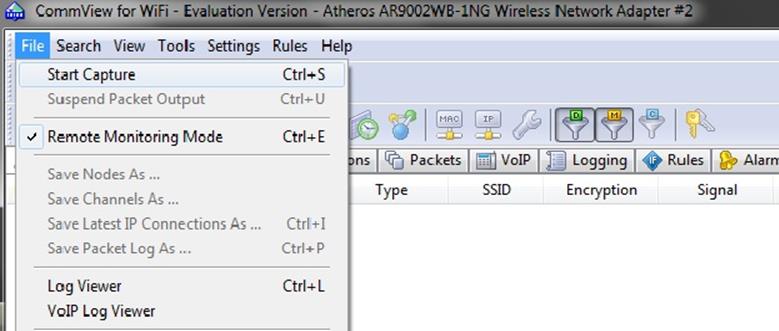
After that a new window appears and then click on "start scanning".
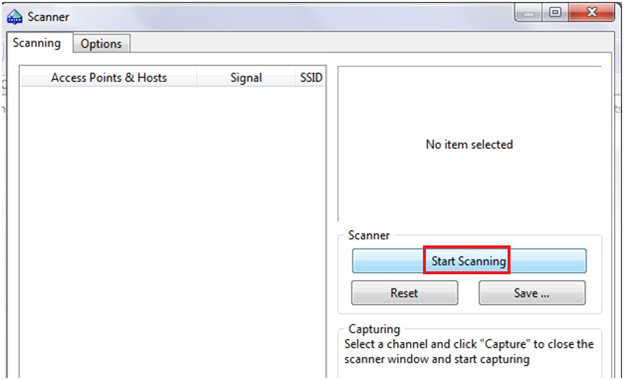
After scanning its shows the list of all channels and the wireless networks which are running on specified channels as shown in the figure below:
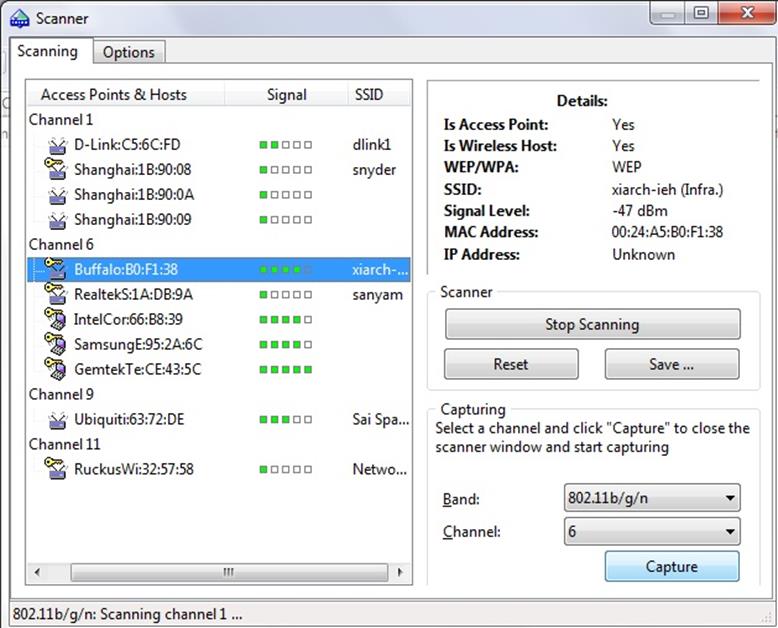
In the above figure I selected a network which is running on channel 6.For details see the right side of the window, it shows the network encryption type, SSID and MAC address. Then click on "capture" and wait for the packet data. You have to create a minimum of 5000 packets for cracking a WEP key. When the numbers of packets are high, it's easier for you to crack the key as shown in the figure below:
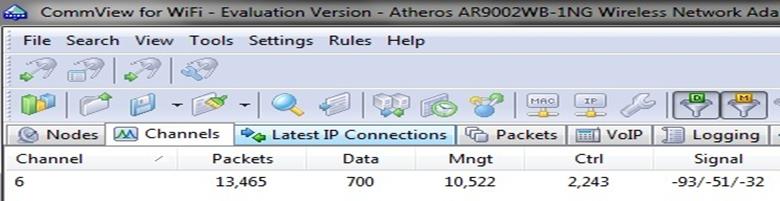
When sufficient packets create the "go to file option", click on "stop capture".

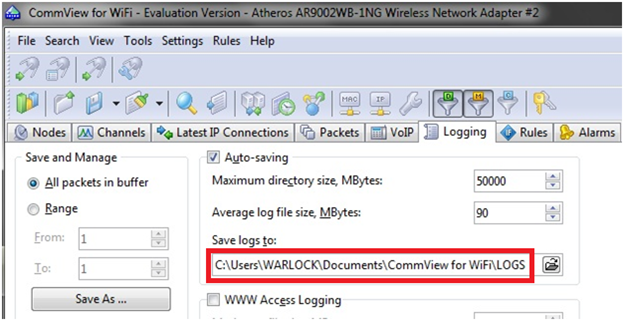
After the capturing process is complete, it creates a log file in the "log folder". You can check your log folder directory by clicking on "log tab". In the figure below it shows the directory of "my log folder" which is in "my documents/CommView for Wifi/Logs".
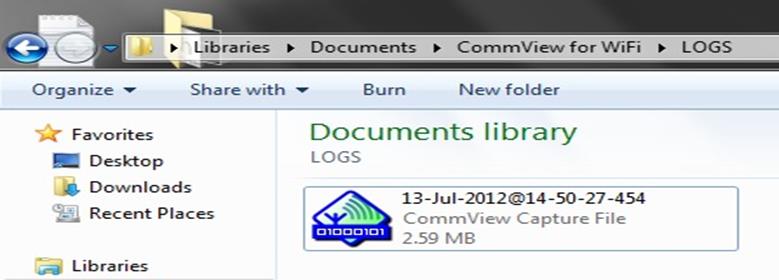
Now go to the log folder there you can see a capture file like shown in the figure below:
Now just double click on the file and a new window appears, then go to "file option" select "export logs" then select "Wireshark/Tcpdump format" and save your file. Here I save my file name as "hack.cap" in my desktop shown in the figure below:
Now open your "Aircrack GUI" and browse for your saved capture file as shown in the figure below:
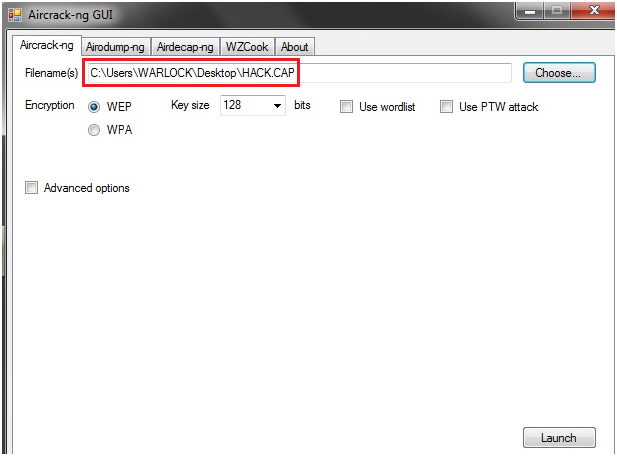
After that click on the "launch button" then a cmd window appears, asking for index no. of target network here my target network index no. is 1 like shown in the figure below:
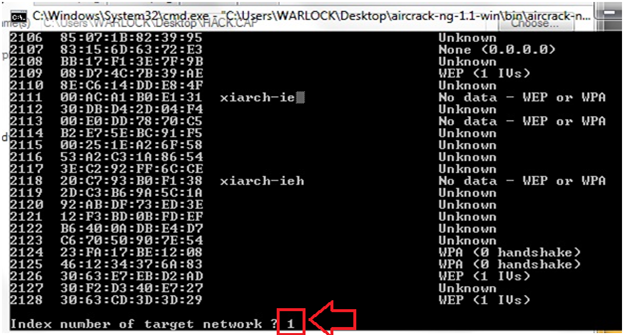
After putting in your index number, press "enter" and the cracking process starts, if the key is decrypted successfully like shown in the figure below:
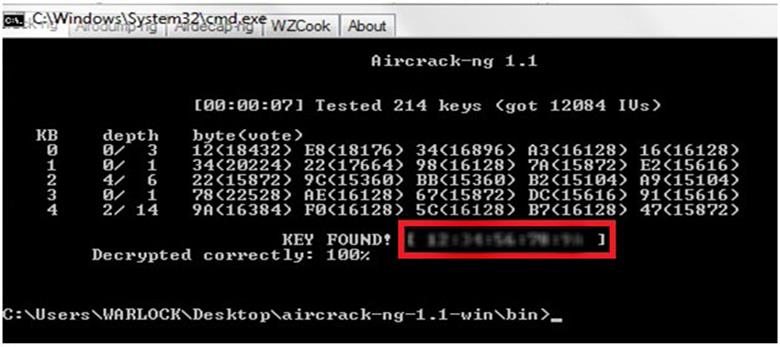
CONCLUSIONS: Hence we conclude that the WEP key is not secured. If we create a 256 bit key that can also be cracked, but that is time consuming and we have to capture a higher number of packets and data.
INTERESTED IN LEARNING MORE? CHECK OUT OUR ETHICAL HACKING TRAINING COURSE. FILL OUT THE FORM BELOW FOR A COURSE SYLLABUS AND PRICING INFORMATION.
REFERENCES:
http://www.squidoo.com/what-is-wifi
http://mobileoffice.about.com/od/glossary/g/wi-fi.htm
http://en.wikipedia.org/wiki/Wi-Fi
http://compnetworking.about.com/od/wirelesssecurity/f/what-is-a-wireless-key.htm
http://compnetworking.about.com/od/wirelessfaqs/f/wep_keys.htm

FREE role-guided training plans
http://compnetworking.about.com/cs/wirelesssecurity/g/bldef_wpa.htm






